AWS Toolkit for Jetbrains User Guide AWS Toolkit for Jetbrains User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Said GUERRAB
Said GUERRAB CONTACT 404-5100 Boulevard Pie IX E-mail: [email protected] H1X 2B6 Website: www.sguerrab-developper.com Montreal (QC) Phone: 438-935-8707 SUMMARY 05 years of experience designing and developing websites. Bilingual French-English. Implementation of numerous IT projects within the school. Design and implementation of websites in PHP, MySQL, JSP, HTML5, CSS3, Sass, Less, Stylus, and JavaScript, Bootstrap, D3.js, MVC framworks (PHP Laravel), Photoshop... Web project management (specifications, deadlines, risks management...). Audio editing, video editing, and graphic design. SEO for websites Autonomous, organized, have a team spirit, available, highly motivated, adaptable to new situations, can work under pressure. TECHNICAL Operating Systems: Windows, Linux , Mac OS X SKILLS Programming Languages: Java, JSP, Ruby, Cobol, VB.NET, C++, PHP, HTML/CSS, JavaScript Markup Languages:JSON, YAML, XML CSS Preprocessors: Sass CSS, Stylus CSS, Less CSS Editors & IDEs: Eclipse, PHPStorm, NetBeans, RubyMine, Sublime Text… Version Control Systems: GIT, Github, Bitbucket, SVN Frameworks & libraries: Laravel, JQuery, Bootstrap, D3.js... CMS: Drupal, Joomla, WordPress Server management: Apache, Tomcat, Glassfish, CPanel, DNS Database: Oracle SQL, PL/SQL, SQL Server, MySQL, Access. Office Applications:Excel, Word, Powerpoint and LibreOffice suite Other software: Microsoft Project, Microsoft Visio, Oracle Forms, Oracle Reports Graphism: Photoshop, The Gimp, Illustrator, Inkscape et InDesign. Maintening:Software (installation and updating). PROFESSIONAL Identify the needs of clients. SKILLS Analyze specifications of the website. Establish a site plan with the design of each page. Choosing tools for the development of the site . Coordinate the collection and the organization of information to include on the site. Collaborate in the definition of the architecture of the site and the choice of navigation scenarios. -
Overall Features Performance Price
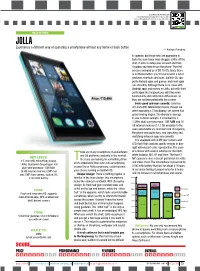
Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE JOLLA Experience a different way of operating a smartphone without any home or back button — Ashok Pandey to operate, but those who are upgrading to taste the new flavor may struggle a little. At the start, it asks to setup your account and then, it guides you how to use the phone. The first screen reminded us of BB 10 OS. Since there is no Home button, you’ll have to learn a lot of gestures, shortcuts and cues. Sailfish OS sup- ports Android apps and games, and most apps run smoothly. Although there is no issue with Android apps and games on Jolla, but with third party apps like facebook you will find some functionality and notification differences, as Price: `15,490 they are not integrated with the system. Feels good and runs smooth: Jolla has 4.5-inch qHD (960x450p) display, though we were expecting a 720p display, yet screen has good viewing angles. The display is average to use in direct sunlight. It is backed by a 1.4GHz dual-core processor, 1GB RAM and 16 GB internal memory (13.7 GB available to the user) expandable via microSD card. Navigating the phone was quite easy, and launching and switching between apps was smooth. It is equipped with 8 MP rear camera with LED flash that captures quality images in day- light with decent color reproduction. The cam- here are many smartphone manufacturers era comes with several settings for the flash, and OS platforms available in the market. -
Fira Code: Monospaced Font with Programming Ligatures
Personal Open source Business Explore Pricing Blog Support This repository Sign in Sign up tonsky / FiraCode Watch 282 Star 9,014 Fork 255 Code Issues 74 Pull requests 1 Projects 0 Wiki Pulse Graphs Monospaced font with programming ligatures 145 commits 1 branch 15 releases 32 contributors OFL-1.1 master New pull request Find file Clone or download lf- committed with tonsky Add mintty to the ligatures-unsupported list (#284) Latest commit d7dbc2d 16 days ago distr Version 1.203 (added `__`, closes #120) a month ago showcases Version 1.203 (added `__`, closes #120) a month ago .gitignore - Removed `!!!` `???` `;;;` `&&&` `|||` `=~` (closes #167) `~~~` `%%%` 3 months ago FiraCode.glyphs Version 1.203 (added `__`, closes #120) a month ago LICENSE version 0.6 a year ago README.md Add mintty to the ligatures-unsupported list (#284) 16 days ago gen_calt.clj Removed `/**` `**/` and disabled ligatures for `/*/` `*/*` sequences … 2 months ago release.sh removed Retina weight from webfonts 3 months ago README.md Fira Code: monospaced font with programming ligatures Problem Programmers use a lot of symbols, often encoded with several characters. For the human brain, sequences like -> , <= or := are single logical tokens, even if they take two or three characters on the screen. Your eye spends a non-zero amount of energy to scan, parse and join multiple characters into a single logical one. Ideally, all programming languages should be designed with full-fledged Unicode symbols for operators, but that’s not the case yet. Solution Download v1.203 · How to install · News & updates Fira Code is an extension of the Fira Mono font containing a set of ligatures for common programming multi-character combinations. -

Pycharm Reference Card.Pdf
Default Keymap Default Keymap Default Keymap Editing Compile and Run Usage Search Ctrl + Space Basic code completion (the name of any class, method Alt + Shift + F10 Select configuration and run Alt + F7 / Ctrl + F7 Find usages / Find usages in file or variable) Alt + Shift + F9 Select configuration and debug Ctrl + Shift + F7 Highlight usages in file Ctrl + Alt + Space Class name completion (the name of any project class Shift + F10 Run Ctrl + Alt + F7 Show usages independently of current imports) Shift + F9 Debug Refactoring Ctrl + Shift + Enter Complete statement Ctrl + Shift + F10 Run context configuration from editor Ctrl + P Parameter info (within method call arguments) F5 Copy Debugging Ctrl + Q Quick documentation lookup F6 Move Shift + F1 External Doc F8 Step over Alt + Delete Safe Delete Ctrl + mouse over code Brief Info F7 Step into Shift + F6 Rename Ctrl + F1 Show descriptions of error or warning at caret Shift + F8 Step out Ctrl + F6 Change Signature Alt + Insert Generate code... Alt + F9 Run to cursor Ctrl + Alt + N Inline Ctrl + O Override methods Alt + F8 Evaluate expression Ctrl + Alt + M Extract Method Ctrl + Alt + T Surround with... Ctrl + Alt + F8 Quick evaluate expression Ctrl + Alt + V Introduce Variable Ctrl + / Comment/uncomment with line comment F9 Resume program Ctrl + Alt + F Introduce Field Ctrl + Shift + / Comment/uncomment with block comment Ctrl + F8 Toggle breakpoint Ctrl + Alt + C Introduce Constant Ctrl + W Select successively increasing code blocks Ctrl + Shift + F8 View breakpoints Ctrl + Alt + P Introduce -

Syllabus Instructor
Syllabus Instructor That's me! I am Eric Reed, and you can email me at [email protected] (mailto:[email protected]) . It's easiest for me if you ask questions through the private or public message center here in the course, and only use email if you have trouble logging in. I get a huge amount of email and there's a chance that a time critical question will get lost if you email me. Why do I get so much email? I am also the STEM Center (http://foothill.edu/stemcenter) director here at Foothill. Which, by the way, is a good place to know. More about that later. I teach both math and computer science. I hold an M.S. in math from CSU East Bay and an M.S. in computer science from Georgia Tech. Feel free to ask me about either one. What you really need to know is that I am glad you are here, and my goal is your success in this course. Office Hours You can find me online on Sundays from 10am11am at foothill.edu/stemcenter/onlinecs We will hold two office hours on campus as well: Tuesday 11AM Noon Room 4412 Friday 6pm7pm Room 4601 You may always feel free to contact me for an appointment. Oh, what about this course? CS 3C is an advanced lower division computer programming course using the Python language. The truth is, the course is more about the computer science concepts than the language. We will learn about time complexity (BigO notation), data structures like trees and hash tables, and topics related to algorithms like sorts and minimum spanning trees To succeed in this class, you need a solid understanding of Python structure and statements, and some experience with object oriented design. -

A Comparison of C++, C#, Java, and PHP in the Context of E-Learning
A Comparison of C++, C#, Java, and PHP in the context of e-learning MIKAEL OLSSON KTH Information and Communication Technology Master of Science Thesis Stockholm, Sweden 2009 TRITA-ICT-EX-2009:8 A Comparison of C++, C#, Java, and PHP in the context of e‐learning Mikael Olsson April 30, 2009 Master’s Thesis in Computer Science Royal Institute of Technology Examiner: Prof. Gerald Q. Maguire Jr. ‐ i ‐ Abstract The first part of this master thesis presents an effective method for producing video tutorials. This method was used during this thesis project to create tutorials on the e- learning site PVT (http://www.programmingvideotutorials.com). Part one also discloses how the production method was developed and how tutorials produced using this method compare to professional video tutorials. Finally, it evaluates the result of this thesis work and the efficiency of the production method. The second part of this thesis compares the syntactical similarities and differences between four of the languages taught via video tutorials for PVT. These languages are: C++, C#, Java, and PHP. The purpose of this comparison is to provide a bridge for programmers knowing one of these languages to rapidly learn one or more of the other languages. The reason why this would be necessary is because there is no single language suited for every area of software development. Knowing a multitude of languages gives a programmer a wider range of job opportunities and more choices in how to solve their problems. Part two of the thesis also includes a comparison of Java and C# in the context of a video tutorial series that shows how to build a basic text editor. -

Parallel Computing in Python
2017 / 02 / Parallel Computing 09 in Python Reserved All Rights PRACE Winter School 2017 @ Tel-Aviv/Israel Mordechai Butrashvily All material is under 1 Few Words • I’m a graduate student @ Geophysics, Tel-Aviv University • Dealing with physics, geophysics & applied mathematics 2017 / 02 / • Parallel computing is essential in my work 09 • Participated in PRACE Summer of HPC 2013 • Don’t miss a chance to take part Reserved All Rights • Registration ends by 19/2 • Apply here: • https://summerofhpc.prace-ri.eu/apply 2 • You would enjoy it, and if not I’m here to complain… Why Are We Here? • Python is very popular, simple and intuitive • Increasing use in many fields of research & industry 2017 / • Open-source and free 02 / • Many toolboxes available in almost every field 09 • NumPy/SciPy are prerequisite for scientists • Replacement for MATLAB/Mathematica (to some extent) All Rights Reserved All Rights • Natural to ask if parallel computing can be simpler too • Indeed yes! • And also take advantage of existing C/Fortran code 3 (My) Audience Assumptions • Some may know python • But not much of its multiprocessing capabilities 2017 / 02 / • Some may know parallel computing 09 • But not quite familiar with python • Working in Linux environments Reserved All Rights • Not mandatory but highly advised • Knowing a descent programming language 4 (My) Workshop Goals • Don’t worry 2017 / • The workshop was designed for introductory purposes 02 / • First basic theory, then practical hands-on session 09 • Hands-on will be in different levels (3 as usual) -

Resharper Benefits for You and Your Business
ReSharper Benefits For You and Your Business ReSharper is the most intelligent productivity tool for .NET development. However, it proves to be a great asset not only for software engineers, but also for your whole software development business. ReSharper brings the necessary intelligence, code insight and productivity to give your business a competitive advantage on three organization levels: • Benefits for developers • Benefits for project managers • Benefits for business These benefits only get better with each new ReSharper release, due to ongoing performance improvements and added functionality. For example, recent versions of ReSharper have introduced ReSharper Build, which finds ways to reduce compi- lation time in Visual Studio, as well as new code inspections and refactorings. Even as Microsoft makes improvements to new releases of Visual Studio, ReSharper stays way ahead of the curve. Benefits for business Benefits for project managers Benefits for developers ReSharper Benefits For You and Your Business 1 www.jetbrains.com/resharper Benefits for developers • Save time on compilation, locating & fixing errors – ReSharper instantly detects and highlights errors in your code and allows automatic corrections for most errors • Automate routine tasks – Quickly create methods, properties, variables or classes from their usages, generate constructors, properties, delegating and equality members; implement and override members; and much more • Get useful hints right when you need them – IntelliSense, including code completion and quick parameter -

Scratch, Blocky & Co., Blocksysteme Zum Programmieren
Notizen Lothar Griess • 26. Mai 2018 Scratch, Blocky & Co., Blocksysteme zum Programmieren Scratch-Alternativen, … https://wiki.scratch.mit.edu/wiki/Alternatives_to_Scratch HTML5 als Grundlage wär besser, die Zukunft von Flash ist unklar. Liste der Modifikationen ... https://scratch-dach.info/wiki/Liste_der_Modifikationen Enchanting (Scratch Modifikation) ... https://scratch-dach.info/wiki/Enchanting_(Scratch_Modifikation) Beetle Blocks ist wie Scratch oder BlocksCAD für 3D-Grafiken... https://scratch-dach.info/wiki/Beetle_Blocks Beetle Blocks GitHub Repository ... https://github.com/ericrosenbaum/BeetleBlocks Beetle Blocks (3D-Design), … http://beetleblocks.com/ Mod Share … z.B.: Supported Scratch-Modifications … https://wiki.scratch.mit.edu/wiki/Mod_Share Scratch … https://wiki.scratch.mit.edu/wiki/Scratch Snap … https://wiki.scratch.mit.edu/wiki/Snap_(Scratch_Modification) Bingo … https://wiki.scratch.mit.edu/wiki/Bingo_(Scratch_Modification) Panther … https://wiki.scratch.mit.edu/wiki/Panther_(Scratch_Modification) Insanity … https://wiki.scratch.mit.edu/wiki/Insanity_(Scratch_Modification) … weitere: Stack, Kitcat, Ghost, Streak • • • Blockly is used by hundreds of projects, most of them educational: ... https://developers.google.com/blockly/ Blockly, RoboBlockly, ... https://code.org/learn Google Education, 1 Stunde, ... https://hourofcode.com/blockly Got PCs with slow (or non-existent) internet access? Download the Blockly tutorials that were the precursor of the Code.org tutorials - a single 3MB ZIP file can be loaded onto any computer or used off a memory stick Blockly Games … https://blockly-games.appspot.com/ App Inventor … http://appinventor.mit.edu/explore/ Code (div.) … https://code.org/ Ozo Blockly (Mini-Roboter) - Ozobot Bit robot using the OzoBlockly editor. … http://ozoblockly.com/ micro:bit (Raspberrs Pi, MicroPython) … http://microbit.org/ BlocklyProp … www.parallax.com/product/program-blocklyprop wonder workshop (dash-Roboter) … www.makewonder.de Robertar, NEPO (div.) … https://lab.open-roberta.org// Made w/ Code (div. -
Xdebug Tutorial
Welcome! Xdebug tutorial PHP Konferenca - Ljubljana, Slovenia Derick Rethans - [email protected] - twitter: @derickr http://derickrethans.nl/talks.html About Me Derick Rethans ● Dutchman living in London ● PHP development ● Author of the mcrypt, input_filter, dbus, translit and date/time extensions ● Author of Xdebug ● Contributor to the Apache Zeta Components Incubator project (formerly eZ Components) ● Freelancer doing PHP (internals) development I Do Not Need a Debugger ● printf(), var_dump() and echo are good enough I Do Not Need a Debugger I Do Need a Debugger ● Xdebug: An Open Source debugging tool ● About 8 years old ● Works on "every" operating system ● Version 2.1 released about three months ago This Tutorial ● Installation overview ● Downloading, compiling and configuring Xdebug ● Basic function overview ● Playing with settings, stack traces and function traces break ● Profiling ● Profiling your own code ● Code coverage ● (Setting up code-coverage with PHP Unit) break ● Debugging ● Setting up your IDE for debugging Installation The Xdebug extension ● Zend extension, and not a PHP extension ● Xdebug is very PHP-version sensitive ● Different compilers under Windows ● Debug/non-debug ● Threadsafe or not In PHP 5.1 and 5.2: zend_extension=/local/php/lib/php/extensions/no-debug-non-zts- 20090626/xdebug.so zend_extension_ts=/local/php/lib/php/extensions/debug-zts- 20090626/xdebug.so zend_extension_debug=/local/php/lib/php/extensions/debug-non-zts- 20090626/xdebug.so In PHP 5.3: zend_extension=/local/php/lib/php/extensions/no-debug-non-zts- -

Kotlin 1.4 Online Event October 14, 2020 Kathrinpetrova
Kotlin 1.4 Online Event It's time for Kotlin Multiplatform Mobile! Ekaterina Petrova KathrinPetrova October 14, 2020 I love mobile development, but I can’t stand writing the Me neither! same code twice! UI Views Presentation Presenters, View Models, Controllers Business / Domain Entities, Use Cases, Interactors Data / Core Repositories, HTTP Clients, Cache UI centric UI Views Presentation Presenters, View Models, Controllers Business / Domain Entities, Use Cases, Interactors Data / Core Repositories, HTTP Clients, Cache ⚙ Core centric UI centric UI Views React Native Flutter Presentation Presenters, View Models, Controllers Xamarin Forms Business / Domain Entities, Use Cases, Interactors Data / Core Repositories, HTTP Clients, Cache ⚙ Core centric UI centric UI Views React Native Flutter How can I share Presentation business logic Presenters, View Models, Controllers Xamarin Forms and core code? Business / Domain Entities, Use Cases, Interactors Data / Core Repositories, HTTP Clients, Cache ⚙ Core centric UI centric UI for thin clients, Views React Native simple apps, MVP Flutter Presentation Presenters, View Models, Controllers Xamarin Forms Business / Domain Entities, Use Cases, Interactors Data / Core Repositories, HTTP Clients, Cache ⚙ Core centric UI centric UI for thin clients, Views React Native simple apps, MVP Flutter Presentation Presenters, View Models, Controllers Xamarin Forms Business / Domain Entities, Use Cases, Interactors for complex apps, Fat clients, Data / Core strict requirements Repositories, HTTP Clients, -

NET Core, ASP.NET Core, and ASP.NET Core MVC Brave New World Outline
.NET Core, ASP.NET Core, and ASP.NET Core MVC brave new world Outline • Motivation • .NET Core • ASP.NET Core • ASP.NET Core MVC Motivation • .NET has a strong history • Very popular • Lots of investments • There is more than just Windows • Many more platforms, devices, and clouds • .NET is evolving • .NET needs to learn to run in more places • .NET needs modern tooling .NET runtimes target a platform • .NET Framework • Windows-only • .NET Core • Cross-platform runtime • .NET Native (UWP) • Mono • Windows Phone • More… .NET Core : next gen .NET for server apps • Cross platform • Windows, Linux, Mac, FreeBSD • Portable • Can be ~/bin deployed • Can be user or machine installed as well • Open source • https://github.com/dotnet/coreclr • Contains core runtime and mscorlib (e.g. GC, JIT, BCL) • Does not contain many frameworks (e.g. WCF, WPF) Development ecosystem • SDK • Command-line tooling (dotnet) • Project system • File-system based project system (project.json) • Runtime, libraries, and packaging • NuGet-focused • Editors/IDEs • Any text editor (VS Code, Emacs, Sublime, etc) and OmniSharp (OSS) • Visual Studio (Microsoft) • Project Rider (JetBrains) Installing .NET SDK • Use nightly builds (until RC2 is released) • https://github.com/dotnet/cli dotnet : command line tool • Create new project • Install NuGet dependencies • Build application • Load .NET and run application • Package library • Publish application dotnet new • Creates new project • program.cs • project.json • Console-based application using System; namespace ConsoleApplication