Supporting Operating System Installation | 3
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ironkey™ Workspace W200
IRONKEY™ WORKSPACE W200 WINDOWS TO GO CERTIFIED Depend on the Microsoft-certified Windows To Go solution that delivers a true Windows 10 or 8.1 desktop embedded on a trusted IronKey USB flash drive. BENEFITS Affordably deliver a full Windows desktop that boots from USB and uses the DEPLOY AN AFFORDABLE MOBILE available host system resources. ™ WORKSPACE PC ON A STICK SOLUTION Rely on IronKey’s portable desktop Balancing the demands of growing workforces with the restrictions of tight budgets expertise and proven dependability in a can make it difficult to properly equip employees, contractors, field personnel and sleek, rugged new chassis. teleworkers with a mobile computing environment you can trust. Now there’s Equip users to work anywhere using your IronKey Workspace W200 PC on a Stick drives for Windows To Go. Offering an IT-managed corporate desktop image. ultra-affordable alternative to a laptop with a savings of up to 95%, these IronKey drives give mobile workers a full Windows desktop image, including the ability to Protect portable desktops with full disk run all applications directly from the USB device or safely access Office 365, Citrix, encryption and password authentication VPN or other SaaS clients from an IT-managed environment. leveraging Microsoft BitLocker or other third-party software encryption MOBILIZE ACROSS THE ENTERPRISE technology. With IronKey Workspace W200 drives, mobile workers run a complete Windows 10 Completely bypass the host computer or Windows 8.1 Enterprise workspace from a USB 3.0 flash drive on any and any local viruses or loggers for a clean compatible PC, tablet or Mac. -

Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC
Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ Boot Disk User Guide Contents 1.0 Product Overview .......................................................................................................... -

Illustrated Tutorial: Creating a Bootable USB Flash Drive for Windows XP
Illustrated tutorial: Creating a bootable Version 1.0 February 15, 2007 USB flash drive for Windows XP By Greg Shultz The ability to boot Windows XP from a USB Flash Drive (UFD) offers endless possibilities. For example, you might make an easy-to-use troubleshooting tool for booting and analyzing seemingly dead PCs. Or you could transport your favorite applications back and forth from home to work without having to install them on both PCs. However, before you can create a bootable UFD, you must clear a few hurdles. You saw that one coming didn’t you? The first hurdle is having a PC in which the BIOS will allow you to configure the USB port to act as a bootable device. The second hurdle is having a UFD that that will work as a bootable device and that’s large enough and fast enough to boot an operating system such as Windows XP. The third hurdle is finding a way to condense and install Windows XP on a UFD. If you have a PC that was manufactured in the last several years, chances are that its BIOS will allow you to configure the USB port to act as a bootable device. If you have a good qual- ity UFD that’s at least 512 KB and that was manufactured in the last couple of years, you’ve probably cleared the second hurdle. And once you’ve cleared those first two hur- dles, the third one is a piece of cake. All you have to do is download and run some free soft- ware to create the bootable UFD. -

Vembu Hyper-V Virtual Appliance Installation Guide - Offsitedr Vembu Hyper-V Virtual Appliance Installation Guide - Offsitedr
Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR A Hyper-V virtual appliance is a template that creates virtual machines instantly on Hyper-V virtual environment without manual VM creation or separate installation of operating system or Vembu OffsiteDR server. The downloaded file will be in zip format. Unzipping the file will have following: · Virtual appliance template file (VHD) · User Guide on How to deploy Hyper-V Virtual Appliance · ReadMe file Supported Versions: Windows Server 2012 R2, Windows 10 and Windows Server 2016 Steps to Deploy Virtual appliance on Hypervisor: Note: · Copy the downloaded virtual appliance zip file in a Windows/Linux GUI based machine to proceed with deployment. · Provided Virtual Appliance setup have 8 Core CPU and 16GB RAM set by default. It is recommended to have an equivalent configuration or more in the underlying Hyper-V Host. · Open the Hyper-V Manager console. · Right click on the corresponding server under Hyper-V Manager. 2 / 13 Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR · Check whether Virtual Appliance folder contains the 3 folders shown in the screen shot below. · Right click over Hyper-V host → select Import Virtual machine. · Select the folder containing VHD and XML files. 3 / 13 Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR · Select the VM to import and click next. 4 / 13 Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR · Choose import type as appropriate. 5 / 13 Vembu Hyper-V Virtual Appliance Installation Guide - OffsiteDR · Select location of configuration files for the VM and proceed with Next. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Windows Speed Secrets Unleashed
Windows Speed Secrets Unleashed Free E -book Top 10 Ways to Speed Up Windows XP or Vista W W W . T U N E - Y O U R - P C . C O M Table of Contents Windows XP XP Speed Tip #1: Disable Startup Programs ..........................................................................2 XP Speed Tip #2: Increase Virtual Memory ............................................................................5 XP Speed Tip #3: Remove Spyware and Adware ...................................................................8 XP Speed Tip #4: Optimize Visual Effects ..............................................................................9 XP Speed Tip #5: Speed Up File Browsing ..........................................................................12 XP Speed Tip #6: Clean Your Windows Registry .................................................................13 XP Speed Tip #7: Enable Direct Memory Access (DMA) ......................................................14 XP Speed Tip #8: Cleanup Your Hard Disk ..........................................................................17 XP Speed Tip #9: Defrag Your Hard Disk .............................................................................19 XP Speed Tip #10: Disable File Indexing..............................................................................21 Windows Vista Vista Speed Tip #1: Disable Startup Programs .....................................................................22 Vista Speed Tip #2: Increase Virtual Memory .......................................................................25 -

Advanced Windows SIG January 17, 2002 Disk Management Note: Material for Paragraphs 1, 2,And 3 Based on Microsoft Windows XP Inside/Out Chapter 26
Advanced Windows SIG January 17, 2002 Disk Management Note: material for paragraphs 1, 2,and 3 based on Microsoft Windows XP Inside/Out Chapter 26 If you have mastered hard-disk setup utilities from Windows 98 and Me, prepare to unlearn everything you know. Windows XP offers new capabilities and a new set of tools. 1. Definitions • Disk or hard Disk Î physical disk drive installed on computer o First hard disk drive Î Disk 0 o Second hard disk drive Î Disk 1 o Third hard disk drive Î Disk 2 • Basic Disk Î Contains one or more partitions o A partition Î A portion of a disk that functions as if it were a separate disk o A primary partition Î used for starting Windows - can not be further subdivided o An extended partition Î can be further divided into one or more logical drives each of which can be formatted separately and assigned a drive letter • Volume Î When a partition or logical drive is formatted for a particular file system (FAT, FAT32, or NTFS) and assigned a drive letter, it is called a volume Disk Management rev 1.doc Page 1 of 5 1/16/2002 D R Wright 2. Windows XP Disk Management Utility • Provides tools to manage disks, partitions, volumes and logical drives • Go to Start Î Right click My Computer Î Manage Î Disk Management • Perform the following tasks: o Check size, file system, status o Create partitions, logical drives, and volumes o Assign drive letters to hard disk volumes, removable disk drives, and CD-ROM drives o Changes usually take effect immediately and without need to reboot 3. -

Windows 7 Bitlocker™ Drive Encryption Security Policy for FIPS 140-2 Validation
Windows 7 BitLocker™ Security Policy Page 1 of 16 Windows 7 BitLocker™ Drive Encryption Security Policy For FIPS 140-2 Validation For Windows 7 Document version 1.0 08/31/2011 1. Table of Contents 1. TABLE OF CONTENTS ......................................................................................................................... 1 2. INTRODUCTION .................................................................................................................................. 2 2.1 List of Cryptographic Modules ........................................................................................................................... 2 2.2 Brief Module Description ................................................................................................................................... 3 2.3 Validated Platforms ........................................................................................................................................... 4 3. INTEGRITY CHAIN OF TRUST .......................................................................................................... 4 4. CRYPTOGRAPHIC BOUNDARIES ..................................................................................................... 5 4.1 Overall Cryptographic Boundary........................................................................................................................ 5 4.2 BitLocker™ Components Included in the Boundary .......................................................................................... 5 4.3 Other Windows -

Devicelock® DLP 8.3 User Manual
DeviceLock® DLP 8.3 User Manual © 1996-2020 DeviceLock, Inc. All Rights Reserved. Information in this document is subject to change without notice. No part of this document may be reproduced or transmitted in any form or by any means for any purpose other than the purchaser’s personal use without the prior written permission of DeviceLock, Inc. Trademarks DeviceLock and the DeviceLock logo are registered trademarks of DeviceLock, Inc. All other product names, service marks, and trademarks mentioned herein are trademarks of their respective owners. DeviceLock DLP - User Manual Software version: 8.3 Updated: March 2020 Contents About This Manual . .8 Conventions . 8 DeviceLock Overview . .9 General Information . 9 Managed Access Control . 13 DeviceLock Service for Mac . 17 DeviceLock Content Security Server . 18 How Search Server Works . 18 ContentLock and NetworkLock . 20 ContentLock and NetworkLock Licensing . 24 Basic Security Rules . 25 Installing DeviceLock . .26 System Requirements . 26 Deploying DeviceLock Service for Windows . 30 Interactive Installation . 30 Unattended Installation . 35 Installation via Microsoft Systems Management Server . 36 Installation via DeviceLock Management Console . 36 Installation via DeviceLock Enterprise Manager . 37 Installation via Group Policy . 38 Installation via DeviceLock Enterprise Server . 44 Deploying DeviceLock Service for Mac . 45 Interactive Installation . 45 Command Line Utility . 47 Unattended Installation . 48 Installing Management Consoles . 49 Installing DeviceLock Enterprise Server . 52 Installation Steps . 52 Installing and Accessing DeviceLock WebConsole . 65 Prepare for Installation . 65 Install the DeviceLock WebConsole . 66 Access the DeviceLock WebConsole . 67 Installing DeviceLock Content Security Server . 68 Prepare to Install . 68 Start Installation . 70 Perform Configuration and Complete Installation . 71 DeviceLock Consoles and Tools . -
Understanding Windows 10 – a Guide to Help Get You Started Settings
Understanding Windows 10 – A Guide to Help Get you Started By Jim Hillier – July 14, 2015 https://davescomputertips.com/understanding-windows-10-a-guide-to-help-get-you-started/ Following an initial perusal of Windows 10 it appeared that Microsoft included a lot of changes merely for the sake of change, presumably to help expand the gap between Windows 8 and Windows 10. However, after spending more time working with the new operating system you will realize that statement is incorrect, and here’s why. Settings – The Windows 10 Nerve Center At the very heart of Windows 10 is the ―Settings‖ menu which provides the interface for managing how the operating system displays and behaves. Consequently, a number of previously easily accessible settings/options have been moved into the Settings menus for the sake of centralization. While this may well now force users to dig a little deeper in order to locate a particular setting, I can appreciate the logic behind it, everything in one place, and no fragmentation. Finding “Screen Resolution in Windows 10 For example: Accessing ―Screen Resolution‖ settings has long been a simple matter of selecting the option from the desktop right click menu. Now, in Windows 10, one needs to take a rather more convoluted path: 1. Click Start and then Settings 2. Click System, then click Display(the Display tab should open by default) 3. Click ―Advanced display settings‖ There it is! Adding Desktop Shortcuts to System Locations in Windows 10 This is another setting location that has changed and integrated into the all, encompassing Settings menu. -
Flexapp™ Techbrief: Using Vhds Vs. Vmdks Page 1
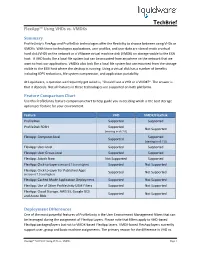
TechBrief FlexApp™ Using VHDs vs. VMDKs Summary ProfileUnity’s FlexApp and ProfileDisk technologies offer the flexibility to choose between using VHDs or VMDKs. With these technologies applications, user profiles, and user data are stored inside a virtual hard disk (VHD) on the network or a VMware virtual machine disk (VMDK) on storage visible to the ESXi host. A VHD looks like a local file system but can be mounted from anywhere on the network that we want to host our applications. VMDKs also look like a local file system but are mounted from the storage visible to the ESXi host where the desktop is running. Using a virtual disk has a number of benefits including IOPS reductions, file system compression, and application portability. At Liquidware, a question we frequently get asked is, “Should I use a VHD or a VMDK?”. The answer is that it depends. Not all features in these technologies are supported on both platforms. Feature Comparison Chart Use this ProfileUnity feature comparison chart to help guide you in deciding which is the best storage option per feature for your environment. Feature VHD VMDK/FlexDisk ProfileDisk Supported Supported ProfileDisk RDSH Supported Not Supported (starting in v6.7.0) FlexApp: Computer-level Supported Supported (starting in v6.7.0) FlexApp: User-level Supported Supported FlexApp: User Group-level Supported Supported FlexApp: Attach Now Not Supported Supported FlexApp: Click-to-Layer (version 6.7.0 and higher) Supported Not Supported FlexApp: Click-to-Layer for Published Apps Supported Not Supported (version 6.7.0 and higher) FlexApp: Cached Mode Application Deployment Supported Not Supported FlexApp: Use of Other ProfileUnity UEM Filters Supported Not Supported FlexApp: Cloud Storage, AWS S3, Google GCS Supported Not Supported and Azure Blob Deployment Differences One of the most powerful features of ProfileUnity is the User Environment Management filters that can be leveraged during the assignment of FlexApp Layers. -

Guidelines for Designing Embedded Systems with Windows 10 Iot Enterprise
Guidelines for Designing Embedded Systems with Windows 10 IoT Enterprise Version 2.0 Published July 15, 2016 Guidelines for designing embedded systems 1 CONFIDENTIAL Contents Overview .................................................................................................................................................................................................... 4 Building a task-specific experience ............................................................................................................................................ 4 General Group Policy settings ....................................................................................................................................................... 4 Application control ................................................................................................................................................................................ 5 Application boot options ................................................................................................................................................................. 5 Auto-boot Universal Windows apps ...................................................................................................................................... 5 Auto-boot Classic Windows apps ........................................................................................................................................... 5 Limit application access with AppLocker ...............................................................................................................................