Hakin9 Extra Magazine We Prepared All Rights to Trade Marks Presented in the an Interview with Dmitry L
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Maxtor External Hdd Software
Maxtor external hdd software This software contains the MacOS 9 driver for the Maxtor OneTouch external hard This software contains Retrospect Express HD for use with original Maxtor. Software & App Support Windows AutoRun icons for the Maxtor Basics Portable external drive. Identifying and troubleshooting hard drive noise issues. Get information about Seagate Software & Apps. Samsung Drive Manager · Sdrive · Media Sync software for Windows · Media Sync software for Mac OS. Windows Autorun icons for the Maxtor Basics Portable external drive. Serial Specific Identifying and troubleshooting hard drive noise issues · How to use Disk. Maxtor Hard Disk Drive Free Driver Download | Free Download Seagate Drive Drivers Download Removable Drive · Maxtor USB Drivers Download USB. Editors' Note: Clicking on the Download Now (Visit Site) button above will open a connection to a third-party site. cannot completely ensure the. Seagate Maxtor OneTouch III USB drivers are tiny programs that enable your External Hard Drive hardware to communicate with your operating system. Download the latest Seagate External Hard Drive device drivers (Official and Certified). Seagate External Hard Drive drivers updated daily. Download ad Size: MB. This hard disk recovery tool restores data from corrupted, formatted and inaccessible Note - If you want to get back files from Maxtor external hard drive, then. If your external hard drive is not working properly nor recognized in Windows 10 but was fine in the previous OS, then it's most likely because. Free data recovery software for Maxtor external hard disk drive data recovery after quick format. The Maxtor Manager software enables advanced features, such as backing up and Power on your Maxtor external hard drive and connect it to your computer. -

Proxy Notice
NOTICE OF ANNUAL MEETING OF STOCKHOLDERS OF BROOKS AUTOMATION, INC. TO BE HELD ON JANUARY 18, 2011 The 2011 Annual Meeting of Stockholders of Brooks Automation, Inc. (“Brooks” or the “Company”) will be held on January 18, 2011 at 10:00 a.m., local time, at 15 Elizabeth Drive, Chelmsford, Massachusetts 01824 for the following purposes: 1. To elect nine directors to serve for the ensuing year and until their successors are duly elected. 2. To ratify the selection of PricewaterhouseCoopers LLP as our independent registered accounting firm for the 2011 fiscal year. 3. To transact any other matters which may properly come before the Annual Meeting or any adjourned session thereof. The Board of Directors has fixed November 30, 2010 as the record date for determining the stockholders entitled to notice of, and to vote at, the Annual Meeting. All stockholders are cordially invited to attend the Annual Meeting. To ensure your representation at the Annual Meeting we urge you to complete a proxy telephonically, electronically or by mail, if you requested a proxy statement be mailed to you as described in the proxy statement. This year we will again take advantage of the Securities and Exchange Commission rule allowing companies to furnish proxy materials to their stockholders over the Internet. This so-called e-proxy process is becoming familiar to many investors and it can serve to expedite stockholders’ receipt of proxy materials, lower costs and diminish the environmental impact of our annual meeting. Stockholders who choose to receive e-proxy materials have been sent a notice with instructions as to how to access our proxy statement and annual report, as well as how to vote. -

Seagate Technology Plc
SEAGATE TECHNOLOGY PLC FORM 10-K (Annual Report) Filed 08/03/18 for the Period Ending 06/29/18 Telephone (353) (1) 234-3136 CIK 0001137789 Symbol STX SIC Code 3572 - Computer Storage Devices Industry Computer Hardware Sector Technology Fiscal Year 06/30 http://www.edgar-online.com © Copyright 2018, EDGAR Online, a division of Donnelley Financial Solutions. All Rights Reserved. Distribution and use of this document restricted under EDGAR Online, a division of Donnelley Financial Solutions, Terms of Use. Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended June 29, 2018 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File No. 001-31560 SEAGATE TECHNOLOGY PUBLIC LIMITED COMPANY (Exact name of registrant as specified in its charter) Ireland 98-0648577 (State or other jurisdiction of incorporation or organization) (I.R.S. Employer Identification Number) 38/39 Fitzwilliam Square Dublin 2, Ireland (Address of principal executive offices) Registrant’s telephone number, including area code: (353) (1) 234-3136 Securities registered pursuant to Section 12 (b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Ordinary Shares, par value $0.00001 per share The NASDAQ Global Select Market Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. -

Production Networks in Asia: a Case Study from the Hard Disk Drive
ADBI Working Paper Series Production Networks in Asia: A Case Study from the Hard Disk Drive Industry Daisuke Hiratsuka No. 301 July 2011 Asian Development Bank Institute Daisuke Hiratsuka is director-general of the Institute of Developing Economies, Japan External Trade Organization. This paper is the revised version of the paper presented at the ADBI-WIIW Conference, "Comparative Analysis of Production Networks in Asia and Europe", held in Vienna on 15–16 July 2010. The author would like to thank Dr. Nippon Poapongsakorn, president of the Thailand Development Research Institute, for his helpful comments on the previous version. The views expressed in this paper are the views of the authors and do not necessarily reflect the views or policies of ADBI, the Asian Development Bank (ADB), its Board of Directors, or the governments they represent. ADBI does not guarantee the accuracy of the data included in this paper and accepts no responsibility for any consequences of their use. Terminology used may not necessarily be consistent with ADB official terms. The Working Paper series is a continuation of the formerly named Discussion Paper series; the numbering of the papers continued without interruption or change. ADBI’s working papers reflect initial ideas on a topic and are posted online for discussion. ADBI encourages readers to post their comments on the main page for each working paper (given in the citation below). Some working papers may develop into other forms of publication. Suggested citation: Hiratsuka, D. 2011. Production Networks in Asia: A Case Study from the Hard Disk Drive Industry. ADBI Working Paper 301. -
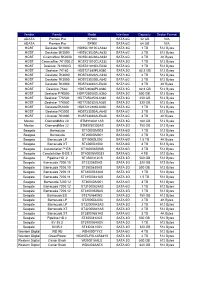
Vendor Family Model Interface Capacity Sector Format
Vendor Family Model Interface Capacity Sector Format ADATA Premier Pro SP600 SATA 6G 32 GB N/A ADATA Premier Pro SP900 SATA 6G 64 GB N/A HGST Deskstar 5K1000 HDS5C1010CLA382 SATA 3G 1 TB 512 Bytes HGST Deskstar 5K3000 HDS5C3020ALA632 SATA 6G 2 TB 512 Bytes HGST CinemaStar 5K2000 HCS5C2020ALA632 SATA 6G 2 TB 4K Bytes HGST CinemaStar 7K1000.C HCS721010CLA332 SATA 3G 1 TB 512 Bytes HGST Deskstar 7k1000.D HDS721010DLE630 SATA 6G 1 TB 512 Bytes HGST Deskstar 7K160 HDS721680PLA380 SATA 3G 82.3 GB 512 Bytes HGST Deskstar 7K2000 HDS722020ALA330 SATA 3G 2 TB 512 Bytes HGST Deskstar 7K3000 HDS723020BLA642 SATA 6G 2 TB 512 Bytes HGST Deskstar 7K4000 HDS724040ALE640 SATA 6G 4 TB 4K Bytes HGST Deskstar 7K80 HDS728080PLA380 SATA 3G 82.3 GB 512 Bytes HGST Deskstar P7K500 HDP725050GLA360 SATA 3G 500 GB 512 Bytes HGST Deskstar T7K500 HDT725025VLA380 SATA 3G 250 GB 512 Bytes HGST Deskstar T7K500 HDT725032VLA360 SATA 3G 320 GB 512 Bytes HGST Deskstar7K1000 HDS721010KLA330 SATA 3G 1 TB 512 Bytes HGST Deskstar7K3000 HDS723030ALA640 SATA 6G 3 TB 512 Bytes HGST Ultrastar 7K4000 HUS724040ALE640 SATA 6G 4 TB 4K Bytes Maxtor DiamondMax 20 STM3160811AS SATA 3G 160 GB 512 Bytes Maxtor DiamondMax 22 STM3750330AS SATA 3G 750 GB 512 Bytes Seagate Barracuda ST1000DM003 SATA 6G 1 TB 512 Bytes Seagate Barracuda ST2000DM001 SATA 6G 2 TB 512 Bytes Seagate Barracuda LP ST1500DL003 SATA 6G 1.5 TB 4K Bytes Seagate Barracuda XT ST4000DX000 SATA 6G 4 TB 512 Bytes Seagate Constellation™ ES ST33000650NS SATA 6G 3 TB 512 Bytes Seagate Constellation ® ES.3 ST4000NM0033 SATA 6G 4 -

Masstor Systems Corporation
Report to the Computer History Museum on the Information Technology Corporate Histories Project Masstor Systems Corporation Masstor Systems Corporation Company Details Name: Masstor Systems Corporation Sector: Data Storage Sector Description Description goes here Facilitators Bob Howie Email - Statistics Contributors (1), Events (0), Stories (0), Documents (1), References (0), Discussions (0 threads, 0 posts) Entered By: Luanne Johnson August 17, 2006 Contributors Contributor Erik Salbu Date Joined September 1975 Job Description TBA Date Entered August 18, 2006 Timeline There are no events for this company in the collection Stories There are no stories for this company in the collection Documents Title: Masstor History Overview Author: Bob Howie Created: December 28, 2006 Publisher: Donated By: Bob Howie Filename: doc-459536e276ee0.doc (Size: 42 KB) Pages: Cataloguer: Copyright: Description: Page 1035 Report to the Computer History Museum on the Information Technology Corporate Histories Project Masstor Systems Corporation Brief History of Masstor. Needs: Product Descriptions IPO Information Customer Information and more ... -------------------------------------------------------------------------------- Entered By: Bob Howie December 29, 2006 References There are no references for this company in the collection Discussions There are no discussions for this company in the collection Page 1036 Report to the Computer History Museum on the Information Technology Corporate Histories Project Maxtor Maxtor Company Details Name: Maxtor Sector: -

Editorial Style Guide February 2018
Editorial Style Guide February 2018 Creative Services Revision 1.2 [email protected] Table of Contents Editorial Style Guide Notes for Sub-Brands (such as LaCie) External References Definitive Guides Legal Guidelines for Writing Legal Review Process Disclaimers Disclaimer Elements Typical Disclaimer Trademarks Trademark Use With Company Name Trademark Use With Product or Feature Names Third-Party Trademarks Corporate Current Products Legacy Products Current Features/Technologies Legacy Features/Technologies Permissions, Disclosures, and Citations Designer Credits Warranty Use of Language Compound Words 1 Numbers Units of Measure Rounding Areal Density Capacity Dimensions Electricity Performance/Speed Power Dissipation Shock Sound Temperature Time Vibration Lists Capitalization Punctuation Apostrophes Commas Semicolons Colons Dashes Parentheses Ellipses Multiplication Sign Quotation Marks Italics 2 URLs Acronyms and Abbreviations Acronyms to Avoid Acronyms You Do Not Have to Spell Out Word List Sub-Brand-Specific Exceptions LaCie 3 Editorial Style Guide This style guide establishes writing style conventions for Seagate and sub-brand writers and editors in order to help them achieve stylistic consistency across all platforms. This document is the sole point of reference for all public-facing copy published by Seagate and Seagate sub-brands. Send questions, comments, and suggestions to: [email protected] Notes for Sub-Brands (such as LaCie) Per company strategy, some sub-brands may be expected to maintain their unique voice, despite being a holding of Seagate. However, in the interest of centralizing copy standards across all of Seagate and its sub-brands, we expect all sub-brands to use this document as the single point of reference for copy standards. -

Vista Procedure
PART C.Hardware Periphery Compatibility 1.Power Supplies M/B Power Supply Model AcBel IP-500 HB9024 CP-850 CP-1000 EA-500D Antec EA-650-GREEN EA-750 HCG-900 AeroCool STRIKE-X-600 Bubalus PE600WJD Century Star Big Pinwheel 320 RS-A00-SPPA-D3 RS-C00-80GA-D3 CoolerMaster RS-D00-SPHA-D3 RS-460-ASAA-D3 RS-700-PCAA-E3 COMMANDER IRP-COM750 CMPSU-850AX CORSAIR CMPSU-850TXM DELUX DLP-650PG EMG600AWT EnerMAX EPM850EWT Enertronix EN-300(ATX-300C) AX-260HHC FSP AX-310HHN GoldenField ATX-S395(Silence) ATX-350P4 (PLUS) BTX-400SD GreatWall BTX-500GT BTX-600SE HAMER MIT750 HuntKey HK400-55AP 2.3+ Huntkey HuntKey Win7 HuntKey HK1000-11PEP-X7 900 J POWER SP-1000PS-IM LEPA G1600-MA OCZ FTY750 ROSEWILL RBR1000-M SS-760KM Seasonic SS-1000XP SS-1250XM ST-800PGD Seventeam ST-500PFL Segotep 400P(SG-400PYJ) Sharkoon SHA-R600M Silverstone SST-ST40F-ES H97-PLUS PAGE 1 Model Silverstone SST-ST60F-P SF-550P14PE Super Flower SF-350P14XE TP-650AH3CCG (Toughpower Grand 650W) TP-1050AH3CSG (Toughpower Grand 1050W) Thermaltake TP-1200AH3CSG (Toughpower Grand 1200W) Toughpower-TP-775AH3CC 2.Hard Drives 2.1. HDD Devices Type Model HDS723030ALA640 HDS723020BLA642 HITACHI HDS721010DLE630 HDS721050DLE630 HDS724040ALE640 ST2000DL003 ST500DM002 ST1000DM003 ST3000DM001 Seagate ST2000DM001 ST1000LM014 ST4000DM000 ST1000DX001 SATA 6G ST2000NM0033 DT01ACA100 TOSHIBA DT01ACA050 WD1002FAEX WD10EADX WD5000AAKX WD2002FAEX WD20EARX WD WD30EZRX WD10EALX WD10EZEX WD20EFRX WD30EFRX WD4001FAEX HDT721010SLA360 HITACHI HDS721010CLA332 HD753LJ HD502IJ SATA 3G SAMSUNG HD103SJ HD203WI Seagate ST31000528AS WD WD6401AALS H97-PLUS PAGE 2 Type Model SATA 3G WD WD22EADS Seagate ST500NM0001 SAS 6G HITACHI HUS724020ALS640 WD WD3001BKHG 2.2. -

Inside Inside DISKCON
INSIGHT to data storage — trends, technologies, products Summer 2002 Published by IDEMA®—the trade association for the data storage industry DISKCON USA special preview issue Full technical conference information and registration card inside! insideinsidewhat’s 66 DISKCON USA Preview The Future of Optical Discs: 1818 Choosing a Winner 2222 Secure Erase of Disk Drive Data Critical Dimension Metrology for Next 2626 Generation Thin-Film Recording Head Processes ULTRASONICS Eliminate Damage To Sensitive Parts... Use Ceramically Enhanced Ultrasonics to Achieve .1 Submicron Cleanliness CREST ULTRASONICS SCOTCH ROAD • PO BOX 7266 • TRENTON, NJ 08628 • PHONE: 609-883-4000 • FAX: 609-883-6452 www.crest-ultrasonics.com contents Mark Geenen—President Storage, The Ultimate Technology—the theme for the DISKCON USA 2002 Trade Show and Technical Conference. IDEMA is 6 pleased to welcome you to DISKCON, the world’s only series of DISKCON USA Preview trade shows that is tailored to the HDD industry. Please join us for what promises to be a compelling week of exhibits, new products, technical sessions, standards meetings, and networking. 18 Here are some of the highlights of what you can enjoy The Future of Optical September 16-19 in San Jose: Discs: Choosing a Winner DISKCON trade show: The DISKCON USA trade show is the largest assemblage of exhibitors with products and technologies designed specifically for the HDD industry. Key technologies and 22 equipment that foster our industry’s meteoric improvement in areal density and Secure Erase of Disk Drive Data performance are first seen at DISKCON. Attending the show guarantees that you will be completely up to speed on the industry’s infrastructure. -

SEAGATE TECHNOLOGY PUBLIC LIMITED COMPANY (Exact Name of Registrant As Specified in Its Charter)
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended June 28, 2019 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File No. 001-31560 SEAGATE TECHNOLOGY PUBLIC LIMITED COMPANY (Exact name of registrant as specified in its charter) Ireland 98-0648577 (State or other jurisdiction of incorporation or organization) (I.R.S. Employer Identification Number) 38/39 Fitzwilliam Square Dublin 2, Ireland (Address of principal executive offices) D02 NX53 (Zip Code) Registrant’s telephone number, including area code: (353) (1) 234-3136 Securities registered pursuant to Section 12 (b) of the Act: Title of Each Class Trading Symbol(s) Name of Each Exchange on Which Registered Ordinary Shares, par value $0.00001 per share STX The NASDAQ Global Select Market Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. YES ☒ NO ☐ Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. YES ☐ NO ☒ Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

Fasttrak TX2300/TX4300 Hard Disk Drive Compatibilitylist
FastTrak TX2300/TX4300 Hard Disk Drive CompatibilityList Max FW Spindle NCQ / Drive Vendor Drive Family Model Capacity Transfer Version Speed TCQ Mode Western Digital Caviar SE WD2500JD 08.02D08 250.0GB 7200 RPM SATA150 Western Digital Caviar SE WD1600JD 02.05D02 160.0GB 7200 RPM SATA150 Western Digital Caviar WD1200JD 02.05D02 120.0GB 7200 RPM SATA150 Western Digital Raptor WD 740GD 31.08F31 74.8GB 10000 RPM TCQ SATA150 Western Digital Raptor WD 360GD 35.06K35 36.0GB 10000 RPM SATA150 Hitachi Deskstar 7K400 HDS724040KLSA80 KFA0A32A 400.0GB 7200 RPM SATA150 Hitachi Deskstar 7K250 HDS722525VLSA80 V360A60A 250.0GB 7200 RPM SATA150 Hitachi Deskstar 7K250 HDS722516VSA80 V360A60A 160.0GB 7200 RPM SATA150 Hitachi Deskstar 7K250 HDS722512VLSA80 V360A60A 123.5GB 7200 RPM SATA150 Hitachi Deskstar 7K250 HDS722580VLSA80 V360A60A 80.0GB 7200 RPM SATA150 Seagate Barracuda 7200.7 ST3160827AS 3.00 160.0GB 7200 RPM NCQ SATA150 Seagate Barracuda 7200.7 ST3120827AS 3.42 120.0GB 7200 RPM NCQ SATA150 Seagate Barracuda 7200.7 ST380817AS 3.42 80.0GB 7200 RPM NCQ SATA150 Seagate Barracuda 7200.7 ST3160023AS 3.05 160.0GB 7200 RPM SATA150 Seagate Barracuda 7200.7 ST3120026AS 3.05 120.0GB 7200 RPM SATA150 Seagate Barracuda - V ST3120023AS 3.01 120.0GB 7200 RPM SATA150 Seagate Barracuda - V ST380023AS 3.01 80.0GB 7200 RPM SATA150 Seagate Barracuda 7200.7 ST380013AS 3.01 80.0GB 7200 RPM SATA150 Seagate Barracuda 7200.7 ST3250823AS 3.01 250.0GB 7200 RPM NCQ SATA150 Seagate Barracuda 7200.7 ST3300831AS 3.01 300.0GB 7200 RPM NCQ SATA150 Seagate Barracuda 7200.7 ST3400832AS -

The Disk Drive Industry's Dynamic Past
Tuesday Conference Session 3 Roadmaps: The Past and Future of Storage DISK DRIVES: A hard life, but never boring James N. Porter DISK/TREND YESTERDAY’S DISK DRIVES The 1950’s 1956: IBM 350 RAMAC -- 5 MB • First disk drive • 50 24-inch disks • Hydrostatic air bearing heads • Demonstrated market and producibility The 1960’s 1961: Bryant Computer 4240 -- 90 MB • First disk drive with zoned recording • 24 39-inch disks 1962: IBM 1301 “Adv. Disk File” -- 28 MB • First drive with hydrodynamic air bearing heads • 25 or 50 24-inch disks 1963: IBM 1311 “Low Cost File”--2.68 MB • First drive with removable disk pack • First production 14-inch disk drive The 1960’s 1965: IBM 2310 “Ramkit” -- 1.024 MB • First single disk cartridge drive • First voice coil actuator 1966: IBM 2314 Storage Facility--29.17 MB • Eight drives with single controller • Removable disk pack (11 disks) • First drive with ferrite core heads 1967: Memorex 630 -- 7.25 MB • First IBM plug compatible disk drive The 1970’s 1971: IBM 3330-1 “Merlin” -- 100 MB • First track-following servo system 1971: IBM 23FD “Minnow” -- 81 KB • First production flexible disk drive • 8-inch disks, read only 1973: IBM 3340 “Winchester” -- 35/70 MB • First disk drive with low mass heads, lubricated disks, sealed assembly • Removable 3348 Data Module The 1970’s 1974: IBM 3330-11 “Iceberg” -- 200 MB • IBM’s last disk pack drive 1975: IBM 62GV “Gulliver” -- 5/9 MB • First drive with rotary actuator 1976: Shugart Associates SA400 -- 218 KB • First 5.25-inch flexible disk drive The 1970’s 1976: IBM 3350 “Madrid” -- 317.5 MB • Reintroduction of fixed disk media 1979: IBM 3370 “New File Project”--571 MB • First moving head drive with thin film heads, 2-7 encoding.