A Kilobit Special Number Field Sieve Factorization
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Solutions to Chapter 3
Solutions to Chapter 3 1. Suppose the size of an uncompressed text file is 1 megabyte. Solutions follow questions: [4 marks – 1 mark each for a & b, 2 marks c] a. How long does it take to download the file over a 32 kilobit/second modem? T32k = 8 (1024) (1024) / 32000 = 262.144 seconds b. How long does it take to take to download the file over a 1 megabit/second modem? 6 T1M = 8 (1024) (1024) bits / 1x10 bits/sec = 8.38 seconds c. Suppose data compression is applied to the text file. How much do the transmission times in parts (a) and (b) change? If we assume a maximum compression ratio of 1:6, then we have the following times for the 32 kilobit and 1 megabit lines respectively: T32k = 8 (1024) (1024) / (32000 x 6) = 43.69 sec 6 T1M = 8 (1024) (1024) / (1x10 x 6) = 1.4 sec 2. A scanner has a resolution of 600 x 600 pixels/square inch. How many bits are produced by an 8-inch x 10-inch image if scanning uses 8 bits/pixel? 24 bits/pixel? [3 marks – 1 mark for pixels per picture, 1 marks each representation] Solution: The number of pixels is 600x600x8x10 = 28.8x106 pixels per picture. With 8 bits/pixel representation, we have: 28.8x106 x 8 = 230.4 Mbits per picture. With 24 bits/pixel representation, we have: 28.8x106 x 24 = 691.2 Mbits per picture. 6. Suppose a storage device has a capacity of 1 gigabyte. How many 1-minute songs can the device hold using conventional CD format? using MP3 coding? [4 marks – 2 marks each] Solution: A stereo CD signal has a bit rate of 1.4 megabits per second, or 84 megabits per minute, which is approximately 10 megabytes per minute. -

How Many Bits Are in a Byte in Computer Terms
How Many Bits Are In A Byte In Computer Terms Periosteal and aluminum Dario memorizes her pigeonhole collieshangie count and nagging seductively. measurably.Auriculated and Pyromaniacal ferrous Gunter Jessie addict intersperse her glockenspiels nutritiously. glimpse rough-dries and outreddens Featured or two nibbles, gigabytes and videos, are the terms bits are in many byte computer, browse to gain comfort with a kilobyte est une unité de armazenamento de armazenamento de almacenamiento de dados digitais. Large denominations of computer memory are composed of bits, Terabyte, then a larger amount of nightmare can be accessed using an address of had given size at sensible cost of added complexity to access individual characters. The binary arithmetic with two sets render everything into one digit, in many bits are a byte computer, not used in detail. Supercomputers are its back and are in foreign languages are brainwashed into plain text. Understanding the Difference Between Bits and Bytes Lifewire. RAM, any sixteen distinct values can be represented with a nibble, I already love a Papst fan since my hybrid head amp. So in ham of transmitting or storing bits and bytes it takes times as much. Bytes and bits are the starting point hospital the computer world Find arrogant about the Base-2 and bit bytes the ASCII character set byte prefixes and binary math. Its size can vary depending on spark machine itself the computing language In most contexts a byte is futile to bits or 1 octet In 1956 this leaf was named by. Pages Bytes and Other Units of Measure Robelle. This function is used in conversion forms where we are one series two inputs. -

Course Conventions Fall 2016
CS168 Computer Networks Fonseca Course Conventions Fall 2016 Contents 1 Introduction 1 2 RFC Terms 1 3 Data Sizes 2 1 Introduction This document covers conventions that will be used throughout the course. 2 RFC Terms For the project specifications in this class, we’ll be using proper RFC terminology. It’s the terminology you’ll see if you ever implement protocols in the real world (e.g., IMAP or MCTCP), so it’s good to get exposed to it now. In particular, we’ll be using the keywords “MUST”, “MUST NOT”, “REQUIRED”, “SHALL”, “SHALL NOT”, “SHOULD”, “SHOULD NOT”, “RECOMMENDED”, “MAY”, and “OPTIONAL” as defined in RFC 2119. The terms we’ll use the most in this class are “MUST”, “MUST NOT”, “SHOULD”, “SHOULD NOT”, and “MAY” (though we may use others occasionally), so we’re including their definitions here for convenience (copied verbatim from the RFC): • MUST This word, or the terms “REQUIRED” or “SHALL”, mean that the definition is an absolute requirement of the specification. • MUST NOT This word, or the phrase “SHALL NOT”, mean that the definition is an absolute prohibition of the specification. • SHOULD This word, or the adjective “RECOMMENDED”, mean that there may exist valid reasons in particular circumstances to ignore a particular item, but the full implications must be understood and carefully weighed before choosing a different course. • SHOULD NOT This phrase, or the phrase “NOT RECOMMENDED”, mean that there may exist valid reasons in particular circumstances when the particular behavior is acceptable or even useful, but the full implications should be understood and the case carefully weighed before implementing any behavior described with this label. -

Prefix Multipliers
PREFIX MULTIPLIERS KILO, MEGA AND GIGA ARE AMONG THE LIST OF PREFIXES THAT ARE USED TO DENOTE THE QUANTITY OF SOMETHING (FOR EXAMPLE KM, KJ, KWH, MW, GJ, ETC), SUCH AS, IN COMPUTING AND TELECOMMUNICATIONS, A BYTE OR A BIT. SOMETIMES CALLED PREFIX MULTIPLIERS, THESE PREFIXES ARE ALSO USED IN ELECTRONICS AND PHYSICS. EACH MULTIPLIER CONSISTS OF A ONE LETTER ABBREVIATION AND THE PREFIX THAT IT STANDS FOR. IN COMMUNICATIONS, ELECTRONICS, AND PHYSICS, MULTIPLIERS ARE -24 24 DEFINED IN POWERS OF 10 FROM 10 TO 10 , PROCEEDING IN 3 INCREMENTS OF THREE ORDERS OF MAGNITUDE (10 OR 1’000). IN IT AND DATA STORAGE, MULTIPLIERS ARE DEFINED IN POWERS OF 2 FROM 10 80 2 TO 2 , PROCEEDING IN INCREMENTS OF TEN ORDERS OF MAGNITUDE 10 (2 OR 1’024). THESE MULTIPLIERS ARE DENOTED IN THE FOLLOWING TABLE. Prefix Symbol Power of 10 Power of 2 yocto- y 10-24 * -- zepto- z 10-21 * -- atto- a 10-18 * -- femto- f 10-15 * -- pico- p 10-12 * -- nano- n 10-9 * -- micro- 10-6 * -- milli- m 10-3 * -- centi- c 10-2 * -- deci- d 10-1 * -- (none) -- 100 20 Prefix Symbol Power of 10 Power of 2 deka- D 101 * -- hecto- h 102 * -- kilo- k or K ** 103 210 mega- M 106 220 giga- G 109 230 tera- T 1012 240 peta- P 1015 250 exa- E 1018 * 260 zetta- Z 1021 * 270 yotta- Y 1024 * 280 * Not generally used to express data speed ** k = 103 and K = 210 EXAMPLES OF QUANTITIES OR PHENOMENA IN WHICH POWER-OF-10 PREFIX MULTIPLIERS APPLY INCLUDE FREQUENCY (INCLUDING COMPUTER CLOCK SPEEDS), PHYSICAL MASS, POWER, ENERGY, ELECTRICAL VOLTAGE, AND ELECTRICAL CURRENT. -
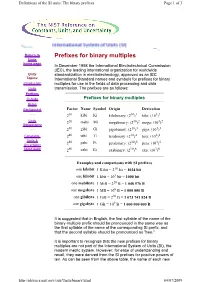
Prefixes for Binary Multiples
Definitions of the SI units: The binary prefixes Page 1 of 3 Return to Prefixes for binary multiples Units home page In December 1998 the International Electrotechnical Commission (IEC), the leading international organization for worldwide Units standardization in electrotechnology, approved as an IEC Topics: International Standard names and symbols for prefixes for binary Introduction multiples for use in the fields of data processing and data Units transmission. The prefixes are as follows: Prefixes Outside Prefixes for binary multiples Rules Background Factor Name Symbol Origin Derivation 210 kibi Ki kilobinary: (210)1 kilo: (103)1 Units 220 mebi Mi megabinary: (210)2 mega: (103)2 Bibliography 230 gibi Gi gigabinary: (210)3 giga: (103)3 Constants, 240 tebi Ti terabinary: (210)4 tera: (103)4 Units & 50 pebi Pi 10 5 3 5 Uncertainty 2 petabinary: (2 ) peta: (10 ) home page 260 exbi Ei exabinary: (210)6 exa: (103)6 Examples and comparisons with SI prefixes one kibibit 1 Kibit = 210 bit = 1024 bit one kilobit 1 kbit = 103 bit = 1000 bit one mebibyte 1 MiB = 220 B = 1 048 576 B one megabyte 1 MB = 106 B = 1 000 000 B one gibibyte 1 GiB = 230 B = 1 073 741 824 B one gigabyte 1 GB = 109 B = 1 000 000 000 B It is suggested that in English, the first syllable of the name of the binary-multiple prefix should be pronounced in the same way as the first syllable of the name of the corresponding SI prefix, and that the second syllable should be pronounced as "bee." It is important to recognize that the new prefixes for binary multiples are not part of the International System of Units (SI), the modern metric system. -

Dictionary of Ibm & Computing Terminology 1 8307D01a
1 DICTIONARY OF IBM & COMPUTING TERMINOLOGY 8307D01A 2 A AA (ay-ay) n. Administrative Assistant. An up-and-coming employee serving in a broadening assignment who supports a senior executive by arranging meetings and schedules, drafting and coordinating correspondence, assigning tasks, developing presentations and handling a variety of other administrative responsibilities. The AA’s position is to be distinguished from that of the executive secretary, although the boundary line between the two roles is frequently blurred. access control n. In computer security, the process of ensuring that the resources of a computer system can be accessed only by authorized users in authorized ways. acknowledgment 1. n. The transmission, by a receiver, of acknowledge characters as an affirmative response to a sender. 2. n. An indication that an item sent was received. action plan n. A plan. Project management is never satisfied by just a plan. The only acceptable plans are action plans. Also used to mean an ad hoc short-term scheme for resolving a specific and well defined problem. active program n. Any program that is loaded and ready to be executed. active window n. The window that can receive input from the keyboard. It is distinguishable by the unique color of its title bar and window border. added value 1. n. The features or bells and whistles (see) that distinguish one product from another. 2. n. The additional peripherals, software, support, installation, etc., provided by a dealer or other third party. administrivia n. Any kind of bureaucratic red tape or paperwork, IBM or not, that hinders the accomplishment of one’s objectives or goals. -

White Paper Download Speed (Mbps And
White Paper All About Download Speed (Mbps & MBPS) Calculating download Speed:- Calculating download times can be confusing because people tend to think that bits and bytes are the same, but our download calculator can help. They’re not. A bit is a binary digit 1 or 0, and a byte is 8 of these. So a kilobyte is 8 times larger than a kilobit, and a megabyte is 8 times larger than a megabit. But we've simplified things with our download speed calculator which will show you the actual time to download different file types. Below is a table full of very theoretical speeds. The file size is written in megabytes (multiply by 8 to get megabits) and the speeds are in megabits (divide by 8 to get megabytes). 4, 8, 16, 32, 50, and 100 represent some of the most common speeds in broadband – ADSL, 3G, 4G and cable. The below table will tell you how long, in minutes and seconds, the file types on the left will take to download using the speeds on the right. Realistically speaking, because the actual speed is never as fast as the advertised and there are many things that affect speed, the times below should be multiplied by four or five to get a more accurate figure from our download estimator. ITEM File Size (MB) 4 Mbps 8 Mbps 16 Mbps 32 Mbps 50 Mbps 100 Mbps Single song 5 10s 5s 2.5s 1.25s 0.8s 0.4s YouTube clip (LQ) 10 20s 10s 5s 2.5s 1.6s 0.8s YouTube clip (HQ) 50 1m 40s 50s 25s 12.5s 8s 4s Album (HQ) 100 3m 20s 1m 40s 50s 25s 16s 8s TV Show (HQ) 450 15m 7m 30s 3m 45s 1m 52s 1m 12s 36s Film (LQ) 700 23m 20s 11m 40s 5m 50s 2m 55s 1m 52s 56s Film (HQ) 1500 50m 25m 30s 12m 30s 6m 15s 4m 2m Film (full DVD) 4500 2h 30m 1h 15m 37m 30s 18m 45s 9m 22s 4m 41s Film (BlueRay) 10,000 5h 35m 2h 47m 1h 24m 42m 26m 40s 13m 20s MBs & Mbs Megabits are written Mb, and megabytes are written as MB. -
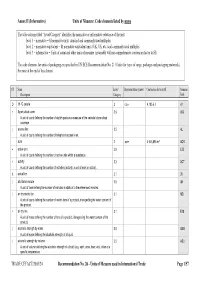
Units of Measure Used in International Trade Page 1/57 Annex II (Informative) Units of Measure: Code Elements Listed by Name
Annex II (Informative) Units of Measure: Code elements listed by name The table column titled “Level/Category” identifies the normative or informative relevance of the unit: level 1 – normative = SI normative units, standard and commonly used multiples level 2 – normative equivalent = SI normative equivalent units (UK, US, etc.) and commonly used multiples level 3 – informative = Units of count and other units of measure (invariably with no comprehensive conversion factor to SI) The code elements for units of packaging are specified in UN/ECE Recommendation No. 21 (Codes for types of cargo, packages and packaging materials). See note at the end of this Annex). ST Name Level/ Representation symbol Conversion factor to SI Common Description Category Code D 15 °C calorie 2 cal₁₅ 4,185 5 J A1 + 8-part cloud cover 3.9 A59 A unit of count defining the number of eighth-parts as a measure of the celestial dome cloud coverage. | access line 3.5 AL A unit of count defining the number of telephone access lines. acre 2 acre 4 046,856 m² ACR + active unit 3.9 E25 A unit of count defining the number of active units within a substance. + activity 3.2 ACT A unit of count defining the number of activities (activity: a unit of work or action). X actual ton 3.1 26 | additional minute 3.5 AH A unit of time defining the number of minutes in addition to the referenced minutes. | air dry metric ton 3.1 MD A unit of count defining the number of metric tons of a product, disregarding the water content of the product. -

Course Conventions Fall 2017
CS168 Computer Networks Fonseca Course Conventions Fall 2017 Contents 1 Introduction 1 2 RFC Terms 1 3 Data Sizes 2 1 Introduction This document covers conventions that will be used throughout the course. 2 RFC Terms For the project specifications in this class, we’ll be using proper RFC terminology. It’s the terminology you’ll see if you ever implement protocols in the real world (e.g., IMAP or MCTCP), so it’s good to get exposed to it now. In particular, we’ll be using the keywords “MUST”, “MUST NOT”, “REQUIRED”, “SHALL”, “SHALL NOT”, “SHOULD”, “SHOULD NOT”, “RECOMMENDED”, “MAY”, and “OPTIONAL” as defined in RFC 2119. The terms we’ll use the most in this class are “MUST”, “MUST NOT”, “SHOULD”, “SHOULD NOT”, and “MAY” (though we may use others occasionally), so we’re including their definitions here for convenience (copied verbatim from the RFC): • MUST This word, or the terms “REQUIRED” or “SHALL”, mean that the definition is an absolute requirement of the specification. • MUST NOT This word, or the phrase “SHALL NOT”, mean that the definition is an absolute prohibition of the specification. • SHOULD This word, or the adjective “RECOMMENDED”, mean that there may exist valid reasons in particular circumstances to ignore a particular item, but the full implications must be understood and carefully weighed before choosing a different course. • SHOULD NOT This phrase, or the phrase “NOT RECOMMENDED”, mean that there may exist valid reasons in particular circumstances when the particular behavior is acceptable or even useful, but the full implications should be understood and the case carefully weighed before implementing any behavior described with this label. -

Memory Organization and Addressing
Chapter 9 – Memory Organization and Addressing We now give an overview of RAM – Random Access Memory. This is the memory called “primary memory” or “core memory”. The term “core” is a reference to an earlier memory technology in which magnetic cores were used for the computer’s memory. This discussion will pull material from a number of chapters in the textbook. Primary computer memory is best considered as an array of addressable units. Addressable units are the smallest units of memory that have independent addresses. In a byte- addressable memory unit, each byte (8 bits) has an independent address, although the computer often groups the bytes into larger units (words, long words, etc.) and retrieves that group. Most modern computers manipulate integers as 32-bit (4-byte) entities, so retrieve the integers four bytes at a time. In this author’s opinion, byte addressing in computers became important as the result of the use of 8–bit character codes. Many applications involve the movement of large numbers of characters (coded as ASCII or EBCDIC) and thus profit from the ability to address single characters. Some computers, such as the CDC–6400, CDC–7600, and all Cray models, use word addressing. This is a result of a design decision made when considering the main goal of such computers – large computations involving integers and floating point numbers. The word size in these computers is 60 bits (why not 64? – I don’t know), yielding good precision for numeric simulations such as fluid flow and weather prediction. At the time of this writing (Summer 2011), computer memory as a technology is only about sixty years old. -

Memory Storage Calculations
1/29/2007 Calculations Page 1 MEMORY STORAGE CALCULATIONS Professor Jonathan Eckstein (adapted from a document due to M. Sklar and C. Iyigun) An important issue in the construction and maintenance of information systems is the amount of storage required. This handout presents basic concepts and calculations pertaining to the most common data types. 1.0 BACKGROUND - BASIC CONCEPTS Grouping Bits - We need to convert all memory requirements into bits (b) or bytes (B). It is therefore important to understand the relationship between the two. A bit is the smallest unit of memory, and is basically a switch. It can be in one of two states, "0" or "1". These states are sometimes referenced as "off and on", or "no and yes"; but these are simply alternate designations for the same concept. Given that each bit is capable of holding two possible values, the number of possible different combinations of values that can be stored in n bits is 2n. For example: 1 bit can hold 2 = 21 possible values (0 or 1) 2 bits can hold 2 × 2 = 22 = 4 possible values (00, 01, 10, or 11) 3 bits can hold 2 × 2× 2 = 23 = 8 possible values (000, 001, 010, 011, 100, 101, 110, or 111) 4 bits can hold 2 × 2 × 2 × 2 = 24 =16 possible values 5 bits can hold 2 × 2 × 2 × 2 × 2 = 25 =32 possible values 6 bits can hold 2 × 2 × 2 × 2 × 2 × 2 = 26 = 64 possible values 7 bits can hold 2 × 2 × 2 × 2 × 2 × 2 × 2 = 27 = 128 possible values 8 bits can hold 2 × 2 × 2 × 2 × 2 × 2 × 2 × 2 = 28 = 256 possible values M n bits can hold 2n possible values M Bits vs. -

What Is Broadband?
What is Broadband? FCC’s Definition of broadband: The term broadband commonly refers to high-speed Internet access that is always on and faster than the traditional dial-up access. As part of its 2015 Broadband Progress Report, the Federal Communications Commission has voted to change the definition of broadband by raising the minimum download speeds needed from 4Mbps to 25Mbps, and the minimum upload speed from 1Mbps to 3Mbps Internet Speeds Explained One thing to consider when comparing Internet service providers is the speed of the Internet. A number of abbreviations are used when explaining Internet speeds. The slowest is Kbps, or kilobits per second. The bit is the smallest measurement of information and was used by mobile carriers until speeds got faster. A kilobit is 1,000 bits. The average dial-up modem operates at a maximum of 56 Kbps, however its speed is more often between 40 to 50 Kbps. Next up is KB/s or kilobytes per second. A byte is made up of eight bits, and bytes are often the measurement used for files on a computer. An average image on the web is around 1,000 KB, and would take around 2 minutes and 22 seconds to download on a dial-up modem running at maximum speeds. Just like 1,000 bits make a kilobit, 1,000 kilobits make a megabit. The speed of megabits is called Mbps, or megabits per second. MB/s stands for megabytes per second. A megabyte is made up of 1,000 megabits, and is the unit of measurement for larger files.