Net Search (See[ R] Net Search)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -
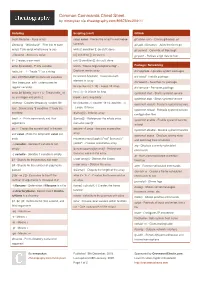
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Click to Add Title Click to Add Subtitle (If Applicable) Click to Add
Identifying Command, Control and Communication Networks from Interactions and Activities Observations Georgiy Levchuk, Ph.D., Aptima Inc. Yuri Levchuk, Ph.D., Aptima Inc. CCRTS, 2006 © 2006, Aptima, Inc. 1 Agenda Challenges of tactical operations Proposed integrated solution concept Focus of this research: adversary organization identification Technical approach Results and conclusions © 2006, Aptima, Inc. 2 3 Major Challenges of Tactical Operations Conflicts Trends Technology/Information Trends Adversary’s Trends 70 4500 Past 60 4000 Large-size forces of well-known 3500 50 organizational forms 3000 40 Current 2500 Main telephone lines 30 Small- to moderate-size militia 2000 Mobile cellular forces taking many less #, Millions subscribers 20 1500 Internet users organized forms # of US forces ops forces US # of 10 1000 Future: Adaptive Enemy 0 500 Almost unrestricted ability to 1946-1969 1970-1990 1991-2006 0 connect and coordinate 1992 1998 2004 2010 (est) Years Year Can change size and adapt Past Past structure Slow-time conflict Mainly hard-line communications Numbered engagements Current Internet traffic doubles/year Current 630,000 phone lines installed/week Tactical Planning Issues Asymmetric threats and 50,000 new wireless users/day changing missions 650M SIGINT cables generated High manpower needs (~0.001% to products) Takes long time Future: Increased # of Ops 34M voice mail messages/day High info gaps, complexity, Fast-paced engagements 7.7M e-mails sent/min overload Larger number of and Future: Data Explosion Biases of human decisions higher time criticality Data impossible to analyze manually © 2006, Aptima, Inc. 3 Solution: A System to Aid Battlefield CMDR to Design Effective Counteractions against Tactical Adversary Semi-automated System CMDR & planning staff Battlefield Execute attacks against enemy Gather intel INPUT PRODUCT •comm. -

(PI-Net): Facial Image Obfuscation with Manipulable Semantics
Perceptual Indistinguishability-Net (PI-Net): Facial Image Obfuscation with Manipulable Semantics Jia-Wei Chen1,3 Li-Ju Chen3 Chia-Mu Yu2 Chun-Shien Lu1,3 1Institute of Information Science, Academia Sinica 2National Yang Ming Chiao Tung University 3Research Center for Information Technology Innovation, Academia Sinica Abstract Deepfakes [45], if used to replace sensitive semantics, can also mitigate privacy risks for identity disclosure [3, 15]. With the growing use of camera devices, the industry However, all of the above methods share a common has many image datasets that provide more opportunities weakness of syntactic anonymity, or say, lack of formal for collaboration between the machine learning commu- privacy guarantee. Recent studies report that obfuscated nity and industry. However, the sensitive information in faces can be re-identified through machine learning tech- the datasets discourages data owners from releasing these niques [33, 19, 35]. Even worse, the above methods are datasets. Despite recent research devoted to removing sen- not guaranteed to reach the analytical conclusions consis- sitive information from images, they provide neither mean- tent with the one derived from original images, after manip- ingful privacy-utility trade-off nor provable privacy guar- ulating semantics. To overcome the above two weaknesses, antees. In this study, with the consideration of the percep- one might resort to differential privacy (DP) [9], a rigorous tual similarity, we propose perceptual indistinguishability privacy notion with utility preservation. In particular, DP- (PI) as a formal privacy notion particularly for images. We GANs [1, 6, 23, 46] shows a promising solution for both also propose PI-Net, a privacy-preserving mechanism that the provable privacy and perceptual similarity of synthetic achieves image obfuscation with PI guarantee. -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre .............................................................................................................................. -

January 2019 Edition
Tunkhannock Area High School Tunkhannock, Pennsylvania The Prowler January 2019 Volume XIV, Issue XLVII Local Subst itute Teacher in Trouble Former TAHS substitute teacher, Zachary Migliori, faces multiple charges. By MADISON NESTOR Former substitute teacher Wyoming County Chief out, that she did not report it originally set for December at Tunkhannock Area High Detective David Ide, started to anyone. 18 was moved to March 18. School, Zachary Migliori, on October 11 when the When Detective Ide asked If he is convicted, he will was charged with three felony parents of a 15-year old Migliori if he knew that one face community service, and counts of distributing obscene student found pornographic of the girls he sent explicit mandatory counseling. material, three misdemeanor images and sexual texts messages to was a 15-year- Tunkhannock Area High counts of open lewdness, and on their daughter’s phone. old, he explained that he School took action right away three misdemeanor counts of The parent then contacted thought she was 18-years-old to ensure students’ safety, unlawful contact with minors. Detective Ide, who found because she hung out with and offers counseling to any This comes after the results after investigating that the many seniors. After being students who need it. of an investigation suspecting substitute teacher was using informed of one victim being Sources:WNEP, lewd contact with students a Snapchat account with the 15-years-old, Migliori said he WCExaminer, CitizensVoice proved to be true. According name ‘Zach Miggs.’ was disgusted with himself. to court documents, Migliori Two 17-year old females Judge Plummer set used Facebook Messenger also came forward, one of Migliori’s bail at $50,000. -

S.Ha.R.K. Installation Howto Tools Knoppix Live CD Linux Fdisk HD
S.Ha.R.K. Installation Tools HowTo • Linux fdisk utility • A copy of Linux installation CD • A copy of Windows® installation CD Tullio Facchinetti University of Pavia - Italy • Some FreeDOS utilities • A copy of S.Ha.R.K. S.Ha.R.K. Workshop S.Ha.R.K. Workshop Knoppix live CD Linux fdisk Command action a toggle a bootable flag Download ISO from b edit bsd disklabel c toggle the dos compatibility flag d delete a partition http://www.knoppix.org l list known partition types m print this menu n add a new partition o create a new empty DOS partition table p print the partition table q quit without saving changes • boot from CD s create a new empty Sun disklabel t change a partition's system id • open a command shell u change display/entry units v verify the partition table • type “su” (become root ), password is empty w write table to disk and exit x extra functionality (experts only) • start fdisk (ex. fdisk /dev/hda ) Command (m for help): S.Ha.R.K. Workshop S.Ha.R.K. Workshop HD partitioning HD partitioning 1st FreeDOS FAT32 FreeDOS must be installed Primary 2nd Windows® FAT32 into the first partition of your HD or it may not boot 3rd Linux / extX Data 1 FAT32 format data partitions as ... Extended FAT32, so that you can share Data n FAT32 your data between Linux, last Linux swap swap Windows® and FreeDOS S.Ha.R.K. Workshop S.Ha.R.K. Workshop 1 HD partitioning Windows ® installation FAT32 Windows® partition type Install Windows®.. -

NETSTAT Command
NETSTAT Command | NETSTAT Command | Use the NETSTAT command to display network status of the local host. | | ┌┐────────────── | 55──NETSTAT─────6─┤ Option ├─┴──┬────────────────────────────────── ┬ ─ ─ ─ ────────────────────────────────────────5% | │┌┐───────────────────── │ | └─(──SELect───6─┤ Select_String ├─┴ ─ ┘ | Option: | ┌┐─COnn────── (1, 2) ──────────────── | ├──┼─────────────────────────── ┼ ─ ──────────────────────────────────────────────────────────────────────────────┤ | ├─ALL───(2)──────────────────── ┤ | ├─ALLConn─────(1, 2) ────────────── ┤ | ├─ARp ipaddress───────────── ┤ | ├─CLients─────────────────── ┤ | ├─DEvlinks────────────────── ┤ | ├─Gate───(3)─────────────────── ┤ | ├─┬─Help─ ┬─ ───────────────── ┤ | │└┘─?──── │ | ├─HOme────────────────────── ┤ | │┌┐─2ð────── │ | ├─Interval─────(1, 2) ─┼───────── ┼─ ┤ | │└┘─seconds─ │ | ├─LEVel───────────────────── ┤ | ├─POOLsize────────────────── ┤ | ├─SOCKets─────────────────── ┤ | ├─TCp serverid───(1) ─────────── ┤ | ├─TELnet───(4)───────────────── ┤ | ├─Up──────────────────────── ┤ | └┘─┤ Command ├───(5)──────────── | Command: | ├──┬─CP cp_command───(6) ─ ┬ ────────────────────────────────────────────────────────────────────────────────────────┤ | ├─DELarp ipaddress─ ┤ | ├─DRop conn_num──── ┤ | └─RESETPool──────── ┘ | Select_String: | ├─ ─┬─ipaddress────(3) ┬ ─ ───────────────────────────────────────────────────────────────────────────────────────────┤ | ├─ldev_num─────(4) ┤ | └─userid────(2) ─── ┘ | Notes: | 1 Only ALLCON, CONN and TCP are valid with INTERVAL. | 2 The userid -

Net Search — Search the Internet for Installable Packages
Title stata.com net search — Search the Internet for installable packages Description Quick start Syntax Options Remarks and examples Also see Description net search searches the Internet for community-contributed additions to Stata, including, but not limited to, community-contributed additions published in the Stata Journal (SJ) and in the Stata Technical Bulletin (STB). net search lists the available additions that contain the specified keywords. The community-contributed materials found are available for immediate download by using the net command or by clicking on the link. In addition to typing net search, you may select Help > Search... and choose Search net resources. This is the recommended way to search for community-contributed additions to Stata. Quick start Search community-contributed commands for all terms word1, word2, and word3 net search word1 word2 word3 As above, but search for any term net search word1 word2 word3, or Search Internet sources other than the Stata Journal and the Stata Technical Bulletin net search word1 word2 word3, nosj 1 2 net search — Search the Internet for installable packages Syntax net search word word ::: , options options Description or list packages that contain any of the keywords; default is all nosj search non-SJ and non-STB sources tocpkg search both tables of contents and packages; the default toc search tables of contents only pkg search packages only everywhere search packages for match filenames search filenames associated with package for match errnone make return code 111 instead of 0 when no matches found Options or is relevant only when multiple keywords are specified. By default, net search lists only packages that include all the keywords. -

Unix (And Linux)
AWK....................................................................................................................................4 BC .....................................................................................................................................11 CHGRP .............................................................................................................................16 CHMOD.............................................................................................................................19 CHOWN ............................................................................................................................26 CP .....................................................................................................................................29 CRON................................................................................................................................34 CSH...................................................................................................................................36 CUT...................................................................................................................................71 DATE ................................................................................................................................75 DF .....................................................................................................................................79 DIFF ..................................................................................................................................84 -

Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment
Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment Lecture notes: 1. Scope of the course Prerequisite for ENEE 150 (see the last page for more details), very basic skills in programming and UNIX. a. Principles of programming and software development. b. C will be used as the programming language to illustrate the concepts. c. Basic skills in UNIX operating systems. 2. How to program (or develop software package in the future) a. Document everything you do in each of the following steps. b. Understand the project/problem requirements c. Develop algorithm (the way or method to solve the problem) d. Plan for the implementation of your algorithm (data structure, etc.) e. Write the programming (C, C++, Java, Matlab, etc.) f. Compile the program (gcc or cc in GLUE UNIX for C codes. Compiler is the interpreter that translates the program written in the so-called high level programming languages like C by human, who call themselves programmers, and understandable by human to the low level language that the computer understands.) g. Execute, test, and debug your program on sample data. h. Go back to step d. (modify your code) if necessary (programming or syntax bugs). i. Go back to step c. or step b. if there are serious problems (algorithm or logic bugs). j. Confirm that all the project requirements are met. (output format, etc.) 3. What is UNIX? a. UNIX is an operating system, like windows, which is a complex set of computer codes that manages the activities and resources of the computer. It is very popular in universities and colleges. -

ANSWERS ΤΟ EVEN-Numbered
8 Answers to Even-numbered Exercises 2.1. WhatExplain the following unexpected are result: two ways you can execute a shell script when you do not have execute permission for the file containing the script? Can you execute a shell script if you do not have read permission for the file containing the script? You can give the name of the file containing the script as an argument to the shell (for example, bash scriptfile or tcsh scriptfile, where scriptfile is the name of the file containing the script). Under bash you can give the following command: $ . scriptfile Under both bash and tcsh you can use this command: $ source scriptfile Because the shell must read the commands from the file containing a shell script before it can execute the commands, you must have read permission for the file to execute a shell script. 4.3. AssumeWhat is the purpose ble? you have made the following assignment: $ person=zach Give the output of each of the following commands. a. echo $person zach b. echo '$person' $person c. echo "$person" zach 1 2 6.5. Assumengs. the /home/zach/grants/biblios and /home/zach/biblios directories exist. Specify Zach’s working directory after he executes each sequence of commands. Explain what happens in each case. a. $ pwd /home/zach/grants $ CDPATH=$(pwd) $ cd $ cd biblios After executing the preceding commands, Zach’s working directory is /home/zach/grants/biblios. When CDPATH is set and the working directory is not specified in CDPATH, cd searches the working directory only after it searches the directories specified by CDPATH.