Internet Explorer in Linux with Ies4linux EXPLORER UNLEASHED Nina Hoff , Fotolia
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

My Cloud EX2 Ultra
My Cloud™ EX2 Ultra Privater Cloud-Speicher Bedienungsanleitung WD Service und Support Sollten Probleme auftreten, geben Sie uns bitte Gelegenheit, sie zu beheben, bevor Sie das Produkt zurücksenden. Viele technische Fragen können über unsere Knowledge Base oder unseren E-Mail-Support unter http://support.wd.com beantwortet werden. Falls Sie dort keine geeignete Antwort finden oder Sie einen persönlichen Kontakt bevorzugen, rufen Sie WD unter der unten angegebenen Telefonnummer Ihres Landes an. Ihr Produkt schließt eine 30-tägige kostenlose telefonische Unterstützung während der Garantiezeit ein. Diese 30-tägige Frist beginnt mit dem Datum Ihres ersten telefonischen Kontakts mit dem technischen Support von WD. Der E-Mail-Support ist für die gesamte Garantiezeit kostenlos, und unsere gesamte Knowledge Base ist rund um die Uhr verfügbar. Damit wir Sie weiterhin über neue Funktionen und Serviceleistungen informieren können, denken Sie bitte daran, Ihr Produkt im Internet zu registrieren unter http://register.wd.com. Zugriff auf den Onlinesupport Auf unserer Produktsupport-Website unter http://support.wd.com können Sie unter den folgenden Themen wählen: Downloads – Laden Sie Treiber, Software und Updates für Ihr WD-Produkt herunter. Registrierung – Registrieren Sie Ihr WD-Produkt, um die neuesten Updates und Sonderangebote zu erhalten. Garantie- und Austauschservices – Informationen über Garantie, Produktersatz (RMA), RMA-Status und Datenwiederherstellung. Knowledge Base – Suchen Sie nach Schlüsselwort, Ausdruck oder Antwort-ID. Installation – Hier finden Sie online Hilfe zur Installation Ihres WD-Produkts oder Ihrer Software. WD Community – Tauschen Sie Ihre Gedanken mit anderen WD-Benutzern aus. Online-Schulungszentrum – Kommen Sie hierhin, um das meiste aus Ihrem privaten Cloud-Speichergerät herauszuholen: (http://www.wd.com/setup). -

Symantec Netrecon™ 3.6 Security Update 21 Release Notes Symantec Netrecon Security Update 21 Release Notes
Symantec NetRecon™ 3.6 Security Update 21 Release Notes Symantec NetRecon Security Update 21 Release Notes The software that is described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version: v3.6 040831 Copyright Notice Copyright 2004 Symantec Corporation. All Rights Reserved. Any technical documentation that is made available by Symantec Corporation is the copyrighted work of Symantec Corporation and is owned by Symantec Corporation. NO WARRANTY. The technical documentation is being delivered to you AS-IS and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014. Trademarks Symantec and the Symantec logo are U.S. registered trademarks, and Symantec NetRecon, Symantec Enterprise Security Architecture, Symantec Enterprise Security Manager, LiveUpdate, and Symantec Security Response are trademarks of Symantec Corporation. Microsoft, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product names that are mentioned in this manual may be trademarks or registered trademarks of their respective companies and are hereby acknowledged. Printed in the United States of America. 3 Technical support As part of Symantec Security Response, the Symantec Global Technical Support group maintains support centers throughout the world. -

Symantec Netrecon™ 3.6 Security Update 24 Release Notes Symantec Netrecon Security Update 24 Release Notes
Symantec NetRecon™ 3.6 Security Update 24 Release Notes Symantec NetRecon Security Update 24 Release Notes The software that is described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version: v3.6 040930 Copyright Notice Copyright 2005 Symantec Corporation. All Rights Reserved. Any technical documentation that is made available by Symantec Corporation is the copyrighted work of Symantec Corporation and is owned by Symantec Corporation. NO WARRANTY. The technical documentation is being delivered to you AS-IS and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014. Trademarks Symantec and the Symantec logo are U.S. registered trademarks, and Symantec NetRecon, Symantec Enterprise Security Architecture, Symantec Enterprise Security Manager, LiveUpdate, and Symantec Security Response are trademarks of Symantec Corporation. Microsoft, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product names that are mentioned in this manual may be trademarks or registered trademarks of their respective companies and are hereby acknowledged. Printed in the United States of America. 3 Technical support As part of Symantec Security Response, the Symantec Global Technical Support group maintains support centers throughout the world. -

Detecting and Analyzing Insecure Component Integration
Taeho Kwon December 2011 Computer Science Detecting and Analyzing Insecure Component Integration Abstract Component technologies have been widely adopted for designing and engineering software ap- plications and systems, which dynamically integrate software components to achieve desired func- tionalities. Engineering software in a component-based style has significant benefits, such as im- proved programmer productivity and software reliability. To support component integration, oper- ating systems allow an application to dynamically load and use a component. Although developers have frequently utilized such a system-level mechanism, programming errors can lead to insecure component integration and serious security vulnerabilities. The security and reliability impact of component integration has not yet been much explored. This dissertation systematically investigates security issues in dynamic component integration and their impact on software security. On the conceptual level, we formulate two types of insecure component integration—unsafe component loading and insecure component usage—and present practical, scalable techniques to detect and analyze them. Our techniques operate directly on soft- ware binaries and do not require source code. On the practical level, we have used them to discover new vulnerabilities in popular, real-world software, and show that insecure component integration is prevalent and can be exploited by attackers to subvert important software and systems. Our research has had substantial practical impact and helped -

Windows® Scripting Secrets®
4684-8 FM.f.qc 3/3/00 1:06 PM Page i ® WindowsSecrets® Scripting 4684-8 FM.f.qc 3/3/00 1:06 PM Page ii 4684-8 FM.f.qc 3/3/00 1:06 PM Page iii ® WindowsSecrets® Scripting Tobias Weltner Windows® Scripting Secrets® IDG Books Worldwide, Inc. An International Data Group Company Foster City, CA ♦ Chicago, IL ♦ Indianapolis, IN ♦ New York, NY 4684-8 FM.f.qc 3/3/00 1:06 PM Page iv Published by department at 800-762-2974. For reseller information, IDG Books Worldwide, Inc. including discounts and premium sales, please call our An International Data Group Company Reseller Customer Service department at 800-434-3422. 919 E. Hillsdale Blvd., Suite 400 For information on where to purchase IDG Books Foster City, CA 94404 Worldwide’s books outside the U.S., please contact our www.idgbooks.com (IDG Books Worldwide Web site) International Sales department at 317-596-5530 or fax Copyright © 2000 IDG Books Worldwide, Inc. All rights 317-572-4002. reserved. No part of this book, including interior design, For consumer information on foreign language cover design, and icons, may be reproduced or transmitted translations, please contact our Customer Service in any form, by any means (electronic, photocopying, department at 800-434-3422, fax 317-572-4002, or e-mail recording, or otherwise) without the prior written [email protected]. permission of the publisher. For information on licensing foreign or domestic rights, ISBN: 0-7645-4684-8 please phone +1-650-653-7098. Printed in the United States of America For sales inquiries and special prices for bulk quantities, 10 9 8 7 6 5 4 3 2 1 please contact our Order Services department at 1B/RT/QU/QQ/FC 800-434-3422 or write to the address above. -

Effective Web Design, Second Edition
Effective Web Design Effective Web Design, Second Edition Ann Navarro SYBEX® Associate Publisher: Cheryl Applewood Contracts and Licensing Manager: Kristine O'Callaghan Acquisitions and Developmental Editor: Raquel Baker Editors: Joseph A. Webb, James A. Compton, Colleen Wheeler Strand Production Editor: Dennis Fitzgerald Technical Editor: Marshall Jansen Book Designer: Maureen Forys, Happenstance Type-O-Rama Graphic Illustrator: Tony Jonick Electronic Publishing Specialist: Maureen Forys, Happenstance Type-O-Rama Proofreaders: Nelson Kim, Nancy Riddiough, Leslie E.H. Light Indexer: Ann Rogers CD Coordinator: Christine Harris CD Technician: Kevin Ly Cover Designer: Design Site Cover Illustrator/Photographer: Dan Bowman Copyright © 2001 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. World rights reserved. page 1 Effective Web Design The author(s) created reusable code in this publication expressly for reuse by readers. Sybex grants readers limited permission to reuse the code found in this publication or its accompanying CD-ROM so long as (author(s)) are attributed in any application containing the reusable code and the code itself is never distributed, posted online by electronic transmission, sold, or commercially exploited as a stand- alone product. Aside from this specific exception concerning reusable code, no part of this publication may be stored in a retrieval system, transmitted, or reproduced in any way, including but not limited to photocopy, photograph, magnetic, or other record, without the prior agreement and written permission of the publisher. An earlier version of this book was published under the title Effective Web Design © 1998 SYBEX Inc. Library of Congress Card Number: 2001088112 ISBN: 0-7821-2849-1 SYBEX and the SYBEX logo are either registered trademarks or trademarks of SYBEX Inc. -
Dc60 Java and Web Programming Dec 2014
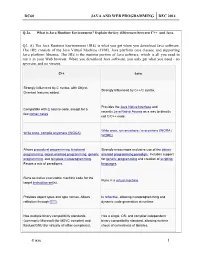
DC60 JAVA AND WEB PROGRAMMING DEC 2014 Q.2 a. What is Java Runtime Environment? Explain the key differences between C++ and Java. Q2. A) The Java Runtime Environment (JRE) is what you get when you download Java software. The JRE consists of the Java Virtual Machine (JVM), Java platform core classes, and supporting Java platform libraries. The JRE is the runtime portion of Java software, which is all you need to run it in your Web browser. When you download Java software, you only get what you need - no spyware, and no viruses. C++ Java Strongly influenced by C syntax, with Object- Strongly influenced by C++/C syntax. Oriented features added. Provides the Java Native Interface and Compatible with C source code, except for a recently Java Native Access as a way to directly few corner cases. call C/C++ code. Write once, run anywhere / everywhere (WORA / Write once, compile anywhere (WOCA). WORE). Allows procedural programming, functional Strongly encourages exclusive use of the object- programming, object-oriented programming, generic oriented programming paradigm. Includes support programming, and template metaprogramming. for generic programming and creation of scripting Favors a mix of paradigms. languages. Runs as native executable machine code for the Runs in a virtual machine. target instruction set(s). Provides object types and type names. Allows Is reflective, allowing metaprogramming and reflection through RTTI. dynamic code generation at runtime. Has multiple binary compatibility standards Has a single, OS- and compiler-independent (commonly Microsoft (for MSVC compiler) and binary compatibility standard, allowing runtime Itanium/GNU (for virtually all other compilers)). check of correctness of libraries. -

The User Friendly Guide to INTERNET & COMPUTER TERMS
The User Friendly Guide to INTERNET & COMPUTER TERMS Charles Steed Gold Standard Press Inc. Reno, Nevada Copyright ã 2001 Charles Steed and Gold Standard Press Inc. Permission is granted to ALL USERS and readers to download, print and freely dis- tribute The User Friendly Guide To Internet & Computer Terms. No changes to this text is authorized. THIS TEXT MAY NOT BE SOLD EXCEPT BY AUTHORIZED AGENTS OR REPRESENTATIVES OF GOLD STANDARD PRESS INC. For information, contact Gold Standard Press Inc. 1475 Terminal Way, Suite E, Reno, Nevada 89502, tel. 360-482-2510. This book contains information gathered from many sources. It is published for gen- eral reference and not as a substitute for independent verification by users when circumstances warrant. It is sold with the understanding that neither the author nor publisher is engaged in rendering legal, psychological, accounting or professional advice. The publisher and author disclaim any personal liability, either directly or indirectly, for advice presented within. Although the author and publisher have used care and diligence in the preparation, and made every effort to ensure the accuracy and completeness of information contained in this book, we assume no responsibility for errors, inaccuracies, omissions, or any inconsistency herein. Any slights of people, places, publishers, books, or organizations are unintentional. The online version of this text has been slightly modified to faciliate easy download- ing. No significant differences from the printed version are present. Library of Congress -

По Неофициални Статистически Данни Повече От 80% От Дяла На Използваните Браузери Се Пада На Microsoft Internet Explorer
Ангелина Тагарева, ф.н. 43153, 3 курс, специалност информатика Радостин Цанев, ф.н. 43089, 3 курс, специалност информатика Анализ на излезлите експлойти за Internet Еxplorer Курсов проект по Мрежова Сигурност – Сигурен Код Ангелина Тагарева, ф.н. 43153 Радостин Цанев, ф.н. 43089 По неофициални статистически данни повече от 80% от дяла на използваните браузери се пада на Microsoft Internet Explorer. Като най-често използван интернет браузер, сигурността очевидно не е била основна задача при имплементирането му. Свидетелство за това са многобройните уязвимости и експлойти, излези за този продукт. Интересното в случая е, че уязвимостите в MS IE са пъти повече от конкурентни open source решения, въпреки че кодът на браузера е затворен. Преди за започнем същинското изложение на излезлите експлйти за Microsoft Internet Explorer, ще направим няколко уточнения. Първо е важно да отбележим каква е разликата между уязвимост и експлойт. Уязвимост представлява проблем в сигурността на даден софтуер. Експлойтът е програмен код, който се възплозва от тази уязвимост. Тези две понятия вървят ръка за ръка, затова в нашето изложение ще посочваме първо за каква уязвимост се отнасят дадените експлойти и чак след това ще пристъпваме към самото им разглеждане. В политиката за сигурността на IE е застъпена идеята за различни зони на сигурност. Те биват четири вида: Internet Zone, Local Zone, Trusted Sites и Restricted Sites. Според официалния сайт на Microsoft, "Сигурността, залегната в Internet Explorer 6 е добре балансирана. При първата инсталлация на браузера, той поставя всички уеб сайтове в Internet Zone със средно ниво на сигурност. По този начин може да браузвате сигурно и ще бъдете предупраждавани преди свалянето на потенциално опасно съдържание". -

Internet Explorer
Internet Explorer From Wikipedia, the free encyclopedia Jump to: navigation, search Windows Internet Explorer Wikipedia's Main Page in Windows Internet Explorer 7 running on Windows Vista. Developed by Microsoft Initial release August 1995 (12–13 years ago) Latest release 7.0.5730.13 (Windows XP/Windows 2003 Server) 7.0.6001.18000 (Windows Vista SP1) / 2008 Preview release 8.0.6001.17184 (IE8, Beta 1) / March 5, 2008 OS Microsoft Windows Mac OS System 7 to Mac OS X (discontinued) Solaris and HP-UX (discontinued) Genre Web browser and RSS Reader License Proprietary EULA Website microsoft.com/ie Windows Internet Explorer (formerly Microsoft Internet Explorer abbreviated MSIE), commonly abbreviated to IE, is a series of graphical web browsers developed by Microsoft and included as part of the Microsoft Windows line of operating systems starting in 1995. It has been the most widely used web browser since 1999, attaining a peak of about 95% usage share during 2002 and 2003 with IE5 and 6 but steadily declining since, despite the introduction of IE7. Microsoft spent over 100 million dollars (USD) a year [1] in the late 1990s, with over 1000 people working on IE by 1999. [2] Internet Explorer was first released as part of the add-on package Plus! for Windows 95. Later versions were available as free downloads, or in service packs, and included in the OEM service releases of Windows 95 and later versions of Windows. The most recent release is version 7.0, which is available as a free update for Windows XP Service Pack 2, and Windows Server 2003 with Service Pack 1 or later, Windows Vista, and Windows Server 2008. -

My Cloud EX2 Ultra Private Cloud Storage Software
My Cloud™ EX2 Ultra Private Cloud Storage User Manual WD Service and Support Should you encounter any problem, please give us an opportunity to address it before returning this product. Most technical support questions can be answered through our knowledge base or email support service at http://support.wd.com. If the answer is not available or if you prefer, please contact WD at the best telephone number shown below. Your product includes 30 days of free telephone support during the warranty period. This 30-day period starts on the date of your first telephone contact with WD Technical Support. Email support is free for the entire warranty period and our extensive knowledge base is available 24/7. To help us keep you informed of new features and services, remember to register your product online at http://register.wd.com. Accessing Online Support Visit our product support website at http://support.wd.com and choose from these topics: Downloads—Download drivers, software, and updates for your WD product. Registration—Register your WD product to get the latest updates and special offers. Warranty & RMA Services—Get warranty, product replacement (RMA), RMA status, and data recovery information. Knowledge Base—Search by keyword, phrase, or answer ID. Installation—Get online installation help for your WD product or software. WD Community—Share your thoughts and connect with other WD users. Learning Center — Start here to get the most out of your Private Cloud Storage device (http://www.wd.com/setup). Contacting WD Technical Support When contacting WD for support have your WD product serial number, system hardware, and system software versions available. -

Seventh Framework Programme Information and Communication Technologies
SEVENTH FRAMEWORK PROGRAMME NFORMATION AND OMMUNICATION ECHNOLOGIES I C T Project Accessibility Assessment Simulation Environment for New Applications Design and Development (ACCESSIBLE, Grant Agreement No. 224145) Deliverable D 2.1 - State of the Art Survey in Accessibility Research and Market Survey Lead beneficiary CS WP. no, title WP2 – User needs, benchmarking, accessibility and and activity type simulation requirements (RTD) Contributing Task (s) Task 2.2: Literature review and market survey Dissemination Public level Delivery date January 2010 Status Updated Final File name and “ACCESSIBLE_D2.1_FINAL_updated_Jan2010.doc”, 10486 Kb size ACCESSIBLE Deliverable D2.1 -PU- Grant Agreement No. 224145 Authors List Leading Author (Editor) Surname Initials Beneficiary Name Contact email (Short Name) Staehli Benjamin SB CS [email protected] Co-authors (In alphabetic order) # Surname Initials Beneficiary Name Contact email (Short Name) 1 Mourouzis Alexandros MA CERTH/HIT [email protected], 2 Chalkia Eleni CE CERTH/HIT [email protected] 3 Bekiaris Evangelos BE CERTH/HIT [email protected] 5 Lopes, Rui R. FFCUL [email protected] 6 Kavadias Christoforos Ch. Solinet [email protected] 7 Antona AM FORTH [email protected] (add lines as appropriate) Peer Reviewers List # Surname Initials Contact email 1 Ntoa Stavroula NS [email protected] 2 Nitsch H [email protected] January 2010 -iii- CS ACCESSIBLE Deliverable D2.1 -PU- Grant Agreement No. 224145 History of versions Table Date Comments September 2009 1st version of D2.1 November 2009 First updated version of D2.1 with optimised methodological framework, updated standards and devices SoA. January 2010 Second updated version after the comments of the reviewers on the first ACCESSIBLE review.