WEIS 2016 Paper 43-1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
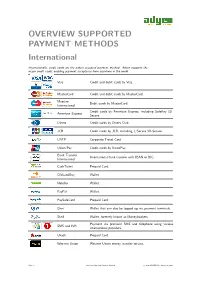
OVERVIEW SUPPORTED PAYMENT METHODS International
OVERVIEW SUPPORTED PAYMENT METHODS International Internationally, credit cards are the widest accepted payment method. Adyen supports the major credit cards, enabling payment acceptance from anywhere in the world. Visa Credit and debit cards by Visa. MasterCard Credit and debit cards by MasterCard. Maestro Debit cards by MasterCard. International Credit cards by American Express, including SafeKey 3D- American Express Secure. Diners Credit cards by Diners Club. JCB Credit cards by JCB, including J/Secure 3D-Secure. UATP Corporate Travel Card. Union Pay Credit cards by UnionPay. Bank Transfer International bank transfer with IBAN or BIC. International CashTicket Prepaid Card. ClickandBuy Wallet. Neteller Wallet. PayPal Wallet. PaySafeCard Prepaid Card. Qiwi Wallet that can also be topped up via payment terminals. Skrill Wallet, formerly known as Moneybookers. Payment via premium SMS and telephone using various SMS and IVR international providers. Ukash Prepaid Card. Western Union Western Union money transfer service. Page 1 Overview Supported Payment Methods c 2012 ADYEN BV - August 23, 2012 Europe Loyalty cards Support for various loyalty and store cards. Austria Bank Transfer Offline bank transfer. Sofortbanking Online banking supporting various local banks. Belgium Bank Transfer Offline bank transfer. BanContact / Mr. Debit card in Belgium. Cash Sofortbanking Online banking supporting various local banks. Denmark Primarily credit card and the local debit scheme. Bank Transfer Offline bank transfer. Dankort Local debit card scheme. Open Invoice Payments on credit by open invoice. Finland Primarily Credit Card. Besides this there is a very good market share for online banking. Bank Transfer Offline bank transfer. Ålandsbanken Online banking. Handelsbanken Online banking. Nordea Online banking. -

Notes 12 Bibliography 13
Bringing E-money to the Poor E-money to Bringing Public Disclosure Authorized Public Disclosure Authorized DIRECTIONS IN DEVELOPMENT Finance Riley and Kulathunga Bringing E-money to the Poor Public Disclosure Authorized Successes and Failures Thyra A. Riley and Anoma Kulathunga Public Disclosure Authorized Bringing E-money to the Poor DIRECTIONS IN DEVELOPMENT Finance Bringing E-money to the Poor Successes and Failures Thyra A. Riley and Anoma Kulathunga © 2017 International Bank for Reconstruction and Development / The World Bank 1818 H Street NW, Washington, DC 20433 Telephone: 202-473-1000; Internet: www.worldbank.org Some rights reserved 1 2 3 4 20 19 18 17 This work is a product of the staff of The World Bank with external contributions. The findings, interpreta- tions, and conclusions expressed in this work do not necessarily reflect the views of The World Bank, its Board of Executive Directors, or the governments they represent. The World Bank does not guarantee the accuracy of the data included in this work. The boundaries, colors, denominations, and other information shown on any map in this work do not imply any judgment on the part of The World Bank concerning the legal status of any territory or the endorsement or acceptance of such boundaries. Nothing herein shall constitute or be considered to be a limitation upon or waiver of the privileges and immunities of The World Bank, all of which are specifically reserved. Rights and Permissions This work is available under the Creative Commons Attribution 3.0 IGO license (CC BY 3.0 IGO) http:// creativecommons.org/licenses/by/3.0/igo. -

Overcoming Fragmentation – the Payments Platform Challenge OVERCOMING FRAGMENTATION – the PAYMENTS PLATFORM CHALLENGE
Overcoming Fragmentation – The Payments Platform Challenge OVERCOMING FRAGMENTATION – THE PAYMENTS PLATFORM CHALLENGE CONTENTS 1. Overcoming the Fragmented Payment Landscape with Open Payment Platforms 03 1.1 Executive Summary 03 2. About Key Payment Markets 04 2.1 Payment Market Characteristics in the USA 05 2.2 Payment Market Characteristics in Canada 06 2.3 Payment Market Characteristics in Australia 07 2.4 Payment Market Characteristics in China 08 2.5 Payment Market Characteristics in Singapore 09 2.6 Payment Market Characteristics in Malaysia 10 2.7 Payment Market Characteristics in Indonesia 11 2.8 Payment Market Characteristics in the Philippines 12 2.9 Comparing the Payment Markets 13-14 3. The Digital Payments World – Competitive Fragmentation 15-19 4. The Impact of Fragmentation on Payment Platforms 20-21 5. How Open Payment Platforms can overcome Fragmentation 22-24 6. Key Findings from the Report 25 7. About the Research 26 Overcoming Fragmentation – The Payments Platform Challenge 2 Overcoming the Fragmented Payment 1 Landscape with Open Payment Platforms 1.1 Executive Summary Global payment trends and digital technologies are driving change in many key payment markets. The omni-channel payment behaviour of increasingly online consumers, the multiple payment service demands of merchants, the globalisation of merchant businesses and technology driven fragmentation of payment services are real challenges for payment platform providers. This report highlights the impact of payment fragmentation in the digital payments world seen in key payment markets around the world, through the lens of both merchant businesses and the payments industry. In today’s world, global businesses are seeking a global solution that helps them consolidate their local business, grant them access to information in real-time and generate reports, ad-hoc, to make key decisions that help them manage cash flow, inventory and monitor their customer behaviour. -

Raas Initiating 20210203
BANXA Holdings Inc Initiation of Coverage Providing secure access to digital assets Fintech BANXA Holdings Inc (TSX-V:BNXA) is a global Payments Service Provider (PSP) serving the digital asset/cryptocurrency industry. It does so by using its platform as a 3 February 2021 “bridge” between the fiat/cash/banking system and the digital asset/exchange system. Share detail The company is headquartered in Australia where it has pioneered easy to access, TSX-V Code BNXA local payments platforms for retail investors to acquire cryptocurrencies. More recently it has expanded its infrastructure to the B2B market, partnering with the Share price (1 Feb ’21) C$2.10 leading cryptocurrency exchanges, including OK Group, Binance, KuCoin and EDGE Market Capitalisation C$85.5M Wallet. It has also expanded to the UK, the European Union, USA and Canada. Since Shares on issue 40.7M the launch of its flagship B2B product, BANXA has seen significant growth in Total Net cash post IPO ~$6.0M Payments Volumes (TPV), including 1,000% growth in January 2021 TPV to A$55m. BANXA listed on the Toronto Stock Exchange on January 6, through a reverse merger Free float ~65% with Toronto-listed A-Labs Capital I Corp, with a market capitalisation at listing of Upside Case C$40.7m. We initiate coverage of BANXA with a base case discounted cashflow Scalable business model in high growth sector derived valuation of C$3.47/share, which implies a CAGR of 36% in 10-year free Delivering both online and offline payments cashflows, in a sector that is forecasted to generate >50% CAGR over the same period. -

P R a C T I C E U P D A
Please read this update and contact this office P r a c t i c e if you have any queries U p d a t e NOVEMBER 2014 Can you access your super fund Breast implants and tummy tuck? for medical procedures? However, the taxpayer apparently made a second withdrawal (of approximately $20,000) from her Editor: The following relates to a newspaper article superannuation fund to pay for breast implants that appeared recently in a national newspaper and a tummy tuck. and was then subsequently picked up by national Editor: Clients need to understand that there TV and radio. are only very limited circumstances under which As it concerns a taxpayer withdrawing all of her superannuation monies can be withdrawn to pay $30,000 balance from her superannuation fund for a medical procedure, under the umbrella of for weight loss, a tummy tuck and breast implants, ‘compassionate grounds’. clients who heard about it or saw it on TV may be When can super monies be released on incorrectly contemplating accessing their super. ‘compassionate grounds’ Compassionate grounds to withdraw Where an SMSF member is suffering a severe superannuation medical condition and cannot afford to pay for such medical expenses, they can apply to the DHS The taxpayer involved suffered from obesity. On (not the ATO) to have some of their super funds this basis, she obtained a written statement from released on ‘compassionate grounds'. her medical practitioner in which it was argued that without this stomach reduction procedure, it was Basically, a member will be entitled to claim likely that she would experience severe ill health 'compassionate grounds' where: that could possibly be a life threatening condition. -

Ecommerce Connectors Market Overview
eCommerce Connectors Market Overview Global Coverage October 4th, 2021 Global Coverage eCommerce Connectors Market Overview eCommerce Connectors Market Overview This overview includes detailed information on the payment methods and acquirers in ACI’s global payment network, grouped by region and subdivided by country. The list’s focus on region and country will assist payment providers and their merchants to identify the payment options available wherever they want to compete. Additionally, the appendix at the end of this document contains information regarding connectors’ international and cross-border licenses. Africa BOTSWANA PAYMENT METHOD BRANDS CONNECTOR NAME Wallet PayPal PayPal** (Alternative Payments) DJIBOUTI PAYMENT METHOD BRANDS CONNECTOR NAME Wallet PayPal PayPal** (Alternative Payments) ALGERIA PAYMENT METHOD BRANDS CONNECTOR NAME Wallet PayPal PayPal** (Alternative Payments) EGYPT PAYMENT METHOD BRANDS CONNECTOR NAME Credit Card Mastercard, Visa Arab African International Bank (AAIB) (Card Payments) Banque Misr Commercial International Bank (CIB) National Bank of Egypt Virtual Currency Bitcoin Payment21 | Moving Media GmbH DBA (Alternative Payments) Wallet PayPal PayPal** (Alternative Payments) * European Cross-border license as defined by Visa and MasterCard ** International license © October 4th, 2021 ACI Worldwide. All rights reserved. _|_ globalcoverage.aciworldwide.com Page 2 of 69 Global Coverage eCommerce Connectors Market Overview GHANA PAYMENT METHOD BRANDS CONNECTOR NAME Virtual Currency Bitcoin Payment21 | Moving -

XU Magazine - the Independent Magazine for Xero Users, by Xero Users
The independent magazine for Xero users, by Xero users ISSUE 16 magazine COVER STORY Let Receipt Bank Do It, So You Don’t Have To INTERVIEW Steve Vamos Xero’s new CEO ISSN 2054-7226 16 Plus lots more from Xero connected Apps 9 772054 722009 Brought to you by PKF New Zealand (pkf.co.nz) Follow us on Twitter: @PKFI Issue 16 / 1 Brought to you by Brought to you by PKF New Zealand View Point Tax Brought to you by PKF New Zealand Proposed Ring- PKF Asia Dorian Crighton, Business Jono Bredin, Head of Tax Advisory Services Director, Director, PKF Bredin McCormack PKF Goldsmith Fox - Recastle - Dunedin Christchurch [email protected] Fencing of [email protected] catches the Residential Chris Lamb, Business Advisory Services Director, PKF Property Losses Rutherfords - Palmerston North Xero Bug [email protected] A ny day now, Inland D orian Crighton from interest of the Asian delegates go to As far as the rest of the conference Revenue is expected to Christchurch and Chris another level as they watched how went, China is, of course, hugely finalise their views on a proposal Lamb from Palmerston North Xero was transforming how their significant and PKF has a broad which will limit the ability of a recently attended the June PKF clients could do business in Asia. representation in China. We learnt property investor to offset losses Asia Pacific Conference which took The hands-on Xero demonstration a lot from the PKF China desk from their residential property place in Ho Chi Minh City, Vietnam. -
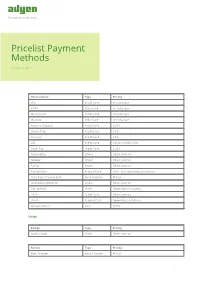
Adyen Commercial Documentation
Pricelist Payment Methods February 10, 2014 International Type Pricing Visa Credit Card Interchange+ V-PAY Debit Card Interchange+ MasterCard Credit Card Interchange+ Maestro Debit Card Interchange+ American Express Credit Card 3,95% Diners Club Credit Card 3,5% Discover Credit Card 3,5% JCB Credit Card Contact Adyen Sales Union Pay Credit Card 3,25% ClickandBuy Wallet Direct contract Neteller Wallet Direct contract PayPal Wallet Direct contract PaySafeCard Prepaid Card 10% - 12% depending on industry SEPA Bank Transfer EUR Bank Transfer e 0,20 Skrill (MoneyBookers) Wallet Direct contract SMS and IVR Other Depending on country UATP Credit Card Direct contract Ukash Prepaid Card Depending on industry Western Union Cash 0,50% Europe Europe Type Pricing Loyalty cards Other Direct contract Austria Type Pricing Bank Transfer Bank Transfer e 0,20 1 Austria Type Pricing EPS Online Banking Direct contract SEPA Direct Debit Direct Debit e 0,25 SOFORT Banking Online Banking Depends on industry 1% - 5% Denmark Type Pricing Bank Transfer Bank Transfer e 0,20 Dankort Debit Card Direct contract Danske Bank Online Banking e 0,55 Jyske Bank Online Banking 1,8% (min e 0,35) Nordea Online Banking 1,8% (min e 0,35) Open Invoice Open Invoice Direct contract SEPA Direct Debit Direct Debit e 0,25 Finland Type Pricing Bank Transfer Bank Transfer e 0,20 Ålandsbanken Online Banking e 0,55 Aktia Online Banking e 0,55 Danske Bank Online Banking e 0,55 Handelsbanken Online Banking e 0,55 Nordea Online Banking e 0,70 OP-Pohjola Online Banking e 0,55 Open Invoice Open -
Satago (Latin): to Satisfy/Pay a Creditor
The independent magazine for Xero users, by Xero users ISSUE 10 magazine ON DEMAND BUSINESS FINANCE Satago (Latin): to satisfy/pay a creditor COVER STORY ISSN 2054-7226 Satago’s Steven Renwick explains how 10 the Financial Web is transforming the 9 772054 722009 traditional lending landscape Have you subscribed? Go to subscriptions.xumagazine.com Follow us on Twitter: @xumagazine Issue 10 / 1 Have you subscribed for FREE? Go to subscriptions.xumagazine.com 30+ Integrations ALL-IN-ONE PROJECT MANAGEMENT SOFTWARE Powerful Job Mobile app workflowmax.com/xero 2 / Issue 10 XU Magazine - the independent magazine for Xero users, by Xero users. Find us online at: xumagazine.com Have you subscribed? Go to subscriptions.xumagazine.com Follow us on Twitter: @xumagazine Issue 10 / 3 46 / CASE STUDY - How simple Xero feature that’ll get you paid on 98 / Top tips for Xero users: Budget process automation helped time Manager Welcome to issue 10... increase efficiency & growth 76 / TUTORIAL - AutoEntry: 100 / Mitigating risk and making 6 / 2017 Up and Coming Tech traditional lending landscape advanced, feature-rich automation data security a top priority of data entry to Xero 8 / Explained: Xero Partner Program 22 / From rock music photographer Points to helping businesses develop 82 / Introducing mTrio 9 / TUTORIAL - Provide 24 / Why philanthropy matters: 84 / Mindset over money: why magazine Management Reports to Clients your small business guide to giving spending more on marketing is not The independent magazine Without Breaking a Sweat the answer -

Who's Who in Payments 2020
Insights into Payments and Beyond Who’s Who in Payments 2020 Complete Overview of Key Payment Providers Key media partner: Who’s Who in Payments 2020 Complete Overview of Key Payment Providers Contact us For inquiries on editorial opportunities please contact: Email: [email protected] To subscribe to our newsletters, click here For general advertising information, contact: Mihaela Mihaila Email: [email protected] RELEASE VERSION 1.0 MARCH 2020 COPYRIGHT © THE PAYPERS BV ALL RIGHTS RESERVED TEL: + 31 20 893 4315 FAX: + 31 20 658 0671 MAIL: [email protected] Management Summary As the payments value chain is maturing, retail prices for online payments are steadily dropping, while the level of service offered to merchants is only increasing. Consequently, payment providers aim to gain scale and increase capabilities through strategic acquisitions, constantly reshaping the payments ecosystem. This report describes the global payment solutions provider space today, defines the capabilities offered by the different participants in the ecosystem, and presents the dynamics of this space constantly shaped by innovation and consolidation. Our commitment Here, at The Paypers, we are aiming to provide clear perspectives on the ever-changing commerce and payments environment, in order to help professionals and industry players stay abreast of all these developments and understand the opportunities that arise. With that in mind, we created Who’s Who in Payments – Complete Overview of Key Payment Providers, a relevant source of reference and a must-read about the payments industry. The first edition of the report tackles some of the key trends that are relevant for merchants, payments professionals, and not only – such as the size of the ecommerce market and the development of the payments ecosystem, the latest innovation in payments and essential trends to watch, the payment landscape of 2020, the M&A activity in the payments space, and more. -

ONLINE PAYMENT METHODS Worlwide Supported Payment Methods Overview
ONLINE PAYMENT METHODS Worlwide supported payment methods overview Nexway’s range of payment methods is part of Nexway MONETIZE solution. MONETIZE starts with Nexway acting as merchant of record (MoR). You keep control of your pro- duct and catalog, customers, user experience, and marketing operations. Nexway, as MoR and your legal reseller, is liable to the financial institutions that process the payments to ensure security and data integrity. Nexway se cures transactions and payments worldwide, collects and remits orders and sales tax, provides fulfillment integrations, and ensures data compliance, leaving you the time to invest in your products & services! Built upon a micro-service and API based architecture, Monetize is able to couple next generation payments, AI and big data capabilities to provide a unique approach to software, game and service monetization. Nexway Nexway Payment Methods| © Nexway 2017 Nexway supports flexible payment options! CARD PAYMENTS ALTERNATIVE PAYMENTS MOBILE WALLETS We accept major credit card We support several ways to We give customers the option payments from over 140 pay including major alterna- to use Apple Pay ™, Android countries worldwide. tive payment methods, online Pay ™ and other mobile wal- and offline bank transfers, lets. direct debits and more. MAIN PAYMENT CARDS Payment cards are not the only way to pay for online transactions. In reality there are more than 300 different types of payments in the e-commerce world. Nexway Nexway Payment Methods| © Nexway 2017 ALTERNATIVE PAYMENT METHODS & WALLET ONLINE BANK TRANSFERS Online: Customers use their online or real-time Bank account to transfer money with imme- diate online authorisation. Examples: iDEAL, eNets, Sofort, Giropay Offline: Customers make an offline payment by using a payment reference. -

Review of the International Landscape of Innovation in Payments and Insights for UK Payments
Review of the International Landscape of Innovation in Payments and Insights for UK Payments Summary Findings An Accenture report commissioned by the Payment Systems Regulator + Contents 1. Foreword 4 2. Introduction 6 3. Methodology 7 4. Emerging trends in payments 10 5. Worldwide scan of payments innovation 14 6. Appendices 34 Disclaimer This document has been prepared solely for the benefit of the Payment Systems Regulator (PSR) in reliance upon instructions given by the PSR. The document cannot be relied on by any third party, whose circumstances or requirements may be different. Accordingly, no liability of any kind is accepted, whatsoever or howsoever caused, to any third party arising from reliance in any way on any part of this document. Each recipient is entirely responsible for the consequences of its use, including any actions taken or not taken by the recipient based on this document. 3 1. Foreword In this report Accenture has scanned worldwide innovations in payments for the UK Payment Systems Regulator (PSR). We reviewed over 100 payments innovations from simple consumer apps to major infrastructure changes, and payments policy initiatives. We have focused on their motives, key features, interactions and the policies used. We have reviewed each innovation to identify its impact and relevance for UK payments. 4 5 2. Introduction Following the Call for Inputs issued The PSR has engaged Accenture to by the Financial Conduct Authority in gather facts, evidence and, where April 2014, the PSR has mobilised and appropriate, stakeholder views on entered into an initial period of evidence innovation in payments from around the gathering and informal engagement world.