Deploying Android Security Updates: an Extensive Study Involving Manufacturers, Carriers, and End Users
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Flash Yellow Powered by the Nationwide Sprint 4G LTE Network Table of Contents
How to Build a Successful Business with Flash Yellow powered by the Nationwide Sprint 4G LTE Network Table of Contents This playbook contains everything you need build a successful business with Flash Wireless! 1. Understand your customer’s needs. GO TO PAGE 3 2. Recommend Flash Yellow in strong service areas. GO TO PAGE 4 a. Strong service map GO TO PAGE 5 3. Help your customer decide on a service plan GO TO PAGE 6 4. Ensure your customer is on the right device GO TO PAGE 8 a. If they are buying a new device GO TO PAGE 9 b. If they are bringing their own device GO TO PAGE 15 5. Device Appendix – Is your customer’s device compatible? GO TO PAGE 28 2 Step 1. Understand your customer’s needs • Mostly voice and text - Flash Yellow network would be a good fit in most metropolitan areas. For suburban / rural areas, check to see if they live in a strong Flash Yellow service area. • Average to heavy data user - Check to see if they live in a strong Flash Yellow service area. See page 5. If not, guide them to Flash Green or Flash Purple network to ensure they get the best customer experience. Remember, a good customer experience is the key to keeping a long-term customer! 3 Step 2. Recommend Flash Yellow in strong areas • Review Flash Yellow’s strong service areas. Focus your Flash Yellow customer acquisition efforts on these areas to ensure high customer satisfaction and retention. See page 5. o This is a top 24 list, the network is strong in other areas too. -
Ibeta-Device-Invento
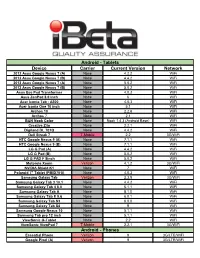
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel (C) Factory Unlocked 9 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel -
Sprint Complete
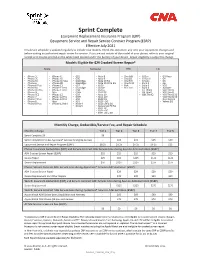
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) Effective July 2021 This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair* Apple Samsung HTC LG • iPhone 5 • iPhone X • GS5 • Note 8 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone XS • GS6 • Note 9 • One E8 • G Flex II • G4 • iPhone 5S • iPhone XS Max • GS6 Edge • Note 20 5G • One M9 • G Stylo • G5 • iPhone 6 • iPhone XR • GS6 Edge+ • Note 20 Ultra 5G • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 11 • GS7 • GS10 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone 11 Pro • GS7 Edge • GS10e • HTC U11 • Stylo 6 • X power • iPhone 6S Plus • iPhone 11 Pro • GS8 • GS10+ • G7 ThinQ • V40 ThinQ • iPhone SE Max • GS8+ • GS10 5G • G8 ThinQ • V50 ThinQ • iPhone SE2 • iPhone 12 • GS9 • Note 10 • G8X ThinQ • V60 ThinQ 5G • iPhone 7 • iPhone 12 Pro • GS9+ • Note 10+ • V60 ThinQ 5G • iPhone 7 Plus • iPhone 12 Pro • A50 • GS20 5G Dual Screen • iPhone 8 Max • A51 • GS20+ 5G • Velvet 5G • iPhone 8 Plus • iPhone 12 Mini • Note 4 • GS20 Ultra 5G • Note 5 • Galaxy S20 FE 5G • GS21 5G • GS21+ 5G • GS21 Ultra 5G Monthly Charge, Deductible/Service Fee, and Repair Schedule -

Essential Phone on Its Way to Early Adopters 24 August 2017, by Seung Lee, the Mercury News
Essential Phone on its way to early adopters 24 August 2017, by Seung Lee, The Mercury News this week in a press briefing in Essential's headquarters in Palo Alto. "People have neglected hardware for years, decades. The rest of the venture business is focused on software, on service." Essential wanted to make a timeless, high-powered phone, according to Rubin. Its bezel-less and logo- less design is reinforced by titanium parts, stronger than the industry standard aluminum parts, and a ceramic exterior. It has no buttons in its front display but has a fingerprint scanner on the back. The company is also making accessories, like an attachable 360-degree camera, and the Phone will work with products from its competition, such as the Apple Homekit. Essential, the new smartphone company founded by Android operating system creator Andy Rubin, "How do you build technology that consumers are is planning to ship its first pre-ordered flagship willing to invest in?" asked Rubin. "Inter-operability smartphones soon. The general launch date for is really, really important. We acknowledge that, the Essential Phone remains unknown, despite and we inter-operate with companies even if they months of publicity and continued intrigue among are our competitors." Silicon Valley's gadget-loving circles. Recently, Essential's exclusive carrier Sprint announced it While the 5.7-inch phone feels denser than its will open Phone pre-orders on its own website and Apple and Samsung counterparts, it is bereft of stores. Essential opened up pre-orders on its bloatware - rarely used default apps that are website in May when the product was first common in new smartphones. -

Weekly Wireless Report August 18, 2017
Week Ending: Weekly Wireless Report August 18, 2017 This Week’s Stories Apple Is On The Hunt For Original TV Shows Inside This Issue: August 16, 2017 This Week’s Stories Apple is finally getting serious about original TV programming. Apple Is On The Hunt For Original TV Shows Two Apple executives have been meeting with Hollywood agents and producers to hear pitches about possible shows for Apple to buy, according to two producers who have met with them. Facebook Is Building A New $750 Million Data Center In Ohio The execs, Jamie Erlicht and Zack Van Amburg, were hired from Sony Pictures Television in June to oversee Apple's video programming. Products & Services New Apple, Samsung These pitch meetings have placed Apple in direct competition with Netflix, HBO and other Smartphone Challenger Is Finally distributors. Available For Pre-Order Some producers are eager to work with Apple, sensing a first-mover advantage. Others have a lot of YouTube TV Now Available To questions about how Apple will distribute its shows. When "House of Cards" debuted on Netflix, 50% Of U.S. Households marking the streaming service's entrance into original programming, the service already had a large catalog of licensed programming. Apple, Aetna Hold Secret Meetings To Bring Apple Watch To Millions Of Aetna Customers Apple doesn't have that -- but it does have iPhones in hundreds of millions of hands. Emerging Technology The meetings were first reported by The Wall Street Journal on Wednesday. Apple is said to be AI Is Taking Over The Cloud budgeting about $1 billion to acquire and produce original TV shows over the next year, according to the Journal. -

Darkreader: Bridging the Gap Between Perception and Reality Of
DarkReader: Bridging the Gap Between Perception and Reality of Power Consumption in Smartphones for Blind Users Jian Xu∗ Syed Masum Billah* Roy Shilkrot Stony Brook University Stony Brook University Stony Brook University Stony Brook, USA Stony Brook, USA Stony Brook, USA [email protected] [email protected] [email protected] Aruna Balasubramanian Stony Brook University Stony Brook, USA [email protected] ABSTRACT This paper presents a user study with 10 blind participants to understand their perception of power consumption in smart- phones. We found that a widely used power saving mechanism for smartphones–pressing the power button to put the smart- phone to sleep–has a serious usability issue for blind screen reader users. Among other findings, our study also unearthed several usage patterns and misconceptions of blind users that contribute to excessive battery drainage. Informed by the first user study, this paper proposes DarkReader, a screen reader developed in Android that bridges users’ perception of power consumption to reality. DarkReader darkens the screen by truly turning it off, but allows users to interact with their smart- phones. A second user study with 10 blind participants shows that participants perceived no difference in completion times in performing routine tasks using DarkReader and default screen reader. Yet DarkReader saves 24% to 52% power depending Figure 1. A blind user is interacting with his smartphone using a (A) on tasks and screen brightness. standard screen reader (e.g., TalkBack in Android), and (B) DarkReader. Unlike TalkBack, DarkReader keeps the screen off to save power. Author Keywords Vision impairment, blind; screen readers, TalkBack, Android, iOS; low-power, battery, screen, brightness; privacy, curtain INTRODUCTION mode, shoulder-surfing. -
![Arxiv:1910.06663V1 [Cs.PF] 15 Oct 2019](https://docslib.b-cdn.net/cover/5599/arxiv-1910-06663v1-cs-pf-15-oct-2019-1465599.webp)
Arxiv:1910.06663V1 [Cs.PF] 15 Oct 2019
AI Benchmark: All About Deep Learning on Smartphones in 2019 Andrey Ignatov Radu Timofte Andrei Kulik ETH Zurich ETH Zurich Google Research [email protected] [email protected] [email protected] Seungsoo Yang Ke Wang Felix Baum Max Wu Samsung, Inc. Huawei, Inc. Qualcomm, Inc. MediaTek, Inc. [email protected] [email protected] [email protected] [email protected] Lirong Xu Luc Van Gool∗ Unisoc, Inc. ETH Zurich [email protected] [email protected] Abstract compact models as they were running at best on devices with a single-core 600 MHz Arm CPU and 8-128 MB of The performance of mobile AI accelerators has been evolv- RAM. The situation changed after 2010, when mobile de- ing rapidly in the past two years, nearly doubling with each vices started to get multi-core processors, as well as power- new generation of SoCs. The current 4th generation of mo- ful GPUs, DSPs and NPUs, well suitable for machine and bile NPUs is already approaching the results of CUDA- deep learning tasks. At the same time, there was a fast de- compatible Nvidia graphics cards presented not long ago, velopment of the deep learning field, with numerous novel which together with the increased capabilities of mobile approaches and models that were achieving a fundamentally deep learning frameworks makes it possible to run com- new level of performance for many practical tasks, such as plex and deep AI models on mobile devices. In this pa- image classification, photo and speech processing, neural per, we evaluate the performance and compare the results of language understanding, etc. -

Projectreport.Pdf (2.519Mb)
! Mobile App Monetization – Expectations and Attitudes Formed by Users in Response to Advertising and Pay To Download Monetization Models Master’s Program Missouri School of Journalism University of Missouri by Anthony Brown Dr. Margaret Duffy, Committee Chair Jim Spencer Dr. Kevin Wise August, 2013 ii Acknowledgments Thanks to Dr. Duffy and Dr. Wise for their guidance and leadership throughout this too-lengthy process. Your patience and flexibility is a golden virtue. Thanks also to Jim Spencer, whose final firm push is exactly what I needed to put my head down and carry this research across the finish line. iii Table of Contents ACKNOWLEDGMENTS ........................................................................ ii LIST OF TABLES ................................................................................. iv ABSTRACT ............................................................................................ v Chapter 1. INTRODUCTION ........................................................................ 1 2. ACTIVITIES DESCRIPTION ....................................................... 3 3. EVALUATION ........................................................................... 14 4. PHYSICAL EVIDENCE ............................................................. 15 5. ANALYSIS ................................................................................ 16 APPENDIX 1. ONLINE SURVEY TEXT AND RESULTS ................................ 31 2. FOCUS GROUP DISCUSSION GUIDE AND TRANSCRIPT ... 61 3. PROJECT PROPOSAL ........................................................... -
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP)
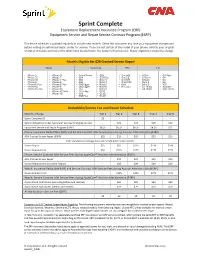
Sprint Complete Equipment Replacement Insurance Program (ERP) Equipment Service and Repair Service Contract Program (ESRP) This device schedule is updated regularly to include new models. Check this document any time your equipment changes and before visiting an authorized repair center for service. If you are not certain of the model of your phone, refer to your original receipt or it may be printed on the white label located under the battery of your device. Repair eligibility is subject to change. Models Eligible for $29 Cracked Screen Repair Apple Samsung HTC LG • iPhone 5 • iPhone SE • Grand Prime • GS9 • One M8 • G Flex • G3 Vigor • iPhone 5C • iPhone 7 • GS4 • GS9 Plus • One E8 • G Flex II • G4 • iPhone 5S • iPhone 7 Plus • GS5 • Note 3 • One M9 • G Stylo • G5 • iPhone 6 • iPhone 8 • GS6 • Note 4 • One M10 • Stylo 2 • G6 • iPhone 6 Plus • iPhone 8 Plus • GS6 Edge • Note 5 • Bolt • Stylo 3 • V20 • iPhone 6S • iPhone X • GS6 Edge+ • Note 8 • HTC U11 • G7 ThinQ • X power • iPhone 6S Plus • iPhone XS • GS7 • Note 9 • G8 ThinQ • V40 ThinQ • iPhone XS Max • GS7 Edge • GS10 • iPhone XR • GS8 • GS10e • GS8 Plus • GS10+ Deductible/Service Fee and Repair Schedule Monthly Charge Tier 1 Tier 2 Tier 3 Tier 4 Tier 5 Sprint Complete $9 $9 - - - - Sprint Complete (Includes AppleCare® Services for eligible devices) - $15 $15 $15 $19 Equipment Service and Repair Program (ESRP) $8.25 $8.25 $8.25 $8.25 $11 Phone: Insurance Deductibles (ERP) and Service Contract ADH Service Fees during Asurion Administration (ESRP) ADH Cracked Screen Repair (ESRP) $25 $29 $29 $29 $29 ESRP standalone coverage does not include $29 cracked screens. -

Supplemental Materials for the PREVENTS Roadmap
Supplemental Materials for the PREVENTS Roadmap Table of Contents Supplemental Materials for the PREVENTS Roadmap ............................................................. 1 Table of Contents ...........................................................................................................................2 Introduction ...................................................................................................................................9 What Causes Suicide?............................................................................................................................................ 9 Complexity of the Problem ................................................................................................................................. 10 Why Public Health? ............................................................................................................................................. 11 What Are Risk and Protective Factors? ............................................................................................................... 12 High Risk Groups and Subpopulations ................................................................................................................ 13 Evaluation ............................................................................................................................................................ 13 How Will Success Be Measured? ........................................................................................................................ -

PH-1 Cell Phone Texas Instrument Challenge
Robo Royals 67671C Malik C. PH-1 Cell Phone Texas Instrument Challenge I have disassembled an Essential Phone made by PH-1 with an Android operating system (it did not have any TI contents inside). I selected this device because I wanted to see the hardware behind the screen of the phone. Also, how hard it is to make a cell phone and how cell phones work and the components inside where the motherboard SOC, the battery, the heat shield, the font, and 2 back cameras, speaker, screen connector, USB-c, sim card, cell tower antenna capsules, Bluetooth antenna colonials, board connectors tray, 2H GHz antenna,5G Hz antenna, fingerprint reader, cell antenna. These are my research findings on each part of the system and what they do. The battery gives power to the phone. To replace the battery, you have to take off the screen and there is a large chance that it might break beyond repair. The heat shields It's there to protect the battery from too much heat to make sure the phone won't go on fire and if you don't put enough power. The front camera takes pictures of you it is also its own component and the 2 back cameras that take pictures in front of you the rear body also has a magnetic part for a camera add on and the front camera hadn't been there in the older version. Also the cameras have lenses that are made by Sony., the speaker plays sounds, the screen connector connects all of the layers of hardware to the screen such as the motherboard the various antennas such as the Bluetooth antennas, The USB-c can carry more power and gives an easier plugin for your phone than the Micro-USB port and cable (this is an improved charger), the cell tower antenna capsules let you connect to the nearest cell tower, Bluetooth antenna cables let you connect to Bluetooth services. -
Device Carrier Current Version Network Android
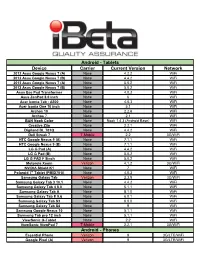
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel 3 XL None 9 3G/LTE/WiFi HTC Desire (International)