Framing the System Replacement Decision: a Library Illustration
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

ISO/TC46 (Information and Documentation) Liaison to IFLA
ISO/TC46 (Information and Documentation) liaison to IFLA Annual Report 2015 TC46 on Information and documentation has been leading efforts related to information management since 1947. Standards1 developed under ISO/TC46 facilitate access to knowledge and information and standardize automated tools, computer systems, and services relating to its major stakeholders of: libraries, publishing, documentation and information centres, archives, records management, museums, indexing and abstracting services, and information technology suppliers to these communities. TC46 has a unique role among ISO information-related committees in that it focuses on the whole lifecycle of information from its creation and identification, through delivery, management, measurement, and archiving, to final disposition. *** The following report summarizes activities of TC46, SC4, SC8 SC92 and their resolutions of the annual meetings3, in light of the key-concepts of interest to the IFLA community4. 1. SC4 Technical interoperability 1.1 Activities Standardization of protocols, schemas, etc. and related models and metadata for processes used by information organizations and content providers, including libraries, archives, museums, publishers, and other content producers. 1.2 Active Working Group WG 11 – RFID in libraries WG 12 – WARC WG 13 – Cultural heritage information interchange WG 14 – Interlibrary Loan Transactions 1.3 Joint working groups 1 For the complete list of published standards, cfr. Appendix A. 2 ISO TC46 Subcommittees: TC46/SC4 Technical interoperability; TC46/SC8 Quality - Statistics and performance evaluation; TC46/SC9 Identification and description; TC46/SC 10 Requirements for document storage and conditions for preservation - Cfr Appendix B. 3 The 42nd ISO TC46 plenary, subcommittee and working groups meetings, Beijing, June 1-5 2015. -

Označením a Třídicím Znakem Uvedeným Níže (Tyto Normy Se Přejímají Pouze Tímto Oznámením Bez Vydání Titulní Strany ČSN Tiskem)
ÚŘADU PRO TECHNICKOU NORMALIZACI, METROLOGII A STÁTNÍ ZKUŠEBNICTVÍ Číslo 2/99 OBSAH: ČÁST A - OZNÁMENÍ Oddíl 1. České technické normy ČSNI č.10/99 o vydání českých technických norem, jejich změn, oprav a zrušení str. Upozornění redakce str. ČSNI č.11/99 o schválení evropských a mezinárodních norem k přímému používání jako ČSN str. ČSNI č.12/99 o veřejném projednání návrhů norem ETSI str. ČSNI č 13/99 o vydání norem ETSI str. ČSNI č.14/99 o návrzích na zrušení ČSN str. ČSNI č.15/99 o úkolech tvorby norem zařazených do plánu str. ČSNI č. /99 o schválených EN normách a jiných dokumentech (CENELEC) - viz příloha str. ČSNI č. /99 o veřejném projednání norem EN (CENELEC) - viz příloha str. Oddíl 2. Metrologie Oddíl 3. Autorizace ÚNMZ č. 3/99 o zajištění posuzování shody prostředků zdravotnické techniky autorizovanými osobami str. Oddíl 4. Akreditace ČIA č. 2/99 o vydání osvědčení o akreditaci a o ukončení platnosti osvědčení o akreditaci str. Oddíl 5. Notifikace ÚNMZ č.2/99 Informačního střediska WTO o notifikacích Členů Dohody mezi státy ESVO a ČR a smluvních stran str. Oddíl 6. Ostatní oznámení ČÁST B - SDĚLENÍ ČÁST C - PŘEVZATÉ INFORMACE Oznámení ESČ o schválení a vydání Předpisu Elektrotechnického svazu českého podle čl. 4. odst. 6 stanov ESČ str. ČÁST A - OZNÁMENÍ Oddíl 1 – České technické normy OZNÁMENÍ č.10/99 Českého normalizačního institutu o vydání ČSN, jejich změn, oprav a zrušení Český normalizační institut podle § 4 zákona č. 22/1997 Sb., oznamuje, že byly vydány, změněny, opraveny nebo zrušeny dále uvedené ČSN: VYDANÉ ČSN 1. -

Gestão De Projeto E Produção De Uma Ponte Ferroviária Em Estrutura Metálica
Gestão de projeto e produção de uma ponte ferroviária em estrutura metálica RAFAEL TIAGO FERRAZ DE AZEVEDO novembro de 2019 GESTÃO DE PROJETO E PRODUÇÃO DE UMA PONTE FERROVIÁRIA EM ESTRUTURA METÁLICA Rafael Tiago Ferraz de Azevedo 1140520 2019 Instituto Superior de Engenharia do Porto Departamento de Engenharia Mecânica GESTÃO DE PROJETO E PRODUÇÃO DE UMA PONTE FERROVIÁRIA EM ESTRUTURA METÁLICA Rafael Tiago Ferraz de Azevedo 1140520 Dissertação apresentada ao Instituto Superior de Engenharia do Porto para cumprimento dos requisitos necessários à obtenção do grau de Mestre em Engenharia Mecânica, realizada sob a orientação do Doutor Raul Duarte Salgueiral Gomes Campilho, Professor adjunto do Departamento de Engenharia Mecânica do ISEP. 2019 Instituto Superior de Engenharia do Porto Departamento de Engenharia Mecânica JÚRI Presidente Doutor Luís Carlos Ramos Nunes Pinto Ferreira Professor Adjunto, Instituto Superior de Engenharia do Porto Orientador Doutor Raul Duarte Salgueiral Gomes Campilho Professor Adjunto, Instituto Superior de Engenharia do Porto Arguente Doutor Paulo Manuel Salgado Tavares de Castro Professor Catedrático, Faculdade de Engenharia da Universidade do Porto GESTÃO DE PROJETO E PRODUÇÃO DE UMA PONTE FERROVIÁRIA EM ESTRUTURA METÁLICA RAFAEL TIAGO FERRAZ DE AZEVEDO AGRADECIMENTOS Em primeiro lugar, gostava de deixar o meu sincero agradecimento à empresa Metalongo – Metalúrgica de Valongo, SA por me ter recebido da melhor forma possível durante todo o período de estágio. A todos os seus colaboradores, principalmente do departamento técnico pela disponibilidade e apoio prestado e em particular ao Eng.º Pedro Bastos, orientador de estágio, por me ter dado esta oportunidade. Ao orientador do ISEP, Doutor Raul Campilho, pela disponibilidade demonstrada e pelo excelente acompanhamento que faz aos alunos. -

Iqlrdky; ,Oa Lwpuk Fokku 'Kcnkoyh ¼Vaxzst+H-Fgunh½
Glossary of Terms in Library and Information Science (English - Hindi) iqLrdky; ,oa lwpuk foKku 'kCnkoyh ¼vaxzst+h-fgUnh½ Revised Edition (2018) la'kksf/kr laLdj.k ¼2018½ Faculty of Library and Information Science School of Social Sciences Indira Gandhi National Open University Maidan Garhi, New Delhi-110068 Terminology Preparation Committee (1999) Prof. S.B. Ghosh (Chairperson) Dr. Pandey S.K. Sharma Faculty of Lib. & Inf. Sc. Chief Librarian University Grants IGNOU, New Delhi-110068 Commission New Delhi-110017 Dr. S. R. Gupta Dr. J.P.Singh Reader Scientist ‘D’ Dept. of Lib. & Inf. Sc. DESIDOC University of Delhi Delhi-110054 Delhi-110054 Dr. S.P.Sood Dr. Neela Jagannathan Former Reader University Librarian & Dept. of Lib. & Inf. Sc. Information Officer University of Rajasthan IGNOU, New Delhi-110068 Jaipur-302004 Dr. Uma Kanjilal Dr. U.M.Thakur Reader University Librarian Faculty of Lib. & Inf. Sc. Patna University, Patna IGNOU, New Delhi-110068 Prof. S.M. Tripathi Dr. Reeta Rani Paliwal Former Dean, Faculty of Arts Reader, SOH Jiwaji University, IGNOU, New Delhi-110068 Gwalior-474002 Dr. Pravakar Rath Prof. C.P.Vashisht Sr. Lecturer Dept. of Lib. & Inf. Sc. Faculty of Lib. & Inf. Sc. University of Delhi, Delhi-110007 IGNOU, New Delhi-110068 Dr. Neena Talwar Kanungo Prof. R.Satyanarayana (Coordinator) Faculty of Lib. & Inf. Sc. Sr. Lecturer IGNOU, New Delhi-110068 Faculty of Lib. & Inf. Sc. IGNOU, New Delhi-110068 Terminology Preparation Committee (2018) Prof. Swaraj Basu Prof. Neena Talwar Kanungo Director Faculty of Lib. & Inf. Sc. School of Social Sciences IGNOU, New Delhi-110068 Faculty of History IGNOU, New Delhi-110068 Prof. -

Modern Library and Information Science
MCQs for LIS ABBREVIATIONS, ACRONYMS 1. What is the full form of IATLIS? (a) International Association of Trade Unions of Library & Information Science (b) Indian Association of Teachers in Library & Information Science (c) Indian Airlines Technical Lower Intelligence Services (d) Indian Air Traffic Light Information and Signal 2. IIA founded in USA in 1968 stands for (a) Integrated Industry Association (b) Information Industry Association (c) Integrated Illiteracy eradication Association (d) Institute of Information Association 3. BSO in classification stands for (a) Basic Subject of Organisation (b) Broad System of Ordering (c) Bibliography of Subject Ordering (d) Bibliographic Subject Organisation 4. IPR stands for (a) Indian Press Registration (b) Intellectual Property Right (c) International Property Right (d) Indian Property Regulations 5. NAAC stands for (a) National Accreditation and Authority Council (b) Northern Accreditation and Authorities Committee (c) National Assessment and Accreditation Council (d) Northern Assessment and Accreditation Council 6. ACRL 1 Dr . K.Kamila & Dr. B.Das MCQs for LIS (a) Association of College and Research Libraries (b) All College and Research Libraries (c) Academic Community Research Libraries 7. CILIP (a) Chartered Institute of Library and Information Professionals (b) Community Institute for Library and Information Programmes (c) College level Institute for Library and Information Programmes (d) Centre for Indian Library and Information Professionals 8. SCONUL (a) Society of College National and University Libraries (previously Standing Conference of National and University Libraries) (b) School College National and University Libraries (c) Special Council for National and University Libraries (d) None of these 9. NISCAIR (a) National Institute of Science Communication and Information Resources (b) National Institute of Scientific Cultural and Industrial Research (c) National Institute of Social Cultural and Industrial Research (d) None of the above 10. -

Internet, Interoperability and Standards – Filling the Gaps
Internet, Interoperability and Standards – Filling the Gaps Janifer Gatenby European Product Manager Geac Computers [email protected] Abstract: With major changes in electronic communications, the main focus of standardisation in the library arena has moved from that of supporting efficiency to allowing library users to access external resources and allowing remote access to library resources. There is a new emphasis on interoperability at a deeper level among library systems and on a grander scale within the environment of electronic commerce. The potential of full inter-operability is examined along with its likely impact. Some of the gaps in current standards are examined, with a focus on information retrieval, together with the process for filling those gaps, the interoperation of standards and overlapping standards. Introduction Libraries now find themselves in a very new environment. Even though they have always co-operated with one another and have led standards efforts for decades, their inter- operability has been at arm's length via such means as store and forward interlibrary loans and electronic orders. The initial goals of standardisation were to increase efficiency, e.g. by exchanging cataloguing, by electronic ordering and only secondarily to share resources. Initial standards efforts in libraries concentrated on record exchange as part of the drive to improve efficiency by sharing cataloguing. This led to a raft of bibliographic standards concentrating on: the way in which catalogue records are made (contents - cataloguing rules such as AACR2, classification schemes, subject headings, name headings) how they are identified (LC card number, ISBN, ISSN etc.) how they are structured for exchange (MARC) Viewing library standardisation chronologically, acquisitions was the next area where libraries strove to increase efficiency co-operatively. -

A Könyvtárüggyel Kapcsolatos Nemzetközi Szabványok
A könyvtárüggyel kapcsolatos nemzetközi szabványok 1. Állomány-nyilvántartás ISO 20775:2009 Information and documentation. Schema for holdings information 2. Bibliográfiai feldolgozás és adatcsere, transzliteráció ISO 10754:1996 Information and documentation. Extension of the Cyrillic alphabet coded character set for non-Slavic languages for bibliographic information interchange ISO 11940:1998 Information and documentation. Transliteration of Thai ISO 11940-2:2007 Information and documentation. Transliteration of Thai characters into Latin characters. Part 2: Simplified transcription of Thai language ISO 15919:2001 Information and documentation. Transliteration of Devanagari and related Indic scripts into Latin characters ISO 15924:2004 Information and documentation. Codes for the representation of names of scripts ISO 21127:2014 Information and documentation. A reference ontology for the interchange of cultural heritage information ISO 233:1984 Documentation. Transliteration of Arabic characters into Latin characters ISO 233-2:1993 Information and documentation. Transliteration of Arabic characters into Latin characters. Part 2: Arabic language. Simplified transliteration ISO 233-3:1999 Information and documentation. Transliteration of Arabic characters into Latin characters. Part 3: Persian language. Simplified transliteration ISO 25577:2013 Information and documentation. MarcXchange ISO 259:1984 Documentation. Transliteration of Hebrew characters into Latin characters ISO 259-2:1994 Information and documentation. Transliteration of Hebrew characters into Latin characters. Part 2. Simplified transliteration ISO 3602:1989 Documentation. Romanization of Japanese (kana script) ISO 5963:1985 Documentation. Methods for examining documents, determining their subjects, and selecting indexing terms ISO 639-2:1998 Codes for the representation of names of languages. Part 2. Alpha-3 code ISO 6630:1986 Documentation. Bibliographic control characters ISO 7098:1991 Information and documentation. -

Online Development in the Nordic Countries
Online development in the Nordic countries A history of online information from the 1960s to the ‘00s and NORDINFO’s role in its development Elisabet Mickos (†), Teodora Oker-Blom, Marie Wallin, Lars Klasén, Aud Lamvik and Ulla Retlev (Eds.) Helsinki 2018 Online development in the Nordic countries A history of online information from the 1960s to the ‘00s and NORDINFO’s role in its development Elisabet Mickos (†), Teodora Oker-Blom, Marie Wallin, Lars Klasén, Aud Lamvik and Ulla Retlev (Eds.) i Online development in the Nordic countries © The editors Published 2018 by the editors Teodora Oker-Blom (Finland), Marie Wallin (Sweden), Lars Klasén (Sweden), Aud Lamvik (Norway) and Ulla Retlev (Denmark) Graphic design by Lars Klasén (Sweden) The publishing process began as a project within NORDINFO - the Nordic Council for Scientific Information. NORDINFO was closed down in 2004 and the editors had to take the responsibility of completing the project by publishing this book. Some of the contributions to this book have previously been published as manuscripts in 2007. See: URI http://hdl.handle.net/1975/1490 ISBN 978-952-94-0548-0 (PDF) URI http://hdl.handle.net/10138/235272 Licencees may copy, distribute, display, and perform only verbatim copies of the work, not derivative works and remixes based on it. The book is published under a Creative Commons Attribution Non-derivative licence (CC BY-ND 4.0). ii Online development in the Nordic countries Contents Foreword, acknowledgements Marie Wallin & Teodora Oker-Blom ...................................... v Acronyms, abbreviations and technical terms ......................................................................... viii 1 INTRODUCTION. ONLINE SERVICES - PAST AND PRESENT IN A NORDIC AND INTERNATIONAL PERSPECTIVE Sauli Laitinen ........................................... -

ANSI/NISO Z39.50-2003 Information Retrieval Application Service Definition and Protocol Specification
ANSI/NISO Z39.50-2003 ISSN: 1041-5653 (revision of Z39.50-1995) Information Retrieval (Z39.50): Application Service Definition and Protocol Specification Abstract: This standard defines a client/server based service and protocol for Information Retrieval. It specifies procedures and formats for a client to search a database provided by a server, retrieve database records, and perform related information retrieval functions. The protocol addresses communication between information retrieval applications at the client and server; it does not address interaction between the client and the end-user. An American National Standard Developed by the National Information Standards Organization Approved November 27, 2002 by the American National Standards Institute Published by the National Information Standards Organization Bethesda, Maryland NISO Press, Bethesda, Maryland, U.S.A. ©NISO Published by NISO Press 4733 Bethesda Avenue, Suite 300 Bethesda, MD 20814 www.niso.org Copyright ©2003 by the National Information Standards Organization All rights reserved under International and Pan-American Copyright Conventions. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopy, recording, or any information storage or retrieval system, without prior permission in writing from the publisher. All inquiries should be addressed to NISO Press, 4733 Bethesda Avenue, Suite 300, Bethesda, MD 20814. Printed in the United States of America ISSN: 1041-5653 National Information Standard Series ISBN: 1-880124-55-6 ¥ This paper meets the requirements of ANSI/NISO Z39.48-1992 Permanence of Paper. Library of Congress Cataloging-in-Publication Data National Information Standards Organization (U.S.) Information retrieval (Z39.50) : application service definition and protocol specification : an American national standard / developed by the National Information Standards Organization. -

Standards Available in Electronic Format (PDF) Page 1
Standards available in electronic format (PDF) August 2019 SANS Number Edition Title SANS 1-2:2013 2 Standard for standards Part 2: Recognition of Standards Development Organizations (SDOs) in South Africa SATS 2:2012 1 The development of normative documents other than South African National Standards SANS 2:2013 7.01 Lead-acid starter batteries (SABS 2) SANS 4:2008 3.03 Locks, latches, and associated furniture for doors (SABS 4) (Domestic Type) SANS 11:2007 1.02 Unplasticized poly(vinyl chloride) (PVC-U) (SABS 11) components for external rainwater systems SANS 13:2008 2.03 Wax polish, solvent-based, for floors and furniture (SABS 13) SANS 14:1994/ISO 49:1994, IDT, Ed. 2 1 Malleable cast iron fittings threaded to ISO 7-1 (SABS ISO 49) SANS 15:2008 2.03 Wax emulsion polish for floors and furniture (SABS 15) SANS 16:2007/ISO/IEC 10116:2006, IDT, Ed. 3 2 Information technology - Security techniques - Modes of operation for an n-bit block cipher SANS 17:2014 1.01 Glass and plastics in furniture SANS 18-1:2003/ISO/IEC 10118-1:2000, IDT, Ed. 2 1 Information technology - Security techniques - Hash- functions Part 1: General SANS 18-2:2011/ISO/IEC 10118-2:2010, IDT, Ed. 3 2 Information technology - Security techniques - Hash- functions Part 2: Hash-functions using an n-bit block cipher SANS 18-3:2007/ISO/IEC 10118-3:2004, IDT, Ed. 3 2 Information technology - Security techniques - Hash- functions Part 3: Dedicated hash-functions SANS 18-4:2003/ISO/IEC 10118-4:1998, IDT, Ed. -

Isqv27no1.Pdf
INFORMATION STANDARDS QUARTERLY SPRING 2015 | VOL 27 | ISSUE 1 | ISSN 1041-0031 TOPIC YEAR IN REVIEW AND STATE OF THE STANDARDS NISO 2014 YEAR IN REVIEW TC46 2014 YEAR IN REVIEW THE FUTURE OF LIBRARY RESOURCE DISCOVERY STATE OF THE STANDARDS NEW for 2015: NISO Training Thursdays A technical webinar for those wanting more in-depth knowledge. Free with registration to the related Virtual Conference or register separately. UPCOMING 2015 EDUCATIONAL EVENTS APRIL JUNE OCTOBER 8 Experimenting with BIBFRAME: 10 Taking Your Website Wherever 1 Using Alerting Systems to Reports from Early Adopters You Go: Delivering Great User Ensure OA Policy Compliance (Webinar) Experience to Multiple Devices (Training Thursday) 29 Expanding the Assessment (Webinar) 14 Cloud and Web Services for Toolbox: Blending the Old 17 The Eternal To-Do List: Making Libraries (Webinar) and New Assessment Practices E-books Work in Libraries 28 Interacting with Content: (Virtual Conference) (Virtual Conference) Improving the User Experience 26 NISO/BISG The Changing (Virtual Conference) MAY Standards Landscape (In-person Forum) 7 Implementing SUSHI/ NOVEMBER COUNTER at Your Institution JULY 18 Text Mining: Digging Deep for (Training Thursday) Knowledge (Webinar) 13 Software Preservation and Use: No events in July I Saved the Files But Can I Run DECEMBER Them? (Webinar) AUGUST 2 The Semantic Web: What’s New 20 Not Business as Usual: 12 MOOCs and Libraries: and Cool (Virtual Conference) Special Cases in RDA Serials A Brewing Collaboration NISO December Two-Part Webinar: Cataloging (NISO/NASIG (Webinar) Joint Webinar) Emerging Resource Types SEPTEMBER 9 Part 1: Emerging Resource Types NISO September Two-Part Webinar: 16 Part 2: Emerging The Practicality of Managing “E” NISO Open Teleconferences Resource Types 9 Part 1: Licensing Join us each month for NISO’s Open 16 Part 2: Staffing Teleconferences—an ongoing series of calls held on the second Monday 23 Scholarly Communication of each month as a way to keep Models: Evolution the community informed of NISO’s or Revolution? activities. -
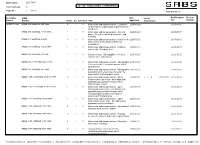
2021-07-07 Report Date : Cost Centre(S)
Report Date : 2021-09-17 Cost Centre(s) : % LIST OF PUBLISHED STANDARDS Page No : 1 Of 5 Total Count: 67 Committee SANS Date Latest Reaffirmation Review/ Number Number Int Ed Ed Sansified Title Approved Amendment due Revision SABS/TC 046 SANS 438:2005/ISO 999:1996 2 1 Y Information and documentation - Guidelines 2005-10-28 2015-08-27 for the content, organization and presentation of indexes SANS 480:2006/ISO 11108:1996 1 1 Y Information and documentation - Archival 2006-03-24 2025-07-17 paper - Requirements for permanence and durability SANS 531:2007/ISO 4:1997 3 1 Y Information and documentation - Rules for the 2007-05-25 2017-03-16 abbreviation of title words and titles of publications SANS 618:2009/ISO 10324:1997 1 1 Y Information and documentation - Holdings 2009-03-13 2014-03-13 statements - Summary level SANS 690:2007/ISO 690:1987 2 1 Y Documentation - Bibliographic references - 2007-05-25 2012-05-25 Content, form and structure SANS 690-2:2007/ISO 690-2:1997 1 1 Y Information and documentation - Bibliographic 2007-05-25 2012-05-25 references Part 2: Electronic documents or parts thereof SANS 832:2007/ISO 832:1994 2 1 Y Information and documentation - Bibliographic 2007-05-25 2018-01-25 description and references - Rules for the abbreviation of bibliographic terms SANS 1105-1:2010/ISO 10161-1:1997 2 1 Y Information and documentation - Open 2010-10-01 2 I A 2010-10-01 2015-10-01 Systems Interconnection - Interlibrary loan application protocol specification Part 1: Protocol specification SANS 1105-2:2011/ISO 10161-2:1997 1 1 Y Information