Forensic Analysis of Browzar
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

My Cloud EX2 Ultra
My Cloud™ EX2 Ultra Privater Cloud-Speicher Bedienungsanleitung WD Service und Support Sollten Probleme auftreten, geben Sie uns bitte Gelegenheit, sie zu beheben, bevor Sie das Produkt zurücksenden. Viele technische Fragen können über unsere Knowledge Base oder unseren E-Mail-Support unter http://support.wd.com beantwortet werden. Falls Sie dort keine geeignete Antwort finden oder Sie einen persönlichen Kontakt bevorzugen, rufen Sie WD unter der unten angegebenen Telefonnummer Ihres Landes an. Ihr Produkt schließt eine 30-tägige kostenlose telefonische Unterstützung während der Garantiezeit ein. Diese 30-tägige Frist beginnt mit dem Datum Ihres ersten telefonischen Kontakts mit dem technischen Support von WD. Der E-Mail-Support ist für die gesamte Garantiezeit kostenlos, und unsere gesamte Knowledge Base ist rund um die Uhr verfügbar. Damit wir Sie weiterhin über neue Funktionen und Serviceleistungen informieren können, denken Sie bitte daran, Ihr Produkt im Internet zu registrieren unter http://register.wd.com. Zugriff auf den Onlinesupport Auf unserer Produktsupport-Website unter http://support.wd.com können Sie unter den folgenden Themen wählen: Downloads – Laden Sie Treiber, Software und Updates für Ihr WD-Produkt herunter. Registrierung – Registrieren Sie Ihr WD-Produkt, um die neuesten Updates und Sonderangebote zu erhalten. Garantie- und Austauschservices – Informationen über Garantie, Produktersatz (RMA), RMA-Status und Datenwiederherstellung. Knowledge Base – Suchen Sie nach Schlüsselwort, Ausdruck oder Antwort-ID. Installation – Hier finden Sie online Hilfe zur Installation Ihres WD-Produkts oder Ihrer Software. WD Community – Tauschen Sie Ihre Gedanken mit anderen WD-Benutzern aus. Online-Schulungszentrum – Kommen Sie hierhin, um das meiste aus Ihrem privaten Cloud-Speichergerät herauszuholen: (http://www.wd.com/setup). -

A Generic Data Exchange System for F2F Networks
The Retroshare project The GXS system Decentralize your app! A Generic Data Exchange System for F2F Networks Cyril Soler C.Soler The GXS System 03 Feb. 2018 1 / 19 The Retroshare project The GXS system Decentralize your app! Outline I Overview of Retroshare I The GXS system I Decentralize your app! C.Soler The GXS System 03 Feb. 2018 2 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows, (+ Android). C.Soler The GXS System 03 Feb. 2018 3 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows. C.Soler The GXS System 03 Feb. 2018 3 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows. C.Soler The GXS System 03 Feb. 2018 3 / 19 The Retroshare project The GXS system Decentralize your app! The Retroshare Project I Mesh computers using signed TLS over TCP/UDP/Tor/I2P; I anonymous end-to-end encrypted FT with swarming; I mail, IRC chat, forums, channels; I available on Mac OS, Linux, Windows. -

Anonymous Rate Limiting with Direct Anonymous Attestation
Anonymous rate limiting with Direct Anonymous Attestation Alex Catarineu Philipp Claßen Cliqz GmbH, Munich Konark Modi Josep M. Pujol 25.09.18 Crypto and Privacy Village 2018 Data is essential to build services 25.09.18 Crypto and Privacy Village 2018 Problems with Data Collection IP UA Timestamp Message Payload Cookie Type 195.202.XX.XX FF.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:01 1e550 195.202.XX.XX Chrome.. 2018-07-09 Page https://analytics.twitter.com/user/konark Cookie=966347bfd 14:06 modi 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:10 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 Page https://booking.com/hotels/barcelona Cookie=966347bfd 16:15 1e55040434abe… 195.202.XX.XX Chrome.. 2018-07-09 QueryLog [face, facebook.com] Cookie=966347bfd 14:10 1e55040434abe… 195.202.XX.XX FF.. 2018-07-09 Page https://shop.flixbus.de/user/resetting/res Cookie=966347bfd 18:40 et/hi7KTb1Pxa4lXqKMcwLXC0XzN- 1e55040434abe… 47Tt0Q 25.09.18 Crypto and Privacy Village 2018 Anonymous data collection Timestamp Message Type Payload 2018-07-09 14 Querylog [face, facebook.com] 2018-07-09 14 Querylog [boo, booking.com] 2018-07-09 14 Page https://booking.com/hotels/barcelona 2018-07-09 14 Telemetry [‘engagement’: 0 page loads last week, 5023 page loads last month] More details: https://gist.github.com/solso/423a1104a9e3c1e3b8d7c9ca14e885e5 http://josepmpujol.net/public/papers/big_green_tracker.pdf 25.09.18 Crypto and Privacy Village 2018 Motivation: Preventing attacks on anonymous data collection Timestamp Message Type Payload 2018-07-09 14 querylog [book, booking.com] 2018-07-09 14 querylog [fac, facebook.com] … …. -

DARK WEB INVESTIGATION GUIDE Contents 1
DARK WEB INVESTIGATION GUIDE Contents 1. Introduction 3 2. Setting up Chrome for Dark Web Access 5 3. Setting up Virtual Machines for Dark Web Access 9 4. Starting Points for Tor Investigations 20 5. Technical Clues for De-Anonymizing Hidden Services 22 5.1 Censys.io SSL Certificates 23 5.2 Searching Shodan for Hidden Services 24 5.3 Checking an IP Address for Tor Usage 24 5.4 Additional Resources 25 6. Conclusion 26 2 Dark Web Investigation Guide 1 1. Introduction 3 Introduction 1 There is a lot of confusion about what the dark web is vs. the deep web. The dark web is part of the Internet that is not accessible through traditional means. It requires that you use a technology like Tor (The Onion Router) or I2P (Invisible Internet Project) in order to access websites, email or other services. The deep web is slightly different. The deep web is made of all the webpages or entire websites that have not been crawled by a search engine. This could be because they are hidden behind paywalls or require a username and password to access. We are going to be setting up access to the dark web with a focus on the Tor network. We are going to accomplish this in two different ways. The first way is to use the Tor Browser to get Google Chrome connected to the the Tor network. This is the less private and secure option, but it is the easiest to set up and use and is sufficient for accessing material on the dark web. -

Symantec Netrecon™ 3.6 Security Update 21 Release Notes Symantec Netrecon Security Update 21 Release Notes
Symantec NetRecon™ 3.6 Security Update 21 Release Notes Symantec NetRecon Security Update 21 Release Notes The software that is described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version: v3.6 040831 Copyright Notice Copyright 2004 Symantec Corporation. All Rights Reserved. Any technical documentation that is made available by Symantec Corporation is the copyrighted work of Symantec Corporation and is owned by Symantec Corporation. NO WARRANTY. The technical documentation is being delivered to you AS-IS and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014. Trademarks Symantec and the Symantec logo are U.S. registered trademarks, and Symantec NetRecon, Symantec Enterprise Security Architecture, Symantec Enterprise Security Manager, LiveUpdate, and Symantec Security Response are trademarks of Symantec Corporation. Microsoft, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product names that are mentioned in this manual may be trademarks or registered trademarks of their respective companies and are hereby acknowledged. Printed in the United States of America. 3 Technical support As part of Symantec Security Response, the Symantec Global Technical Support group maintains support centers throughout the world. -

Symantec Netrecon™ 3.6 Security Update 24 Release Notes Symantec Netrecon Security Update 24 Release Notes
Symantec NetRecon™ 3.6 Security Update 24 Release Notes Symantec NetRecon Security Update 24 Release Notes The software that is described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version: v3.6 040930 Copyright Notice Copyright 2005 Symantec Corporation. All Rights Reserved. Any technical documentation that is made available by Symantec Corporation is the copyrighted work of Symantec Corporation and is owned by Symantec Corporation. NO WARRANTY. The technical documentation is being delivered to you AS-IS and Symantec Corporation makes no warranty as to its accuracy or use. Any use of the technical documentation or the information contained therein is at the risk of the user. Documentation may include technical or other inaccuracies or typographical errors. Symantec reserves the right to make changes without prior notice. No part of this publication may be copied without the express written permission of Symantec Corporation, 20330 Stevens Creek Blvd., Cupertino, CA 95014. Trademarks Symantec and the Symantec logo are U.S. registered trademarks, and Symantec NetRecon, Symantec Enterprise Security Architecture, Symantec Enterprise Security Manager, LiveUpdate, and Symantec Security Response are trademarks of Symantec Corporation. Microsoft, MS-DOS, Windows, and Windows NT are registered trademarks of Microsoft Corporation. Other product names that are mentioned in this manual may be trademarks or registered trademarks of their respective companies and are hereby acknowledged. Printed in the United States of America. 3 Technical support As part of Symantec Security Response, the Symantec Global Technical Support group maintains support centers throughout the world. -

An Analysis of Private Browsing Modes in Modern Browsers
An Analysis of Private Browsing Modes in Modern Browsers Gaurav Aggarwal Elie Bursztein Collin Jackson Dan Boneh Stanford University CMU Stanford University Abstract Even within a single browser there are inconsistencies. We study the security and privacy of private browsing For example, in Firefox 3.6, cookies set in public mode modes recently added to all major browsers. We first pro- are not available to the web site while the browser is in pose a clean definition of the goals of private browsing private mode. However, passwords and SSL client cer- and survey its implementation in different browsers. We tificates stored in public mode are available while in pri- conduct a measurement study to determine how often it is vate mode. Since web sites can use the password man- used and on what categories of sites. Our results suggest ager as a crude cookie mechanism, the password policy that private browsing is used differently from how it is is inconsistent with the cookie policy. marketed. We then describe an automated technique for Browser plug-ins and extensions add considerable testing the security of private browsing modes and report complexity to private browsing. Even if a browser ad- on a few weaknesses found in the Firefox browser. Fi- equately implements private browsing, an extension can nally, we show that many popular browser extensions and completely undermine its privacy guarantees. In Sec- plugins undermine the security of private browsing. We tion 6.1 we show that many widely used extensions un- propose and experiment with a workable policy that lets dermine the goals of private browsing. -

Detecting and Analyzing Insecure Component Integration
Taeho Kwon December 2011 Computer Science Detecting and Analyzing Insecure Component Integration Abstract Component technologies have been widely adopted for designing and engineering software ap- plications and systems, which dynamically integrate software components to achieve desired func- tionalities. Engineering software in a component-based style has significant benefits, such as im- proved programmer productivity and software reliability. To support component integration, oper- ating systems allow an application to dynamically load and use a component. Although developers have frequently utilized such a system-level mechanism, programming errors can lead to insecure component integration and serious security vulnerabilities. The security and reliability impact of component integration has not yet been much explored. This dissertation systematically investigates security issues in dynamic component integration and their impact on software security. On the conceptual level, we formulate two types of insecure component integration—unsafe component loading and insecure component usage—and present practical, scalable techniques to detect and analyze them. Our techniques operate directly on soft- ware binaries and do not require source code. On the practical level, we have used them to discover new vulnerabilities in popular, real-world software, and show that insecure component integration is prevalent and can be exploited by attackers to subvert important software and systems. Our research has had substantial practical impact and helped -

Windows® Scripting Secrets®
4684-8 FM.f.qc 3/3/00 1:06 PM Page i ® WindowsSecrets® Scripting 4684-8 FM.f.qc 3/3/00 1:06 PM Page ii 4684-8 FM.f.qc 3/3/00 1:06 PM Page iii ® WindowsSecrets® Scripting Tobias Weltner Windows® Scripting Secrets® IDG Books Worldwide, Inc. An International Data Group Company Foster City, CA ♦ Chicago, IL ♦ Indianapolis, IN ♦ New York, NY 4684-8 FM.f.qc 3/3/00 1:06 PM Page iv Published by department at 800-762-2974. For reseller information, IDG Books Worldwide, Inc. including discounts and premium sales, please call our An International Data Group Company Reseller Customer Service department at 800-434-3422. 919 E. Hillsdale Blvd., Suite 400 For information on where to purchase IDG Books Foster City, CA 94404 Worldwide’s books outside the U.S., please contact our www.idgbooks.com (IDG Books Worldwide Web site) International Sales department at 317-596-5530 or fax Copyright © 2000 IDG Books Worldwide, Inc. All rights 317-572-4002. reserved. No part of this book, including interior design, For consumer information on foreign language cover design, and icons, may be reproduced or transmitted translations, please contact our Customer Service in any form, by any means (electronic, photocopying, department at 800-434-3422, fax 317-572-4002, or e-mail recording, or otherwise) without the prior written [email protected]. permission of the publisher. For information on licensing foreign or domestic rights, ISBN: 0-7645-4684-8 please phone +1-650-653-7098. Printed in the United States of America For sales inquiries and special prices for bulk quantities, 10 9 8 7 6 5 4 3 2 1 please contact our Order Services department at 1B/RT/QU/QQ/FC 800-434-3422 or write to the address above. -

The Potential Harms of the Tor Anonymity Network Cluster Disproportionately in Free Countries
The potential harms of the Tor anonymity network cluster disproportionately in free countries Eric Jardinea,1,2, Andrew M. Lindnerb,1, and Gareth Owensonc,1 aDepartment of Political Science, Virginia Tech, Blacksburg, VA 24061; bDepartment of Sociology, Skidmore College, Saratoga Springs, NY 12866; and cCyber Espion Ltd, Portsmouth PO2 0TP, United Kingdom Edited by Douglas S. Massey, Princeton University, Princeton, NJ, and approved October 23, 2020 (received for review June 10, 2020) The Tor anonymity network allows users to protect their privacy However, substantial evidence has shown that the preponder- and circumvent censorship restrictions but also shields those ance of Onion/Hidden Services traffic connects to illicit sites (7). distributing child abuse content, selling or buying illicit drugs, or With this important caveat in mind, our data also show that the sharing malware online. Using data collected from Tor entry distribution of potentially harmful and beneficial uses is uneven, nodes, we provide an estimation of the proportion of Tor network clustering predominantly in politically free regimes. In particular, users that likely employ the network in putatively good or bad the average rate of likely malicious use of Tor in our data for ways. Overall, on an average country/day, ∼6.7% of Tor network countries coded by Freedom House as “not free” is just 4.8%. In users connect to Onion/Hidden Services that are disproportion- countries coded as “free,” the percentage of users visiting Onion/ ately used for illicit purposes. We also show that the likely balance Hidden Services as a proportion of total daily Tor use is nearly of beneficial and malicious use of Tor is unevenly spread globally twice as much or ∼7.8%. -
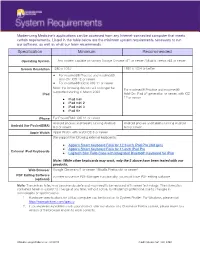
Specification Minimum Recommended
Modernizing Medicine’s applications can be accessed from any Internet-connected computer that meets certain requirements. Listed in the table below are the minimum system requirements necessary to run our software, as well as what our team recommends. Specification Minimum Recommended Operating System Any system capable of running Google Chrome v71 or newer / Mozilla Firefox v64 or newer 1280 x 10241 1920 x 1024 or better Screen Resolution ● For modmed® Practice and modmed® Add-On: iOS 12 or newer ● For modmed® Kiosk: iOS 11 or newer Note: the following devices will no longer be For modmed® Practice and modmed® supported starting in March 2020. th Add-On: iPad 5 generation or newer, with iOS iPad 12 or newer ● iPad mini ● iPad mini 2 ● iPad mini 3 ● iPad Air iPhone For PocketEMA: iOS 11 or newer Android phones and tablets running Android Android phones and tablets running Android Android (for PocketEMA) 6.0 or newer 6.0 or newer Apple Watch Apple Watch with watchOS 3 or newer We support the following external keyboards: ● Apple's Smart Keyboard Folio for 12.9-inch iPad Pro (3rd gen) ● Apple's Smart Keyboard Folio for 11-inch iPad Pro External iPad Keyboards ● Logitech Slim Folio Case with Integrated Bluetooth Keyboard for iPad Note: While other keyboards may work, only the 3 above have been tested with our products. Google Chrome v71 or newer / Mozilla Firefox v64 or newer2 Web Browser PDF Editing Software In order to use the PDF Manager Functionality, you must have PDF editing software (optional) Note: The devices listed may become obsolete and may need to be replaced with newer technology. -

Technical and Legal Overview of the Tor Anonymity Network
Emin Çalışkan, Tomáš Minárik, Anna-Maria Osula Technical and Legal Overview of the Tor Anonymity Network Tallinn 2015 This publication is a product of the NATO Cooperative Cyber Defence Centre of Excellence (the Centre). It does not necessarily reflect the policy or the opinion of the Centre or NATO. The Centre may not be held responsible for any loss or harm arising from the use of information contained in this publication and is not responsible for the content of the external sources, including external websites referenced in this publication. Digital or hard copies of this publication may be produced for internal use within NATO and for personal or educational use when for non- profit and non-commercial purpose, provided that copies bear a full citation. www.ccdcoe.org [email protected] 1 Technical and Legal Overview of the Tor Anonymity Network 1. Introduction .................................................................................................................................... 3 2. Tor and Internet Filtering Circumvention ....................................................................................... 4 2.1. Technical Methods .................................................................................................................. 4 2.1.1. Proxy ................................................................................................................................ 4 2.1.2. Tunnelling/Virtual Private Networks ............................................................................... 5