Unicenter CA-Insight Performance Monitor for DB2 for Z/OS and OS/390 Concepts and Facilities
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Z/OS ISPF Services Guide COMMAND NAME
z/OS 2.4 ISPF Services Guide IBM SC19-3626-40 Note Before using this information and the product it supports, read the information in “Notices” on page 399. This edition applies to Version 2 Release 4 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2021-06-22 © Copyright International Business Machines Corporation 1980, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................ xv Tables................................................................................................................xvii Preface...............................................................................................................xix Who should use this document?............................................................................................................... xix What is in this document?......................................................................................................................... xix How to read the syntax diagrams..............................................................................................................xix z/OS information...............................................................................................xxiii How to send your comments to IBM................................................................... -

TSO/E Programming Guide
z/OS Version 2 Release 3 TSO/E Programming Guide IBM SA32-0981-30 Note Before using this information and the product it supports, read the information in “Notices” on page 137. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-02-16 © Copyright International Business Machines Corporation 1988, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures....................................................................................................... ix List of Tables........................................................................................................ xi About this document...........................................................................................xiii Who should use this document.................................................................................................................xiii How this document is organized............................................................................................................... xiii How to use this document.........................................................................................................................xiii Where to find more information................................................................................................................ xiii How to send your comments to IBM......................................................................xv -
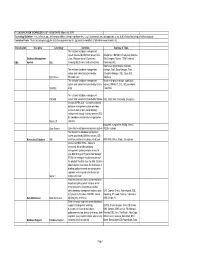
TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: a Set of Knowledge, Skills And/Or Abilities, Taking a Significant Time (E.G
IT CLASSIFICATION TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: A set of knowledge, skills and/or abilities, taking a significant time (e.g. 6 months) to learn, and applicable to the defined classification specification assigned. Example of Tools: These are examples only for illustration purposes and are not meant to constitute a full and/or comprehensive list. Classification Discipline Technology Definition Example of Tools The relational database management system provided by IBM that runs on Unix, Omegamon, IBM Admin Tools, Log Analyzer, Database Management Linux, Windows and z/OS platforms DB2 Compare, Nsynch, TSM, Universal DBA System DB2 including DB2 Connect and related tools Command, SQL SQL Server Mgmt Studio, Red Gate, The relational database management Vantage, Tivoli, Snap Manager, Toad, system and related tools provided by Enterprise Manager, SQL, Azure SQL SQL Server Microsoft Corp Database The relational database management Oracle enterprise manager, application system and related tools provided by Oracle express, RMAN, PL SQL, SQL developer, ORACLE Corp Toad, SQL The relational database management SYBASE system and related tools provided by Sybase ASE, OEM, RAC, Partioning, Encryption Cincom SUPRA SQL – Cincom's relational database management system provides access to data in open and proprietary environments through industry-standard SQL for standalone and client/server application Supra 2.X solutions. phpadmin, mysqladmin, MySql, Vertica, Open Source Open Source database management system SQLite, Hadoop The hierarchical database management system provided by IBM that runs on z/OS Hierarchical Database IMS mainframe platform including related tools BMC IMS Utilities, Strobe, Omegamon Cincom SUPRA® PDM – Cincom's networked, hierarchical database management system provides access to your data through a Physical Data Manager (PDM) that manages the data structures of the physical files that store the data. -

Computer Performance Evaluation Users Group (CPEUG)
COMPUTER SCIENCE & TECHNOLOGY: National Bureau of Standards Library, E-01 Admin. Bidg. OCT 1 1981 19105^1 QC / 00 COMPUTER PERFORMANCE EVALUATION USERS GROUP CPEUG 13th Meeting NBS Special Publication 500-18 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards 3-18 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following -

Resource Measurement Facility User's Guide
z/OS Version 2 Release 3 Resource Measurement Facility User's Guide IBM SC34-2664-30 Note Before using this information and the product it supports, read the information in “Notices” on page 381. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-02-16 © Copyright International Business Machines Corporation 1990, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures..................................................................................................... xiii List of Tables........................................................................................................xv About this document.......................................................................................... xvii Who should use this document................................................................................................................xvii How this document is organized.............................................................................................................. xvii z/OS information...................................................................................................................................... xviii How to read syntax diagrams.................................................................................................................. xviii Symbols................................................................................................................................................xix -

System Automation for Z/OS: User S Guide
System Automation for z/OS IBM User’s Guide Version 3 Release 5 SC34-2718-00 System Automation for z/OS IBM User’s Guide Version 3 Release 5 SC34-2718-00 Note Before using this information and the product it supports, be sure to read the general information under Appendix E, “Notices,” on page 263. Editions This edition applies to IBM Tivoli System Automation for z/OS (Program Number 5698-SA3) Version 3 Release 5, an IBM licensed program, and to all subsequent releases and modifications until otherwise indicated in new editions or technical newsletters. This edition replaces SC34-2647-00. © Copyright IBM Corporation 1996, 2014. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures .............. vii | Operating Groups ........... 29 | Moving MOVE Groups ......... 29 Tables ............... ix Controlling Application Move and Server Management .............. 29 Move Functions ............ 29 Accessibility ............ xi Controlling Application Move with Preference Using assistive technologies ......... xi Values ............... 31 Keyboard navigation of the user interface .... xi SA z/OS Automation Flags ......... 40 Automation Agent Flags ......... 40 Dotted decimal syntax diagrams ... xiii The Automation Manager Global Automation Flag ................ 42 How to send your comments to IBM .. xv Setting Automation Flags ......... 43 Relationship Between Automation Flags and About this publication ....... xvii Resource Status ............ 43 Automation Flags and Minor Resource Flags .. 44 Who Should Use This Publication ...... xvii Statuses Supplied by the Automation Manager .. 44 Where to Find More Information....... xvii Observed Status ............ 46 The System Automation for z/OS Library... xvii Automation Status ........... 47 Related Product Information ....... xviii Desired Status ............ 48 Related Online Information ....... -

ISPF User's Guide Volume I
z/OS Version 2 Release 3 ISPF User's Guide Volume I IBM SC19-3627-30 Note Before using this information and the product it supports, read the information in “Notices” on page 213. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-06-21 © Copyright International Business Machines Corporation 1980, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. xi Tables..................................................................................................................xv Preface..............................................................................................................xvii About this document................................................................................................................................ xvii Who should use this document................................................................................................................xvii What is in this document?........................................................................................................................ xvii How to read the syntax diagrams............................................................................................................xviii z/OS information...............................................................................................xxiii -
Mainframe Talent Drain Our Recent Survey Shows Mainframes Are Here to Stay
2020 Mainframe Market Pulse survey | A commissioned study conducted by Forrester Consulting on behalf of Deloitte Mainframe talent drain Our recent survey shows mainframes are here to stay. Will IT organizations have the talent they need to deliver on hybrid strategies? Think mainframes are on their way out? Think again. But the workforce with the skills to support these Deloitte’s 2020 Mainframe Market Pulse survey tells an systems is aging out—and the pipeline to fill these alternative story. Business and IT leaders show plenty of roles is diminishing. How are business and IT leaders interest in mainframes—especially in upgrading legacy addressing this talent gap to support their mainframe environments as the foundation for hybrid strategies in needs as they move into the future? data and transaction-heavy industries. Here’s what 261 business and IT leaders revealed about the talent gap and how they’re attempting to mitigate it. These survey insights offer a window into their thinking, and can be useful in guiding your talent, investment, and IT strategies. Skill set slow-down Rising reliance on mainframes 91% OF RESPONDENTS You should skill up your talent pool identifiedEXPANDING their to support strategic IT investments. mainframe footprints as a moderate or critical priority over the next year. Reduced access to mainframe talent BUT 79% cited their top 71% said their mainframe team mainframe-related challenge is is understaffed acquiring the right resources and skills to get work done. and 54% noted their mainframe team is underfunded “The aging population of mainframe employees is a concern for long-term stability.” – Director of IT at a healthcare organization Where it hurts 93% said 59% said 56% said It’s moderately to extremely We have mainframe knowledge/ There are major talent gaps in challenging to acquire the right skills gaps among our own the workforce when it comes mainframe resources and skills. -

Ultrastar C15K600 SAS OEM Specification
Hard Disk Drive Specification Ultrastar C15K600 2.5” SAS Hard Disk Drive Models HUC156060CSS200 HUC156060CS4200 HUC156060CSS201 HUC156060CS4201 HUC156060CSS204 HUC156060CS4204 HUC156060CSS205 HUC156060CS4205 HUC156045CSS200 HUC156045CS4200 HUC156045CSS201 HUC156045CS4201 HUC156045CSS204 HUC156045CS4204 HUC156045CSS205 HUC156045CS4205 HUC156030CSS200 HUC156030CS4200 HUC156030CSS201 HUC156030CS4201 HUC156030CSS204 HUC156030CS4204 Version: 1.6 HUC156030CSS205 HUC156030CS4205 27 July 2016 HGST Ultrastar C15K600 Hard Disk Drive Specification 1 Revised Edition (Rev 1.6) (27 July 2016) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent with local law: HGST, A WESTERN DIGITAL COMPANY, PROVIDES THIS PUBLICATION "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer or express or implied warranties in certain transactions, therefore, this statement may not apply to you. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. HGST may make improvements or changes in any products or programs described in this publication at any time. It is possible that this publication may contain reference to, or information about, HGST products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that HGST intends to announce such HGST products, programming, or services in your country. Technical information about this product is available by contacting your local HGST representative or on the Internet at http://www.hgst.com HGST may have patents or pending patent applications covering subject matter in this document. -

ISPF Services Guide
z/OS Version 2 Release 3 ISPF Services Guide IBM SC19-3626-30 Note Before using this information and the product it supports, read the information in “Notices” on page 395. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-06-21 © Copyright International Business Machines Corporation 1980, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................ xv Tables................................................................................................................xvii Preface...............................................................................................................xix Who should use this document?............................................................................................................... xix What is in this document?......................................................................................................................... xix How to read the syntax diagrams..............................................................................................................xix z/OS information...............................................................................................xxiii How to send your comments to IBM................................................................... -

PGI Fortran Reference Copyright © 2005, Stmicroelectronics, Inc
PGI® Fortran Reference The Portland Group STMicroelectronics 9150 SW Pioneer Court, Suite H Wilsonville, OR 97070 www.pgroup.com While every precaution has been taken in the preparation of this document, The Portland Group™, a wholly-owned subsidiary of STMicroelectronics, makes no warranty for the use of its products and assumes no responsibility for any errors that may appear, or for damages resulting from the use of the information contained herein. STMicroelectronics retains the right to make changes to this information at any time, without notice. The software described in this document is distributed under license from STMicroelectronics and may be used or copied only in accordance with the terms of the license agreement. No part of this document may be reproduced or transmitted in any form or by any means, for any purpose other than the purchaser's personal use without the express written permission of STMicroelectronics. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this manual, STMicroelectronics was aware of a trademark claim. The designations have been printed in caps or initial caps. Thanks is given to the Parallel Tools Consortium and, in particular, to the High Performance Debugging Forum for their efforts. PGF90, PGF95, PGC++, Cluster Development Kit, CDK and The Portland Group are trademarks and PGI, PGHPF, PGF77, PGCC, PGPROF, and PGDBG are registered trademarks of STMicroelectronics, Inc. Other brands and names are the property of their respective owners. The use of STLport, a C++ Library, is licensed separately and license, distribution and copyright notice can be found in online documentation for a given release of the PGI compilers and tools. -

ISPF Dialog Developer's Guide and Reference
z/OS Version 2 Release 3 ISPF Dialog Developer's Guide and Reference IBM SC19-3619-30 Note Before using this information and the product it supports, read the information in “Notices” on page 403. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-06-21 © Copyright International Business Machines Corporation 1980, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. ix Tables................................................................................................................ xiii Preface................................................................................................................xv About this document.................................................................................................................................. xv Who should use this document..................................................................................................................xv What is in this document?.......................................................................................................................... xv How to read the syntax diagrams..............................................................................................................xvi z/OS information.................................................................................................xxi