Compounding Offenses
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-
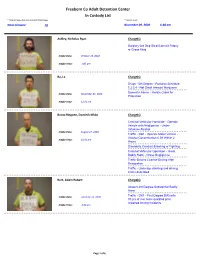
In Custody List **Total Inmates Does Not Include ICE Detainees **Current As Of: Total Inmates: 28 November 09, 2020 6:48 Am
Freeborn Co Adult Detenton Center In Custody List **Total Inmates does not include ICE Detainees **Current as of: Total Inmates: 28 November 09, 2020 6:48 am Ashley, Nicholas Ryan Charge(s) Burglary-3rd Deg-Steal/Commit Felony or Gross Misd Intake Date: October 15, 2020 Intake Time: 1:05 pm Ba, La Charge(s) Drugs - 5th Degree - Possess Schedule 1,2,3,4 - Not Small Amount Marijuana Domestic Abuse - Violate Order for Intake Date: November 01, 2020 Protection Intake Time: 12:21 am Boots-Ringoen, Dominik Nikko Charge(s) Criminal Vehicular Homicide - Operate Vehicle with Negligence - Under Influence Alcohol Intake Date: August 27, 2020 Traffic - DWI - Operate Motor Vehicle - Alcohol Concentration 0.08 Within 2 Intake Time: 10:31 pm Hours Disorderly Conduct-Brawling or Fighting Criminal Vehicular Operation - Great Bodily Harm - Gross Negligence Traffic-Drivers License-Driving After Revocation Traffic - Underage drinking and driving; Crime described Burt, Adam Robert Charge(s) Assault-3rd Degree-Substantial Bodily Harm Traffic - DWI - First-Degree DWI;w/in Intake Date: February 14, 2020 10 yrs of 3 or more qualified prior impaired driving incidents Intake Time: 4:43 pm Page 1 of 6 Everet, Michael Leonard Charge(s) Harassment; Restraining Order - Violate and knows of temporary or restraining order Intake Date: November 06, 2020 Intake Time: 5:53 pm Fishel, Adam Dwayne Charge(s) Fleeing a Peace Officer in a Motor Vehicle Traffic - DWI - Operate Motor Vehicle - Intake Date: November 01, 2020 Alcohol Concentration 0.08 Within 2 Hours Intake Time: -

Monetary Forgery in the Digital Age: Will Physical-Digital Cash Be a Solution?1
Monetary Forgery in the Digital Age: Will Physical-Digital Cash Be a Solution?1 N ICOLAS CHRISTIN2, ALESSANDRO ACQUISTI3, BRYAN PARN04 AND ADRIAN PERRIG5 Abstract: Despite cryptographic breakthroughs in the area of digital cash and the rapid advance of information technology, physical cash remains the dominant currency: it is easy to use and its exchanges are largely independent of computing devices. However, physical cash is vulnerable to rising threats such as high quality, government-mandated forgeries. Can a hybrid of physical and digital cash protect more effectively against these threats? We discuss the rise of high-quality counterfeits and review technological solutions to thwart such threats. Specifically, we study mechanisms to combine physical cash with digital cash to remove their respective shortcomings and obtain their combined advantages. The mechanisms range from cryptographic signatures embedded in 2-D barcodes to online verification systems assisted by physical one-way functions. Notably, we compare these different proposals by looking at them through the prism of economics, and examining their cost and benefit trade-offs. 1 A preliminary, abbreviated version appeared in the Proceedings of the Twelfth International Conference on Financial Cryptography and Data Security (FC'oS). Cozumel, Mexico. January 2S-31, 200S. 2 Carnegie Mellon University, Information Networking Institute 3 Carnegie Mellon University, Heinz School of Public Policy and Management 4 Carnegie Mellon University, Department of Electrical and Computer Engineering & Microsoft Research 5 Carnegie Mellon University, Department of Electrical and Computer Engineering & Carnegie Mellon University, Department of Engineering and Public Policy 172 I/S: A JOURNAL OF LAW AND POLICY [Vol. 7:2 1. -

THE NATIONAL CENTER on INSTITUTIONS and ALTERNATI'ves 'I33'122nd ST., N.W., WASHINGTON, D.C
If you have issues viewing or accessing this file contact us at NCJRS.gov. I' I~~~~----~~~~~--'_'_'~------~--~--~ 7i'---..I> ', SENTENCED PRISONERS UNDER 18 YEARS OF AGE I IN ADULT CORRECTIONAL FAeILITIES: I A NATIONAL SURVEY I I I I I I I I I I I I I I N .. C..... A" .. tiE NAtIONAL CENTER ON INS1/'ITUTIONS AND ALYJi:iRNAl'IVr=S I 13:!J1 2~t1d ST., U.W./ WASHINCTON, Q.C. :ZOb31 I------------~........----..------------- I I H.C.I.A. THE NATIONAL CENTER ON INSTITUTIONS AND ALTERNATI'VES 'I33'122nd ST., N.W., WASHINGTON, D.C. :;:0037 202/659-4'156 I I Jerome G. Miller President I Advisory Board Members Severa Austin John McKnight Human Services Planner Center/or Urban Affairs Nortbwestern Universi~y I Madison, Wirconsin Loren Beckley UOydOtlUn Cbief, Juvenile Probnt;;", Cent.r for Cnrninol Justice San Mateo County, California Hart'ar;) Law Seboo! Lou Brin Milton Rector I Department ofSociology National Council on Crime University of Massacbus~tts and Delinquency Hackensack. New Jersey AI Bronstein National Prison Project David Rothenberg Fortune Society I Washington. D.C. New York, New York Larry Brown Action Agency David Rothman Washington, D.C Center for Social Policy Columbia University JohnM.Burns I Vice President Andrew Rutherford Westingbor;.re Corporation University 0/ Birmingham New York. New York Birmingham, England Ro~rt Drinan Peter Sandmann Representative, U.S. Congress Yout/) Law Cenler I Wasbington, D.C. Sa" Francisco, California Erving Goffman Peter Schrag Department 0/ Sociolligy Journalirl University 0/ Penn~ylvania Berkeley, California I Jay Haley Joseph Sorrentino Family Tberapy Institute Author, Juvenile Court Judge Cbevy Chase, Maryland Los Angeles. -

Recent Trends in Banknote Counterfeiting
Recent Trends in Banknote Counterfeiting Meika Ball[*] Photo: Reserve Bank of Australia Abstract Law enforcement intervention has shut down several large counterfeiting operations and led to a decline in counterfeiting rates over the past couple of years. At the same time, the increased availability of low-cost, high-quality printing technology has meant that the quality of counterfeits has improved. This article discusses trends in banknote counterfeiting in Australia and the impact of counterfeiting on different stakeholders. RESERVE BANK OF AUSTRALIA BULLETIN – MARCH 2019 1 Introduction As Australia’s banknote issuing authority, the Reserve Bank of Australia (the Bank) aims to prevent counterfeiting and maintain public confidence in the security of Australian banknotes. Counterfeiting is a crime and amounts to theft; since counterfeits are worthless, if an individual or business unknowingly accepts a counterfeit in exchange for something of value, they have been stolen from. More broadly, counterfeiting can erode public confidence in physical currency, which carries social and economic costs. Counterfeiting is prosecuted under the Crimes (Currency) Act 1981, which prescribes a number of offences. These include: • making, buying or selling counterfeit money • passing counterfeit money • possessing, importing or exporting counterfeit money • possessing, importing or exporting materials used to counterfeit money • sharing information about how to counterfeit money • wilfully damaging genuine money. Penalties for counterfeiting can be severe, including fines of up ot $75,000 and/or up to 14 years imprisonment for responsible individuals. The Bank assists in preventing counterfeiting by ensuring that Australia’s circulating banknotes are secure and of high quality, and by raising public awareness of banknote security features. -

Fire and Arson Scene Evidence: a Guide for Public Safety Personnel
U.S. Department of Justice Office of Justice Programs National Institute of Justice FireFire andand ArsonArson SceneScene Evidence:Evidence: A Guide for Public Safety Personnel Research Report U.S. Department of Justice Office of Justice Programs 810 Seventh Street N.W. Washington, DC 20531 Janet Reno Attorney General Daniel Marcus Acting Associate Attorney General Mary Lou Leary Acting Assistant Attorney General Julie E. Samuels Acting Director, National Institute of Justice Office of Justice Programs National Institute of Justice World Wide Web Site World Wide Web Site http://www.ojp.usdoj.gov http://www.ojp.usdoj.gov/nij Fire and Arson Scene Evidence: A Guide for Public Safety Personnel Written and Approved by the Technical Working Group on Fire/Arson Scene Investigation June 2000 NCJ 181584 Julie E. Samuels Acting Director David G. Boyd, Ph.D. Deputy Director Richard M. Rau, Ph.D. Project Monitor Opinions or points of view expressed in this document represent a consensus of the authors and do not necessarily reflect the official position of the U.S. Department of Justice. The National Institute of Justice is a component of the Office of Justice Programs, which also includes the Bureau of Justice Assistance, the Bureau of Justice Statistics, the Office of Juvenile Justice and Delinquency Prevention, and the Office for Victims of Crime. Message From the Attorney General ctions taken at the outset of an investigation at a fire and Aarson scene can play a pivotal role in the resolution of a case. Careful, thorough investigation is key to ensuring that potential physical evidence is not tainted or destroyed or potential witnesses overlooked. -

THE CRIME of ARSON Paul Sadler, Jr
Journal of Criminal Law and Criminology Volume 41 | Issue 3 Article 4 1950 The rC ime of Arson Paul Jr. Sadler Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation Paul Jr. Sadler, The rC ime of Arson, 41 J. Crim. L. & Criminology 290 (1950-1951) This Article is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. THE CRIME OF ARSON Paul Sadler, Jr. The following article is from a thesis the author prepared while pursuing his studies in Social Relations at Harvard University, from which he received his A.B. degree in June, -1950. Mr. Sadler is currently employed as a fire investigator adjuster for the General Adjustment Bureau, Inc., Boston, Mass.-EDrroR. I The crime of arson is an extraordinarily complex one by its definition alone. Its complexity makes many difficulties to the student. It also gives the perpetrator some advantages. To begin with, arson, like murder and most admirality crimes, exists in several degrees of indict- ment. These degrees are wholly dependent upon the type and use of the structure or property burned, degree of involvement of participants, and often the time of day in which the crime is committed.' But what degrees now exist are only created by modern statutory defini- tion over and above the original common law of England, which law, in comparison with 20th century statutes, seems very defective in scope. -

Should Commission of a Contemporaneous Arson, Burglary
Santa Clara Law Review Volume 49 | Number 1 Article 1 2009 Should Commission of a Contemporaneous Arson, Burglary, Kidnapping, Rape, or Robbery Be Sufficient to Make a Murderer Eligible for a Death Sentence? - An Empirical and Normative Analysis David McCord Follow this and additional works at: http://digitalcommons.law.scu.edu/lawreview Part of the Law Commons Recommended Citation David McCord, Should Commission of a Contemporaneous Arson, Burglary, Kidnapping, Rape, or Robbery Be Sufficient to Make a Murderer Eligible for a Death Sentence? - An Empirical and Normative Analysis, 49 Santa Clara L. Rev. 1 (2009). Available at: http://digitalcommons.law.scu.edu/lawreview/vol49/iss1/1 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara Law Review by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. SHOULD COMMISSION OF A CONTEMPORANEOUS ARSON, BURGLARY, KIDNAPPING, RAPE, OR ROBBERY BE SUFFICIENT TO MAKE A MURDERER ELIGIBLE FOR A DEATH SENTENCE?-AN EMPIRICAL AND NORMATIVE ANALYSIS By David McCord* INTRODUCTION Most death penalty jurisdictions make a murderer death- eligible if the murder was committed contemporaneously with one of five felonies: arson, burglary, kidnapping, rape, or robbery.1 In recent years, however, this traditional approach has been challenged by two blue-ribbon panels-the Illinois Commission on Capital Punishment and the Massachusetts Governor's Council on Capital Punishment-both of which advocated abolition of these five felonies as death-eligibility aggravators.2 The stakes in this debate are high because these five felonies-hereinafter "the contemporaneous felonies"-are frequent companions of murder: over sixty percent of death-eligible defendants contemporaneously commit at least one of them,3 and robbery alone qualifies more murderers for death-eligibility than any other * Professor of Law, Drake University Law School; J.D. -

Juvenile Firesetting: a Research Overview
U.S. Department of Justice Office of Justice Programs Office of Juvenile Justice and Delinquency Prevention J. Robert Flores, Administrator May 2005 Of fice of Justice Pr ograms • Par tnerships for Safer Communities • www.ojp.usdoj.gov Juvenile Firesetting: A Message From OJJDP A Research Overview In the hands of children, fire can be a destructive force. Each year, fires set by youth claim hundreds of lives and destroy millions of dollars’ worth of Charles T. Putnam and John T. Kirkpatrick property. By understanding how and why juve The consequences of juvenile firesetting following project goals. First, review the niles set fires, professionals and policy- can be tragic and costly. In a typical year, existing research literature on juvenile fire- makers can make informed decisions fires set by children and youth claim the setting behavior and offer a distillation of about how best to address this harmful lives of approximately 300 people and that literature. Second, convene a confer behavior. destroy more than $300 million worth of ence of researchers and fire, justice, and In 2002, the National Association of property. Children are the predominant clinical professionals to provide a forum State Fire Marshals (NASFM) began for constructive discussion about existing victims of these fires, accounting for 85 developing applied research initiatives of every 100 lives lost (U.S. Fire Adminis and future research. Third, deliver a report to help professionals curtail juvenile tration, 1997, 2004). to NASFM in April 2003 outlining pressing firesetting. The project included a areas of new research that would directly review of the research literature, a A thorough understanding of juvenile benefit the professional community. -

The Unnecessary Crime of Conspiracy
California Law Review VOL. 61 SEPTEMBER 1973 No. 5 The Unnecessary Crime of Conspiracy Phillip E. Johnson* The literature on the subject of criminal conspiracy reflects a sort of rough consensus. Conspiracy, it is generally said, is a necessary doctrine in some respects, but also one that is overbroad and invites abuse. Conspiracy has been thought to be necessary for one or both of two reasons. First, it is said that a separate offense of conspiracy is useful to supplement the generally restrictive law of attempts. Plot- ters who are arrested before they can carry out their dangerous schemes may be convicted of conspiracy even though they did not go far enough towards completion of their criminal plan to be guilty of attempt.' Second, conspiracy is said to be a vital legal weapon in the prosecu- tion of "organized crime," however defined.' As Mr. Justice Jackson put it, "the basic conspiracy principle has some place in modem crimi- nal law, because to unite, back of a criniinal purpose, the strength, op- Professor of Law, University of California, Berkeley. A.B., Harvard Uni- versity, 1961; J.D., University of Chicago, 1965. 1. The most cogent statement of this point is in Note, 14 U. OF TORONTO FACULTY OF LAW REv. 56, 61-62 (1956): "Since we are fettered by an unrealistic law of criminal attempts, overbalanced in favour of external acts, awaiting the lit match or the cocked and aimed pistol, the law of criminal conspiracy has been em- ployed to fill the gap." See also MODEL PENAL CODE § 5.03, Comment at 96-97 (Tent. -

Report on the Legal Protection of Banknotes in the European Union Member States
ECB EZB EKT BCE EKP REPORT ON THE LEGAL PROTECTION OF BANKNOTES IN THE EUROPEAN UNION MEMBER STATES November 1999 REPORT ON THE LEGAL PROTECTION OF BANKNOTES IN THE EUROPEAN UNION MEMBER STATES November 1999 © European Central Bank, 1999 Address Kaiserstrasse 29 D-60311 Frankfurt am Main Germany Postal address Postfach 16 03 19 D-60066 Frankfurt am Main Germany Telephone +49 69 1344 0 Internet http://www.ecb.int Fax +49 69 1344 6000 Telex 411 144 ecb d All rights reserved. Reproduction for educational and non-commercial purposes is permitted provided that the source is acknowledged. The views expressed in this paper are those of the author and do not necessarily reflect those of the European Central Bank. ISBN 92-9181-051-7 2 ECB Report on the legal protection of banknotes • November 1999 Contents EXECUTIVE SUMMARY 5 I. LEGAL PROTECTION OF EURO BANKNOTES 7 A. THE CRIMINAL APPROACH: COUNTERFEITING 7 1. The legal situation in the Member States 7 2. The desired legal situation 9 3. The risk of increased counterfeit activity 11 4. The possibilities of prevention – co-operation and co-ordination 12 5. The harmonisation of sanctions 18 6. The detention of counterfeit banknotes 18 B. THE CIVIL APPROACH: COPYRIGHT PROTECTION (COMPLEMENTARY TOOLS AND SETTING CRITERIA FOR LEGAL REPRODUCTIONS) 20 1. Copyright protection for euro banknotes 20 2. The use of the © sign on euro banknotes 22 3. The enforcement of copyright 23 4. The reproduction of euro banknotes 24 C. THE MATERIAL APPROACH: ANTI-COPYING DEVICES FOR REPRODUCTION EQUIPMENT 26 II. LEGAL ASPECTS OF FIDUCIARY CIRCULATION 28 A. -

Police Perjury: a Factorial Survey
The author(s) shown below used Federal funds provided by the U.S. Department of Justice and prepared the following final report: Document Title: Police Perjury: A Factorial Survey Author(s): Michael Oliver Foley Document No.: 181241 Date Received: 04/14/2000 Award Number: 98-IJ-CX-0032 This report has not been published by the U.S. Department of Justice. To provide better customer service, NCJRS has made this Federally- funded grant final report available electronically in addition to traditional paper copies. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. Department of Justice. FINAL-FINAL TO NCJRS Police Perjury: A Factorial Survey h4ichael Oliver Foley A dissertation submitted to the Graduate Faculty in Criminal Justice in partial fulfillment of the requirements for the degree of Doctor of Philosophy. The City University of New York. 2000 This document is a research report submitted to the U.S. Department of Justice. This report has not been published by the Department. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. Department of Justice. I... I... , ii 02000 Michael Oliver Foley All Rights Reserved This document is a research report submitted to the U.S. Department of Justice. This report has not been published by the Department. Opinions or points of view expressed are those of the author(s) and do not necessarily reflect the official position or policies of the U.S. -

Incest Statutes
Statutory Compilation Regarding Incest Statutes March 2013 Scope This document is a comprehensive compilation of incest statutes from U.S. state, territorial, and the federal jurisdictions. It is up-to-date as of March 2013. For further assistance, consult the National District Attorneys Association’s National Center for Prosecution of Child Abuse at 703.549.9222, or via the free online prosecution assistance service http://www.ndaa.org/ta_form.php. *The statutes in this compilation are current as of March 2013. Please be advised that these statutes are subject to change in forthcoming legislation and Shepardizing is recommended. 1 National Center for Prosecution of Child Abuse National District Attorneys Association Table of Contents ALABAMA .................................................................................................................................................................. 8 ALA. CODE § 13A-13-3 (2013). INCEST .................................................................................................................... 8 ALA. CODE § 30-1-3 (2013). LEGITIMACY OF ISSUE OF INCESTUOUS MARRIAGES ...................................................... 8 ALASKA ...................................................................................................................................................................... 8 ALASKA STAT. § 11.41.450 (2013). INCEST .............................................................................................................. 8 ALASKA R. EVID. RULE 505 (2013)