Report for Emwis-Mt.Org
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
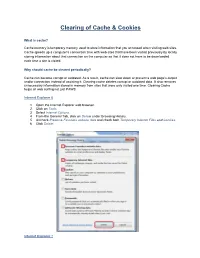
Clearing of Cache & Cookies
Clearing of Cache & Cookies What is cache? Cache memory is temporary memory used to store information that you accessed when visiting web sites. Cache speeds up a computer’s connection time with web sites that have been visited previously by locally storing information about that connection on the computer so that it does not have to be downloaded each time a site is visited. Why should cache be cleared periodically? Cache can become corrupt or outdated. As a result, cache can slow down or prevent a web page’s output and/or connection instead of assisting it. Clearing cache deletes corrupt or outdated data. It also removes unnecessary information stored in memory from sites that were only visited one time. Clearing Cache helps all web surfing not just PAWS. Internet Explorer 8 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Select Internet Options. 4. From the General Tab, click on Delete under Browsing History. 5. Uncheck Preserve Favorites website data and check both Temporary Internet Files and Cookies. 6. Click Delete. Internet Explorer 7 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. Click on Delete under Browsing History. 5. Click Delete cookies. 6. When prompted, click Yes. 7. Click on Delete Internet Files. 8. When prompted, click Yes. 9. Click Close. 10. Click OK. 11. Close and reopen the browser for the changes to go into effect. Internet Explorer 6 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. -

Browser Wars
Uppsala universitet Inst. för informationsvetenskap Browser Wars Kampen om webbläsarmarknaden Andreas Högström, Emil Pettersson Kurs: Examensarbete Nivå: C Termin: VT-10 Datum: 2010-06-07 Handledare: Anneli Edman "Anyone who slaps a 'this page is best viewed with Browser X' label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of read- ing a document written on another computer, another word processor, or another network" - Sir Timothy John Berners-Lee, grundare av World Wide Web Consortium, Technology Review juli 1996 Innehållsförteckning Abstract ...................................................................................................................................... 1 Sammanfattning ......................................................................................................................... 2 1 Inledning .................................................................................................................................. 3 1.1 Bakgrund .............................................................................................................................. 3 1.2 Syfte ..................................................................................................................................... 3 1.3 Frågeställningar .................................................................................................................... 3 1.4 Avgränsningar ..................................................................................................................... -

Issues with Using IE9 Browser
NOTICE: Browser Compatibility Issues with Internet Explorer 9 VIPR uses eAuthentication for authentication and the eAuth system is most compatible with Internet Explorer 8. Therefore, IE8 is the preferred browser for use with VIPR. Older versions of Internet Explorer (IE6, IE7) as well as the current version of Mozilla Firefox are working options also. If a customer is using IE9 and having issues, there are several options available to the user in this case: Option 1: Change IE9 to browse in IE8 mode • Open IE9 and hit the F12 key (or Tools > Developer Tools Menu). Click Browser Mode and select IE8. Try again. Option 2: Download Mozilla Firefox, make it your default browser, and try again • Mozilla Firefox can be downloaded from http://www.mozilla.org/en-US/firefox/new/ • To make Firefox the default browser: 1. At the top of the Firefox window, click on the Firefox button (Tools menu in Windows XP) and then click Options. 2. Select the Advanced panel, then click the General tab, and then click Check Now. 3. Select Yes to set Firefox as your default browser. Option 3: Rollback from IE9 to IE8 1. Open the Control Panel. Click on Programs and Features. This may be called Add/Remove programs if you are using an older version of Windows. 2. Click on View Installed Updates in the left pane. 3. Right click on Windows Internet Explorer 9 and select Uninstall. 4. Restart your computer when prompted and it should now be running IE8. If you continue to have issues with logging into VIPR, please contact the IIA Helpdesk at 866-224-7677, or by e-mail at [email protected]. -

Böngésző Programok 23. Tétel
23.tétel 1.0 Böngész ő programok használata, összehasonlítása. Az információ keresés technikái. Bogdán;Sleisz Böngész ő programok (Használata, összehasonlítása. Az információ keresés technikái) 23. tétel Az Internet kialakulása 20. század második felére helyezhet ő. Az ARPA rendszerb ől fejl ődött tovább az USA-ban, azóta folyamatosan fejlesztgetik a különböz ő protokollokat, illetve technológiákat, az adatforgalom sebességének növelése érdekében. Komoly tévhitet képez a világban, hogy az Internet az a böngész őben megjeleníthet ő weboldalak összessége. Nagy tévedés, ugyanis ez csak a HTTP protokoll által szolgáltatott tartalom, amely a teljes internetes adatforgalomnak kevesebb, mint az 1/10-ét képezi. Az internetet úgy kell elképzelni, mint egy hardvereszközt, ami az egész világot lefedi, a rajta elérhet ő szolgáltatásokat pedig nevezzük "szoftvereknek". Kétségkívül az egyik legelterjedtebb szolgáltatás ("szoftver") a 80-as port -on kommunikáló HTTP protokoll, amihez tartozik egy kommunikációs nyelv is. A HTTP protokoll célja hagyományos esetben- a távoli "szerveren/kiszolgálón" elhelyezked ő weboldal letöltése a helyi számítógépre. 1. A böngész ő a HTTP kommunikációs nyelven megfogalmazott kérést küld a szerver felé, hogy szeretnénk megjeleníteni a kért weboldalt 2. A szerver válaszol. Többféle üzenetet küldhet vissza a böngész őnek, és minden üzenethez tartozik egy azonosító szám is, úgynevezett Status Code. A legismertebb visszatérési érték talán a Not Found (a keresett weboldal nem található), melynek Status Code-ja a 404. Ilyet könnyedén el őidézhetünk, ha pl. nem létez ő oldalt próbálunk letölteni. A leggyakoribb azonban, ha a 200-as üzenetet kapjuk vissza, vagyis megjelenik az oldal. 3. Ezek után a böngész ő elkezdi letölteni a kért oldal forráskódját . A forráskód egy olyan leíró kód nagyrészt HTML nyelven, amely leírja, hogyan néz ki a weboldal. -

Reference Manual for Skills Development Facilitators
Reference Manual for Skills Development Facilitators 2020 The MICT SETA SDF Reference Manual 2020 Table of Contents Our Vision: ........................................................................................................................................ 3 Our Mission: ..................................................................................................................................... 3 Our Values ........................................................................................................................................ 3 PART A .............................................................................................................................................. 4 Introduction and Background Information ..................................................................................... 5 Acronyms and Definitions ................................................................................................................ 7 Process Information ......................................................................................................................... 8 The Organizing Framework for Occupations (OFO) ..................................................................... 17 Expenses that may be included in the ATR/PTR and WSP/PTP .................................................. 26 The MICT SETA Perspective .......................................................................................................... 27 Applying for Discretionary Grant Funding .................................................................................. -

Ÿþh Y P E R I O N I N S T a L L a T I O N S T a R T H E R E R E L E a S E 9 . 3
Hyperion Installation Start Here RELEASE 9.3.3 Updated: June 2011 Hyperion Installation Start Here, 9.3.3 Copyright © 2007, 2011, Oracle and/or its affiliates. All rights reserved. Authors: EPM Information Development Team Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS: Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

CL5708I / CL5716I 8 / 16-Port Single Rail LCD KVM Over IP Switch User Manual CL5708I / CL5716I User Manual
EMC Information CL5708I / CL5716I 8 / 16-Port Single Rail LCD KVM over IP Switch User Manual CL5708I / CL5716I User Manual Compliance Statements FEDERAL COMMUNICATIONS COMMISSION INTERFERENCE STATEMENT This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the interference at his own expense. The device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. FCC Caution Any changes or modifications not expressly approved by the party responsible for compliance could void the user's authority to operate this equipment. Warning Operation of this equipment in a residential environment could cause radio interference. Achtung Der Gebrauch dieses Geräts in Wohnumgebung kann Funkstörungen verursachen. KCC Statement ii CL5708I / CL5716I User Manual Industry Canada Statement This Class A digital apparatus complies with Canadian ICES-003. RoHS This product is RoHS compliant. About this Manual This user manual is provided to help you get the most out of your LCD KVM over IP switch. -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -

Basic Browser Maintenance for Internet Explorer 6
Basic Browser Maintenance Contents Windows Basic Browser Maintenance .......................................................................................... 2 Internet Explorer 9 ................................................................................................................................ 2 Internet Explorer 10 or 11 ..................................................................................................................... 2 Firefox (Current Version) ..................................................................................................................... 3 Google Chrome (Current Version) ....................................................................................................... 3 Mac Basic Browser Maintenance .................................................................................................. 4 Safari 5, 6, 7 .......................................................................................................................................... 4 Firefox (Current Version) ..................................................................................................................... 4 Google Chrome (Current Version) ....................................................................................................... 4 Last Updated Summer 2014 [1] Windows Basic Browser Maintenance Internet Explorer 9 1. In Internet Explorer, click Tools > Internet Options (If no Tools tab showing, click gear icon, click Safety and click Delete Browsing History and skip to step -

Policy Center Requirements Operating Systems: the Following Operating Systems Are Recommended to Access Policy Center
Policy Center Requirements Operating Systems: The following operating systems are recommended to access Policy Center. Operating Systems Supported: Microsoft Windows Vista SP2 Microsoft Windows 7 Microsoft Windows 8 Microsoft Windows 10 * *There are some known issues with these Operating Systems. For more details, see ‘Known Issues’ section below. Internet Browsers: The following browsers are required to access Policy Center. If you currently use an older Microsoft browser than listed, or a non-Microsoft browser, you may receive other errors or experience other unknown issues. Browsers Supported: 32-bit Microsoft Internet Explorer 7+ 32-bit Microsoft Internet Explorer 8+ * 32-bit Microsoft Internet Explorer 9+ * 32-bit Microsoft Internet Explorer 10+ * 32-bit Microsoft Internet Explorer 11+ * *There are some known issues with these browsers. For more details, see ‘Known Issues’ section below. Additional Requirements:** Adobe Reader version 7 or higher (or a similar PDF viewer) Guidewire Document Assistant ActiveX plug-in **Required to view system generated documents. Microsoft Office 2007 or 2010 is suggested to view all other documents. You are responsible for uploading policy documents to Policy Center before and after submission of the application. Upload only what is needed. Most file types are acceptable. All documents will be retained according to TWIA’s document retention policy. Claims Center Requirements Internet Browsers: To provide the best user experience it is recommended to use browsers that support HTML5 & CSS3. Claims Center is a web application accessed through a web browser. There are tiered levels of support for web browsers: Tier 1 includes browsers used in testing environments. Tier 2 includes browsers that can present the core functionality and content, but may not be pixel perfect and may not to perform as well as Tier 1 browsers. -

Effective Web Design, Second Edition
Effective Web Design Effective Web Design, Second Edition Ann Navarro SYBEX® Associate Publisher: Cheryl Applewood Contracts and Licensing Manager: Kristine O'Callaghan Acquisitions and Developmental Editor: Raquel Baker Editors: Joseph A. Webb, James A. Compton, Colleen Wheeler Strand Production Editor: Dennis Fitzgerald Technical Editor: Marshall Jansen Book Designer: Maureen Forys, Happenstance Type-O-Rama Graphic Illustrator: Tony Jonick Electronic Publishing Specialist: Maureen Forys, Happenstance Type-O-Rama Proofreaders: Nelson Kim, Nancy Riddiough, Leslie E.H. Light Indexer: Ann Rogers CD Coordinator: Christine Harris CD Technician: Kevin Ly Cover Designer: Design Site Cover Illustrator/Photographer: Dan Bowman Copyright © 2001 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. World rights reserved. page 1 Effective Web Design The author(s) created reusable code in this publication expressly for reuse by readers. Sybex grants readers limited permission to reuse the code found in this publication or its accompanying CD-ROM so long as (author(s)) are attributed in any application containing the reusable code and the code itself is never distributed, posted online by electronic transmission, sold, or commercially exploited as a stand- alone product. Aside from this specific exception concerning reusable code, no part of this publication may be stored in a retrieval system, transmitted, or reproduced in any way, including but not limited to photocopy, photograph, magnetic, or other record, without the prior agreement and written permission of the publisher. An earlier version of this book was published under the title Effective Web Design © 1998 SYBEX Inc. Library of Congress Card Number: 2001088112 ISBN: 0-7821-2849-1 SYBEX and the SYBEX logo are either registered trademarks or trademarks of SYBEX Inc. -

Browser Security Comparison – a Quantitative Approach Page| I of V Version 0.0 Revision Date: 12/6/2011
Browser Security Comparison A Quantitative Approach Document Profile Version 0.0 Published 12/6/2011 Revision History Version Date Description 0.0 12/26/2011 Document published. Browser Security Comparison – A Quantitative Approach Page| i of v Version 0.0 Revision Date: 12/6/2011 Contents Authors .......................................................................................................................................................... v Executive Summary ....................................................................................................................................... 1 Methodology Delta ................................................................................................................................... 1 Results ....................................................................................................................................................... 2 Conclusion ................................................................................................................................................. 2 Introduction .................................................................................................................................................. 3 Analysis Targets ........................................................................................................................................ 4 Analysis Environment................................................................................................................................ 4 Analysis