"A Shadow History of the Internet", Finn Brunton
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Eszter Babarczy: Community Based Trust on the Internet
PTE BTK Nyelvtudományi Doktori Iskola Kommunikáció Doktori Program Babarczy Eszter: Community Based Trust on the Internet Doktori értekezés Témavezető: Horányi Özséb egyetemi tanár 2011. 1 Community-based trust on the internet Tartalom Introduction .................................................................................................................................................. 3 II. A very brief history of the internet ........................................................................................................... 9 Early Days ............................................................................................................................................... 11 Mainstream internet .............................................................................................................................. 12 The internet of social software .............................................................................................................. 15 III Early trust related problems and solutions ............................................................................................ 20 Trading .................................................................................................................................................... 20 Risks of and trust in content ....................................................................................................................... 22 UGC and its discontents: Wikipedia ...................................................................................................... -

The Internet Is a Semicommons
GRIMMELMANN_10_04_29_APPROVED_PAGINATED 4/29/2010 11:26 PM THE INTERNET IS A SEMICOMMONS James Grimmelmann* I. INTRODUCTION As my contribution to this Symposium on David Post’s In Search of Jefferson’s Moose1 and Jonathan Zittrain’s The Future of the Internet,2 I’d like to take up a question with which both books are obsessed: what makes the Internet work? Post’s answer is that the Internet is uniquely Jeffersonian; it embodies a civic ideal of bottom-up democracy3 and an intellectual ideal of generous curiosity.4 Zittrain’s answer is that the Internet is uniquely generative; it enables its users to experiment with new uses and then share their innovations with each other.5 Both books tell a story about how the combination of individual freedom and a cooperative ethos have driven the Internet’s astonishing growth. In that spirit, I’d like to suggest a third reason that the Internet works: it gets the property boundaries right. Specifically, I see the Internet as a particularly striking example of what property theorist Henry Smith has named a semicommons.6 It mixes private property in individual computers and network links with a commons in the communications that flow * Associate Professor, New York Law School. My thanks for their comments to Jack Balkin, Shyam Balganesh, Aislinn Black, Anne Chen, Matt Haughey, Amy Kapczynski, David Krinsky, Jonathon Penney, Chris Riley, Henry Smith, Jessamyn West, and Steven Wu. I presented earlier versions of this essay at the Commons Theory Workshop for Young Scholars (Max Planck Institute for the Study of Collective Goods), the 2007 IP Scholars conference, the 2007 Telecommunications Policy Research Conference, and the December 2009 Symposium at Fordham Law School on David Post’s and Jonathan Zittrain’s books. -

Internet... the Final Frontier. Eine Ethnographie. Schlußbericht Des Projekts 'Interaktionsraum Internet. Netzkultur Und Ne
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Research Papers in Economics econstor www.econstor.eu Der Open-Access-Publikationsserver der ZBW – Leibniz-Informationszentrum Wirtschaft The Open Access Publication Server of the ZBW – Leibniz Information Centre for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112 Provided in cooperation with: Wissenschaftszentrum Berlin für Sozialforschung (WZB) Suggested citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (1998) : Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation, Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit- Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112, http:// hdl.handle.net/10419/49813 Nutzungsbedingungen: Terms of use: Die ZBW räumt Ihnen als Nutzerin/Nutzer das unentgeltliche, The ZBW grants you, the user, the non-exclusive right to use räumlich unbeschränkte und zeitlich auf die Dauer des Schutzrechts the selected work free of charge, territorially unrestricted and beschränkte einfache Recht ein, das ausgewählte Werk im Rahmen within the time limit of the term of the property rights according der unter to the terms specified at → http://www.econstor.eu/dspace/Nutzungsbedingungen → http://www.econstor.eu/dspace/Nutzungsbedingungen nachzulesenden vollständigen Nutzungsbedingungen zu By the first use of the selected work the user agrees and vervielfältigen, mit denen die Nutzerin/der Nutzer sich durch die declares to comply with these terms of use. -

Jargon File, Version 4.0.0, 24 Jul 1996
JARGON FILE, VERSION 4.0.0, 24 JUL 1996 This is the Jargon File, a comprehensive compendium of hacker slang illuminating many aspects of hackish tradition, folklore, and humor. This document (the Jargon File) is in the public domain, to be freely used, shared, and modified. There are (by intention) no legal restraints on what you can do with it, but there are traditions about its proper use to which many hackers are quite strongly attached. Please extend the courtesy of proper citation when you quote the File, ideally with a version number, as it will change and grow over time. (Examples of appropriate citation form: "Jargon File 4.0.0" or "The on-line hacker Jargon File, version 4.0.0, 24 JUL 1996".) The Jargon File is a common heritage of the hacker culture. Over the years a number of individuals have volunteered considerable time to maintaining the File and been recognized by the net at large as editors of it. Editorial responsibilities include: to collate contributions and suggestions from others; to seek out corroborating information; to cross-reference related entries; to keep the file in a consistent format; and to announce and distribute updated versions periodically. Current volunteer editors include: Eric Raymond [email protected] Although there is no requirement that you do so, it is considered good form to check with an editor before quoting the File in a published work or commercial product. We may have additional information that would be helpful to you and can assist you in framing your quote to reflect not only the letter of the File but its spirit as well. -

Online Identifiers in Everyday Life
© 2010 by Benjamin M. Gross. All rights reserved. ONLINE IDENTIFIERS IN EVERYDAY LIFE BY BENJAMIN M. GROSS DISSERTATION Submied in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Library and Information Science in the Graduate College of the University of Illinois at Urbana-Champaign, 2010 Urbana, Illinois Doctoral Commiee: Associate Professor Michael Twidale, Chair Professor Geof Bowker, University of Pisburgh Professor Chip Bruce Associate Professor Ann Bishop Abstract Identifiers are an essential component of online communication. Email addresses and instant messenger usernames are two of the most common online identi- fiers. is dissertation focuses on the ways that social, technical and policy fac- tors affect individual’s behavior with online identifiers. Research for this dissertation was completed in two parts, an interview-based study drawn from two populations and an examination of the infrastructure for managing identifiers in two large consumer services. e exploratory study ex- amines how individuals use online identifiers to segment and integrate aspects of their lives. e first population is drawn from employees of a financial ser- vice firm with substantial constraints on communication in the workplace. e second population is drawn from a design firm with minimal constraints on com- munication. e two populations provide the opportunity to explore the social, technical, and policy issues that arise from diverse communication needs, uses, strategies, and technologies. e examination of systems focuses on the infras- tructure that Google and Yahoo! provide for individuals to manage their iden- tifiers across multiple services, and the risks and benefits of employing single sign-on systems. -

Democratic Participation in the Discursive Management of Usenet
Proceedings of the 35th Hawaii International Conference on System Sciences - 2002 1 Democratic Participation in the Discursive Management of Usenet John C. Paolillo, SLIS and Informatics and David Heald, Computer Science Indiana University, Bloomington <[email protected]> <[email protected]> voters can take advantage of the increased information Abstract available to them, and the greater freedom (i.e., the ability to “vote in one’s pajamas”) and lower costs [11] Internet voting, sometimes proposed as a means of afforded by online voting will thereby ameliorate past enhancing democratic participation, is partly inspired problems of potentially uninformed, apathetic elector- by the democratic process of newsgroup creation on ates and limited access to the polls on account of loca- Usenet. To better understand how online voting might tion, disability, race, etc. These forecasts raise the ex- influence democratic participation more generally, we pectation of higher election turnouts, including among conducted an empirical investigation into the voting traditionally disenfranchised groups. activity on newsgroups in the comp hierarchy of Use- In much this spirit of optimism, the Spring 2000 net since 1989. Counter to expectation, participation Arizona Democratic Party primary offered voters the does not appear to be organized into factions or interest option of casting online and mail-in ballots in addition groups, but rather there are distinct, individualized pat- to more traditional voting options. This experiment terns of voting. At a coarser level of analysis, some was not entirely successful, however, and it was chal- interest-based patterns do emerge, but these appear to lenged early on by voting-rights groups who feared that correspond to frequent individual voters instead of co- problems of differential access to the Internet could lead herent groups of voters. -

PKI Endbericht 24.05.13 12:28
PKI Endbericht 24.05.13 12:28 Startseite Über uns Endbericht (Hyper-)Texte Allerlei Interaktionen Sitemap Internet... the Final Frontier: eine Ethnographie Captain's Log Kulturraum Internet Regierende Techniken und Techniken des Regierens: zur Politik im Netz Hello Usenet - Good-bye? Über das Rauschen eines Mediums 'Last Chance for Common Sense': Interaktionsraum Internet in der Zusammenschau Literaturliste Akronyme und Abkürzungen Zusammenfassung Das im Herbst 1998 abgeschlossene Forschungsprojekt "Interaktionsraum Internet" hat sich mit den konstitutiven Merkmalen der Netzkultur und Netzwerkorganisation beschäftigt. Im Vordergrund des Interesses stand das dynamische Zusammenspiel technischer und gesellschaftlicher Konventionen in der Organisation wie auch im Wandel des Netzes. Die ethnographisch angeleitete Binnenperspektive auf das Internet konzentrierte sich auf drei ausgewählte Bereiche, um Prozesse der Institutionenbildung und die Formen ihrer Transformation zu studieren: die hegemoniale Betriebstechnik der Netzknoten (UNIX), die grundlegende Übertragungstechnik im Netz (das Internet Protokoll IP) und einen populären Kommunikationsdienst (Usenet). Der Schlußbericht des Projekts enthält die Ergebnisse der drei Untersuchungsstränge. Gezeigt wird anhand der Entwicklung in den drei Feldern, daß sich der Wandel des Netzes weder beliebig noch anarchisch vollzieht. Das dezentral organisierte Internet beruht vielmehr auf technisch wie http://duplox.wzb.eu/endbericht/index.html Seite 1 von 7 PKI Endbericht 24.05.13 12:28 organisatorisch verteilten Formen der Koordination, in denen individuelle Handlungspräferenzen kollektiv definitionsmächtig werden. Abstract The research project "Interaktionsraum Internet", which completed its mission in Autumn 1998, studied the constitutive features of network culture and network organization. Special emphasis was given to the dynamic interplay of technical and social conventions regarding both the Net's organization as well as its change. -

The Internet Is a Semicommons
Fordham Law Review Volume 78 Issue 6 Article 5 2010 The Internet is a Semicommons James Grimmelmann Follow this and additional works at: https://ir.lawnet.fordham.edu/flr Part of the Law Commons Recommended Citation James Grimmelmann, The Internet is a Semicommons, 78 Fordham L. Rev. 2799 (2010). Available at: https://ir.lawnet.fordham.edu/flr/vol78/iss6/5 This Article is brought to you for free and open access by FLASH: The Fordham Law Archive of Scholarship and History. It has been accepted for inclusion in Fordham Law Review by an authorized editor of FLASH: The Fordham Law Archive of Scholarship and History. For more information, please contact [email protected]. The Internet is a Semicommons Cover Page Footnote Associate Professor, New York Law School. My thanks for their comments to Jack Balkin, Shyam Balganesh, Aislinn Black, Anne Chen, Matt Haughey, Amy Kapczynski, David Krinsky, Jonathon Penney, Chris Riley, Henry Smith, Jessamyn West, and Steven Wu. I presented earlier versions of this essay at the Commons Theory Workshop for Young Scholars (Max Planck Institute for the Study of Collective Goods), the 2007 IP Scholars conference, the 2007 Telecommunications Policy Research Conference, and the December 2009 Symposium at Fordham Law School on David Post’s and Jonathan Zittrain’s books. This essay may be freely reused under the terms of the Creative Commons Attribution 3.0 United States license, http://creativecommons.org/licenses/by/3.0/us/. This article is available in Fordham Law Review: https://ir.lawnet.fordham.edu/flr/vol78/iss6/5 THE INTERNET IS A SEMICOMMONS James Grimmelmann* I. -
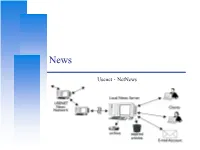
Usenet、Netnews
News Usenet、NetNews Computer Center, CS, NCTU Computer Center, News outline Introduction • History of netnews • History of newsgroups • News operations Transfer protocol • NNTP – Network News Transfer Protocol News softwares • Reader: tin • Server: INN – InterNet News 2 Introduction to News Computer Center, CS, NCTU Computer Center, Introduction to news (1) Usenet is a worldwide distributed Internet discussion system. • The initial Internet community • Like bulletin board systems (BBS) • Hybrid between e-mail and web forums • Absence of a central server and dedicated administrator The format and transmission of Usenet articles is similar to that of Internet e-mail messages. Usenet has significant cultural importance in the networked world • FAQ, spam. 4 Computer Center, CS, NCTU Computer Center, Introduction to news (2) Spamming: In 1994, advertisers began broadcasting messags to all newsgroups at once. Usenet has diminished in importance with respect to Internet forums, blogs, and mailing lists. Google made efforts to buy archive of Usenet newsgroups to attempt to create a complete one. Google has a web search interface and also allows newsgroup posting. • http://groups.google.com Usenet is a “must-have” resource? Year 1996 1997 1998 1999 2000 2001 2002 2003 Daily Vol. (GB) 4.5 9 12 26 82 181 257 492 Year 2004 2005 2006 2007 2008 2009 2010 2011 Daily Vol. (TB) 1 1.52 2.27 2.95 3.07 4.65 5.42 7.52 5 Computer Center, CS, NCTU Computer Center, Introduction to news (3) 6 Computer Center, CS, NCTU Computer Center, History (1) Origins -

Amateur Computerist Newsletter
The Amateur Computerist Webpage: http://www.ais.org/~jrh/acn/ Fall 1992 The Wonderful World of Usenet News Supplement Table of Contents Introduction. Page 1 THE NET WORKS. Page 3 ‘Arte’, Computers and. Page 11 Computer as a Democratizer.. Page 25 CityNet in. Page 31 Learning About Usenet.. Page 32 Freenet BBS’s.. Page 34 Usenet News. Page 35 Two Books to Help Users:. Page 46 Liberation Technology. Page 53 In Memorial. Page 59 Introduction One day during a programming class, one UAW member explained that people at Ford had taken classes in BASIC because they wanted to see what the computer could do. This special supplement begins a serious answer to that question by featuring several articles about one of the most important developments in the world of computers and telecommunications – the creation, use, and potential of Usenet News. The different articles in this issue examine this development from different perspectives. Hopefully they will begin the process of seriously looking at this important development of our current times which has been made possible by the computer and Page 1 the computer pioneers who have taken on to develop its potential. Recently, on Usenet News, a professor from Germany, posted a request for nominations for who was likely to, or should get the Nobel Prize in Economics. One response was that the prize should go to reward the significant achievement of the pioneers of Usenet News instead of to an economist creating useless models, as usual. Just a few years ago, such a response would not have been heard outside of one’s small circle of friends. -

The Virtual Community Homesteading on the Electronic Frontier
The Virtual Community Homesteading on the Electronic Frontier by Howard Rheingold ADDISON-WESLEY PUBLISHING COMPANY Reading, MA Copyright © 1993 by Howard Rheingold "When you think of a title for a book, you are forced to think of something short and evocative, like, well, 'The Virtual Community,' even though a more accurate title might be: 'People who use computers to communicate, form friendships that sometimes form the basis of communities, but you have to be careful to not mistake the tool for the task and think that just writing words on a screen is the same thing as real community.'" – HLR We know the rules of community; we know the healing effect of community in terms of individual lives. If we could somehow find a way across the bridge of our knowledge, would not these same rules have a healing effect upon our world? We human beings have often been referred to as social animals. But we are not yet community creatures. We are impelled to relate with each other for our survival. But we do not yet relate with the inclusivity, realism, self-awareness, vulnerability, commitment, openness, freedom, equality, and love of genuine community. It is clearly no longer enough to be simply social animals, babbling together at cocktail parties and brawling with each other in business and over boundaries. It is our task--our essential, central, crucial task--to transform ourselves from mere social creatures into community creatures. It is the only way that human evolution will be able to proceed. M. Scott Peck The Different Drum: Community-Making -

Project Report for Msc in Business Systems Analysis & Design
City University MSc in Business Systems Analysis & Design Project Report 2007 UNISoN: A tool to aid evaluation of sociability in on-line discussion boards Name: Stephen Thomas Leonard E-mail address: [email protected] Supervisor: Dr Panayiotis Zaphiris Declaration By submitting this work, I declare that this work is entirely my own except those parts duly identified and referenced in my submission. It complies with specified word limits and the requirements and regulations detailed in the coursework instructions and any other relevant programme and module documentation. In submitting this work, I acknowledge that I have read and understood the regulations and code regarding academic misconduct, including that related to plagiarism, as specified in the Programme Handbook. I also acknowledge that this work will be subject to a variety of checks for academic misconduct. Signed Stephen Leonard Stephen Leonard (abbh224) - 2 - Abstract This report presents a tool that can be used to aid the study of online social networks. It builds upon earlier work that studied Usenet groups which were limited by the manual data collection methods used. The main goal of the application is to allow the user to select newsgroups they are interested in, quickly download large numbers of messages and allow them to preview the data. It includes a graphical representation of the networks which clearly shows the clusters and isolated individuals in the network. The report will show that the application will yield the same results as manual data collection methods, but at a much faster rate. The chosen output file format is compatible with Pajek, a popular open source social network analysis tool.