Ÿþh Y P E R I O N I N S T a L L a T I O N S T a R T H E R E R E L E a S E 9 . 3
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
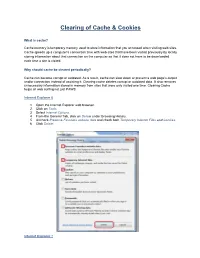
Clearing of Cache & Cookies
Clearing of Cache & Cookies What is cache? Cache memory is temporary memory used to store information that you accessed when visiting web sites. Cache speeds up a computer’s connection time with web sites that have been visited previously by locally storing information about that connection on the computer so that it does not have to be downloaded each time a site is visited. Why should cache be cleared periodically? Cache can become corrupt or outdated. As a result, cache can slow down or prevent a web page’s output and/or connection instead of assisting it. Clearing cache deletes corrupt or outdated data. It also removes unnecessary information stored in memory from sites that were only visited one time. Clearing Cache helps all web surfing not just PAWS. Internet Explorer 8 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Select Internet Options. 4. From the General Tab, click on Delete under Browsing History. 5. Uncheck Preserve Favorites website data and check both Temporary Internet Files and Cookies. 6. Click Delete. Internet Explorer 7 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. Click on Delete under Browsing History. 5. Click Delete cookies. 6. When prompted, click Yes. 7. Click on Delete Internet Files. 8. When prompted, click Yes. 9. Click Close. 10. Click OK. 11. Close and reopen the browser for the changes to go into effect. Internet Explorer 6 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. -

Browser Wars
Uppsala universitet Inst. för informationsvetenskap Browser Wars Kampen om webbläsarmarknaden Andreas Högström, Emil Pettersson Kurs: Examensarbete Nivå: C Termin: VT-10 Datum: 2010-06-07 Handledare: Anneli Edman "Anyone who slaps a 'this page is best viewed with Browser X' label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of read- ing a document written on another computer, another word processor, or another network" - Sir Timothy John Berners-Lee, grundare av World Wide Web Consortium, Technology Review juli 1996 Innehållsförteckning Abstract ...................................................................................................................................... 1 Sammanfattning ......................................................................................................................... 2 1 Inledning .................................................................................................................................. 3 1.1 Bakgrund .............................................................................................................................. 3 1.2 Syfte ..................................................................................................................................... 3 1.3 Frågeställningar .................................................................................................................... 3 1.4 Avgränsningar ..................................................................................................................... -

CL5708I / CL5716I 8 / 16-Port Single Rail LCD KVM Over IP Switch User Manual CL5708I / CL5716I User Manual
EMC Information CL5708I / CL5716I 8 / 16-Port Single Rail LCD KVM over IP Switch User Manual CL5708I / CL5716I User Manual Compliance Statements FEDERAL COMMUNICATIONS COMMISSION INTERFERENCE STATEMENT This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the interference at his own expense. The device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. FCC Caution Any changes or modifications not expressly approved by the party responsible for compliance could void the user's authority to operate this equipment. Warning Operation of this equipment in a residential environment could cause radio interference. Achtung Der Gebrauch dieses Geräts in Wohnumgebung kann Funkstörungen verursachen. KCC Statement ii CL5708I / CL5716I User Manual Industry Canada Statement This Class A digital apparatus complies with Canadian ICES-003. RoHS This product is RoHS compliant. About this Manual This user manual is provided to help you get the most out of your LCD KVM over IP switch. -

Effective Web Design, Second Edition
Effective Web Design Effective Web Design, Second Edition Ann Navarro SYBEX® Associate Publisher: Cheryl Applewood Contracts and Licensing Manager: Kristine O'Callaghan Acquisitions and Developmental Editor: Raquel Baker Editors: Joseph A. Webb, James A. Compton, Colleen Wheeler Strand Production Editor: Dennis Fitzgerald Technical Editor: Marshall Jansen Book Designer: Maureen Forys, Happenstance Type-O-Rama Graphic Illustrator: Tony Jonick Electronic Publishing Specialist: Maureen Forys, Happenstance Type-O-Rama Proofreaders: Nelson Kim, Nancy Riddiough, Leslie E.H. Light Indexer: Ann Rogers CD Coordinator: Christine Harris CD Technician: Kevin Ly Cover Designer: Design Site Cover Illustrator/Photographer: Dan Bowman Copyright © 2001 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. World rights reserved. page 1 Effective Web Design The author(s) created reusable code in this publication expressly for reuse by readers. Sybex grants readers limited permission to reuse the code found in this publication or its accompanying CD-ROM so long as (author(s)) are attributed in any application containing the reusable code and the code itself is never distributed, posted online by electronic transmission, sold, or commercially exploited as a stand- alone product. Aside from this specific exception concerning reusable code, no part of this publication may be stored in a retrieval system, transmitted, or reproduced in any way, including but not limited to photocopy, photograph, magnetic, or other record, without the prior agreement and written permission of the publisher. An earlier version of this book was published under the title Effective Web Design © 1998 SYBEX Inc. Library of Congress Card Number: 2001088112 ISBN: 0-7821-2849-1 SYBEX and the SYBEX logo are either registered trademarks or trademarks of SYBEX Inc. -

Browser Security Comparison – a Quantitative Approach Page| I of V Version 0.0 Revision Date: 12/6/2011
Browser Security Comparison A Quantitative Approach Document Profile Version 0.0 Published 12/6/2011 Revision History Version Date Description 0.0 12/26/2011 Document published. Browser Security Comparison – A Quantitative Approach Page| i of v Version 0.0 Revision Date: 12/6/2011 Contents Authors .......................................................................................................................................................... v Executive Summary ....................................................................................................................................... 1 Methodology Delta ................................................................................................................................... 1 Results ....................................................................................................................................................... 2 Conclusion ................................................................................................................................................. 2 Introduction .................................................................................................................................................. 3 Analysis Targets ........................................................................................................................................ 4 Analysis Environment................................................................................................................................ 4 Analysis -

Web Design.” I Found Books on Everything from HTML to XML and from Web Graphics to Web Usability
Free ebooks ==> www.ebook777.com Free ebooks ==> www.ebook777.com Web Design: A Beginner’s Guide Second Edition www.ebook777.com Free ebooks ==> www.ebook777.com About the Author Wendy Willard is a designer, consultant, writer, and educator who has been involved in web design for about 15 years. She is the author of HTML: A Beginner’s Guide, Fourth Edition, and other books. Wendy is a graduate of Art Center College of Design in Pasadena, California. About the Technical Editor Kathi McCracken-Dente is a user experience strategist with an expertise in designing for e-commerce, communities, and web applications. Before starting McCracken Design, a web design agency in Oakland, California, she was a designer at frog design, Addwater, and Intuit. Her clients include Yahoo!, Intuit, PowerReviews, and LeapFrog. She is a graduate of Duke University and Art Center College of Design. Free ebooks ==> www.ebook777.com Web Design: A Beginner’s Guide Second Edition Wendy Willard New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto Free ebooks ==> www.ebook777.com Copyright © 2010 by The McGraw-Hill Companies. All rights reserved. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher. ISBN: 978-0-07-170135-8 MHID: 0-07-170135-4 The material in this eBook also appears in the print version of this title: ISBN: 978-0-07-170134-1, MHID: 0-07-170134-6. -

Architectural Styles of Extensible REST-Based Applications
Institute for Software Research University of California, Irvine Architectural Styles of Extensible REST-based Applications Justin R. Erenkrantz University of California, Irvine [email protected] August 2006 ISR Technical Report # UCI-ISR-06-12 Institute for Software Research ICS2 110 University of California, Irvine Irvine, CA 92697-3455 www.isr.uci.edu www.isr.uci.edu/tech-reports.html Architectural Styles of Extensible REST-based Applications Justin R. Erenkrantz Institute for Software Research University of California, Irvine Irvine, CA 92697-3425 [email protected] ISR Technical Report # UCI-ISR-06-12 August 2006 Abstract: At the beginning of the World Wide Web (WWW or Web), there was no clear set of principles to guide the decisions being made by developers and architects. In these early days, a cacophony emerged without a clear direction to guide the evolution of the Web. If there was any direction during the inception of the Web, it was a weak focus on how communication might occur between machines on the Web and the content that was to be transferred. Within a matter of a few years, scalability and other design concerns threatened the future of the early Web - this led to the introduction of REpresentation State Transfer architectural style (REST). The REST style imposed constraints on the exchange of communication over the Web and provided guidance for further modifications to the underlying protocols. The introduction of REST, through the HTTP/1.1 protocol, restored order to the Web by articulating the necessary constraints required for participation. In this survey, we will characterize any environment that is governed by REST constraints to be in a RESTful world. -

The User Friendly Guide to INTERNET & COMPUTER TERMS
The User Friendly Guide to INTERNET & COMPUTER TERMS Charles Steed Gold Standard Press Inc. Reno, Nevada Copyright ã 2001 Charles Steed and Gold Standard Press Inc. Permission is granted to ALL USERS and readers to download, print and freely dis- tribute The User Friendly Guide To Internet & Computer Terms. No changes to this text is authorized. THIS TEXT MAY NOT BE SOLD EXCEPT BY AUTHORIZED AGENTS OR REPRESENTATIVES OF GOLD STANDARD PRESS INC. For information, contact Gold Standard Press Inc. 1475 Terminal Way, Suite E, Reno, Nevada 89502, tel. 360-482-2510. This book contains information gathered from many sources. It is published for gen- eral reference and not as a substitute for independent verification by users when circumstances warrant. It is sold with the understanding that neither the author nor publisher is engaged in rendering legal, psychological, accounting or professional advice. The publisher and author disclaim any personal liability, either directly or indirectly, for advice presented within. Although the author and publisher have used care and diligence in the preparation, and made every effort to ensure the accuracy and completeness of information contained in this book, we assume no responsibility for errors, inaccuracies, omissions, or any inconsistency herein. Any slights of people, places, publishers, books, or organizations are unintentional. The online version of this text has been slightly modified to faciliate easy download- ing. No significant differences from the printed version are present. Library of Congress -

IMI Release Notes Internal Market Information System
EUROPEAN COMMISSION DIRECTORATE-GENERAL INFORMATICS Information systems Directorate Brussels, April 2008 European Commission IMI Release Notes Internal Market Information System Information on IMI compatibility with internet browsers and supported platforms Version 1.100 Commission européenne, B-1049 Bruxelles / Europese Commissie, B-1049 Brussel - Belgium. Telephone: (32-2) 299 11 11. Commission européenne, L-2920 Luxembourg. Telephone: (352) 43 01-1. TABLE OF CONTENTS 1. INTRODUCTION .................................................................................................................................... 3 1.1. Purpose .................................................................................................................................................... 3 1.2. Scope ....................................................................................................................................................... 3 1.3. Overview ................................................................................................................................................. 3 2. ABOUT THIS RELEASE........................................................................................................................ 3 3. COMPATIBILITY AND SUPPORTED PLATFORMS ...................................................................... 3 3.1. Web browsers .......................................................................................................................................... 3 3.2. Screen resolution and -

インターネットマガジン1999年6月号―INTERNET Magazine No.53
最新最強のブラウザーとうたわれるインタ ーネットエクスプローラ5 をインストールして みて、「なあんだこれだ け? IE 4と変わら ないじゃん」とがっかりした人は多いのでは ないだろうか。これまで雑誌やウェブで紹介 集中企画 された新機能を見ても、今いちピンとこな いと思ってはいないだろうか。それもその はず、IE 5の便利さはちょっとやそっとで 本誌 は見つけられない。隠れた機能を探し出し、 チュー ン ア ップするのがIE 5活用のポイント だ。インストールしたそのままの状態で使い 続けるだけではもったいない。IE 5の実力 を限界まで引き出してみよう。それには本誌 だけでしか読めないとっておきのチューン ア 公開! ップ術 が 役 に立つだろう。 独占 塩田紳二+編集部 インターネットエクスプローラ5 ューンアップ! 192 INTERNET magazine 1999/6 インターネットマガジン/株式会社インプレスR&D ©1994-2007 Impress R&D INTERNET EXPLORER 5 tune UP! IE 5の本当の 「スゴさ」はここにある。 IE 5では、もっぱら移動ボタンやオートコンプリート機能ばかりが大きく取り上げら れているようだ。確かにユーザーがすばやく効率的にウェブにアクセスできる新機能 は重要だ。しかし、IE 5 で注目すべき点はそれだけだろうか。 かつて大きく宣伝されたチャンネルがIE 5 ではずされたことを考えてみよう。IE 4 では、ユーザーが黙っていてもコンテンツ が自動的にやってくるプッシュ機能に期待が集まった。しかしプッシュは結局流行しなかった。IE 5 はユーザーに積極性を 求めるようになった。自分なりの使いこなし方を見つければそれだけ便利さが増すのがIE 5 の本当の「すごさ」だ。 カスタマイズが柔軟にできる! INTERNET EXPLORER 5 tune UP! ツールバーのボタンが変更できるようになったことに代表されるように、 SP.194 IE 5ではユーザーインターフェイスを自在にカスタマイズできる。イン 1. ストールしたらまず画面の構成を自分好みに変えてみよう。カスタマ 2. SP.196 イズできるのはインターフェイスだけではない。インストールするコン 7. SP.206 ポーネントは細かく選べるようになったし、アドインソフトも豊富に用 意されている。アウトルックエクスプレス5 の振り分け機能は大幅に向 8 . SP.208 上した。ユーザーが上手に設定すればそれだけIE 5 を便利なブラウザ ーに育てることができる。 ウェブ上 のサービスと連 携 できる! INTERNET EXPLORER 5 tune UP! IE 5の目玉機能の1つがウェブを見ながらニュースや音楽を聴けるラジ オバーだ。しかし実際にはラジオバーの本当の機能は「ラジオステー 3 . SP.198 ションガイド」にあると言っていい。またアドレスバーやエクスプロー ラバーを使った検索機能もエキサイトやライコスといった検索サイト 4. SP.200 と結び付いたものだ。関連サイト機能はアレクサ社の技術を使ってい るし、エクスプローラバーにウェブサイトの情報を埋め込むアドインソ フトもある。IE 5ではこれまで以上にウェブ上の各種のサービスと連携 する機能が強化されている。 オフィスでもモバイルで も 使 える! INTERNET EXPLORER 5 tune UP! ブラウザーを漠然とウェブを見て回るために使うだけではつまらない。 役立つ情報を効率よく保管し、整理して再利用するためのツールがIE 5 . SP.202 -

Różnice W Renderingu Witryn Www W Konkurencyjnych Przeglądarkach I Sposoby Ich Niwelowania
POLITECHNIKA SZCZECIŃSKA WYDZIAŁ INFORMATYKI Marcin Wichary RÓŻNICE W RENDERINGU WITRYN WWW W KONKURENCYJNYCH PRZEGLĄDARKACH I SPOSOBY ICH NIWELOWANIA Szczecin 2001 SPIS TREŚCI WSTĘP.........................................................................................4 1. HTML – JĘZYK I PRZEGLĄDARKI........................................6 1.1. Rozwój HTML i pokrewnych technologii ......................................6 1.2. Rozwój przeglądarek ....................................................................10 1.3. Udział przeglądarek w rynku........................................................18 1.4. Sposoby tworzenia serwisu WWW...............................................22 2. RÓŻNICE W INTERPRETACJI HTML ..................................28 2.1. Czcionki .......................................................................................29 2.2. Tabele...........................................................................................32 2.3. CSS...............................................................................................40 2.4. JavaScript .....................................................................................43 2.5. Ramki...........................................................................................44 2.6. Filtry.............................................................................................47 2.7. Tagi właściwe tylko dla konkretnych przeglądarek ......................48 2.8. Elementy graficzne.......................................................................51 -

Mozilla Firefox Project a Mozilla Alapítvány Egy Non-Profit Szervezet, Mely Támogatja És Fejleszti a Nyílt Forráskódú Mozilla Projectet
Debreceni Egyetem Informatika Kar Modern böngészők a ma Világának A böngészők technológiai fejlődésének elemzése Témavezető: Készítette: Dr. Hajdu András Benkő Péter Egyetemi Adjunktus Gazdaságinformatikus (BSc) Debrecen 2010 Tartalomjegyzék BEVEZETÉS ...................................................................................................................... 3 1. A BÖNGÉSZŐK SZÜLETÉSE ...................................................................................... 6 1.1 AZ INTERNET HAJNALÁN ..................................................................................... 7 1.2 A BÖNGÉSZŐK KORÁNAK KEZDETE: MOSAIC ÉS NETSCAPE ................................... 9 2. A MICROSOFT URALOM ÉS AZ INTERNET EXPLORER SOROZAT ............... 11 2.1 INTERNET EXPLORER 1.0. .................................................................................. 12 2.2 INTERNET EXPLORER 2.0 .................................................................................... 13 2.3 INTERNET EXPLORER 3.0. .................................................................................. 13 2.4 A BÖNGÉSZŐ HÁBORÚ KEZDETE ......................................................................... 14 2.5 INTERNET EXPLORER 4.0. .................................................................................. 15 2.6 INTERNET EXPLORER 5.0. .................................................................................. 17 2.7 INTERNET EXPLORER 6.0. .................................................................................. 18 2.8 A MICROSOFT