Lightweight Mutual Authentication Protocol for Low -Cost Rfid Tags
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Degree of Loop Assessment in Microvideo
DEGREE OF LOOP ASSESSMENT IN MICROVIDEO Shumpei Sano, Toshihiko Yamasaki, and Kiyoharu Aizawa Department of Information and Communication Engineering, The University of Tokyo 7-3-1 Hongo, Bunkyo-ku, Tokyo 113-8656, Japan fsano, yamasaki, [email protected] ABSTRACT Table 1. Ratio of loop/non-loop video in 1,022 microvideo This paper presents a degree-of-loop assessment method for on Vine with a tag “#loop”. microvideo clips. Loop video is one of the popular features non-loop video loop video in microvideo, but there are so many non-loop video tagged Number of video 906 116 with “loop” on microvideo services. This is because upload- Ratio 88.6 % 11.4 % ers or spammers also know that loop video is popular and they their official web site, Vine is introduced as “a mobile service want to draw attention from viewers. In this paper, we statisti- 5 cally analyze the scene dynamics of the video by using color, that lets you capture and share short looping video ,” there optical flow, saliency maps, and evaluate the degree-of-loop. are two characteristics in Vine. First is video length shortness. We have collected more than 1,000 video clips from Vine and Max video length in Vine is 6.5 seconds, which is shorter than subjectively evaluated their degree-of-loop. Experimental re- the other similar services. Second is looping. Shared video sults show that our proposed algorithm can classify loop/non- on Vine are automatically played repeatedly, and many loop loop video with 85.7% accuracy and categorize them into five video which seamlessly connect the last and the first frames degree-of-loop categories with 61.5% accuracy. -

Young Adult Library Services Association
THE OFFICIAL JOURNAL OF THE YOUNG ADULT LIBRARY SERVICES ASSOCIATION young adult 2012 library library services services VOLUME 13 | NUMBER 2 WINTER 2015 ISSN 1541-4302 $17.50 INSIDE: VOICES OF HOMELESS YOUTH: COMMUNITY PARTNERSHIPS IN LIBRARY TRAINING HAND IN HAND: TEENS, TECH, AND COMMUNITY ENGAGEMENT LIBRARIES ARE FOR ISSUE MAKING: ROBOTS TEENS & TECH AND MORE.... Their legacy is A Calling. An Honor. A Lie. “Secrets, danger, and romance meet in this unforgettable epic fantasy.” —KAMI GARCIA, #1 New York Times bestselling coauthor of Beautiful Creatures “A tightly-woven, action-packed story of survival and adventure, Seeker is perfect for fans of Game of Thrones.” —TAHEREH MAFI, New York Times bestselling author of Shatter Me Illustration © 2015 by Bose Collins; Photograph © 2015 Christopher Day/Shutterstock HC: 978-0-385-74407-2 • $18.99 GLB: 978-0-375-99148-6 • $21.99 Aud: 978-0-8041-6758-1 • $50.00 Lib. Aud: 978-0-8041-6760-4 • $50.00 Ages 14 up SeekerSeries.com #SeekerSeries The official journal of The Young adulT librarY ServiceS aSSociaTion young adult library services VOLUME 13 | NUMBER 2 Winter 2015 ISSN 1541-4302 YALSA Perspectives Plus: 4 In the Know: 2 From the Editor YALSA’s National Guidelines Oversight Committee Linda W. Braun By Katherine Trouern-Trend 3 From the President Chris Shoemaker 6 The Future of Library Services for and with Teens: 29 Guidelines for Authors A Call to Action 29 Index to Advertisers 9 YALSA Tune-up 30 The YALSA Update #act4teens 10 Voices of Homeless Youth: Community Partnerships in Library Training By Rekha Kuver Best Practices 13 An Interview with Jonathan Friesen About This Cover By Kris Hickey This Teen Tech Week™ (March 8–14, 2014), YALSA 15 Not as Crazy as It Seems: invites you to celebrate Libraries are for Making... -

Smart Content Providers
Smart Content Providers Video Audio Photos Products/Other #REKT Acast 23hq 23degrees ABC News Adori Labs Accredible 360 Panorama Adventr Allears Achewood 360 Stories Adways Anchor FM Altizure 3DCrafts Alkışlarla Yaşıyorum ART19 deviantART Abstract All Things Digital AudioBoom Dinosaur Comics Acebot.ai Altru Audiomack Dribbble Airtable Alugha Audm Droplr Allego Aniboom Ausha EyeEm Allihoopa Animoto Backtracks Flickr Alpaca Maps Athenascope Bandcamp gfycat Alpha Hat Bambuser BingeWith GifVif Apester Brightcove BlogAudio Giphy AppFollow Buto.tv Blogcast Img.ly Apple Keynote CANAL+ Bubbli Imgur ArcGIS StoryMaps Cayke Buzzsprout instagram Archilogic CBS News Cadence 13 Kuula ARCHIVOS Cinema8 Canva meadd Are.na Cinnamon Changelog Mobypicture AskMen Cincopa Chirbit Momento360 Autodesk Screencast Clip Syndicate Clyp Ow.ly Avocode Clipfish DNBRadio PanoMoments Bad Panda Clippit Flat Pexels Badgr CloudApp Free Music Archive photozou BadJupiter CNBC Genius pikchur Beautiful AI CNN Grooveshark Pollstar Behance CNN Edition Himalaya Publitio Bitmark CNN Money Huffduffer Questionable Content Blogsend.io College Humor iHeartRadio Represent BlueprintUE Confreaks Infinity.fm SmugMug Bootkik Coub Instaread Someecards Boston.com Crackle Last.fm The Hype Machine Box Office Buz Daily Motion Liberated Syndication Tinypic Brainshark Discovery Channel Listle tochka.net Brainsonic dotSUB Listen Notes TwitrPix BranchTrack Dream Broker Megafono uludağ sözlük galeri Bravo Tv DTube Megaphone.fm Vidme buk.io Embedded Mymixtapez Minilogs xkcd Buncee embedly Mixcloud Zoomable -

ANDRE AGASSI Reflections on Success Sisällysluettelo EXECUTIVE SUMMARY
EXECUTIVE SUMMARY 2017 3 WAYS BUILDING to Give UNICORNS Chad Hurley Feedback YouTube CREATE+ the Future Creativity as HOW TO a Roadmap SEE & SURF DISRUPTION Chip Conley AirBnB ANDRE AGASSI Reflections on Success Sisällysluettelo EXECUTIVE SUMMARY Table of Contents Intro Speaker Ratings LINDA LIUKAS KJELL NORDSTRÖM Humans, Computers, Weird, Wired World and Creativity SHEILA HEEN CHIP CONLEY IDA BACKLUND Identify Your Triggered Disruptive Hospitality How to Turn Rejection Reactions to Change the Into a Million-Dollar Way You Receive Business Feedback Partners See you in 2018! CHAD HURLEY ANDRE AGASSI How to Build a Unicorn From 1 to 141 and Back Again Sivu3 EXECUTIVE SUMMARY ~ Table of Contents Introduction Nordic Business Forum SWEDEN January 16, 2017 Stockholm, Sweden n its first year, Nordic Business Forum SWEDEN in Stockholm gathered over 1,000 CEOs, executives, entrepreneurs, and decision-makers from 19 na- Itionalities to the Waterfront Congress Centre. This Executive Summary takes you through all main stage presentations and offers you the key points from each speaker. The visual summaries from the presentations were drawn by Linda Saukko- Rauta. Sivu4 EXECUTIVE SUMMARY ~ Table of Contents Speaker Ratings GRADING SCALE 1 = WEAK – 6 = EXCELLENT 4.87 5.68 5.11 4.95 Linda Liukas Kjell A. Nordström Sheila Heen Chip Conley 3.02 4.65 5.55 Ida Backlund Chad Hurley Andre Agassi Sivu5 EXECUTIVE SUMMARY ~ Table of Contents LINDA LIUKAS Humans, Computers, and Creativity MIKE STURM Every Company Will Be a Technology Company inda Liukas stands on the stage of the Nordic Business Forum with a smile that competes with the house lights in terms of brightness. -

15. Mobile Learning Cochranev3
1 Chapter 15 Design Considerations for Mobile Learning Thomas Cochrane Auckland University of Technology Centre for Learning and Teaching Dr. Thomas Cochrane is an academic advisor and senior lecturer in educational technology at Auckland University of Technology's Centre for Learning and Teaching (CfLAT). In 2011 he was awarded as an Ascilite Fellow. His research interests include mobile learning, social media, and communities of practice. Thomas has implemented over 50 mobile learning projects, enabling student-generated content and student-generated learning contexts, bridging formal and informal learning environments. He has over 100 peer-reviewed publications, receiving best paper awards at Ascilite 2009, ALT-C 2011, ALT-C 2012, and has keynoted at several international educational technology conferences, and was an invited speaker at EdMedia2014 (Tampere, Finland). Vickel Narayan Auckland University of Technology Centre for Learning and Teaching Vickel Narayan is a learning and teaching consultant at the Centre for Learning and Teaching (CfLAT) at the Auckland University of Technology. Previously, Vickel was an academic advisor (eLearning) at Unitec Institute of Technology from 2009 to 2011. He has a keen interest in Web 2.0 technologies and their potential to engage students and teachers in the teaching and learning process. Vickel is particularly interested in exploring mobile Web 2.0 tools for creating, nurturing, and maintaining virtual communities, social connectedness, fostering social constructivism, student generated content and context. 2 Editors’ Foreword Preconditions (when to use the theory) Content • Subject areas in which digital communication and collaboration skills are necessary for producing artifacts for eportfolios. • Learners create, curate, and share content. Learners • All students. -
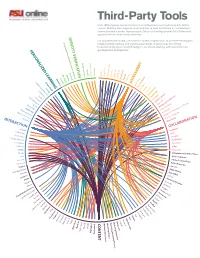
Third-Party Tools Over 100 3Rd Party Tools and Services Are Used by Faculty and Students in ASU Online Courses
Third-Party Tools Over 100 3rd party tools and services are used by faculty and students in ASU Online courses. With the 50+ companies indicated here in bold, ASU Online has established a connection with a vendor representative. These relationships provide ASU Online with opportunities to create true partnerships. IDENTITY VERIFICATION Collaborative partnerships are formed in order to explore ways to use the technology to Respondus ExamGuard (Lockdown Browser) improve online teaching and learning experiences. In some cases ASU Online Instructional Designers and Technologists are actively working with our partners to PERSONALIZED LEARNING guide product development. Software Secure Validator.w3.org vProctor Turnitin ProctorU Bio-Sig ID KeyTrac BibMe Blubbr TV Camtasia Studio Crocodoc Digication Acxiom Final Draft Knewton Grademark HapYak Jslint.com YouTube My WebCamChegg Study ASSESSMENT Mindomo Pearson Writer Cerego Plotagon VideoNot.es Quizlet Respondus VoiceThread Twitter SurveyMonkeyThinglink WebAssign YouSeeU Adobe Connect Remind101Skitch Appearin Blackboard Collaborate PollDaddy Poll Everywhere Camtasia Relay Pixxa Perspective Catme.org Google+ Communities and Circles INTERACTIONPinterest Google+ Hangouts OpenStudy COLLABORATION Piazza PeerMark Kwiksurveys Skype Google Glass StudyBlue Google Calendar StudyRoom FourSquare TweetChat Facebook Vidyo CritViz Wikispaces Citable 3Play Interactive Video Player Celtx Adobe Captivate Box.com Adobe Creative Cloud Adobe Presenter About.me Animoto Zaption Apple iAuthor YouTube Capture ApprenNet -

The Rise of Mobile and Social Short-Form Video: an In-Depth Measurement Study of Vine
The Rise of Mobile and Social Short-Form Video: An In-depth Measurement Study of Vine Baptist Vandersmissen Fr´edericGodin Multimedia Lab, ELIS, Ghent University Multimedia Lab, ELIS, Ghent University iMinds, Ghent, Belgium iMinds, Ghent, Belgium [email protected] [email protected] Wesley De Neve Abhineshwar Tomar 1Multimedia Lab, ELIS, Ghent University Multimedia Lab, ELIS, Ghent University iMinds, Ghent, Belgium iMinds, Ghent, Belgium 2Image and Video Systems Lab [email protected] KAIST, Daejeon, South Korea [email protected] Rik Van de Walle Multimedia Lab, ELIS, Ghent University iMinds, Ghent, Belgium [email protected] In addition, we can observe that a Vine video that is shared frequently on Twitter within Abstract hours after its creation will have more likes on Vine after one week, compared to a Vine Thanks to the increasing popularity of mobile video that is not shared frequently on Twit- devices and online social networks, mobile and ter during this same period of time. However, social video is on the rise, calling for a better we cannot establish a clear link between the understanding of its usage and future impact. number of tweets sharing a Vine video and In this paper, we provide an in-depth measure- its resulting popularity. Finally, by analyzing ment study of Vine, a mobile application that the evolution of the number of likes and the is used for creating and sharing short looping number of shares received by a Vine video on videos of up to six seconds in length. Based on Vine and Twitter, respectively, we can con- a dataset of 851,039 tweets containing a Vine clude that a Vine video receives most user URL, we investigate different aspects of Vine, attention shortly after its creation, with the including hashtag usage, video popularity and amount of user attention received not stop- user attention. -

BM Technologies, Inc. (Exact Name of Registrant As Specified in Its Charter)
As filed with the Securities and Exchange Commission on February 12, 2021 Registration No. 333- UNITED STATES SECURITIES AND EXChANGE COMMISSION Washington, D.C. 20549 FORM S-1 REGISTRATION STATEMENT UNDER THE SECURITIES ACT OF 1933 BM Technologies, Inc. (Exact name of registrant as specified in its charter) Delaware 7389 82-310369 (State or other jurisdiction of (Primary Standard Industrial (I.R.S. Employer incorporation or organization) Classification Code Number) Identification No.) 201 king of Prussia Road, Suite 350 Wayne, PA 19087 (Address, including zip code, and telephone number, including area code, of registrant’s principal executive office) Luvleen Sidhu Chief Executive Officer 201 king of Prussia Road, Suite 350 Wayne, PA 19087 (Name, address, including zip code, and telephone number, including area code, of agent for service) Copies to: Jonathan h. Talcott E. Peter Strand Nelson Mullins Riley & Scarborough LLP 101 Constitution Avenue, NW, Suite 900 Washington, DC 20001 (202) 689-2806 Approximate date of commencement of proposed sale to the public: As soon as practicable after the effective date of this registration statement. If any of the securities being registered on this Form are to be offered on a delayed or continuous basis pursuant to Rule 415 under the Securities Act of 1933, check the following box. ☐ If this Form is filed to register additional securities for an offering pursuant to Rule 462(b) under the Securities Act, check the following box and list the Securities Act registration statement number of the earlier effective registration statement for the same offering. ☐ If this Form is a post-effective amendment filed pursuant to Rule 462(c) under the Securities Act, check the following box and list the Securities Act registration statement number of the earlier effective registration statement for the same offering. -

India Business Quiz
India Business Quiz Business- Quizzes, News and more • Home • About • Global brands • Indian Brands • Indian Brands- II • Jargon buster • Visuals Weekly Business Quiz # 202 October 9, 2013 businessbaatein Uncategorized Brands, Business, India, quiz Leave a comment Q1. Which small town in USA is home to 67 Coca Cola millionaires who have been buying Coke shares since 1920s and have kept with them ? Ans. Quincy, Florida Q 2. Which healthcare venture is funded by Azim Premji in his personal capacity ? Ans. Health Care Global Q 3. Which PSU had supplied critical equipment for LHC thereby deserving some credit for the Nobel prize in Physics this year ? Ans. ECIL Q4. Which brand has replaced Thums Up as the largest selling soft drink in India ? Ans. Sprite Q5. Besides being Public sector banks what is common to Bank of India, Allahabad Bank, United Bank and SBI ? Ans. CMDs are women Q6. Which co recently lost its reign over the purple colour in a UK court against Nestle ? Ans. Cadbury ( Mondelez) Q7. After Enron went bust who owns and runs the infamous Dabhol power plant ? Ans. Ratnagiri Gas and Power Ltd , a JV of NTPC and GAIL Q8. Which cricketer will replace Dhoni as the new face of Big Bazaar ? Ans. Shikhar Dhawan Q9. What is ‘ Latte Art’ ? Ans. Art made on coffee cup while poring cream over coffee Q 10. After China which country stands No 2 as a.shoemaker of the world ? Ans. Vietnam Q 11Match the messaging apps to the country of their origin a. Line b. Whatsapp c. WeChat 1. -

Marketing Digital Ramos Reyes Washington David Salgado Chasipanta Diana Jazmin Moreno Cueva Neima Yadira Vera Campuzano Nury Ruth
RAMOS REYES WASHINGTON DAVID SALGADO CHASIPANTA DIANA JAZMIN MORENO CUEVA NEIMA YADIRA VERA CAMPUZANO NURY RUTH MARKETING DIGITAL RAMOS REYES WASHINGTON DAVID SALGADO CHASIPANTA DIANA JAZMIN MORENO CUEVA NEIMA YADIRA VERA CAMPUZANO NURY RUTH MARKETING DIGITAL RAMOS REYES WASHINGTON DAVID SALGADO CHASIPANTA DIANA JAZMIN MORENO CUEVA NEIMA YADIRA VERA CAMPUZANO NURY RUTH Experiencia académica: Docentes del Instituto Superior Tecnológico Corporativo Edwards Deming. MARKETING DIGITAL Editado por Colloquium ISBN: 978-9942-814-50-0 Primera edición 2019 © Instituto Superior Tecnológico Corporativo Edwards Deming. © Colloquium La obra fue revisada por pares académicos antes de su proceso editorial, en caso de requerir certificación debe solicitarla a: [email protected] Quedan rigurosamente prohibidas, bajo las sanciones en las leyes, la producción o almacenamiento total o parcial de la presente publicación, incluyendo el diseño de la portada, así como la transmisión de la misma por cualquiera de sus medios, tanto si es electrónico, como químico, mecánico, óptico, de grabación o bien de fotocopia, sin la autorización de los titulares del copyright. Ecuador 2019 RAMOS REYES WASHINGTON DAVID SALGADO CHASIPANTA DIANA JAZMIN MORENO CUEVA NEIMA YADIRA VERA CAMPUZANO NURY RUTH MARKETING DIGITAL Contenido Introducción .................................................................................. 4 Capítulo I ........................................................................................ 5 Marketing digital ........................................................................... -

Digital Media Magazine.Cdr
December 2020 | Edition 21 | Special Edition Digital Media Digital Media Trending Discover the Future of Media Follow us on: www.mescindia.org Disclaimer - Media Talk Back is a non-commercial magazine covering insights of Influential Industry Experts and highlighting the opportunities for aspiring candidates/professionals. Images and Copyright content if any used in this magazine is the proprietary of relevant organisations, companies, source. They are being solely used for the purpose of transmitting information and for no monetary value. TABLE OF CONTENT 01 What is Digital Media The Impact of Digital Media Career Opportunities and Employability 02 10 Options in DigitalSocial Media Sector The Irreplaceable 03 Digital Media Influential Insights from Incredible Industry Experts The Irreplaceable 11 04 Digital Marketing Tips to Become an Internet Celebrity Social Media Platforms 12 05 Running the World Inspiring Stories and Advices with Social Media Marketing 13 Internet Celebrities and Sensational 06 Tools and Strategies Figures 07 Types of Social Media Ads Advantages of Social Media 08 Marketing Digital Marketing VS 09 Social Media Marketing Covering for the first time ever. Showcase Section highlighting Excellent Brand Design Tips Digital Marketing Industry with with Mr. Dain Walker. Mr. Chris Do , First time on Media Talk Back. Chance to Grab Influential Chance to learn from the Incredibly Insights of Mr. Ujjawal Trivedi Talented Key Animator of Ramayana - on Digital Media. The Legend of Prince Rama and Co-founder40 of Doga Kobo Studio Mr. Megumu Ishiguro MESSAGE FROM CHAIRMAN Known as a Showman of Indian Cinema; Mr. Ghai is an Indian Film Maker, producer, Director, Script Write r, renowned Educationist. -

Social Media Apps Cheat Sheet 2015
Social Media Apps Cheat Sheet 2015 APP Description $ iPad Android Pinterest Virtual Pinboard to share ideas Free X X Tumblr Interactive blog Free X X LinkedIn Keep up with your professional contacts Free X X Facebook The largest social media site Free X X Facebook If you don’t want to log into Facebook but Free X X Messenger just get notifications. Facebook Pages Helps you manage activity on your Free X X Manager Facebook pages Slingshot Facebook version of snapchat Free X X LiveJournal Meet people through blogging Free X X Google+ Combine all your Google apps in 1 Free X X Twitter Updates in 140 characters or less Free X X TweetBot3 Works with Twitter $0-5 X O TweetCaster Works with Twitter $0-5 X X Twitterific 5 Works with Twitter Free X Osfoora2 Works with Twitter $3 X UberSocial Swiss army knife for Twitter $0-5 X X Find Unfollowers Tracks un/followers on Twitter $0-1 X X Bebo Former social network, now avatar creator Free X X Instagram Edit & share photos Free X X Snapchat Snap a pic & share the moment chatting Free X X Photobucket Share photos to TW & FB Free X X Flickr Share & organize photos online Free X X SnapCrack Works with SnapChat $0-3 X Oggl Share photos Free X Hipstamatic Take retro looking photos $0-2 X O Storehouse / Combine photos & videos to create stories Free X O Picmotion Followers + Track un/followers for Instagram Free X X Followers + Track un/followers for Twitter $0-1 X X AllSync Synchronize followers/friends from Twitter $0-2 X O & FaceBook Vine Create & share video clips Free X X MixBit Create & share video