Verification of Railway Interlocking Systems
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Identification and Localization of Track Circuit False Occupancy Failures Based on Frequency Domain Reflectometry
sensors Article Identification and Localization of Track Circuit False Occupancy Failures Based on Frequency Domain Reflectometry Tiago A. Alvarenga 1 , Augusto S. Cerqueira 1 , Luciano M. A. Filho 1 , Rafael A. Nobrega 1 , Leonardo M. Honorio 1,* and Henrique Veloso 2 1 Electrical Engineering Department, Federal University of Juiz de Fora, Juiz de Fora 36036-900, MG, Brazil; [email protected] (T.A.A.); [email protected] (A.S.C.); luciano.ma.fi[email protected] (L.M.A.F.); [email protected] (R.A.N.) 2 MRS Logística, Juiz de Fora 36060-010, MG, Brazil; [email protected] * Correspondence: [email protected] Received: 15 October 2020; Accepted: 9 December 2020; Published: 18 December 2020 Abstract: Railway track circuit failures can cause significant train delays and economic losses. A crucial point of the railway operation system is the corrective maintenance process. During this operation, the railway lines have the circulation of trains interrupted in the respective sector, where traffic restoration occurs only after completing the maintenance process. Depending on the cause and length of the track circuit, identifying and solving the problem may take a long time. A tool that assists in track circuit fault detection during an inspection adds agility and efficiency in its restoration and cost reduction. This paper presents a new method, based on frequency domain reflectometry, to diagnose and locate false occupancy failures of track circuits. Initially, simulations are performed considering simplified track circuit approximations to demonstrate the operation of the proposed method, where the fault position is estimated by identifying the null points and through non-linear regression on signal amplitude response. -

ERTMS/ETCS Railway Signalling
Appendix A ERTMS/ETCS Railway Signalling Salvatore Sabina, Fabio Poli and Nazelie Kassabian A.1 Interoperable Constituents The basic interoperability constituents in the Control-Command and Signalling Sub- systems are, respectively, defined in TableA.1 for the Control-Command and Sig- nalling On-board Subsystem [1] and TableA.2 for the Control-Command and Sig- nalling Trackside Subsystem [1]. The functions of basic interoperability constituents may be combined to form a group. This group is then defined by those functions and by its remaining exter- nal interfaces. If a group is formed in this way, it shall be considered as an inter- operability constituent. TableA.3 lists the groups of interoperability constituents of the Control-Command and Signalling On-board Subsystem [1]. TableA.4 lists the groups of interoperability constituents of the Control-Command and Signalling Trackside Subsystem [1]. S. Sabina (B) Ansaldo STS S.p.A, Via Paolo Mantovani 3-5, 16151 Genova, Italy e-mail: [email protected] F. Poli Ansaldo STS S.p.A, Via Ferrante Imparato 184, 80147 Napoli, Italy e-mail: [email protected] N. Kassabian Ansaldo STS S.p.A, Via Volvera 50, 10045 Piossasco Torino, Italy e-mail: [email protected] © Springer International Publishing AG, part of Springer Nature 2018 233 L. Lo Presti and S. Sabina (eds.), GNSS for Rail Transportation,PoliTO Springer Series, https://doi.org/10.1007/978-3-319-79084-8 234 Appendix A: ERTMS/ETCS Railway Signalling Table A.1 Basic interoperability constituents in the Control-Command -

CBTC Test Simulation Bench
Computers in Railways XII 485 CBTC test simulation bench J. M. Mera, I. Gómez-Rey & E. Rodrigo CITEF (Railway Technology Research Centre), Escuela Técnica Superior de Ingenieros Industriales, Universidad Politécnica de Madrid, Spain Abstract Due to its safety characteristics, signalling equipment requires a great amount of testing and validation during the different stages of its life cycle, and particularly during the installation and commissioning of a new line or upgrade of an existing line, the latter being even more complicated due to the short engineering periods available overnight. This project aims to develop a tool to reduce the above-mentioned efforts by simulating the CBTC trackside, fulfilling the interfaces between subsystems and elements of these subsystems, and using some real elements. In this way, a testing environment for signalling equipment and data has been developed for the CBTC system. The aims of the project that were set out at the beginning of the development and completed with the present simulator are as follows: Real CBTC equipment trials and integration: CBTC on-board equipment, CBTC Radio Centre, etc. Other signalling elements trials and integration: interlockings and SCCs. CBTC track data validation. In order to achieve these objectives, various simulation applications have been developed, of which the most important are the following: Infrastructure, Automatic trains, Train systems, Planning and Control Desk, etc. This system has been developed, and is currently adding new modules and functionalities, for companies of the Invensys Group: Westinghouse Rail WIT Transactions on The Built Environment, Vol 114, © 2010 WIT Press www.witpress.com, ISSN 1743-3509 (on-line) doi:10.2495/CR100451 486 Computers in Railways XII Systems in the UK and Dimetronic Signals in Spain, which are using it for the new CBTC lines under their responsibility. -

Report on Railway Accident with Freight Car Set That Rolled Uncontrolledly from Alnabru to Sydhavna on 24 March 2010
Issued March 2011 REPORT JB 2011/03 REPORT ON RAILWAY ACCIDENT WITH FREIGHT CAR SET THAT ROLLED UNCONTROLLEDLY FROM ALNABRU TO SYDHAVNA ON 24 MARCH 2010 Accident Investigation Board Norway • P.O. Box 213, N-2001 Lillestrøm, Norway • Phone: + 47 63 89 63 00 • Fax: + 47 63 89 63 01 www.aibn.no • [email protected] This report has been translated into English and published by the AIBN to facilitate access by international readers. As accurate as the translation might be, the original Norwegian text takes precedence as the report of reference. The Accident Investigation Board has compiled this report for the sole purpose of improving railway safety. The object of any investigation is to identify faults or discrepancies which may endanger railway safety, whether or not these are causal factors in the accident, and to make safety recommendations. It is not the Board’s task to apportion blame or liability. Use of this report for any other purpose than for railway safety should be avoided. Photos: AIBN and Ruter As Accident Investigation Board Norway Page 2 TABLE OF CONTENTS NOTIFICATION OF THE ACCIDENT ............................................................................................. 4 SUMMARY ......................................................................................................................................... 4 1. INFORMATION ABOUT THE ACCIDENT ..................................................................... 6 1.1 Chain of events ................................................................................................................... -

Geographic Signaling System (Geo)
FIELD REFERENCE MANUAL GEOGRAPHIC SIGNALING SYSTEM (GEO) JULY 2008 (REVISED SEPTEMBER 2018) DOCUMENT NO. SIG-00-05-09 VERSION D Siemens Mobility 700 East Waterfront Drive Munhall, Pennsylvania 15120 1-800-793-SAFE Copyright © 2008-2018 Siemens Mobility, Inc. All rights reserved PRINTED IN THE U.S.A. PROPRIETARY INFORMATION The material contained herein constitutes proprietary and confidential information, and is the intellectual property of Siemens Mobility, Inc., Rail Automation (Siemens) protected under United States patent, copyright and/or other laws and international treaty provisions. This information and the software it describes are for authorized use only, and may not be: (i) modified, translated, reverse engineered, decompiled, disassembled or used to create derivative works; (ii) copied or reproduced for any reason other than specific application needs; or (iii) rented, leased, lent, sublicensed, distributed, remarketed, or in any way transferred; without the prior written authorization of Siemens. This proprietary notice and any other associated labels may not be removed. TRANSLATIONS The manuals and product information of Siemens Mobility, Inc. are intended to be produced and read in English. Any translation of the manuals and product information are unofficial and can be imprecise and inaccurate in whole or in part. Siemens Mobility, Inc. does not warrant the accuracy, reliability, or timeliness of any information contained in any translation of manual or product information from its original official released version in English and shall not be liable for any losses caused by such reliance on the accuracy, reliability, or timeliness of such information. Any person or entity that relies on translated information does so at his or her own risk. -

Track Inspection – 2009
Santa Cruz County Regional Transportation Commission Track Maintenance Planning / Cost Evaluation for the Santa Cruz Branch Watsonville Junction, CA to Davenport, CA Prepared for Egan Consulting Group December 2009 HDR Engineering 500 108th Avenue NE, Suite 1200 Bellevue, WA 98004 CONFIDENTIAL Table of Contents Executive Summary 4 Section 1.0 Introduction 10 Section 1.1 Description of Types of Maintenance 10 Section 1.2 Maintenance Criteria and Classes of Track 11 Section 2.0 Components of Railroad Track 12 Section 2.1 Rail and Rail Fittings 13 Section 2.1.1 Types of Rail 13 Section 2.1.2 Rail Condition 14 Section 2.1.3 Rail Joint Condition 17 Section 2.1.4 Recommendations for Rail and 17 Joint Maintenance Section 2.2 Ties 20 Section 2.2.1 Tie Condition 21 Section 2.2.2 Recommendations for Tie Maintenance 23 Section 2.3 Ballast, Subballst, Subgrade, and Drainage 24 Section 2.3.1 Description of Railroad Ballast, Subballst, 24 Subgrade, and Drainage Section 2.3.2 Ballast, Subgrade, and Drainage Conditions 26 and Recommendations Section 2.4 Effects of Rail Car Weight 29 Section 3.0 Track Geometry 31 Section 3.1 Description of Track Geometry 31 Section 3.2 Track Geometry at the “Micro-Level” 31 Section 3.3 Track Geometry at the “Macro-Level” 32 Santa Cruz County Regional Transportation Commission Page 2 of 76 Santa Cruz Branch Maintenance Study CONFIDENTIAL Section 3.4 Equipment and Operating Recommendations 33 Following from Track Geometry Section 4.0 Specific Conditions Along the 34 Santa Cruz Branch Section 5.0 Summary of Grade Crossing -

A Dccconcepts “Modelling Advice” Publication
A DCCconcepts “Modelling advice” publication DCC Advice #11 Page 1 Wiring Point-work & Special track conditions for DC or DCC Wiring the track… In plain English, with diagrams! If we had a $ or £ or € for every time we’ve been asked how to wire track and point-work, we’d be writing this on a beach somewhere while sipping a cold beer! A great layout needs good trackwork, so first - a word about trackwork and getting good performance. Choose carefully! DO think about making your own turnouts if you have even moderate skills. It is not as hard as you think, needs only basic skills and tools... and we do our best to make it easy with our top quality gauges, trackwork frets and templates. PLUS we will soon provide a detailed “How to make track” tutorial too. Interested? Then call or email us and we will do our best to help you. No matter what scale you will model in, DO NOT even consider using insulated frogs! Yes, lazy retailers who do not understand what they sell - and modellers who have never done a proper job of laying track so it runs well may well recommend it to you… but do NOT be tempted. No matter which brand makes the turnouts, if you use insulated frogs, you WILL have small locos stalling or also suffer from wider wheels bridging the frog tip and creating momentary shorts that are hard to fix and really are a source of constant frustration. Use more realistic rail sizes please: Usually this will be code 55 in N, or Code 75 and 83 in OO or HO Scale. -

Appendix J Haddington Branch Line Survey
Appendix J Haddington Branch Line Survey AllanRail East Lothian Access STAG Physical feasibility of re-opening the Haddington Rail Branch Line Background The reopening of the Haddington Railway branch line from the East Coast Main Line (ECML) at Longniddry to Haddington is one of the options that are required to be considered in the East Lothian Access STAG. This initial report informs the appraisal work of the feasibility of re-opening the railway, some of the issues and problems that would need to be resolved, choices that are available and suggests an order of magnitude cost. Because the rest of the railway is electrified it is assumed that the Haddington branch will also be equipped with standard 25Kv overhead electrification equipment. The report is based on a physical site walk-over on 21 February 2019, carried out by David Prescott of AllanRail who has considerable experience in the initial development of re-opened railways in Scotland including walk-overs on the Stirling – Alloa – Kincardine, Airdrie- Bathgate and Borders Railway routes in the inception and pre-construction stages. This is not an engineering assessment, but an initial view based on observation and experience. The route is considered in the Longniddry to Haddington direction and the report is broken down into key route sections. Connecting to the ECML The ideal connection to the main line has several desirable operating and engineering requirements: · It should be on the Edinburgh side of Longniddry to minimise the occupation of the ECML; · It should provide as -

Customer Track Maintenance Guide Winter Safety
Customer Track Maintenance Guide Winter Safety Safety is of the utmost importance at CN, not only for our employees but Our goal is to move your products as quickly and safely as possible. also for you, our customers. Please contact your service delivery representative or account manager if you have any questions. We’ve developed this Customer Track Maintenance Guide in order to help bring attention to the additional hazards that are present during the winter Additional information on our seasonal safety guidelines can be found at: months, especially for our crews performing switching activities. www.cn.ca/seasonalsafety Winter is a challenging time for a railroad; many of the service disruptions are caused by accumulations of snow and ice. On the track, problems with switches and crossings are mainly caused by snow — so clearing the snow solves the problem. 3 Flangeways wheel flange Be particularly vigilant where flangeways can be become contaminated with snow, ice, or other material, or where any trackage is covered by excessive amounts of snow or ice, or other material. Ensure equipment can be carefully operated through flangeway over such track. flangeway Be especially aware at crossings, as these are prone to these types minimum of 1.5” clear rail of conditions. of ice, snow, mud, etc. At a minimum, flangeways must be cleared to a depth of 1.5”. Acceptable: Not acceptable: 4 Switches Be aware that switches can become very difficult to line due to cold weather and snow/ice build-up in the switch points. Attempting to line a stiff switch can and does lead to back, leg and arm injuries. -
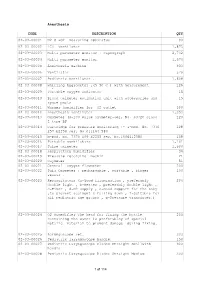
Anesthesia CODE DESCRIPTION QTY 02-03-00001 N2 O +O2
Anesthesia CODE DESCRIPTION QTY 02-03-00001 N2 O +O2 measuring apparatus 90 02-03-00002 ICU Ventilator 1,875 02-03-00003 Multi parameter monitor + capnograph 2,742 02-03-00004 Multi parameter monitor 1,674 02-03-00005 Anesthesia machine 933 02-03-00006 Ventilator 579 02-03-00007 Pediatric ventilator . 1,608 02-03-00008 Whirling hygrometer ,(5-50 C ) with measurement 129 ruler . 02-03-00009 Portable oxygen indicator 15 02-03-00010 Blood oximeter estimation unit with accessories and 15 spare parts 02-03-00011 Warmer humidifier for O2 outlet 300 02-03-00012 Anesthesia Ventilator 1,353 02-03-00013 Oxymeter (S-100 pulse oxymeter-ser, No. S0720 class 120 I type BF 02-03-00014 Cartridge for pressure monitoring :- a-mod. No. 7370 108 257 E2258 ser, No.011164 580 02-03-00015 b-mod. No. 7370 109 E2255 ser, No.1006412580 108 02-03-00016 Portable ventilators 1,101 02-03-00017 Pulse oximeter 1,500 02-03-00018 Respiratory humidifier 36 02-03-00019 Pressure recording machin 21 02-03-00020 Oxymeter 51 02-03-00021 Central oxygen flowmeter 200 02-03-00022 Puls Oxymeter : rechargable , portable , finger 100 sensor . 02-03-00023 Resuscitators (a-Good illumination , preferably 204 double light , b-Heater , preferably double light , c-Timer , d-O2 supply , e-Good support for the baby ,to prevent accident & falling down , f-Suitable for all pediatric age groups , g-Pressure transducer.) 02-03-00024 O2 Humedifier The head for fixing the bottle 200 containing the water is preferabley of special metalic material to prevent damage during fixing. -
8. Portishead to Portbury Dock Junction Overview 17 9
Ref: GS2/140569 Version: 1.00 Date: July 2014 Contents 1. Executive Summary 1 2. Introduction 3 3. Business Objective 6 4. Business Case 9 5. Project Scope 11 6. Deliverables 12 7. Options Considered 13 8. Portishead to Portbury Dock Junction Overview 17 9. Engineering Options 19 10. Bathampton Turnback 52 11. Constructability and Access Strategy 53 12. Cost Estimates 56 13. Project Risks and Assumptions 57 14. High level business case appraisal against whole life costings 58 15. Project Schedule 59 16. Capacity/Route Runner Modelling 60 17. Interface with other Projects 61 18. Impact on Existing Customers, Operators and Maintenance Practice 62 19. Consents Strategy 63 20. Environmental Appraisal 64 21. Common Safety Method for Risk Evaluation Assessment (CSM) 65 22. Contracting Strategy 66 23. Concept Design Deliverables 67 24. Conclusion and Recommendations 68 References 70 Formal Acceptance of Selected Option by Client, Funders and Stakeholders 71 GRIP Stage 2 Governance for Railway Investment Projects Ref: GS2/140569 Version: 1.00 Date: July 2014 Appendices A Drawings B Cost Estimate C Qualitative Cost Risk Analysis D Capacity Modelling E Environmental Appraisal F Signalling Appraisal G Photograph Gallery H Track Bed Investigation (Factual, Interpretative and Hazardous Classification) I Visualisations (Galingaleway and Sheepway Gate Farm) J Interdisciplinary Design Certificate K Portishead Station Options Appraisal Report (produced by North Somerset Council) GRIP Stage 2 Governance for Railway Investment Projects Ref: GS2/140569 Version: 1.00 Date: July 2014 Issue Record Issue No Brief History Of Amendment Date of Issue 0.01 First Draft 30 May 2014 0.02 Second Draft updated to include comments 13 June 2014 1.00 Report Issued 18 July 2014 Distribution List Name Organisation Issue No. -

HOW to REDUCE the IMPACT of TRACK CIRCUIT FAILURES Stanislas Pinte, Maurizio Palumbo, Emmanuel Fernandes, Robert Grant ERTMS Solutions/Nxgen Rail Services
S. Pinte, M. Palumbo, E. Fernandes, R. Grant HOW TO REDUCE THE IMPACT OF TRACK CIRCUITS FAILURES ERTMS Solutions/NxGen Rail Services HOW TO REDUCE THE IMPACT OF TRACK CIRCUIT FAILURES Stanislas Pinte, Maurizio Palumbo, Emmanuel Fernandes, Robert Grant ERTMS Solutions/NxGen Rail Services Summary Every year, thousands of track circuit failures are reported by railway infrastructure managers in Europe and worldwide, resulting in significant delays which can also lead to substantial economic costs and penalties. For this reason, the ability to detect and diagnose the health of track circuits to prevent or provide a fast response to these failures, can generate a significant benefit for infrastructure managers. In many countries, a process of periodic manual inspection of wayside assets (including track circuits) is in place, but the benefits of this strategy are limited by several factors related to safety, the time required to perform the inspection, and difficulties associated with making manual measurements. With the purpose of minimizing economic loss and operational delay, as well as offering railway infrastructure managers a tool that can provide an automated and effective maintenance strategy, ERTMS Solutions has designed the TrackCircuitLifeCheck (TLC). The TrackCircuitLifeCheck is a track circuit measurement instrument that can be installed on track inspection or commercial trains to automatically diagnose AC, DC, and pulsed track circuits, thus enabling a preventive maintenance strategy, based on the analysis of multi-pass data from each track circuit over time, and the application of standard deviation analysis. KEYWORDS: Track Circuits, Preventive Maintenance, Train Detection, Train Protection, In-Cab Signaling, UM-71, TVM, TrackCircuitLifeCheck. INTRODUCTION This paper presents a high level functional and architectural description of track circuits, with a In order to detect the presence of trains on a special focus on AC track circuits.