Mapping Breakpoint Types: an Exploratory Study
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Said GUERRAB
Said GUERRAB CONTACT 404-5100 Boulevard Pie IX E-mail: [email protected] H1X 2B6 Website: www.sguerrab-developper.com Montreal (QC) Phone: 438-935-8707 SUMMARY 05 years of experience designing and developing websites. Bilingual French-English. Implementation of numerous IT projects within the school. Design and implementation of websites in PHP, MySQL, JSP, HTML5, CSS3, Sass, Less, Stylus, and JavaScript, Bootstrap, D3.js, MVC framworks (PHP Laravel), Photoshop... Web project management (specifications, deadlines, risks management...). Audio editing, video editing, and graphic design. SEO for websites Autonomous, organized, have a team spirit, available, highly motivated, adaptable to new situations, can work under pressure. TECHNICAL Operating Systems: Windows, Linux , Mac OS X SKILLS Programming Languages: Java, JSP, Ruby, Cobol, VB.NET, C++, PHP, HTML/CSS, JavaScript Markup Languages:JSON, YAML, XML CSS Preprocessors: Sass CSS, Stylus CSS, Less CSS Editors & IDEs: Eclipse, PHPStorm, NetBeans, RubyMine, Sublime Text… Version Control Systems: GIT, Github, Bitbucket, SVN Frameworks & libraries: Laravel, JQuery, Bootstrap, D3.js... CMS: Drupal, Joomla, WordPress Server management: Apache, Tomcat, Glassfish, CPanel, DNS Database: Oracle SQL, PL/SQL, SQL Server, MySQL, Access. Office Applications:Excel, Word, Powerpoint and LibreOffice suite Other software: Microsoft Project, Microsoft Visio, Oracle Forms, Oracle Reports Graphism: Photoshop, The Gimp, Illustrator, Inkscape et InDesign. Maintening:Software (installation and updating). PROFESSIONAL Identify the needs of clients. SKILLS Analyze specifications of the website. Establish a site plan with the design of each page. Choosing tools for the development of the site . Coordinate the collection and the organization of information to include on the site. Collaborate in the definition of the architecture of the site and the choice of navigation scenarios. -
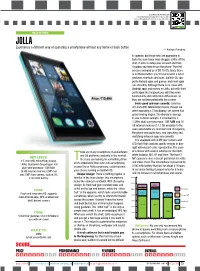
Overall Features Performance Price
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -
Fira Code: Monospaced Font with Programming Ligatures
Personal Open source Business Explore Pricing Blog Support This repository Sign in Sign up tonsky / FiraCode Watch 282 Star 9,014 Fork 255 Code Issues 74 Pull requests 1 Projects 0 Wiki Pulse Graphs Monospaced font with programming ligatures 145 commits 1 branch 15 releases 32 contributors OFL-1.1 master New pull request Find file Clone or download lf- committed with tonsky Add mintty to the ligatures-unsupported list (#284) Latest commit d7dbc2d 16 days ago distr Version 1.203 (added `__`, closes #120) a month ago showcases Version 1.203 (added `__`, closes #120) a month ago .gitignore - Removed `!!!` `???` `;;;` `&&&` `|||` `=~` (closes #167) `~~~` `%%%` 3 months ago FiraCode.glyphs Version 1.203 (added `__`, closes #120) a month ago LICENSE version 0.6 a year ago README.md Add mintty to the ligatures-unsupported list (#284) 16 days ago gen_calt.clj Removed `/**` `**/` and disabled ligatures for `/*/` `*/*` sequences … 2 months ago release.sh removed Retina weight from webfonts 3 months ago README.md Fira Code: monospaced font with programming ligatures Problem Programmers use a lot of symbols, often encoded with several characters. For the human brain, sequences like -> , <= or := are single logical tokens, even if they take two or three characters on the screen. Your eye spends a non-zero amount of energy to scan, parse and join multiple characters into a single logical one. Ideally, all programming languages should be designed with full-fledged Unicode symbols for operators, but that’s not the case yet. Solution Download v1.203 · How to install · News & updates Fira Code is an extension of the Fira Mono font containing a set of ligatures for common programming multi-character combinations. -
Xdebug Tutorial
Welcome! Xdebug tutorial PHP Konferenca - Ljubljana, Slovenia Derick Rethans - [email protected] - twitter: @derickr http://derickrethans.nl/talks.html About Me Derick Rethans ● Dutchman living in London ● PHP development ● Author of the mcrypt, input_filter, dbus, translit and date/time extensions ● Author of Xdebug ● Contributor to the Apache Zeta Components Incubator project (formerly eZ Components) ● Freelancer doing PHP (internals) development I Do Not Need a Debugger ● printf(), var_dump() and echo are good enough I Do Not Need a Debugger I Do Need a Debugger ● Xdebug: An Open Source debugging tool ● About 8 years old ● Works on "every" operating system ● Version 2.1 released about three months ago This Tutorial ● Installation overview ● Downloading, compiling and configuring Xdebug ● Basic function overview ● Playing with settings, stack traces and function traces break ● Profiling ● Profiling your own code ● Code coverage ● (Setting up code-coverage with PHP Unit) break ● Debugging ● Setting up your IDE for debugging Installation The Xdebug extension ● Zend extension, and not a PHP extension ● Xdebug is very PHP-version sensitive ● Different compilers under Windows ● Debug/non-debug ● Threadsafe or not In PHP 5.1 and 5.2: zend_extension=/local/php/lib/php/extensions/no-debug-non-zts- 20090626/xdebug.so zend_extension_ts=/local/php/lib/php/extensions/debug-zts- 20090626/xdebug.so zend_extension_debug=/local/php/lib/php/extensions/debug-non-zts- 20090626/xdebug.so In PHP 5.3: zend_extension=/local/php/lib/php/extensions/no-debug-non-zts- -

How to Communicate with Developers
How to Communicate with Developers Employer branding, job listings, and emails that resonate with a tech audience Developers are one of the most in-demand groups of employees these days. And guess what, they noticed this as well: Countless approaches by potential employers, sometimes several messages a day through Linkedin, and a few desperate recruiters even cold calling. So those with technical talents are by no means oblivious to the talent shortage. The good news is that they don’t just use this bargaining power to simply negotiate the highest salaries and most outrageous benefits. Instead, developers are intrinsically motivated. They are looking for the right place to work. Your challenge in this noisy jobs market is to clearly communicate what defines your employer brand, what work needs doing, and, ultimately, who might be the right fit for the role. All of this is easier said than done. Because tech recruiting is a complex business, it is easy to not see the forest for the trees. This guide will help you decide where to start or what to fix next. In the first and more general part, we would like you to take a step back. Before we even think about how to package our job opening and approach a candidate with our offer, we look at what information and knowledge you should gather about your tech team and the company at large. Following that, we will take a practical look at how to write and talk about your company and the role, with a special focus on the job listings and a recruiting emails as a first introduction. -

Java Script Programming, Introduction
Java Script abelski Introduction © 2008 Haim Michael What is Java Script? Java Script is a scripting language running within the browser. Java Script appeared for the first time in 1995, as a scripting language supported by Netscape Navigator. JScript is Microsoft's variation for JavaScript. © 2008 Haim Michael ECMA Script In 1997 Java Script 1.1 was submitted to the European Computer Manufacturers Association (ECMA). ECMA Script, defined by ECMA-262, is the standard Java Script language. ECMA Script defines the very basic parts of the language, including the following: Syntax, Types, Statements, Keywords, Reserved Words, Operators and Objects. © 2008 Haim Michael ECMA Script Each browser implements ECMA Script in a different level. Some implements ECMA Script edition 1, some implements edition 2, some implements edition 3 and some implements edition 4. © 2008 Haim Michael HTML We can embed Java Script code within our HTML page using the <script> element. < script type=”text/javascript” > function do_something() { alert(“Good Morning!”); } < /script > We can have the Java Script code saved within a separated file the HTML shall refer to. < script type=”text/javascript” src=”mycode.js” > < /script > © 2008 Haim Michael HTML We usually place the <script> tag within the <head> element. <head> < script type=”text/javascript” > function do_something() { alert(“Good Morning!”); } < /script > </head> © 2008 Haim Michael IDEs We can develop simple code in JavaScript using a simple text editor. We can alternatively use an Integrated Development Environment, such as IntelliJ, Visual Studio, Eclipse and Netbeans. © 2008 Haim Michael IntelliJ IDEA This IDE is well known as a Java IDE. It is developed by JetBrains. -

Watchdog for Intellij: an IDE Plugin to Analyze Software Testing Practices
WatchDog For IntelliJ: An IDE Plugin To Analyze Software Testing Practices Master’s Thesis Igor Levaja WatchDog For IntelliJ: An IDE Plugin To Analyze Software Testing Practices THESIS submitted in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in COMPUTER SCIENCE by Igor Levaja born in Pozarevac, Serbia Software Engineering Research Group Department of Software Technology Faculty EEMCS, Delft University of Technology Delft, the Netherlands www.ewi.tudelft.nl c 2016 Igor Levaja. All rights reserved. WatchDog For IntelliJ: An IDE Plugin To Analyze Software Testing Practices Author: Igor Levaja Student id: 4318110 Email: [email protected] Abstract Software testing is as old as software development itself – they could not exist one without the other. However, are they equally important? Do software develop- ers devote an equivalent amount of time to both produce software and to test it? An ongoing study of the TestRoots project aims to examine and improve the state of the art of software testing and answer those questions, by observing developers’ everyday behavior. In order to support this effort, we evolved WatchDog, a single-platform software, to become the scalable, multi-platform and production-ready tool which assesses de- veloper testing activities in multiple integrated development environments (IDEs). We further used WatchDog platform to perform a small-scale study in which we examined testing habits of developers who use IntelliJ IDEA and compared them to those of the Eclipse IDE users. Finally, we were able to confirm that IntelliJ users, similarly to the Eclipse users, do not actively practice testing inside their IDEs. -

Default Windows & Linux Keymap
DEFAULT WINDOWS & LINUX KEYMAP Editing Running Refactoring Ctrl + Space Basic code completion Shift + F10 Run F5/F6 Copy/Move Alt + Enter Show intention actions and quick-fixes Shift + F9 Debug Alt + Delete Safe Delete Ctrl + P Parameter info (within method call Ctrl + Shift + F10 Run context configuration from editor Shift + F6 Rename arguments) Ctrl + Shift + X Run command line Ctrl + Alt + N Inline Variable Ctrl + Q Quick documentation lookup Ctrl + Alt + M/V/F/C Extract Method/Variable/Field/Constant Ctrl + mouse over code Brief Info Search/Replace Ctrl + Alt + Shift + T Refactor This (shows all available refactorings) Alt + Insert Generate code... (Getters, Setters, Ctrl + F/R Find/Replace Constructors) F3/Shift + F3 Find next/previous VCS/Local History Ctrl + O Override methods Ctrl + Shift + F/R Find/Replace in path Alt + BackQuote (`) ‘VCS’ quick popup Ctrl + I Implement methods Ctrl + K Commit project to VCS Ctrl + Alt + T Surround with... (if..else, try..catch, for, etc.) Usage Search Ctrl + T Update project from VCS Ctrl + / Comment/uncomment with line comment Alt + F7 / Ctrl + F7 Find usages / Find usages in file Alt + Shift + C View recent changes Ctrl + Shift + / Comment/uncomment with block comment Ctrl + Shift + F7 Highlight usages in file Ctrl + W Select successively increasing code blocks Ctrl + Alt + F7 Show usages General Ctrl + Shift + W Decrease current selection to previous state Double Shift Search everywhere Ctrl + Alt + L Reformat code Navigation Ctrl + Shift + A Find Action Ctrl + Alt + I Auto-indent line(s) Ctrl -
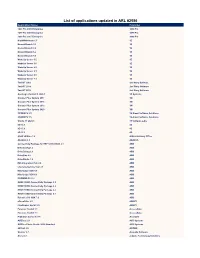
List of Applications Updated in ARL #2586
List of applications updated in ARL #2586 Application Name Publisher 1099 Pro 2005 Enterprise 1099 Pro 1099 Pro 2006 Enterprise 1099 Pro 1099 Pro 2007 Enterprise 1099 Pro NightWatchman 6.5 1E Nomad Branch 5.2 1E Nomad Branch 6.0 1E Nomad Branch 6.2 1E Nomad Branch 6.3 1E WakeUp Server 5.5 1E WakeUp Server 5.6 1E WakeUp Server 6.0 1E WakeUp Server 6.1 1E WakeUp Server 6.5 1E WakeUp Server 7.1 1E TaxACT 2002 2nd Story Software TaxACT 2014 2nd Story Software TaxACT 2018 2nd Story Software Geomagic Control X 2020.1 3D Systems Grouper Plus System 2017 3M Grouper Plus System 2018 3M Grouper Plus System 2019 3M Grouper Plus System 2020 3M CODESYS 2.3 3S-Smart Software Solutions CODESYS 3.5 3S-Smart Software Solutions Studio 3T 2020.9 3T Software Labs 4D 15.1 4D 4D 15.3 4D 4D 16.3 4D ASAP Utilities 7.8 A Must in Every Office AbaStart 2.5 ABACUS Connectivity Package for REF 541/543/545 2.1 ABB DriveConfig 1.2 ABB DriveDebug 2.9 ABB DriveSize 4.9 ABB DriveStudio 1.5 ABB IMS Integration Hub 2.8 ABB Lifecycle Service Tool 2.1 ABB MineScape SDK 5.1 ABB MineScape SDK 6.1 ABB PROMOD IV 11.2 ABB REM615 IED Connectivity Package 2.1 ABB REM615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 2.2 ABB REU615 IED Connectivity Package 5.1 ABB Robotics PC SDK 7.0 ABB eFormFiller 2.5 ABBYY FineReader Sprint 5.0 ABBYY Forensic Toolkit 7.1 AccessData Forensic Toolkit 7.1 AccessData PrizmDoc Server 13.14 AccuSoft ACDSee 2.0 ACD Systems ACDSee Photo Studio 2019 Standard ACD Systems dBTrait 5.5 ACOEM Soulver 2.7 Acqualia Software Arena 4.1 acQuire -

Setting up a Development Environment for Microservices
www.allitebooks.com PHP Microservices Transit from monolithic architectures to highly available, scalable, and fault-tolerant microservices Carlos Pérez Sánchez Pablo Solar Vilariño BIRMINGHAM - MUMBAI www.allitebooks.com PHP Microservices Copyright © 2017 Packt Publishing All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior written permission of the publisher, except in the case of brief quotations embedded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the authors, nor Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about all of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this information. First published: March 2017 Production reference: 1240317 Published by Packt Publishing Ltd. Livery Place 35 Livery Street Birmingham B32PB, UK. ISBN 978-1-78712-537-7 www.packtpub.com www.allitebooks.com Credits Authors Copy Editor Carlos Pérez Sánchez Shaila Kusanale Pablo Solar Vilariño Reviewers Project Coordinator Gabor Zelei Vaidehi Sawant Commissioning Editor Proofreader Aaron Lazar Safis Editing Acquisition Editor Indexer Divya Poojari Mariammal Chettiyar Content Development Editor Graphics Anurag Ghogre Jason Monteiro Technical Editor Production Coordinator Jijo Maliyekal Melwyn Dsa Subhalaxmi Nadar www.allitebooks.com About the Authors Carlos Pérez Sánchez is a backend web developer with more than 10 years of experience in working with the PHP language. -

Towards Left Duff S Mdbg Holt Winters Gai Incl Tax Drupal Fapi Icici
jimportneoneo_clienterrorentitynotfoundrelatedtonoeneo_j_sdn neo_j_traversalcyperneo_jclientpy_neo_neo_jneo_jphpgraphesrelsjshelltraverserwritebatchtransactioneventhandlerbatchinsertereverymangraphenedbgraphdatabaseserviceneo_j_communityjconfigurationjserverstartnodenotintransactionexceptionrest_graphdbneographytransactionfailureexceptionrelationshipentityneo_j_ogmsdnwrappingneoserverbootstrappergraphrepositoryneo_j_graphdbnodeentityembeddedgraphdatabaseneo_jtemplate neo_j_spatialcypher_neo_jneo_j_cyphercypher_querynoe_jcypherneo_jrestclientpy_neoallshortestpathscypher_querieslinkuriousneoclipseexecutionresultbatch_importerwebadmingraphdatabasetimetreegraphawarerelatedtoviacypherqueryrecorelationshiptypespringrestgraphdatabaseflockdbneomodelneo_j_rbshortpathpersistable withindistancegraphdbneo_jneo_j_webadminmiddle_ground_betweenanormcypher materialised handaling hinted finds_nothingbulbsbulbflowrexprorexster cayleygremlintitandborient_dbaurelius tinkerpoptitan_cassandratitan_graph_dbtitan_graphorientdbtitan rexter enough_ram arangotinkerpop_gremlinpyorientlinkset arangodb_graphfoxxodocumentarangodborientjssails_orientdborientgraphexectedbaasbox spark_javarddrddsunpersist asigned aql fetchplanoriento bsonobjectpyspark_rddrddmatrixfactorizationmodelresultiterablemlibpushdownlineage transforamtionspark_rddpairrddreducebykeymappartitionstakeorderedrowmatrixpair_rddblockmanagerlinearregressionwithsgddstreamsencouter fieldtypes spark_dataframejavarddgroupbykeyorg_apache_spark_rddlabeledpointdatabricksaggregatebykeyjavasparkcontextsaveastextfilejavapairdstreamcombinebykeysparkcontext_textfilejavadstreammappartitionswithindexupdatestatebykeyreducebykeyandwindowrepartitioning -

Kevells Documentation Release 0.1
kevells Documentation Release 0.1 kevell April 27, 2015 Contents 1 About pharaohtools 1 1.1 Commands................................................1 2 Indices and tables 497 i ii CHAPTER 1 About pharaohtools Welcome to the pharaohtools documentation! The Pharaohs has its own benefit while comparing to other tools as it is user friendly. In this tool the coding and the entire process depends and based php. As the pharaoh tool is framed as per php, it is easier to re-write the codes if required. Its modules functionality provides support to Mac, Linux or Unix, and also for the windows. It is a known as a shorter route which is less time-consuming, limits the use of manpower, reduces the necessity of input from users while installation. No need to download separately the templates and plug-ins that are used to support the software’s as everything gets covers under a single root. It is extensible, as if any extra module is required the user can frame and design the module as per their requirements and they can include. It is also simpler to rewrite the coding as required. By installing a single application ptconfigure entire modules under the pharaoh tool get enveloped. 1.1 Commands 1.1.1 Jrush Cache Synopsis Jrush auxiliary to clear cache in temporary memory. It has two types of cache. But both are having different functions as specified in their name. They are site clear and admin clear. It is gratified with Ubuntu and cent OS. Deleting files, folders and applications – and clearing the data from the temporary memory – won’t do the trick if you’re going to recycle the content wont be available in your computer.