Syllabus Mobile Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Tohoku University Fact Book 2008 東北大学概要 2008 Tohoku University Fact Book 2008
Tohoku University Fact Book 2008 東北大学概要 2008 Tohoku University Fact Book 2008 CONTENTS 〈Introduction〉 Historical Background ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 01 Mission Statement and Towards Tohoku University 2016・・ 02 Message from the President ・・・・・・・・・・・・・・・・・・・・・・・・・・ 03 Tohoku University’s Official Symbol, School Colors, Song and Logo ・・・・・・・・・・・・・・・・・・・・・・・・ 04 Presidents of Tohoku University ・・・・・・・・・・・・・・・・・・・・・・・ 05 Japan Academy Members ・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 06 Chronological Chart ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 07 Prize Winners ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 09 University Awards ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 12 The 100th Anniversary Projects ・・・・・・・・・・・・・・・・・・・・・・・ 14 〈Organization〉 Organization Chart ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 17 Administrative Staff ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 20 President Election Committee ・・・・・・・・・・・・・・・・・・・・・・・・ 22 Board of Directors ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 22 Management Committee ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 22 Education and Research Council ・・・・・・・・・・・・・・・・・・・・・・ 23 University Personnel ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 24 Faculties ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 25 Graduate Schools ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 25 Research Institutes ・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・・ 26 Inter-Department Institutes for Education and Research ・・ 26 University Collaborating Institutions ・・・・・・・・・・・・・・・・・・・ 27 Institute of Liberal Arts and Sciences・・・・・・・・・・・・・・・・・・・ 27 WPI Advanced Institute for Materials Research(WPI-AIMR) ・・・・ 27 Information Synergy Organization -

Tohoku University Fact Book 2014 Sendai 980-8577 JAPAN Aoba-Ku
Tohoku University Fact Book 201 4 Tohoku University Fact Book 2014 Tohoku University Fact Book 2014 2-1-1, Katahira, Aoba-ku, Sendai 980-8577 JAPAN http://www.tohoku.ac.jp/ 東北大概要EN-AD面-三[1].indd 1 2014/09/01 18:27:52 2014 〈Introduction〉 Historical Background 01 ●Land: 92,746㎡ ●Buildings: 30,847㎡ (as of April 1, 2014) Mission Statement and Towards Tohoku University 2016 02 5 AMAMIYA CAMPUS Message from the President 03 1-1, Amamiya-machi, Tsutsumidori, Aoba-ku, Sendai 981-8555 Phone: +81-22-717-8603 Tohoku University Official Symbol, Logo, School Colors and Songs 04 Graduate School of Agricultural Science / Faculty of Agriculture Presidents of Tohoku University 05 Japan Academy Members 06 Chronological Chart of Tohoku University's History 07 Prize Winners 09 University Awards 13 〈Organization〉 Organization Chart 15 Administrative Staff 18 President Election Committee 20 Board of Directors 20 Management Committee 20 Education and Research Council 21 University Personnel 22 Faculties / Schools 23 Graduate Schools 23 Research Institutes 24 Inter-Department Institutes for Education and Research 24 Tsutsumi-dori 1 University Collaborating Institutions 25 Organization for Advanced Studies 26 3 Advanced Institute for Materials Research (AIMR) 26 2 Tohoku Forum for Creativity 26 Miyagi University of Information Synergy Organization 26 4 5 6 Education Affilated Tohoku Medical Megabank Organization 26 Junior High School Promotion Office of Strategic Innovation 26 1717 Division of Engineering and Technical Staff 26 7 1414 1515 Micro System Integration Center (μSIC) 26 10 1616 Center for Spintronics Integrated Systems 27 Research Organization of Electrical Communication 27 11 8 9 Center for Collaborative Research on Materials Science 27 ■ 1919 Center for Innovative Integrated Electronic Systems 27 Historical Background Organization for Leading Graduate School Program Tohoku University, formerly known as the Tohoku 27 12 Material Solutions Center(MaSC) 27 Imperial University, was founded in 1907. -

The Promise of Ubiquity Mobile As Media Platform in the Global South
EUROPE THE PROMISE OF UBIQUITY MOBILE AS MEDIA PLATFORM IN THE GLOBAL SOUTH 7 2 2 8 2 8 INTERNEWS EUROPE 3 EUROPE THE PROMISE OF UBIQUITY MOBILE AS MEDIA PLATFORM IN THE GLOBAL SOUTH INTERNEWS EUROPE THE PROMISE OF UBIQUITY Credits Produced by John West for Internews Europe © 2008. All rights reserved. This report is available in PDF online at http://www.internews.eu This publication was generously supported by the Dutch Ministry of Foreign Affairs and Internews Network. 2 CONTENTS Table of Contents 1. Executive Summary 1 2. Reach – mobile now matches TV in the South 5 2.1. 2006-8 Explosion 5 2.2. Predicted continued growth 6 2.3. Generalised pattern 7 2.4. South not G7, East or Middle East 8 2.5. Least-Developed Countries 9 2.6. The decision-maker’s bubble 10 2.7. A BOP business 11 a) MNOs and the decline of ARPU 11 b) Handset manufacturers 13 c) Government: critical mass of competition 13 3. Case Studies 15 3.1. Ken Banks – FrontlineSMS 15 3.2. Paul Meyer – Voxiva LLC 16 3.3. Jasmine News Service 17 3.4. Emmanuel de Dinechin – Altai Consulting 18 3.5. Jonathan Marks, Critical Distance 19 3.6. Mike Grenville – 160Characters.org 20 3.7. Bobby Soriano – mobile in the Philippines 21 3.8. Illico Elia, Thomson Reuters Mobile Products 22 3.9. Jan Blom, designer, Nokia, Bangalore 23 4. The implications for southern media 25 4.1. Working Conclusions 25 a) If you don’t do it, someone else will 25 b) It’s only just beginning 25 c) Text is everywhere, voice is (surprisingly) nowhere 25 d) Know what you’re offering 25 e) Know Your Market 26 f) It’s tough down the food chain – strike out on your own if you can 26 g) Look Everywhere for the Business Model 26 h) Broadcast point of departure: participation 26 i) Print point of departure: the right snippet of data 26 5. -

Industry-University Collaboration Activities at TOHOKU UNIVERSITY
Japan - Taiwan Workshop on “Industry-Academia Collaboration” (2015.03.10) Industry-University Collaboration Activities at TOHOKU UNIVERSITY About Tohoku University • Number of Faculties/ Schools: Undergraduate (10), Graduate (16), Professional Graduate Schools (3), Research Institutes (6), Hospital (1) • Number of Students: 17,852 Undergraduate 11,060 Graduate 6,757 International Students 1,532 (Taiwanese Students 42) • Number of Staff: 6,211 As of May 2014 2 Tohoku University’s Vision 3 Core Principles since its Foundation (1907) Practice-Oriented Research First Open-Door Research and Education Satomi Vision (2013) “Leap for World Class” “Lead Reconstruction of Tohoku and Regeneration of Japan” Focus of Industry-University Collaboration □“Leap for World Class” ⇒ Implementation of Large-Scale Joint Research Formulation of Research Centers/Hubs Inducement of New Industries □“Lead Reconstruction of Tohoku and Regeneration of Japan” ⇒ Contribution toward Regional Construction (Industry-University Collaboration leading to attraction of companies and creation of new ventures) 3 + History産学連携活動の歴史 of Industry-University Collaboration Tradition of “Practice-Oriented Research and Education” 1917 Dr. Kotaro Honda’s “KS Steel” (Institute for Materials Research) 1926 Dr. Shuji Yagi & Dr. Shintaro Uda’s “Yagi-Uda Antenna” (Research Institute for Electrical Communication) 1944 Research Institute for Electromagnetic Materials 1961 Semiconductor Research Institute Forerunners of University Startups 1938 Former Tohoku Metal Industries Co., Ltd. (NEC TOKIN Corporation) 1952 Former Yagi Antenna Inc. (Hitachi Kokusai Electric Inc.) Commercial Applications: • Yagi-Uda Antenna TV Antenna • Magnetron Radar, Microwave etc. • Magnetic Recording Yagi-Uda Antenna (1929) Magnetron (1927) Magnetic Recording(1932) Floppy Disk, HDD etc. 4 Tohoku University’s Potential+ ①Ranking by Research Fields ④Number of University Startups 2014 Overall: No. -

Hearing Aid Compatibility Compliance Efforts Status Report #6
Before the Federal Communications Commission Washington, DC In the Matter of ) ) Section 68.4(a) of the Commission’s Rules ) WT Docket No. 01-309 Governing Hearing Aid Compatible Telephones ) ) ) Hearing Aid Compatibility Compliance Efforts Status Report #6 Submitted by the Alliance for Telecommunications Industry Solutions (ATIS) on behalf of The ATIS Incubator Solutions Program #4 Alliance for Telecommunications Industry Solutions 1200 G Street, NW Suite 500 Washington, DC 20005 By: Thomas Goode General Counsel (202) 434-8830 Table of Contents I. INTRODUCTION....................................................................................................................... 3 A. General Overview of AISP.4-HAC ....................................................................................... 4 B. FCC Hearing Aid Compatibility Regulations ....................................................................... 5 II. Consolidated HAC Compliance Report ..................................................................................... 7 Table 1- Consolidated Status Report from Wireless Device Manufacturers on HAC Compliance Devices ............................................................................................................... 7 Table 2- Consolidated Status Report from Service Providers on HAC Compliance Devices 8 III. AISP.4-HAC Working Group Reports ..................................................................................... 8 A. Measurement and Test Plan (WG-4) ................................................................................... -
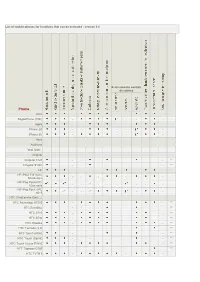
List of Mobile Phones for Functions That Can Be Activated - Version 5.4
List of mobile phones for functions that can be activated - version 5.4 Scaricamento contatti da rubrica Phone Amoi SkypePhone (TRE) - - - - Apple iPhone 2G - - - - - iPhone 3G - - - - Asus Audiovox Vedi Qtek... Cingular Cingular 8125 - - - ** Cingular SYNC - - - ** HP HP iPAQ 514 Voice - - - - - Messenger HP iPaq Pocket PC - - -* - - - - - - 63xx serie HP iPaq Pocket PC -* - - -* - - 6515 HTC (Vedi anche Qtek....) HTC Advantage X7500 - - ** HTC Excalibur - - - ** HTC S710 - - ** HTC S730 - - ** HTC Shadow - - ** HTC Tornado (2.0) ** HTC Touch (Alltel) - - - ** HTC Touch (Sprint) - - - - ** HTC Touch Cruise P3650 - - ** HTC Typhoon C500 ** HTC TyTN II - - - HTC Wizard ** Qteck/HTC P3300 - - - - - - - Qteck/HTC Touch Diamond - - - i-Mate Vedi Qtek LG LG CU500 - - ** LG KE850 - - - - - - - - LG KE850 Prada - - - ** LG KG800 (Chocolate) - - - - - - - - ** LG KS20 - - ** LG KU990 - - - ** LG KU800 - - - - - - - - - ** LG Shine (CU720) N N N ** LG Trax (CU575) N N N N N N ** LG U8550 - - - - -* LG U880 - - - - - - - - LG U900 - - - - - - - - Motorola Motorola A830/ - - - - A835 Motorola A1000 - - - - -* - Motorola A1200 Ming N ** Motorola E1000 - Motorola E398 - - - Motorola i615 N ** Motorola i880 N ** Motorola KRZR K1 - Motorola MPX220 - - - - - - Motorola RAZR2V9/ KRZR K3/ RAZR V3xx/ RAZR - MaxxV6 Motorola RAZR V3i/V3r ** Motorola RAZR V3t ** Motorola RAZR V6 Maxx ** Motorola RIZR Z3 - Motorola ROKR E6 N N ** Motorola Sidekick Slide N N N N ** Motorola SLVR L6 - Motorola SLVR L7 - Motorola U9 N N ** Motorola RAZR V3 - - Motorola V8 - - Motorola -

Tohoku University Fact Book 2013
Tohoku University Fact Book 201 3 Tohoku University Fact Book 2013 東北大学概要 2013 Tohoku University Fact Book 2013 http://www.tohoku.ac.jp/ 東北大概要EN-AD面-初[1].indd 1 2013/06/18 11:13:54 2013 2013 Campus Map ●Land: 92,746㎡ ●Buildings: 31,322㎡ (as of April 1, 2013) 〈Introduction〉 5 AMAMIYA CAMPUS Historical Background 01 1-1, Amamiya-machi, Tsutsumidori, Aoba-ku, Sendai 981-8555 Phone: +81-22-717-8603 Mission Statement and Towards Tohoku University 2016 02 Message from the President 03 Graduate School of Agricultural Science / Faculty of Agriculture Tohoku University's Official Symbol,School Colors, Song and Logo 04 Presidents of Tohoku University 05 Japan Academy Members 06 Chronological Chart of Tohoku University's History 07 Prize Winners 09 University Awards 12 〈Organization〉 Organization Chart 15 Administrative Staff 18 President Election Committee 20 Board of Directors 20 Management Committee 20 Education and Research Council 21 University Personnel 22 Faculties / Schools 23 Tsutsumi-dori 1 Graduate Schools 23 Research Institutes 24 3 Inter-Department Institutes for Education and Research 24 2 University Collaborating Institutions 25 Miyagi University of 4 Advanced Institute for Materials Research (AIMR) 25 5 6 Education Affilated Junior High School Information Synergy Organization 25 1717 Tohoku Medical Megabank Organization 26 7 1414 1515 Division of Engineering and Technical Staff 26 10 1616 Institute of Liberal Arts and Sciences 26 ■ Historical Background Micro System Integration Center (μSIC) 26 11 Tohoku University, formerly known as the Tohoku 8 9 Center for Spintronics Integrated Systems 26 1919 Research Organization of Electrical Communication 26 Imperial University, was founded in 1907. -

OFFICIAL GAZETTE ENGLISH 0OVERNMENT PRINTING BUREAU 1 EDITION W=I-^--T-Fl==Hb Mzmmm*M*I
OFFICIAL GAZETTE ENGLISH 0OVERNMENT PRINTING BUREAU 1 EDITION w=i-^--t-fl==hB mzmmm*m*i EXTRA No. 4 FRIDAY, JANUARY. 7, 1949 NOTICE PUBLIC NOTICE OF SCREENING RESULT No. 15 (December 16-December 31, 1948) January 7, 1949 Director-General of Cabinet Secretariat SATO Eisaku 1 This table shows the screening result made bv the Prime Minister in armrHanrA >*. f^ Imperial Ordinance concerning the Exclusion, Retirement, etc. from Public Offices (Imperial Ordinance No. 1 of 1947), Matters concerning the Exclusion from the Candidature for Mayor of City, Headman of Town or Village and Others (Imperial Ordinance No. 3 of 1947), Matters concerning the Enforcement of Imperial Ordinance No. 1 of 1947 (Cabinet and Home Ministry Ordinance No. 1 of 1947) and provisions of Cabinet Order No. 62 of 1948. 2. This table is to be most widely made public. The office of a city, ward, town or village shall, upon the receipt of this official report, placard the same. This table shall, at least, be placarded for a month, and it shall, upon receipt of the next official report, be replaced by a new one. The old report replaced, shall not be destroyed, and be preserved after binding at the office of the city, ward, town or village, to make it possible for public perusal. 3. The Questionnaires of the persons who were published on this table and of whom the screening has been completed shall be kept and offered for the public perusal at the Inspection Section of the Cabinet Secretariat or offices of the prefectures concerned. Any one may, at his request, freely peruse Questionnaires of the preceding paragraph. -

ED 267 – Arts & Médias
UNIVERSITÉ DE PARIS 3 – SORBONNE NOUVELLE ED 267 – Arts & Médias Thèse pour l'obtention du titre de Docteur en Sciences de l'Information et de la Communication par Alexandre JOLIN sous la direction de Madame Chantal DUCHET Convergence numérique et convergence des stratégies de groupe des éditeurs de chaînes de télévision traditionnels en Europe : vers une redéfinition des modèles d'affaires des éditeurs de services de médias audiovisuels historiques. Soutenue publiquement le 21 janvier 2016 devant le jury composé de : Philippe BOUQUILLION Professeur HDR en Sciences de l’Information et Rapporteur de la Communication Université Paris13 Laurent CRETON Professeur HDR en Sciences de l’Information et Président de la Communication Université Sorbonne Nouvelle - Paris 3 Chantal DUCHET Professeur HDR en Sciences de l’Information et Directrice de thèse de la Communication Université Sorbonne Nouvelle - Paris 3 Thomas PARIS Professeur affilié à HEC School of Management Rapporteur Chargé de Recherches au CNRS RESUMÉ TITRE: Convergence numérique et convergence des stratégies de groupe des éditeurs de chaînes de télévision traditionnels en Europe : vers une redéfinition des modèles d'affaires des éditeurs de services de médias audiovisuels historiques Nous étudions les stratégies de groupe des éditeurs de chaînes de télévision gratuites et payantes historiques, contraintes par les évolutions rapides et structurelles induites par la convergence numérique. Nous structurons notre démonstration en quatre grandes parties suivant une approche stratégique de tradition descriptive, principalement inspirée par l'école de l'environnement. Au cours des trois premières parties, nous exposerons et débâterons des mutations d’un environnement général que nous aborderons à travers trois dimensions : une dimension technologique, une dimension sociale et une dimension économique et réglementaire qui sera également l’occasion d’étudier les effets de l’environnement général sur les sphères industrielles et concurrentielles. -

Release Notes for Cradlepoint Rev 2.2.1 Firmware
Release Notes for CradlePoint rev 2.2.1 Firmware Products supported/tested: Cradlepoint Travel Router (CTR350) Personal Hotspot (PHS300) Phone modems/handsets tested (devices added since 2.1 in blue): USB Modems Franklin CDU-550/Sprint Franklin CDU-680/Sprint and nTelos (GPS - see Known Issues) Huawei E220/AT&T Novatel MC950D/AT&T and Rogers Novatel U720/Sprint and Verizon (GPS – Sprint only) Novatel U727/Sprint and Verizon (GPS – Sprint only) Pantech UM150/Verizon and Alltel Sierra Wireless 595U USB/Sprint, Verizon and Telus (GPS – Sprint only) Sierra Wireless Compass 597U/Sprint (GPS) Sierra Wireless 875U USB/AT&T Sierra Wireless 880U/AT&T Sierra Wireless 881U USB/AT&T Sierra Wireless Compass 885U USB/AT&T ExpressCard Modems (Requires an ExpressCard-to-USB adaptor) Kyocera KPC680/Sprint and Verizon Novatel EX720/Sprint (GPS) Novatel V740/Verizon Novatel X950D/Rogers Option GT Max 3.6 Express/AT&T* Option GT Ultra Express/AT&T* Note: Requires an ExpressCard-to-USB adapter that provides 1.2V Sierra Wireless 597E/Sprint and Telus (GPS - Sprint only) Sierra Wireless 880E/AT&T Handsets HP iPaq 910/AT&T HTC Touch/Sprint HTC Mogul PPC-6800/Sprint (see usage note under RNDIS below) HTC Apache PPC-6700/Sprint LG VX8000 and VX8300/Verizon LG VX7200/Verizon LG Musiq/Sprint LG Fusic LX-500/Sprint Motorola v3c RAZR/Sprint and Verizon Motorola RAZR2/Sprint Motorola Q and Q9c/Sprint Motorola RAZR v3xx/AT&T Motorola Q v9h/AT&T Motorola KRZR/Sprint Palm 700w/Sprint and Verizon Palm 700p/Verizon Palm 755p/Sprint Palm Centro/Sprint * * Note: Use of the Palm Centro requires Router Rev. -

Candid Cameras: Helping Dallas Cops Bust Criminals Page 3
Published by www.TodaysWirelessWorld.com Spring 2007 Candid Cameras: Helping Dallas Cops Bust Criminals Page 3 IN THIS ISSUE Product Review | Page 8 Industry Spotlight | Page 13 Wireless Lifestyle | Page 18 Success Story | Page 23 Digital Two-Way Radios Construction Mt. Everest Expedition Spring ISD Spring 2007 Contents PUBLISHERS: OPENING THOUGHts: Wireless Technology is More than Just a Convenience KENT HUFFMAN 1 Chief Marketing Officer, BearCom COVER StorY: BILL NEWTON Candid Cameras: Helping Dallas Cops Bust Criminals Principal, BNewton Associates 3 EDITORS-IN-CHIEF: ProdUct REVIEW (Motorola Digital Two-Way Radios): JOHN WATSON 8 MOTOTRBO Puts Corporate America in the Passing Lane Chairman, BearCom INDUstrY SpotliGHT (Construction): JERRY DENHAM President & CEO, BearCom 13 Construction Industry Gets a Hand from Wireless Technology MANAGING EDITOR: Comic Strip: HOLT HACKNEY 16 The Adventures of Wireless Woman Partner, Hackney Communications Did YOU KNow? ASSOCIATE EDITORS: Shift from NiCad to Lithium Polymer Recharges the Battery Industry Kristin Kirkham 17 Marketing & Technical Writer, BearCom WirELEss LIFEstYLE (Mt. Everest Expedition): EliZabeth Wiseman 18 Climbers Depend on Mobile Devices at the Top of the World Marketing Coordinator, BearCom SUccEss StorY (Spring ISD): CREATIVE DiREctOR: 23 Implementing Better Communications for a School District RANDY MOTT Principal, Mott Graphics Incorporated CALENdar: CONTRIBUTORS: 24 Upcoming Wireless Industry Events BRENT BISNAR AroUND THE world: Executive Vice President, BearCom 25 Wireless News and Views JOHN CZAPKO Vice President of Sales, BearCom THE BEARWirE: What’s Happening at BearCom IAN TOROK 27 Technical Services Director, BearCom FiNAL Word: MIKE BUTLER Global Demand for Wireless Technology Benefits Us All Engineering Manager, BearCom 28 HUGH JOHNSTON © 2007 BearCom. -

Practical Guidelines for Constructing Accurate Acoustical Spaces Including Advice on the Proper Materials to Use
Auralex® Acoustics, Inc. Practical Guidelines For Constructing Accurate Acoustical Spaces Including Advice On The Proper Materials To Use by Eric T. Smith Edited by Jeff D. Szymanski, PE July 2004 Version 3.0 Published & © Copyright 1993, 2004 by Auralex® Acoustics, Inc. 6853 Hillsdale Court, Indianapolis IN USA 46250-2039 • www.auralex.com FOREWORD.........................................................................................................................................4 WELCOME........................................................................................................................................4 CHAPTER 1..........................................................................................................................................6 BASICS OF ACOUSTICS.................................................................................................................6 ACOUSTICAL DEFINITIONS ...........................................................................................................7 Acoustics 101 Definitions ...........................................................................................................7 GENERAL TECHNICAL INFORMATION.........................................................................................9 STC................................................................................................................................................9 Absorption Coefficients and NRC ............................................................................................12