Contents in This Issue
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

WIKINOMICS How Mass Collaboration Changes Everything
WIKINOMICS How Mass Collaboration Changes Everything EXPANDED EDITION Don Tapscott and Anthony D. Williams Portfolio Praise for Wikinomics “Wikinomics illuminates the truth we are seeing in markets around the globe: the more you share, the more you win. Wikinomics sheds light on the many faces of business collaboration and presents a powerful new strategy for business leaders in a world where customers, employees, and low-cost producers are seizing control.” —Brian Fetherstonhaugh, chairman and CEO, OgilvyOne Worldwide “A MapQuest–like guide to the emerging business-to-consumer relation- ship. This book should be invaluable to any manager—helping us chart our way in an increasingly digital world.” —Tony Scott, senior vice president and chief information officer, The Walt Disney Company “Knowledge creation happens in social networks where people learn and teach each other. Wikinomics shows where this phenomenon is headed when turbocharged to engage the ideas and energy of customers, suppli- ers, and producers in mass collaboration. It’s a must-read for those who want a map of where the world is headed.” —Noel Tichy, professor, University of Michigan and author of Cycle of Leadership “A deeply profound and hopeful book. Wikinomics provides compelling evidence that the emerging ‘creative commons’ can be a boon, not a threat to business. Every CEO should read this book and heed its wise counsel if they want to succeed in the emerging global economy.” —Klaus Schwab, founder and executive chairman, World Economic Forum “Business executives who want to be able to stay competitive in the future should read this compelling and excellently written book.” —Tiffany Olson, president and CEO, Roche Diagnostics Corporation, North America “One of the most profound shifts transforming business and society in the early twenty-first century is the rapid emergence of open, collaborative innovation models. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

IGP® / VGL Emulation Code V™ Graphics Language Programmer's Reference Manual Line Matrix Series Printers
IGP® / VGL Emulation Code V™ Graphics Language Programmer’s Reference Manual Line Matrix Series Printers Trademark Acknowledgements IBM and IBM PC are registered trademarks of the International Business Machines Corp. HP and PCL are registered trademarks of Hewlett-Packard Company. IGP, LinePrinter Plus, PSA, and Printronix are registered trademarks of Printronix, LLC. QMS is a registered trademark and Code V is a trademark of Quality Micro Systems, Inc. CSA is a registered certification mark of the Canadian Standards Association. TUV is a registered certification mark of TUV Rheinland of North America, Inc. UL is a registered certification mark of Underwriters Laboratories, Inc. This product uses Intellifont Scalable typefaces and Intellifont technology. Intellifont is a registered trademark of Agfa Division, Miles Incorporated (Agfa). CG Triumvirate are trademarks of Agfa Division, Miles Incorporated (Agfa). CG Times, based on Times New Roman under license from The Monotype Corporation Plc is a product of Agfa. Printronix, LLC. makes no representations or warranties of any kind regarding this material, including, but not limited to, implied warranties of merchantability and fitness for a particular purpose. Printronix, LLC. shall not be held responsible for errors contained herein or any omissions from this material or for any damages, whether direct, indirect, incidental or consequential, in connection with the furnishing, distribution, performance or use of this material. The information in this manual is subject to change without notice. This document contains proprietary information protected by copyright. No part of this document may be reproduced, copied, translated or incorporated in any other material in any form or by any means, whether manual, graphic, electronic, mechanical or otherwise, without the prior written consent of Printronix, LLC. -

Emerging Trends in Management, IT and Education ISBN No.: 978-87-941751-2-4
Emerging Trends in Management, IT and Education ISBN No.: 978-87-941751-2-4 Paper 3 A STUDY ON REINVENTION AND CHALLENGES OF IBM Kiran Raj K. M1 & Krishna Prasad K2 1Research Scholar College of Computer Science and Information Science, Srinivas University, Mangalore, India 2 College of Computer Science and Information Science, Srinivas University, Mangalore, India E-mail: [email protected] Abstract International Business Machine Corporation (IBM) is one of the first multinational conglomerates to emerge in the US-headquartered in Armonk, New York. IBM was established in 1911 in Endicott, New York, as Computing-Tabulating-Recording Company (CTR). In 1924, CTR was renamed IBM. Big Blue has been IBM's nickname since 19 80. IBM stared with the production of scales, punch cards, data processors and time clock now produce and sells computer hardware and software, middleware, provides hosting and consulting services.It has a worldwide presence, operating in over 175 nations with 3,50,600 staff with $79. 6 billion in annual income (Dec 2018). It is currently competing with Microsoft, Google, Apple, and Amazon. 2012 to 2017 was tough time for IBM, although it invests in the field of research where it faced challenges while trying to stay relevant in rapidly changing Tech-Market. While 2018 has been relatively better and attempting to regain its place in the IT industry. With 3,000 scientists, it invests 7% of its total revenue to Research & Development in 12 laboratories across 6 continents. This resulted in the U.S. patent leadership in IBM's 26th consecutive year. In 2018, out of the 9,100 patents that granted to IBM 1600 were related to Artificial Intelligence and 1,400 related to cyber-security. -

Linking USDA Nutrition Databases to IRI Household-Based and Store-Based Scanner Data, TB-1952, U.S
Uniteited Sd Staates Ds Depaarrttmmeent of Af Aggricuultuuree Economic Research Linking USDA Nutrition Databases to IRI Service Household-Based and Store-Store-BasedBased Technical Bulletin Number 1952 Scanner Data March 2019 Andrea C. Carlson, Elina Tselepidakis Page, Thea Palmer Zimmerman, Carina E. Tornow, and Sigurd Hermansen United States Department of Agriculture Economic Research Service www.ers.usda.gov Recommended citation format for this publication: Andrea C. Carlson, Elina Tselepidakis Page, Thea Palmer Zimmerman, Carina E. Tornow, and Sigurd Hermansen. Linking USDA Nutrition Databases to IRI Household-Based and Store-Based Scanner Data, TB-1952, U.S. Department of Agriculture, Economic Research Service, March 2019. Cover image: Getty images. Use of commercial and trade names does not imply approval or constitute endorsement by USDA. To ensure the quality of its research reports and satisfy governmentwide standards, ERS requires that all research reports with substantively new material be reviewed by qualified technical research peers. This technical peer review process, coordinated by ERS' Peer Review Coordinating Council, allows experts who possess the technical background, perspective, and expertise to provide an objective and meaningful assessment of the output’s substantive content and clarity of communication during the publication’s review. In accordance with Federal civil rights law and U.S. Department of Agriculture (USDA) civil rights regulations and policies, the USDA, its Agencies, offices, and employees, and institutions participating in or administering USDA programs are prohibited from discriminating based on race, color, national origin, religion, sex, gender identity (including gender expression), sexual orientation, disability, age, marital status, family/parental status, income derived from a public assistance program, political beliefs, or reprisal or retaliation for prior civil rights activity, in any program or activity conducted or funded by USDA (not all bases apply to all programs). -
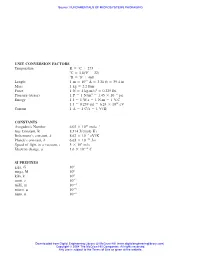
UNIT CONVERSION FACTORS Temperature K C 273 C 1.8(F 32
Source: FUNDAMENTALS OF MICROSYSTEMS PACKAGING UNIT CONVERSION FACTORS Temperature K ϭ ЊC ϩ 273 ЊC ϭ 1.8(ЊF Ϫ 32) ЊR ϭ ЊF ϩ 460 Length 1 m ϭ 1010 A˚ ϭ 3.28 ft ϭ 39.4 in Mass 1 kg ϭ 2.2 lbm Force 1 N ϭ 1 kg-m/s2 ϭ 0.225 lbf Pressure (stress) 1 P ϭ 1 N/m2 ϭ 1.45 ϫ 10Ϫ4 psi Energy 1 J ϭ 1W-sϭ 1 N-m ϭ 1V-C 1Jϭ 0.239 cal ϭ 6.24 ϫ 1018 eV Current 1 A ϭ 1 C/s ϭ 1V/⍀ CONSTANTS Avogadro’s Number 6.02 ϫ 1023 moleϪ1 Gas Constant, R 8.314 J/(mole-K) Boltzmann’s constant, k 8.62 ϫ 10Ϫ5 eV/K Planck’s constant, h 6.63 ϫ 10Ϫ33 J-s Speed of light in a vacuum, c 3 ϫ 108 m/s Electron charge, q 1.6 ϫ 10Ϫ18 C SI PREFIXES giga, G 109 mega, M 106 kilo, k 103 centi, c 10Ϫ2 milli, m 10Ϫ3 micro, 10Ϫ6 nano, n 10Ϫ9 Downloaded from Digital Engineering Library @ McGraw-Hill (www.digitalengineeringlibrary.com) Copyright © 2004 The McGraw-Hill Companies. All rights reserved. Any use is subject to the Terms of Use as given at the website. Source: FUNDAMENTALS OF MICROSYSTEMS PACKAGING CHAPTER 1 INTRODUCTION TO MICROSYSTEMS PACKAGING Prof. Rao R. Tummala Georgia Institute of Technology ................................................................................................................. Design Environment IC Thermal Management Packaging Single Materials Chip Opto and RF Functions Discrete Passives Encapsulation IC Reliability IC Assembly Inspection PWB MEMS Board Manufacturing Assembly Test Downloaded from Digital Engineering Library @ McGraw-Hill (www.digitalengineeringlibrary.com) Copyright © 2004 The McGraw-Hill Companies. -

Sejarah Perkembangan Dan Kemajuan the International Bussines Machines
SEJARAH PERKEMBANGAN DAN KEMAJUAN THE INTERNATIONAL BUSSINES MACHINES Oleh : ANGGARA WISNU PUTRA 1211011018 CIPTA AJENG PRATIWI 1211011034 DERI KURNIAWAN 1211011040 FEBY GIPANTIUS ZAMA 1211011062 NOVITA LIANA SARI 1211011118 RAMA AGUSTINA 1211011128 FAKULTAS EKONOMI DAN BISNIS UNIVERSITAS LAMPUNG BANDAR LAMPUNG 2014 BAB II PEMBAHASAN 2.1 Sejarah berdirinya THE INTERNATIONAL BUSSINES MACHINES (IBM) 1880—1929 Pada tahun 1880-an, beberapa teknologi yang akan menjadi bisnis IBM ditemukan. Julius E. Pitrap menemukan timbangan komputer pada tahun 1885. Alexander Dey menemukan dial recorder tahun 1888. Herman Hollerith menemukan Electric Tabulating Machine 1989 dan pada tahun yang sama Williard Bundy menemukan alat untuk mengukur waktu kerja karyawan. Pada 16 Juni 1911, teknologi-teknologi tersebut dan perusahaan yang memilikinya digabungkan oleh Charles Ranlett Flint dan membentuk Computing Tabulating Recording Company (CTR). Perusahaan yang berbasis di New York ini memiliki 1.300 karyawan dan area perkantoran serta pabrik di Endicott dan Binghamton, New York; Dayton, Ohio; Detroit, Michigan; Washington, D.C.; dan Toronto, Ontario. CTR memproduksi dan menjual berbagai macam jenis mesin mulai dari timbangan komersial hingga pengukur waktu kerja. Pada tahun 1914, Flint merekrut Thomas J. Watson, Sr., dari National Cash Register Company, untuk membantunya memimpin perusahaan. Watson menciptakan slogan, ―THINK‖, yang segera menjadi mantra bagi karyawan CTR. Dalam waktu 11 bulan setelah bergabung, Watson menjadi presiden dari CTR. Perusahaan memfokuskan diri pada penyediaan solusi penghitungan dalam skala besar untuk bisnis. Selama empat tahun pertama kepemimpinannya, Watson sukses meningkatkan pendapatan hingga lebih dari dua kali lipat dan mencapai $9 juta. Ia juga sukses mengembangkan sayap ke Eropa, Amerika Selatan, Asia, dan Australia. Pada 14 Februari 1924, CTR berganti nama menjadi International Business Machines Corporation (IBM). -

Barcodes and Rfids
Barcodes and RFIDs Martin Dodge and Rob Kitchin For: Globalization in Practice (edited by Nigel Thrift, Adam Tickell and Steve Woolgar) Introduction One of the key phenomena of the globalization of commerce has been the internationalisation of goods and brands. A set of diverse practices and processes, including the transformation of transport infrastructure and logistics and the virtualisation of money, have enabled both producers (e.g., goods manufacturers) and sellers (e.g., wholesalers, supermarkets) to massively extend supply chains, to globally expand their markets, and to increase their turnover and profits. A key technology in improving the efficiency and productivity of logistical organisation and operation has been development of sophisticated identification systems that overcome the anonymity of manufactured products by assigning unique numerical identifiers – digital thumbprints - to material products. These identification systems allow products to be effectively and unambiguously processed, shipped and traced through complex logistical networks, to monitor sales, aid account management, refine supply chains and inform marketing strategies. Conceptually they have two distinct components, first an agreed allocation of unique id code numbers and, second, an agreed media to physical store the code. The most obvious manifestation of this technology for product identification and tracking are the parallel black and white printed stripes of barcodes. Barcodes Barcodes, visible on nearly all, retail products are the physical manifestation of UPCs (Universal Product Code) – a code that uniquely identifies a product regardless of location or language. The original UPC concept can be traced back to 1940s, but gained widespread acceptance and usage in the 1970s with the development of a UPC standard by a group of U.S. -

Tips for Marketing Fresh Produce to Retail Grocers: Using PLU and UPC Codes a Guide for Producers
Working with Local Fresh Produce in Retail Settings Tips for Marketing Fresh Produce to Retail Grocers: Using PLU and UPC Codes A Guide for Producers What is a PLU? What is a UPC? PLU and UPC codes help retailers identify or scan your product into their cash register system. Being knowledgeable about the differences in these labels in advance of approaching a retailer may help you get your foot in the door. These codes are not only a necessity for some retailers, but also a marketing tool for your farm, because they carry information about your farm and products along the supply chain. This informational sheet contains information adapted from the Produce Marketing Association. NC Growing Together, a CEFS-led initiative, is funded by the United States Department of Agriculture, National Institute of Food and Agriculture, grant #2012-68004-20363 www.ncgrowingtogether.org PLU and UPC Codes PLU Codes_________________________________________________________________ A PLU code, or price look up code, is a 4 or 5 digit code that is unique to a particular produce item; based upon the commodity, the variety and the size group; and will typically appear on a small sticker that is applied to the individual piece of fresh produce. These codes are standard across the produce industry and in all retail grocers. They help cashiers identify the variety and therefore the price of a product. For example, a hydroponic/greenhouse tomato has the PLU 4799, while a slicing tomato has the PLU 4805. The retailer may charge $2.99 per lb for a hydroponic, but $1.49 per lb for a slicing tomato. -

DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2
Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 DB2 10.5 with BLU Acceleration 00-FM.indd 1 9/17/13 2:26 PM Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 00-FM.indd 2 9/17/13 2:26 PM Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 DB2 10.5 with BLU Acceleration Paul Zikopoulos Sam Lightstone Matt Huras Aamer Sachedina George Baklarz New York Chicago San Francisco Athens London Madrid Mexico City Milan New Delhi Singapore Sydney Toronto 00-FM.indd 3 9/17/13 2:26 PM Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 McGraw-Hill Education books are available at special quantity discounts to use as premiums and sales promotions, or for use in corporate training programs. To contact a representative, please visit the Contact Us pages at www.mhprofessional.com. DB2 10.5 with BLU Acceleration: New Dynamic In-Memory Analytics for the Era of Big Data Copyright © 2014 by McGraw-Hill Education. All rights reserved. Printed in the Unit- ed States of America. Except as permitted under the Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of pub- lisher, with the exception that the program listings may be entered, stored, and exe- cuted in a computer system, but they may not be reproduced for publication. All trademarks or copyrights mentioned herein are the possession of their respective owners and McGraw-Hill Education makes no claim of ownership by the mention of products that contain these marks. -
Ranking System.Xlsx
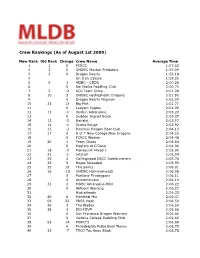
Crew Rankings (As of August 1st 2009) New Rank Old Rank Change Crew Name Average Time 1 1 0 FCRCC 1:57.62 2 2 0 OHDBC Mayfair Predators 1:59.09 3 3 0 Dragon Beasts 1:59.18 4 On S'en Calisse 1:59.25 561ADBC - CSDC 2:00.26 6 0 Kai Ikaika Paddling Club 2:00.73 7 5 -2 SCC Team Chiro 2:01.28 8 10 2 OHDBC Hydrophobic Dragons 2:01.90 9 0 Dragon Hearts Magnum 2:02.59 10 23 13 Big Fish 2:02.77 11 0 Laoyam Eagles 2:02.99 12 11 -1 Verdun Adrenaline 2:03.22 13 0 Sudden Impact Black 2:03.37 14 12 -2 Hanalei 2:03.57 15 14 -1 Scotia Rouge 2:03.92 16 13 -3 Piranhas Dragon Boat Club 2:04.13 17 17 0 U of T New College New Dragons 2:04.25 18 0 FCRCC Women 2:04.48 19 20 1 Team Chaos 2:04.84 20 0 Masters of D'Zone 2:04.96 21 19 -2 Manayunk Mixed I 2:05.00 22 21 -1 Jetstart 2:05.04 23 25 2 Collingwood DBCC Sidelaunchers 2:05.76 24 29 5 Mojos Reloaded 2:05.95 25 35 10 The Saints 2:06.01 26 16 -10 OHDBC Hammerheads 2:06.08 27 0 Portland Firedragons 2:06.11 28 0 Anniemaniacs 2:06.14 29 31 2 MDBC Adrenaline-HRV 2:06.22 30 0 Without Warning 2:06.27 31 HydraHeads 2:06.33 32 40 8 Montreal Mix 2:06.47 33 56 23 PDBC Heat 2:06.50 34 36 2 The Blades 2:06.50 35 38 3 DCH DVP 2:06.56 36 0 San Francisco Dragon Warriors 2:06.60 37 0 Victoria College Paddling Club 2:06.66 38 52 14 MOFO''s 2:06.68 39 0 Philadelphia Police Boat Teams 2:06.75 40 33 -7 TECO Tan Anou Black 2:06.78 41 41 0 3R Dragon - Mixed 2:07.19 42 37 -5 TECO Tan Anou Red 2:07.20 43 49 6 University Elite Force 2:07.27 44 39 -5 Mayfair Warriors 2:07.39 45 51 6 Hydroblades 2:07.39 46 24 -22 PDBC 2:07.79 47 0 UC -

Case Studies on Innovation
I N N O V A A T I O N 1 www.ibscdc.org ITC’s E-Choupal: A Mirage of the American studios declared in May 2007 Immelt charted his own leadership style Poor? that it had obtained the rights for and brought about a cultural revolution in developing a theme park based on the GE. Expectations were high and the E-Choupal is a novel initiative of ITC extremely successful character of the challenges were many. Immelt had to face Limited (ITC), an Indian conglomerate, popular culture Harry Potter in US, UK several challenges. He had to provide to improve its marketing channel in and all over the world. Walt Disney parks leadership and lend vision to a large, diverse agriculture. It has its roots in Project and resorts have also tried to get the rights conglomerate like GE in the post 9/11 Symphony – a pilot project launched in for Harry Potter theme park but failed to volatile global business scenario. He also 1999 to organise ITC’s agri business. The strike a deal with the creator of the Harry had to shift the company’s focus towards business model was designed to Potter character, J.K. Rowling. Universal innovation and customer centricity in accommodate farmers, intermediaries in and Disney have been competing in the addition to posting continued growth in a the traditional model and the company entertainment industry for many years, and sluggish economy. The case study discusses through information technology. The main Walt Disney had been a leader in theme Immelt’s innovation and customer centric objective of e-Choupal is dissemination and parks.