Netshred X Reviewer's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Cache Files Detect and Eliminate Privacy Threats
Award-Winning Privacy Software for OS X Every time you surf the web or use your computer, bits of Recover Disk Space data containing sensitive information are left behind that Over time, the files generated by web browsers can start could compromise your privacy. PrivacyScan provides to take up a large amount of space on your hard drive, protection by scanning for these threats and offers negatively impacting your computer’s performance. multiple removal options to securely erase them from PrivacyScan can locate and removes these space hogs, your system. freeing up valuable disk space and giving your system a speed boost in the process. PrivacyScan can seek and destroy internet files used for tracking your online whereabouts, including browsing history, cache files, cookies, search history, and more. Secure File Shredding Additionally, PrivacyScan can eliminate Flash Cookies, PrivacyScan utilizes advanced secure delete algorithms which are normally hidden away on your system. that meet and exceed US Department of Defense recommendations to ensure complete removal of Privacy Threat: Cookies sensitive data. Cookies can be used to track your usage of websites, determining which pages you visited and the length Intuitive Interface of time you spent on each page. Advertisers can use PrivacyScan’s award-winning design makes it easy to cookies to track you across multiple sites, building up track down privacy threats that exist on your system and a “profile” of who you are based on your web browsing quickly eliminate them. An integrated setup assistant and habits. tip system provide help every step of the way to make file cleaning a breeze. -
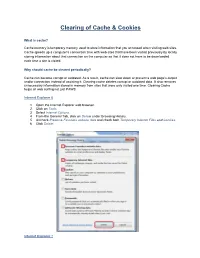
Clearing of Cache & Cookies
Clearing of Cache & Cookies What is cache? Cache memory is temporary memory used to store information that you accessed when visiting web sites. Cache speeds up a computer’s connection time with web sites that have been visited previously by locally storing information about that connection on the computer so that it does not have to be downloaded each time a site is visited. Why should cache be cleared periodically? Cache can become corrupt or outdated. As a result, cache can slow down or prevent a web page’s output and/or connection instead of assisting it. Clearing cache deletes corrupt or outdated data. It also removes unnecessary information stored in memory from sites that were only visited one time. Clearing Cache helps all web surfing not just PAWS. Internet Explorer 8 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Select Internet Options. 4. From the General Tab, click on Delete under Browsing History. 5. Uncheck Preserve Favorites website data and check both Temporary Internet Files and Cookies. 6. Click Delete. Internet Explorer 7 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. Click on Delete under Browsing History. 5. Click Delete cookies. 6. When prompted, click Yes. 7. Click on Delete Internet Files. 8. When prompted, click Yes. 9. Click Close. 10. Click OK. 11. Close and reopen the browser for the changes to go into effect. Internet Explorer 6 1. Open the Internet Explorer web browser. 2. Click on Tools. 3. Click on Internet Options. 4. -

Browser Wars
Uppsala universitet Inst. för informationsvetenskap Browser Wars Kampen om webbläsarmarknaden Andreas Högström, Emil Pettersson Kurs: Examensarbete Nivå: C Termin: VT-10 Datum: 2010-06-07 Handledare: Anneli Edman "Anyone who slaps a 'this page is best viewed with Browser X' label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of read- ing a document written on another computer, another word processor, or another network" - Sir Timothy John Berners-Lee, grundare av World Wide Web Consortium, Technology Review juli 1996 Innehållsförteckning Abstract ...................................................................................................................................... 1 Sammanfattning ......................................................................................................................... 2 1 Inledning .................................................................................................................................. 3 1.1 Bakgrund .............................................................................................................................. 3 1.2 Syfte ..................................................................................................................................... 3 1.3 Frågeställningar .................................................................................................................... 3 1.4 Avgränsningar ..................................................................................................................... -

Apple Has Built a Solution Into Every Mac
Overview Mac OS X iPhone iPod + iTunes Resources Vision Mac OS X solutions VoiceOver from third parties. Browse the wide variety of To make it easier for the blind and those with low-vision to use a accessibility solutions supported computer, Apple has built a solution into every Mac. Called VoiceOver, by Mac OS X. Learn more it’s reliable, simple to learn, and enjoyable to use. In Depth Device Support Application Support Downloads VoiceOver Application Support VoiceOver. A unique solution for the vision-impaired. Every new Mac comes with Mac OS X and VoiceOver installed and includes a variety of accessible More than 50 reasons to use applications. You can also purchase additional Apple and third-party applications to use with VoiceOver. VoiceOver. Learn more While this page lists a few of the most popular applications, many more are available. If you use an application with VoiceOver that’s not on this list, and you would like to have it added, send email to [email protected]. Unlike traditional screen readers, VoiceOver is integrated into the operating system, so you can start using new accessible applications right away. You don’t need to buy an update to VoiceOver, install a new copy, or add the application to a “white list.” Moreover, VoiceOver commands work the same way in every application, so once you learn how to use them, you’ll be able to apply what you know to any accessible application. Apple provides developers with a Cocoa framework that contains common, reusable application components (such as menus, text fields, buttons, and sliders), so developers don’t have to re-create these elements each time they write a new application. -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -
Browser for Mac 10.4.11 Download Mac OS X 10.4.11 Combo Update (PPC) Meet the World’S Most Advanced Operating System
browser for mac 10.4.11 download Mac OS X 10.4.11 Combo Update (PPC) Meet the world’s most advanced operating system. Again. Instantly find what you’re looking for. Get information in an instant with a single click. Mac OS X Tiger delivers 200+ new features which make it easier than ever to find, access and enjoy everything on your computer. Learn more about Mac OS X. What’s New in this Version. The 10.4.11 Update is recommended for all users running Mac OS X Tiger and includes general operating system fixes that enhance the stability, compatibility and security of your Mac. This update also includes Safari 3, the latest version of Apple's web browser. Mac OS X 10.4.11 Combo Update (PPC) SHA-1 Digest: For explanation of what a SHA-1 digest is, please visit this website: Mac OS X: How to verify a SHA-1 digest. For detailed information on this update, please visit this website: About the Mac OS X 10.4.11 Update. For detailed information on security updates, please visit this website: Apple security updates. The Best Browsers for Older Macs Running Tiger. Last week fellow Low End Mac columnist Simon Royal posted a feature comparing nine Web browsers in the context of use on G3 and older G4 Macs. That’s a space I inhabit. While I no longer have any G3 machines in active service, my wife is still using a 700 MHz iBook G3 running Mac OS X 10.4.11 Tiger, and I have two old Pismo PowerBooks in production and road warrior service, both with 550 MHz G4 processor upgrades and also running 10.4.11. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

Ÿþh Y P E R I O N I N S T a L L a T I O N S T a R T H E R E R E L E a S E 9 . 3
Hyperion Installation Start Here RELEASE 9.3.3 Updated: June 2011 Hyperion Installation Start Here, 9.3.3 Copyright © 2007, 2011, Oracle and/or its affiliates. All rights reserved. Authors: EPM Information Development Team Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS: Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -

CL5708I / CL5716I 8 / 16-Port Single Rail LCD KVM Over IP Switch User Manual CL5708I / CL5716I User Manual
EMC Information CL5708I / CL5716I 8 / 16-Port Single Rail LCD KVM over IP Switch User Manual CL5708I / CL5716I User Manual Compliance Statements FEDERAL COMMUNICATIONS COMMISSION INTERFERENCE STATEMENT This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipment generates, uses, and can radiate radio frequency energy and, if not installed and used in accordance with the instruction manual, may cause harmful interference to radio communications. Operation of this equipment in a residential area is likely to cause harmful interference in which case the user will be required to correct the interference at his own expense. The device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may cause undesired operation. FCC Caution Any changes or modifications not expressly approved by the party responsible for compliance could void the user's authority to operate this equipment. Warning Operation of this equipment in a residential environment could cause radio interference. Achtung Der Gebrauch dieses Geräts in Wohnumgebung kann Funkstörungen verursachen. KCC Statement ii CL5708I / CL5716I User Manual Industry Canada Statement This Class A digital apparatus complies with Canadian ICES-003. RoHS This product is RoHS compliant. About this Manual This user manual is provided to help you get the most out of your LCD KVM over IP switch. -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -

Math in HTML
Math in HTML You can put math in your web pages & email (& elsewhere, if you want to use HTML as "cross-media"), without resorting to ugly or oversized pictures, attachments, obscure TeX code, or things like MathML that are hard to edit by hand & few browsers suport yet. MathML will support fancier equations (in browsers, @ least). MathJax does it now, as javascript. To get any of the fancier stuff (big integral signs, etc.) to work, you need new fonts. For now, these either have to be installed (most readers won't) or repeatedly downloaded by the browser (slowing things down; not enormously, but even a few seconds is considered slow by today's standards). This is the best way to go if you need sophisticated math, but simpler stuff (symbols, sub/superscripts) can do without it, & is easier to proofread (mostly WYSIWYG, not TeX). Unicode It mostly involves just using more characters in the usual fonts. Unicode fonts are 16-bit (216 characters), and so have a lot more than your standard 8-bit ASCII fonts. In particular, they include almost all the Greek and math(s) symbols you need for science: e.g., Greek: ΓΔΘΛΞΠΣΥΦΨΩαβγδεζηθικλμνξπρστυφχψωϑϖ Accented, e.g.: čç Combining accents: ὰάα̂α̃ᾱα̈ᾰα̇α̊α̌αα̸ ̅ Arrows: ←↑→↓↔↕⇐⇔⇒⇑⇓ Math: ℏħ◻ ∂∇∏∑∫∮√∞±∓·×∈⊂∼≃≅≈≠≡≤≥≦≧≪≫⊕⊗½⅓¼ Misc: 〈 〉†‡★☺☻ Large delimiters (missing on some computers & mobile devices): # $ % & (etc.) Actually, Unicode is mostly about languages, but you get the math for free. You may have to use an appropriate font, that has all the characters, especially the combining accents; e.g., Lucida Grande (Mac)/Lucida Sans Unicode (MS Windows) seems to have almost everything. -

Comparative Study of Web-Browser.Pdf
International Journal of Computer Architecture and Mobility (ISSN 2319-9229) Volume 1-Issue 4, February 2013 Comparative Study of Web-Browsers Bhawani Singh Chouhan [email protected] Abstract: Internet is the basic need for business languages, algorithms and with continuously ,education and for global communication, enhancing techniques. Internet is only accessed researchers are continuously enhancing usability by web-browser none other applications are and features of web technology, But still certain there to provide or generate applicability for restrictions and specific applicability are there internet mechanism. Web-browser could works for the use of internet like web-browsers or at both the ends ,that is, at client end and at www(world wide web) is the only tool , server end ,which converts information required software package design for accessing internet, by network to generalized form, web-browser without web-browser no-body could access has its own features ,which stores session internet and their features, every web-browser states[3]by several methods, web-browser have has their own accessing features and security their own accessing intensity for software’s and features. In the propose paper several web- web-sites. The format or specification of web browsers are compared with their significance browser is that only www is supported by its and applicability. design architecture. In the propose work several web-browsers with different [4, 5] dimensions Introduction: has been presented and compared to provide generalize design patterns. Internet is the most popular and flexible source for business, education and communication. Related Work: Almost internet has covered broad areas of human perception, may be because of Internet Explorer independence and usability of services available on internet.