3 SAGE by Almost Any Measure -- Scale, Expense, Technical
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open PDF in New Window
BEST AVAILABLE COPY i The pur'pose of this DIGITAL COMPUTER Itop*"°a""-'"""neesietter' YNEWSLETTER . W OFFICf OF NIVAM RUSEARCMI • MATNEMWTICAL SCIENCES DIVISION Vol. 9, No. 2 Editors: Gordon D. Goldstein April 1957 Albrecht J. Neumann TABLE OF CONTENTS It o Page No. W- COMPUTERS. U. S. A. "1.Air Force Armament Center, ARDC, Eglin AFB, Florida 1 2. Air Force Cambridge Research Center, Bedford, Mass. 1 3. Autonetics, RECOMP, Downey, Calif. 2 4. Corps of Engineers, U. S. Army 2 5. IBM 709. New York, New York 3 6. Lincoln Laboratory TX-2, M.I.T., Lexington, Mass. 4 7. Litton Industries 20 and 40 DDA, Beverly Hills, Calif. 5 8. Naval Air Test Centcr, Naval Air Station, Patuxent River, Maryland 5 9. National Cash Register Co. NC 304, Dayton, Ohio 6 10. Naval Air Missile Test Center, RAYDAC, Point Mugu, Calif. 7 11. New York Naval Shipyard, Brooklyn, New York 7 12. Philco, TRANSAC. Philadelphia, Penna. 7 13. Western Reserve Univ., Cleveland, Ohio 8 COMPUTING CENTERS I. Univ. of California, Radiation Lab., Livermore, Calif. 9 2. Univ. of California, SWAC, Los Angeles, Calif. 10 3. Electronic Associates, Inc., Princeton Computation Center, Princeton, New Jersey 10 4. Franklin Institute Laboratories, Computing Center, Philadelphia, Penna. 11 5. George Washington Univ., Logistics Research Project, Washington, D. C. 11 6. M.I.T., WHIRLWIND I, Cambridge, Mass. 12 7. National Bureau of Standards, Applied Mathematics Div., Washington, D.C. 12 8. Naval Proving Ground, Naval Ordnance Computation Center, Dahlgren, Virgin-.a 12 9. Ramo Wooldridge Corp., Digital Computing Center, Los Angeles, Calif. -

Hereby the Screen Stands in For, and Thereby Occludes, the Deeper Workings of the Computer Itself
John Warnock and an IDI graphical display unit, University of Utah, 1968. Courtesy Salt Lake City Deseret News . 24 doi:10.1162/GREY_a_00233 Downloaded from http://www.mitpressjournals.org/doi/pdf/10.1162/GREY_a_00233 by guest on 27 September 2021 The Random-Access Image: Memory and the History of the Computer Screen JACOB GABOURY A memory is a means for displacing in time various events which depend upon the same information. —J. Presper Eckert Jr. 1 When we speak of graphics, we think of images. Be it the windowed interface of a personal computer, the tactile swipe of icons across a mobile device, or the surreal effects of computer-enhanced film and video games—all are graphics. Understandably, then, computer graphics are most often understood as the images displayed on a computer screen. This pairing of the image and the screen is so natural that we rarely theorize the screen as a medium itself, one with a heterogeneous history that develops in parallel with other visual and computa - tional forms. 2 What then, of the screen? To be sure, the computer screen follows in the tradition of the visual frame that delimits, contains, and produces the image. 3 It is also the skin of the interface that allows us to engage with, augment, and relate to technical things. 4 But the computer screen was also a cathode ray tube (CRT) phosphorescing in response to an electron beam, modified by a grid of randomly accessible memory that stores, maps, and transforms thousands of bits in real time. The screen is not simply an enduring technique or evocative metaphor; it is a hardware object whose transformations have shaped the ma - terial conditions of our visual culture. -

The An/Fsq-7
291961 RJ3117 (38413) 4/10/81 Computer Science Research Report HISTORY OF THE DESIGN OF THE SAGE COMPUTER - THE AN/FSQ-7 Morton M. Astrahan IBM Research Laboratory San Jose, California 95193 Jonn T. Jacobs MITRE Corporation Bedford, Massachusetts 01/30 LIMITED DISTRIBUTION NOTICE Tns r uort has been submitted for publication outside of IBM and will orobably be cooyrightea if accected for publication. It 3i been -ssued as a Researcn Reoort for early dissemination of :s contents. In view of tde transfer of coovr gnt to the outside iblisner. ts distribution outside of iBM onor to publication ^ncyld be limited ?o oeer communications ana specific r-jauests. After outside oublicouon. reauests sbouid Do *illed only by reonnts or legally obtained cooies of the artic> ie q.. payment of royalties) Research Division Yorktown Heights, New York • S3n Jose. California * Zurich, Switzerland Copies may be requested from IBM Thomas J. Watson Research Center Distribution Services Post Office Box 21 8 Yorktown Heights. New York 10598 RJ3117 (33413) 4/10/81 Computer Science History of the Design of the SAGE Computer- the AN/FSQ-7 Morton M. Astrahan John F. Jacobs IBM Research Laboratory MITRE Corp. San Jose, California 95193 Bedford, Massachusetts 01730 ABSTRACT: This is the story of the development of the SAGE (Semi-Aucomatic Ground Environment) Air Defense Computer, the AN/FSQ-7. At the time of its operational deployment beginning in 1958, the AN/FSQ-7 was the first large-scale, real-time digital control computer supporting a major mili tary mission. The AN/FSQ-7 design, including its architecture, components and computer programs, drew on RSD programs throughout the United States, but it drew mostly on work being done at MIT Project Whirlwind and at IBM. -

Guide to the Collection of Massachusetts Institute of Technology Computing Projects Subject Collection
Guide to the Collection of Massachusetts Institute of Technology Computing Projects Subject Collection Dates: 1947-1994, bulk 1950-1975 Extent: 9 linear feet in 8 boxes Collection number: X3495.2006 Accession number: 102634702 Processed by: Paula Little, March 2006 MIT Computing Projects Subject Collection X3495.2006 Abstract The Collection of Massachusetts Institute of Technology (MIT) Computing Projects is comprised of technical notes, reports, correspondence and miscellaneous documentation relating to the development of the Whirlwind, TX-0 and T-X2 computers as well as Project MAC (Multiple-Access Computer) at MIT. Included as well are a number of other technical reports relating to computing projects at MIT. The documents span 1947 to 1994. Administrative Information Access Restrictions The collection is open for research. Publication Rights The Computer History Museum (CHM) can only claim physical ownership of the collection. Users are responsible for satisfying any claims of the copyright holder. Permission to copy or publish any portion of the Computer History Museum’s collection must be given by the Computer History Museum. Preferred Citation [Identification of Item], [Item Date], MIT Computing Projects Subject Collection, Lot X3495.2006, Box [#], Folder [#], Computer History Museum. Provenance The provenance is unknown for the MIT Computing Projects Subject Collection. The Collection was originally acquired from a variety of sources in the 1980s and 1990s when the Computer History Museum, then known as The Computer Museum, was located in Boston. At that time, all documents were arranged alphabetically by originating institution or company. Many of the Whirlwind documents most likely were donated to the Museum in 1982 as part of lot X115.82. -

Brief History of Microprogramming
Microprogramming History -- Mark Smotherman A Brief History of Microprogramming Mark Smotherman Last updated: October 2012 Summary: Microprogramming is a technique to implement the control logic necessary to execute instructions within a processor. It relies on fetching low-level microinstructions from a control store and deriving the appropriate control signals as well as microprogram sequencing information from each microinstruction. Definitions and Example Although loose usage has sometimes equated the term "microprogramming" with the idea of "programming a microcomputer", this is not the standard definition. Rather, microprogramming is a systematic technique for implementing the control logic of a computer's central processing unit. It is a form of stored-program logic that substitutes for hardwired control circuitry. The central processing unit in a computer system is composed of a data path and a control unit. The data path includes registers, function units such as shifters and ALUs (arithmetic and logic units), internal processor busses and paths, and interface units for main memory and I/O busses. The control unit governs the series of steps taken by the data path during the execution of a user- visible instruction, or macroinstruction (e.g., load, add, store). Each action of the datapath is called a register transfer and involves the transfer of information within the data path, possibly including the transformation of data, address, or instruction bits by the function units. A register transfer is accomplished by gating out (sending) register contents onto internal processor busses, selecting the operation of ALUs, shifters, etc., through which that information might pass, and gating in (receiving) new values for one or more registers. -
Pioneercomputertimeline2.Pdf
Memory Size versus Computation Speed for various calculators and computers , IBM,ZQ90 . 11J A~len · W •• EDVAC lAS• ,---.. SEAC • Whirlwind ~ , • ENIAC SWAC /# / Harvard.' ~\ EDSAC Pilot• •• • ; Mc;rk I " • ACE I • •, ABC Manchester MKI • • ! • Z3 (fl. pt.) 1.000 , , .ENIAC •, Ier.n I i • • \ I •, BTL I (complexV • 100 ~ . # '-------" Comptometer • Ir.ne l ' with constants 10 0.1 1.0 10 100 lK 10K lOOK 1M GENERATIONS: II] = electronic-vacuum tube [!!!] = manual [1] = transistor Ime I = mechanical [1] = integrated circuit Iem I = electromechanical [I] = large scale integrated circuit CONTENTS THE COMPUTER MUSEUM BOARD OF DIRECTORS The Computer Museum is a non-profit. Kenneth H. Olsen. Chairman public. charitable foundation dedicated to Digital Equipment Corporation preserving and exhibiting an industry-wide. broad-based collection of the history of in Charles W Bachman formation processing. Computer history is Cullinane Database Systems A Compcmion to the Pioneer interpreted through exhibits. publications. Computer Timeline videotapes. lectures. educational programs. C. Gordon Bell and other programs. The Museum archives Digital Equipment Corporation I Introduction both artifacts and documentation and Gwen Bell makes the materials available for The Computer Museum 2 Bell Telephone Laboratories scholarly use. Harvey D. Cragon Modell Complex Calculator The Computer Museum is open to the public Texas Instruments Sunday through Friday from 1:00 to 6:00 pm. 3 Zuse Zl, Z3 There is no charge for admission. The Robert Everett 4 ABC. Atanasoff Berry Computer Museum's lecture hall and rece ption The Mitre Corporation facilities are available for rent on a mM ASCC (Harvard Mark I) prearranged basis. For information call C. -

Computer Oral History Collection, 1969-1973, 1977
Computer Oral History Collection, 1969-1973, 1977 Interviewee: Nat Rochester Interviewer: Henry S. Tropp Also Present: Jean Sammett Date: July 24, 1973 Repository: Archives Center, National Museum of American History TROPP: This is a discussion with Mr. Nat Rochester and Jean Sammett and myself on the 24th of July, 1973, and we're at the IBM--what is it--Systems ROCHESTER: System. TROPP: Development Division on the MIT campus in Cambridge, Massachusetts. [Recorder off] Why don't we start with the MIT period and Project Whirlwind, and why don't we go back and have you tell us how you got into that particular project, how you came there. What your background was and training leading up to that. ROCHESTER: Well, I was working on radar during World War II. And I had been in the MIT Radiation Laboratory, which developed radar, and then, about the middle of the war, I joined Sylvania and built radar equipment for the Radiation Lab. And so at the end of the war I had a shop that was able to build, design and construct radar sets, experimental radar sets and similar things. And then came the problem of beating swords into plowshares. ROCHESTER & TROPP: Laughter] ROCHESTER: And we got a number of different jobs. ...One of the most interesting ones was to build the arithmetic unit of Whirlwind I. And I also got a job building something for NSA, from which I learned something about the technology that was involved, but I can't tell you anything about that. TROPP: For additional information, contact the Archives Center at 202.633.3270 or [email protected] Computer Oral History Collection, 1969-1973, 1977 Nat Rochester Interview, July 24, 1973, Archives Center, National Museum of American History Right. -

167 UNPUBLISHED MATHEMATICAL TABLES 10100009-10132211 and 50000017-50012839 Is Included. AUTOMATIC COMPUTING MACHINERY an AUTOMA
automatic computing machinery 167 UNPUBLISHED MATHEMATICAL TABLES In this issue there is a reference to an unpublished table in RMT 1015 147[A, P].—Leo Storch, Admittance-Impedance Conversion Tables, Tech- nical Memorandum No. 274, Hughes Aircraft Co., Research and Devel- opment Laboratories, Culver City, California. 10 p. manuscript tabu- lated from punched cards. Copy deposited in UMT File. The table gives 4S values of (1 + s2)"1 and s(l + s2)-1 for 5 = 0(.001)1. It is intended to facilitate the calculation of the reciprocal of a complex number. The table is an extension of a table of Jahnke & Emde. [4th ed., appendix, p. 13. j 148 [F].—F. Gruenberger, Lists of primes. Six sheets tabulated from punched cards. Deposited in the UMT File. These lists of primes are for the ranges 10100009 to 10132211 and 50000017 to 50040013. The lists were computed on a CPC as a fill-in project, without attempting to program for speed. A graph showing the distribution of differences between consecutive primes in the ranges 1000003-1024523, 10100009-10132211and 50000017-50012839 is included. F. Gruenberger University of Wisconsin Madison, Wisconsin 149 [F].—A. Gloden, Table of solutions of the congruence a;128+1=0 (mod p) for p < 20000. Manuscript, 2 p., deposited in the UMT File. The table gives for each of the 16 primes p of the form 256¿ + 1 less than 20000, the 64 solutions of the congruence mentioned in the title which are less than \p. A. Gloden 11 rue Jean Jaurès Luxembourg AUTOMATIC COMPUTING MACHINERY Edited by the Staff of the Machine Development Laboratory of the National Bureau of Standards. -

Approved for Public Release. Case 06-1104
APPROVED FOR PUBLIC RELEASE. CASE 06-1104. PROJECT WHIRLWIND SUMMARY REPORT NO. 29 FIRST QUARTER 1952 Submitted to the OFFICE OF NAVAL RESEARCH Under Contract N5ori60 Project NR 048-097 and the UNITED STATES AIR FORCE Under Contract AF19(l22)-458 DIGITAL COMPUTER LABORATORY MASSACHUSETTS INSTITUTE OF TECHNOLOGY Cambridge 39, Massachusetts APPROVED FOR PUBLIC RELEASE. CASE 06-1104. TABLE OF CONTENTS FOREWORD QUARTERLY REVIEW (AND ABSTRACT) SYSTEM ENGINEERING . 1 Storage Reliability and Checking . 2 Input-Output 3 Operational Control Center CIRCUITS AND COMPONENTS . 1 Vacuum Tubes . 2 Component Replacements in WWI . 3 Ferromagnetic and Ferroelectric Cores .4 Transistors , ELECTROSTATIC STORAGE . 1 Tube Program INPUT-OUTPUT . 1 Magnetic Tape . 2 Magnetic Drums MATHEMATICS, CODING, AND APPLICATIONS . 1 Problems Being Solved . 2 Subroutines Completed ACADEMIC PROGRAM IN AUTOMATIC COMPUTATION AND NUMERICAL ANALYSIS . 1 Automatic Computation and Numerical Analysis . 2 Seminars on Computing Machine Methods APPENDIX . 1 Reports and Publications . 2 Professional Society Papers . 3 Visitors e APPROVED FOR PUBLIC RELEASE. CASE 06-1104. 1. QUARTERLY REVIEW tion of the 16x16 ceramic array has been (AND ABSTRACT) operated, but much work remains to be done. FOREWORD A multi-position ferroelectric switch has been developed which can perform many of the During the firstquarter of 1952 the Whirl switching tasks required in an information- wind I computer used one bank of storage handling system. A magnetic-materials group tubes with a density of 32x32 (1024) spots. has been formed for the purpose of develop Project Whirlwind The original bank of 16 x 16 tubes was remov ing ferromagnetic and ferroelectric materi ed from operation. -
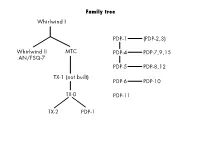
Family Tree Whirlwind I Whirlwind II AN/FSQ-7 MTC TX-1 (Not
Family tree Whirlwind I PDP-1 (PDP-2,3) Whirlwind II MTC PDP-4 PDP-7,9,15 AN/FSQ-7 PDP-5 PDP-8,12 TX-1 (not built) PDP-6 PDP-10 TX-0 PDP-11 TX-2 PDP-1 Whirlwind I block diagram PERIPHERALS PRPC SS 11 16 11 STORAGE 16 IOR 16 STORAGE ELEMENT CS 5 AR 16 SC 5 CONTROL AC 16 BR 16 CONTROL ELEMENT ARITHMETIC ELEMENT Whirlwind I summary INSTRUCTION AC BR ARSAM C(x) 00000 SI SELECT IO UNIT 00001 ILLEGAL 00010 BI BLOCK IN x + n x first word 00011 RD READ IOR IOR 00100 BO BLOCK OUT x + n x 00101 RC RECORD 00110 SD SUM OF DIGITS AC ∨ C(x) C(x) 0 00111 CF CHANGE FIELDS 01000 TS TRANSFER TO STORAGE AC 01001 TD TRANSFER DIGITS C(x)0-4,AC5-15 01010 TA TRANSFER ADDRESS C(x)0-4,AR5-15 01011 CK CHECK 01100 AB ADD BR BR + C(x) C(x) 0 BR + C(x) 01101 EX EXCHANGE C(x) C(x) AC 01110 CP CONDITIONAL SP y+1 01111 SP SUBPROGRAM y+1 10000 CA CLEAR, ADD C(x) + SAM 0 C(x) 0 10001 CS CLEAR, SUBTRACT –C(x) + SAM 0 C(x) 0 10010 AD ADD AC + C(x) C(x) 0 10011 SU SUBTRACT AC – C(x) C(x) 0 10100 CM CLEAR, ADD MAG. |C(x)|+SAM 0 |C(x)| 0 10101 SA SPECIAL ADD AC + C(x) C(x) ±1 or 0 10110 AO ADD ONE C(x) + 1 C(x) 0 C(x) + 1 10111 DM DIFFERENCE OF MAG. -
Microprogramming and Its Relationship to Emulation and Technology*
MICROPROGRAMMING AND ITS RELATIONSHIP TO EMULATION AND TECHNOLOGY* Samuel H. Fuller and Victor R. Lesser Carnesie-Mellon University Pittsburgh, Pennsylvania C. Gordon Bell and Charles Kaman Digital Equipment Corporation Maynard, Massachusetts ABSTRACT data paths; or features of a processor's realization, such as the speed of main memory to that of the control (micro-) This paper is a survey of the development and future memory, are easily rejected on the basis of existing trends in rnicroprograrnrning. We show how the structure of processors that are commonly recosnized to be rnicroprograrnmed processors has been shaped primarily by microprogramrned processors yet do not possess the required two factors= the state of (semiconductor) technology and the features. task of emulation. The other main theme of this article is that it is a fruitless exercise to try to characterize and understand Most of this confusion in alternative definitions of microprograrnming in terms of how it differs from 'regular' microprograrnrning comes from the fact that it has been used programming. The right approach to understanding in two very different ways: (1) in a technological manner to microprogramrning is to recognize that it is primarily applied economically implement a complex instruction set or a small to the task of emulation (interpretation). Through this number of different instruction sets on a single processor, approach the evolution of rnicroprograrnming, independent of and (2) in a software manner to provide programmers with an a particular technology and type of instruction set being extra degree of representational freedom, i.e. develop emulated, is reviewed and future trends indicated. multiple instruction sets, each one appropriate for a particular task domain. -
Jay Wright Forrester
Jay Wright Forrester Born July 14, 1918, Climax, Neb.; Massachusetts Institute of Technology leader of the Whirlwind Project and 1 inventor of the random-access magnetic core memory matrices. 5 Education: BSc, University of Nebraska, 1939; SM, MIT, 1945. Professional Experience: MIT: member, staff Servomechanisms Laboratory, 1940- 1946, director, Digital Computer Laboratory, 1946-1951, head, Digital Computer Division, Lincoln Laboratory, 1951-1956, professor of management, 1956-1972, Germeshausen professor, 1972-1989, Germeshausen professor emeritus and senior lecturer, 1989-present. Honors and Awards: DEng, University of Nebraska, 1954; National Academy of Engineering, 1967; DSc, Boston University, 1969; Valdemar Poulsen Gold Medal, Danish Academy of Technical Sciences, 1969; DEng, Newark College of Engineering, 1971; Medal of Honor, Institute of Electrical and Electronics Engineers, 1972; System, Man, and Cybernetics Award for Outstanding Accomplishment, IEEE, 1972; Benjamin Franklin Fellow, Royal Society of Arts, London, 1972; DEng, Union College, 1973; DEng, University of Notre Dame, 1974; Howard N. Potts Award, Franklin Institute, 1974; honorary member, Society of Manufacturing Engineers,2 1976; Harry Goode Memorial Award, American Federation of Information Processing Societies, 1977; Doctor of Political Science, University of Mannheim, Germany, 1979; Inventors Hall of Fame, 1979; Computer Pioneer Award, IEEE Computer Society, 1982; Jay W. Forrester Chair in Computer Studies at MIT, endowed by Thomas J. Watson, Jr., 1986; James R. Killian, Jr., Faculty Achievement Award, MIT, 1987; honorary professor, Shanghai Institute of Technology, China, 1987; Information Storage Award, IEEE Magnetics Society, 1988; Doctor of Humane Letters, State University of New York, 1988; US National Medal of Technology (with Robert R. Everett), 1989; Pioneer Award, IEEE Aerospace and Electronic Systems Society (with Robert R.