SOX Vulnerability Assessment Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

My Cloud EX2 Ultra
My Cloud™ EX2 Ultra Privater Cloud-Speicher Bedienungsanleitung WD Service und Support Sollten Probleme auftreten, geben Sie uns bitte Gelegenheit, sie zu beheben, bevor Sie das Produkt zurücksenden. Viele technische Fragen können über unsere Knowledge Base oder unseren E-Mail-Support unter http://support.wd.com beantwortet werden. Falls Sie dort keine geeignete Antwort finden oder Sie einen persönlichen Kontakt bevorzugen, rufen Sie WD unter der unten angegebenen Telefonnummer Ihres Landes an. Ihr Produkt schließt eine 30-tägige kostenlose telefonische Unterstützung während der Garantiezeit ein. Diese 30-tägige Frist beginnt mit dem Datum Ihres ersten telefonischen Kontakts mit dem technischen Support von WD. Der E-Mail-Support ist für die gesamte Garantiezeit kostenlos, und unsere gesamte Knowledge Base ist rund um die Uhr verfügbar. Damit wir Sie weiterhin über neue Funktionen und Serviceleistungen informieren können, denken Sie bitte daran, Ihr Produkt im Internet zu registrieren unter http://register.wd.com. Zugriff auf den Onlinesupport Auf unserer Produktsupport-Website unter http://support.wd.com können Sie unter den folgenden Themen wählen: Downloads – Laden Sie Treiber, Software und Updates für Ihr WD-Produkt herunter. Registrierung – Registrieren Sie Ihr WD-Produkt, um die neuesten Updates und Sonderangebote zu erhalten. Garantie- und Austauschservices – Informationen über Garantie, Produktersatz (RMA), RMA-Status und Datenwiederherstellung. Knowledge Base – Suchen Sie nach Schlüsselwort, Ausdruck oder Antwort-ID. Installation – Hier finden Sie online Hilfe zur Installation Ihres WD-Produkts oder Ihrer Software. WD Community – Tauschen Sie Ihre Gedanken mit anderen WD-Benutzern aus. Online-Schulungszentrum – Kommen Sie hierhin, um das meiste aus Ihrem privaten Cloud-Speichergerät herauszuholen: (http://www.wd.com/setup). -

Free Linux Based Ftp Server
Free linux based ftp server Graphical UI based FTP Servers; Terminal/Console based FTP Servers Linux, AIX, UNIX, IBM i, VMware, EC2, Azure, Mac OS, Free FTP server with Graphical · Console/terminal-based · Summary board. The same source code compiles and runs on Linux, OpenBSD, NetBSD, one- disk router), ROOT Linux, Gentoo Linux and almost every other free operating system. Pure-FTPd can act as private FTP server and disallow all anonymous. Learn How FTP Server Works, Setup Open Source vsftpd Server in Linux, On Debian based distros like Ubuntu, you can install it like this. Welcome to the home of CrossFTP Server, the free secure FTP server for Windows, Mac, Linux, and more. almost everything: OS X - +, WinXP - Win+, Linux, Solaris, BSD, Unix, etc! CrushFTP is a robust file transfer server that makes it easy to setup secure is web based allowing you the ability to manage and monitor the server from You can see things like the number of active connections, free drive space. Download the latest and greatest of Linux FTP Server Software here. glFTPd is a free FTP server software for Linux and UNIX based systems. It is highly. Is there any sort of made for Linux FTP server software that features a GUI? I am a total newbie and I am getting my butt kicked by VSFTPD. vsftpd is a GPL licensed FTP server for UNIX systems, including Linux. It is secure and extremely fast. It is stable. Don't take my word for it, though. Below, we will. A glance at the common Linux ftp servers. -

1 KONFIGURACE GLFTPD a PZS-NG 1.1 Zadání 1.2 Teoretický
1 KONFIGURACE GLFTPD A PZS-NG 1.1 Zadání 1. Proveďte nastavení portů pro pasivní režim přenosu. 2. Proveďte vytvoření uživatele a nastavení jeho hodnot ratio, num_logins. 3. Proveďte zabezpečení GlFTPd pomocí SSL/TLS. 4. Nakonfigurujte PZS-NG pro ověřování kontrolních součtů a propojte jejsFTP démonem GlFTPd. 1.2 Teoretický úvod FTP (File Transfer Protocol) je aplikačním protokolem vrstvového modelu TCP/IP (Transmission Control Protocol/Internet Protocol). Využívá dvě TCP spojení trans- portní vrstvy označované jako řídící (kontrolní) a datové.[1, 2] Jedná se o textově orientovaný protokol pracující na principu klient-server, tzn. existuje server, kam jsou připojeni jednotliví klienti (například osobní počítače). Textové příkazy jsou posílány v paketech, které mohou být odchyceny a bez větších problémů přečteny. Nejedná se o nový protokol. FTP byl definován v RFC 114 (Request for Comments). Aktuální je definice v RFC 959[1], které vyšlo v říjnu roku 1985 a s použitím aktu- alizačních RFC je dnes stále využíváno převážně ke sdílení souborů.[1] 1.2.1 Aktivní režim Jedná se většinou o preferovaný režim přenosu, jelikož server nemusí otevírat porty a nemůže být přetížen mnoha žádostmi o data. Jak je zobrazeno na obr. 1.1. Přes řídící spojení je mezi klientem a serverem dohodnuto, na jaké IP adrese a portu budou data k dispozici (pomocí příkazu PORT). Spojení je navázáno ze serveru na sdělenou IP a port, kde se stáhne nebo nahraje soubor. Role serveru a klienta jsou tedy pro datové spojení vyměněny.[2] Tento režim však může být problematický při používání NAT (Network Address Translation) nebo firewallu, kdy je bráněno otevření portu na klientovi a následnému připojení serveru.[2] 1.2.2 Pasivní režim Problém NATu, který je způsoben nemožností připojení na klienta, a firewallu je vyřešen přenosem v pasivním režimu, kdy si klient se serverem nevymění role, ty zůstanou zachovány. -

Symantec Netrecon™ 3.6 Security Update 21 Release Notes Symantec Netrecon Security Update 21 Release Notes
Symantec NetRecon™ 3.6 Security Update 21 Release Notes Symantec NetRecon Security Update 21 Release Notes The software that is described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version: v3.6 040831 Copyright Notice Copyright 2004 Symantec Corporation. All Rights Reserved. Any technical documentation that is made available by Symantec Corporation is the copyrighted work of Symantec Corporation and is owned by Symantec Corporation. NO WARRANTY. The technical documentation is being delivered to you AS-IS and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014. Trademarks Symantec and the Symantec logo are U.S. registered trademarks, and Symantec NetRecon, Symantec Enterprise Security Architecture, Symantec Enterprise Security Manager, LiveUpdate, and Symantec Security Response are trademarks of Symantec Corporation. Microsoft, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product names that are mentioned in this manual may be trademarks or registered trademarks of their respective companies and are hereby acknowledged. Printed in the United States of America. 3 Technical support As part of Symantec Security Response, the Symantec Global Technical Support group maintains support centers throughout the world. -

Symantec Netrecon™ 3.6 Security Update 24 Release Notes Symantec Netrecon Security Update 24 Release Notes
Symantec NetRecon™ 3.6 Security Update 24 Release Notes Symantec NetRecon Security Update 24 Release Notes The software that is described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version: v3.6 040930 Copyright Notice Copyright 2005 Symantec Corporation. All Rights Reserved. Any technical documentation that is made available by Symantec Corporation is the copyrighted work of Symantec Corporation and is owned by Symantec Corporation. NO WARRANTY. The technical documentation is being delivered to you AS-IS and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014. Trademarks Symantec and the Symantec logo are U.S. registered trademarks, and Symantec NetRecon, Symantec Enterprise Security Architecture, Symantec Enterprise Security Manager, LiveUpdate, and Symantec Security Response are trademarks of Symantec Corporation. Microsoft, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product names that are mentioned in this manual may be trademarks or registered trademarks of their respective companies and are hereby acknowledged. Printed in the United States of America. 3 Technical support As part of Symantec Security Response, the Symantec Global Technical Support group maintains support centers throughout the world. -

Servicios De Red E Internet
SERVICIOS DE RED E INTERNET Autor: Miguel Ángel García Felipe IES GREGORIO PRIETO Servicios de Transferencia de Ficheros SERVICIOS DE RED E INTERNET SERVICIOS DE TRANSFERENCIA DE FICHEROS ÍNDICE 1. Funcionalidad del servicio de transferencia de archivos. - Características. Componentes y funcionamiento. - Protocolo FTP. - Tipos de usuarios y accesos al servicio: Acceso anónimo y acceso autorizado. - Configuración del servicio de transferencia de archivos. Permisos y cuotas. - Conexiones y modos: Conexión de control y conexión de datos. Modos activo y pasivo. - Tipos de transferencia de archivos: ASCII y Binario. - Clientes FTP: en línea de comandos, entornos “gráficos” y navegadores / exploradores. - Monitorización y registro del servicio de transferencia de archivos. - Seguridad en FTP. - FTPS (FTP/SSL): FTPS Implícito. FTPS Explícito (FTPES) - Protocolo FXP (File eXchange Protocol). 2. Servicio TFTP (Trivial File Transfer Protocol). 3. Servicios SFTP/SCP. 4. Transferencia o distribución de archivos entre iguales (peer-to-peer). - Características. Protocolos. Software. Configuración. 2 SERVICIOS DE RED E SERVICIOS DE TRANSFERENCIA DE FICHEROS INTERNET 1. Funcionalidad del servicio de transferencia de archivos. - Características. Componentes y funcionamiento. Es una utilidad que permite la copia de un archivo desde un ordenador a otro a través de una red de computadoras. El servicio más usado para realizar este movimiento es el FTP (File Transfer Protocol), el cual consiste en un programa FTP alojado en un servidor -llamado FTP daemon- el cual se encarga de gestionar las transacciones que solicita el cliente. Los movimientos que podemos realizar a la hora de transferir archivos de un equipo a otro son: "download" (bajada de archivos de Internet), "upload" (subida de archivos a Internet), o intercambio de objetos entre dos o más usuarios. -

Detecting and Analyzing Insecure Component Integration
Taeho Kwon December 2011 Computer Science Detecting and Analyzing Insecure Component Integration Abstract Component technologies have been widely adopted for designing and engineering software ap- plications and systems, which dynamically integrate software components to achieve desired func- tionalities. Engineering software in a component-based style has significant benefits, such as im- proved programmer productivity and software reliability. To support component integration, oper- ating systems allow an application to dynamically load and use a component. Although developers have frequently utilized such a system-level mechanism, programming errors can lead to insecure component integration and serious security vulnerabilities. The security and reliability impact of component integration has not yet been much explored. This dissertation systematically investigates security issues in dynamic component integration and their impact on software security. On the conceptual level, we formulate two types of insecure component integration—unsafe component loading and insecure component usage—and present practical, scalable techniques to detect and analyze them. Our techniques operate directly on soft- ware binaries and do not require source code. On the practical level, we have used them to discover new vulnerabilities in popular, real-world software, and show that insecure component integration is prevalent and can be exploited by attackers to subvert important software and systems. Our research has had substantial practical impact and helped -

Windows® Scripting Secrets®
4684-8 FM.f.qc 3/3/00 1:06 PM Page i ® WindowsSecrets® Scripting 4684-8 FM.f.qc 3/3/00 1:06 PM Page ii 4684-8 FM.f.qc 3/3/00 1:06 PM Page iii ® WindowsSecrets® Scripting Tobias Weltner Windows® Scripting Secrets® IDG Books Worldwide, Inc. An International Data Group Company Foster City, CA ♦ Chicago, IL ♦ Indianapolis, IN ♦ New York, NY 4684-8 FM.f.qc 3/3/00 1:06 PM Page iv Published by department at 800-762-2974. For reseller information, IDG Books Worldwide, Inc. including discounts and premium sales, please call our An International Data Group Company Reseller Customer Service department at 800-434-3422. 919 E. Hillsdale Blvd., Suite 400 For information on where to purchase IDG Books Foster City, CA 94404 Worldwide’s books outside the U.S., please contact our www.idgbooks.com (IDG Books Worldwide Web site) International Sales department at 317-596-5530 or fax Copyright © 2000 IDG Books Worldwide, Inc. All rights 317-572-4002. reserved. No part of this book, including interior design, For consumer information on foreign language cover design, and icons, may be reproduced or transmitted translations, please contact our Customer Service in any form, by any means (electronic, photocopying, department at 800-434-3422, fax 317-572-4002, or e-mail recording, or otherwise) without the prior written [email protected]. permission of the publisher. For information on licensing foreign or domestic rights, ISBN: 0-7645-4684-8 please phone +1-650-653-7098. Printed in the United States of America For sales inquiries and special prices for bulk quantities, 10 9 8 7 6 5 4 3 2 1 please contact our Order Services department at 1B/RT/QU/QQ/FC 800-434-3422 or write to the address above. -

Effective Web Design, Second Edition
Effective Web Design Effective Web Design, Second Edition Ann Navarro SYBEX® Associate Publisher: Cheryl Applewood Contracts and Licensing Manager: Kristine O'Callaghan Acquisitions and Developmental Editor: Raquel Baker Editors: Joseph A. Webb, James A. Compton, Colleen Wheeler Strand Production Editor: Dennis Fitzgerald Technical Editor: Marshall Jansen Book Designer: Maureen Forys, Happenstance Type-O-Rama Graphic Illustrator: Tony Jonick Electronic Publishing Specialist: Maureen Forys, Happenstance Type-O-Rama Proofreaders: Nelson Kim, Nancy Riddiough, Leslie E.H. Light Indexer: Ann Rogers CD Coordinator: Christine Harris CD Technician: Kevin Ly Cover Designer: Design Site Cover Illustrator/Photographer: Dan Bowman Copyright © 2001 SYBEX Inc., 1151 Marina Village Parkway, Alameda, CA 94501. World rights reserved. page 1 Effective Web Design The author(s) created reusable code in this publication expressly for reuse by readers. Sybex grants readers limited permission to reuse the code found in this publication or its accompanying CD-ROM so long as (author(s)) are attributed in any application containing the reusable code and the code itself is never distributed, posted online by electronic transmission, sold, or commercially exploited as a stand- alone product. Aside from this specific exception concerning reusable code, no part of this publication may be stored in a retrieval system, transmitted, or reproduced in any way, including but not limited to photocopy, photograph, magnetic, or other record, without the prior agreement and written permission of the publisher. An earlier version of this book was published under the title Effective Web Design © 1998 SYBEX Inc. Library of Congress Card Number: 2001088112 ISBN: 0-7821-2849-1 SYBEX and the SYBEX logo are either registered trademarks or trademarks of SYBEX Inc. -

AEG: Automatic Exploit Generation
AEG: Automatic Exploit Generation Thanassis Avgerinos, Sang Kil Cha, Brent Lim Tze Hao and David Brumley Carnegie Mellon University, Pittsburgh, PA fthanassis, sangkilc, brentlim, [email protected] Abstract two zero-day exploits for previously unknown vulnera- bilities. The automatic exploit generation challenge is given Our automatic exploit generation techniques have a program, automatically find vulnerabilities and gener- several immediate security implications. First, practical ate exploits for them. In this paper we present AEG, the AEG fundamentally changes the perceived capabilities first end-to-end system for fully automatic exploit gener- of attackers. For example, previously it has been be- ation. We used AEG to analyze 14 open-source projects lieved that it is relatively difficult for untrained attackers and successfully generated 16 control flow hijacking ex- to find novel vulnerabilities and create zero-day exploits. ploits. Two of the generated exploits (expect-5.43 and Our research shows this assumption is unfounded. Un- htget-0.93) are zero-day exploits against unknown vul- derstanding the capabilities of attackers informs what nerabilities. Our contributions are: 1) we show how defenses are appropriate. Second, practical AEG has ap- exploit generation for control flow hijack attacks can be plications to defense. For example, automated signature modeled as a formal verification problem, 2) we pro- generation algorithms take as input a set of exploits, and pose preconditioned symbolic execution, a novel tech- output an IDS signature (aka an input filter) that recog- nique for targeting symbolic execution, 3) we present a nizes subsequent exploits and exploit variants [3,8,9]. general approach for generating working exploits once Automated exploit generation can be fed into signature a bug is found, and 4) we build the first end-to-end sys- generation algorithms by defenders without requiring tem that automatically finds vulnerabilities and gener- real-life attacks. -

La Filosofia Open Source: Benefici E Modelli Di Sviluppo Aziendali. Analisi Di Casi Di Interfacciamento Tra Mondo Microsoft E Mondo Linux/Open Source
UNIVERSITÀ DEGLI STUDI DI NAPOLI “PARTHENOPE” FACOLTÀ DI ECONOMIA E COMMERCIO TESI SPERIMENTALE DI LAUREA IN ECONOMIA E GESTIONE DELLE IMPRESE La filosofia Open Source: Benefici e modelli di sviluppo aziendali. Analisi di casi di interfacciamento tra mondo Microsoft e mondo Linux/Open Source Relatore: Candidato: Ch.mo Prof.Giseppe Vito Massimiliano Gambardella matr. CE/935 Correlatore: Ch.mo Prof. Paolo Zanetti Anno accademico 2003/2004 Introduzione Questa tesi `e stata scritta in LATEX 2ε e compilata con Linux. Vuole essere una introduzione al mondo Open Source, con lo scopo di spiegare e di dimostrare il perch`e conviene introdurre i prodotti e la cultura Open Source nelle aziende. All’inizio verra spiegato cos’`e l’Open Source e verranno analizzate alcune delle licenze piu` utilizzate. Poi si passera` al TCO fatto alla AUSL di Rimi- ni per poi finire con un modello di sviluppo aziendale studiato da Martin Fink. Verranno trattati anche alcuni esempi di interfacciamento tra Microsoft e Linux. 3 Ringraziamenti Dedico questa tesi ai miei genitori che mi hanno sostenuto in questi anni, a Cristina che mi ha “sopportato” quando avevo dubbi ed ai miei amici che hanno sempre saputo spronarmi Ringrazio il mio amico RHCE che una sera di ottobre a Milano nel 1999 mi regalo` la mia prima copia originale di Red Hat Linux, facendo cos`ı inizia- re la mia avventura oltre che tutti i componenti della YACME s.r.l. che mi hanno seguito per il TCO ed all’Ing. Zamprogno della AUSL di Rimini per la sua disponibilita,` il Prof. Giuseppe Vito per la fiducia concessami e il Prof. -
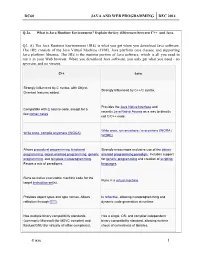
Dc60 Java and Web Programming Dec 2014
DC60 JAVA AND WEB PROGRAMMING DEC 2014 Q.2 a. What is Java Runtime Environment? Explain the key differences between C++ and Java. Q2. A) The Java Runtime Environment (JRE) is what you get when you download Java software. The JRE consists of the Java Virtual Machine (JVM), Java platform core classes, and supporting Java platform libraries. The JRE is the runtime portion of Java software, which is all you need to run it in your Web browser. When you download Java software, you only get what you need - no spyware, and no viruses. C++ Java Strongly influenced by C syntax, with Object- Strongly influenced by C++/C syntax. Oriented features added. Provides the Java Native Interface and Compatible with C source code, except for a recently Java Native Access as a way to directly few corner cases. call C/C++ code. Write once, run anywhere / everywhere (WORA / Write once, compile anywhere (WOCA). WORE). Allows procedural programming, functional Strongly encourages exclusive use of the object- programming, object-oriented programming, generic oriented programming paradigm. Includes support programming, and template metaprogramming. for generic programming and creation of scripting Favors a mix of paradigms. languages. Runs as native executable machine code for the Runs in a virtual machine. target instruction set(s). Provides object types and type names. Allows Is reflective, allowing metaprogramming and reflection through RTTI. dynamic code generation at runtime. Has multiple binary compatibility standards Has a single, OS- and compiler-independent (commonly Microsoft (for MSVC compiler) and binary compatibility standard, allowing runtime Itanium/GNU (for virtually all other compilers)). check of correctness of libraries.