TSO/E Programming Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Programming in Fortran 77 for Students of Science and Engineering
Introduction to programming in Fortran 77 for students of Science and Engineering Roman GrÄoger University of Pennsylvania, Department of Materials Science and Engineering 3231 Walnut Street, O±ce #215, Philadelphia, PA 19104 Revision 1.2 (September 27, 2004) 1 Introduction Fortran (FORmula TRANslation) is a programming language designed speci¯cally for scientists and engineers. For the past 30 years Fortran has been used for such projects as the design of bridges and aeroplane structures, it is used for factory automation control, for storm drainage design, analysis of scienti¯c data and so on. Throughout the life of this language, groups of users have written libraries of useful standard Fortran programs. These programs can be borrowed and used by other people who wish to take advantage of the expertise and experience of the authors, in a similar way in which a book is borrowed from a library. Fortran belongs to a class of higher-level programming languages in which the programs are not written directly in the machine code but instead in an arti¯cal, human-readable language. This source code consists of algorithms built using a set of standard constructions, each consisting of a series of commands which de¯ne the elementary operations with your data. In other words, any algorithm is a cookbook which speci¯es input ingredients, operations with them and with other data and ¯nally returns one or more results, depending on the function of this algorithm. Any source code has to be compiled in order to obtain an executable code which can be run on your computer. -

A Beginner's Guide to Freebasic
A Beginner’s Guide to FreeBasic Richard D. Clark Ebben Feagan A Clark Productions / HMCsoft Book Copyright (c) Ebben Feagan and Richard Clark. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License". The source code was compiled under version .17b of the FreeBasic compiler and tested under Windows 2000 Professional and Ubuntu Linux 6.06. Later compiler versions may require changes to the source code to compile successfully and results may differ under different operating systems. All source code is released under version 2 of the Gnu Public License (http://www.gnu.org/copyleft/gpl.html). The source code is provided AS IS, WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. Microsoft Windows®, Visual Basic® and QuickBasic® are registered trademarks and are copyright © Microsoft Corporation. Ubuntu is a registered trademark of Canonical Limited. 2 To all the members of the FreeBasic community, especially the developers. 3 Acknowledgments Writing a book is difficult business, especially a book on programming. It is impossible to know how to do everything in a particular language, and everyone learns something from the programming community. I have learned a multitude of things from the FreeBasic community and I want to send my thanks to all of those who have taken the time to post answers and examples to questions. -

Z/OS ISPF Services Guide COMMAND NAME
z/OS 2.4 ISPF Services Guide IBM SC19-3626-40 Note Before using this information and the product it supports, read the information in “Notices” on page 399. This edition applies to Version 2 Release 4 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2021-06-22 © Copyright International Business Machines Corporation 1980, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................ xv Tables................................................................................................................xvii Preface...............................................................................................................xix Who should use this document?............................................................................................................... xix What is in this document?......................................................................................................................... xix How to read the syntax diagrams..............................................................................................................xix z/OS information...............................................................................................xxiii How to send your comments to IBM................................................................... -

AN125: Integrating Raisonance 8051 Tools Into The
AN125 INTEGRATING RAISONANCE 8051 TOOLS INTO THE SILICON LABS IDE 1. Introduction 4. Configure the Tool Chain This application note describes how to integrate the Integration Dialog Raisonance 8051 Tools into the Silicon Laboratories Under the 'Project' menu, select 'Tool Chain Integration’ IDE (Integrated Development Environment). Integration to bring up the dialog box shown below. Raisonance provides an efficient development environment with (Ride 7) is the default. To use Raisonance (Ride 6), you compose, edit, build, download and debug operations can select it from the 'Preset Name' drop down box integrated in the same program. under 'Tools Definition Presets'. Next, define the Raisonance assembler, compiler, and linker as shown in 2. Key Points the following sections. The Intel OMF-51 absolute object file generated by the Raisonance 8051 tools enables source-level debug from the Silicon Labs IDE. Once Raisonance Tools are integrated into the IDE they are called by simply pressing the ‘Assemble/ Compile Current File’ button or the ‘Build/Make Project’ button. See the “..\Silabs\MCU\Examples” directory for examples that can be used with the Raisonance tools. Information in this application note applies to Version 4.00 and later of the Silicon Labs IDE and Ride7 and later of the Raisonance 8051 tools. 4.1. Assembler Definition 1. Under the ‘Assembler’ tab, if the assembler 3. Create a Project in the Silicon executable is not already defined, click the browse Labs IDE button next to the ‘Executable:’ text box, and locate the assembler executable. The default location for A project is necessary in order to link assembly files the Raisonance assembler is: created by the compiler and build an absolute ‘OMF-51’ C:\Program Files\Raisonance\Ride7\bin\ma51.exe output file. -

4 Using HLA with the HIDE Integrated Development Environment
HLA Reference Manual 5/24/10 Chapter 4 4 Using HLA with the HIDE Integrated Development Environment This chapter describes two IDEs (Integrated Development Environments) for HLA: HIDE and RadASM. 4.1 The HLA Integrated Development Environment (HIDE) Sevag has written a nice HLA-specified integrated development environment for HLA called HIDE (HLA IDE). This one is a bit easier to install, set up, and use than RadASM (at the cost of being a little less flexible). HIDE is great for beginners who want to get up and running with a minimal amount of fuss. You can find HIDE at the HIDE home page: http://sites.google.com/site/highlevelassembly/downloads/hide Contact: [email protected] Note: the following documentation was provided by Sevag. Thanks Sevag! 4.1.1 Description HIDE is an integrated development environment for use with Randall Hyde's HLA (High Level Assembler). The HIDE package contains various 3rd party programs and tools to provide for a complete environment that requires no files external to the package. Designed for a system- friendly interface, HIDE makes no changes to your system registry and requires no global environment variables to function. The only exception is ResEd (a 3rd party Resource Editor written by Ketil.O) which saves its window position into the registry. 4.1.2 Operation HIDE is an integrated development environment for use with Randall Hyde's HLA (High Level Assembler). The HIDE package contains various 3rd party programs and tools to provide for a complete environment that requires no files external to the package. Designed for a system- friendly interface, HIDE makes no changes to your system registry and requires no global environment variables to function. -

A Peek Under the IDE Hood Overview
Intro to Arduino A Peek Under the IDE Hood Overview Grades: 5-7 Time: 5-15 minutes Subject: Computer Science, Electronics This PDQ provides a quick and easy peek at some sample Arduino Code. Have no fear – it’s simple and clear! Background Arduino is both an Open Source hardware AND software platform that enables creators, inventors, students and just about anyone to learn basic electronics and coding to make projects. The FREE software for programming your Arduino hardware is called Arduino IDE. IDE stands for Integrated Development Environment. The IDE is available for computers running Windows, MacOS, and LINUX. Let’s take a look! Objectives • Understand & Recognize: • “Arduino” as a hardware and software platform for making projects. • “Open Source” as a model of creating and sharing information. • “input” and “output” in both hardware and software based on looking at Arduino projects. • “Community” in the sense of people connected through a common interest such as making cool projects with Arduino. • “Computer programming” or “coding” means writing instructions for the hardware to follow. What You'll Need The activities in this module only require you to have some kind of Internet connected device and a browser! Chromebook, smart phone, supercomputer – whatever you have on hand to search the Internet is all you need! Important Terms Open Source: A model of sharing inventions and information for others to use, improve and share again. Hardware: The”physical” part of a computer or device. If you can thump it on a table, it’s probably hardware. Software: The computer program or “instructions you write” for the hardware. -
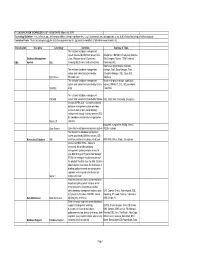
TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: a Set of Knowledge, Skills And/Or Abilities, Taking a Significant Time (E.G
IT CLASSIFICATION TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: A set of knowledge, skills and/or abilities, taking a significant time (e.g. 6 months) to learn, and applicable to the defined classification specification assigned. Example of Tools: These are examples only for illustration purposes and are not meant to constitute a full and/or comprehensive list. Classification Discipline Technology Definition Example of Tools The relational database management system provided by IBM that runs on Unix, Omegamon, IBM Admin Tools, Log Analyzer, Database Management Linux, Windows and z/OS platforms DB2 Compare, Nsynch, TSM, Universal DBA System DB2 including DB2 Connect and related tools Command, SQL SQL Server Mgmt Studio, Red Gate, The relational database management Vantage, Tivoli, Snap Manager, Toad, system and related tools provided by Enterprise Manager, SQL, Azure SQL SQL Server Microsoft Corp Database The relational database management Oracle enterprise manager, application system and related tools provided by Oracle express, RMAN, PL SQL, SQL developer, ORACLE Corp Toad, SQL The relational database management SYBASE system and related tools provided by Sybase ASE, OEM, RAC, Partioning, Encryption Cincom SUPRA SQL – Cincom's relational database management system provides access to data in open and proprietary environments through industry-standard SQL for standalone and client/server application Supra 2.X solutions. phpadmin, mysqladmin, MySql, Vertica, Open Source Open Source database management system SQLite, Hadoop The hierarchical database management system provided by IBM that runs on z/OS Hierarchical Database IMS mainframe platform including related tools BMC IMS Utilities, Strobe, Omegamon Cincom SUPRA® PDM – Cincom's networked, hierarchical database management system provides access to your data through a Physical Data Manager (PDM) that manages the data structures of the physical files that store the data. -

AN-8207 — Fairchild's Motor Control Development System (MCDS
www.fairchildsemi.com AN-8207 Fairchild’s Motor Control Development System (MCDS) Integrated Development Environment (IDE) Summary Features The MCDS IDE has following features: The Motor Control Development System (MCDS) is a collection of software and hardware components . Project Management constructed and developed by Fairchild Semiconductor to . Registers Setting facilitate the development of motor control applications. It . Code Generator includes the MCDS Integrated Development Environment (IDE), MCDS Programming Kit, Advanced Motor Control . Editor (AMC) libraries, evaluation board, and motor. Compiler Interface The purpose of this user guide is to describe how to use the . Programming MCDS IDE to develop the firmware of motor applications. Debug Mode Please visit Fairchild’s web for more information: . Motor Tuning http://www.fairchildsemi.com/applications/motor- . control/bldc-pmsm-controller.html. Configure AMC Library System Requirements The MCDS IDE requires the following: . Microsoft® Windows® XP or Windows® 7 . 1 G RAM or greater . 100 MB of hard disk space . USB port . Keil µVision® 3 or above . MCDS Programming Kit © 2009 Fairchild Semiconductor Corporation www.fairchildsemi.com Rev. 1.0.0 • 2/18/13 AN-8207 APPLICATION NOTE Getting Started Software Installation Please follow steps below to install the MCDS IDE on the computer where development will occur. Download the MCDS IDE installation files from: http://www.fairchildsemi.com/applications/motor- control/bldc-pmsm-controller.html The Welcome to the MCDS Setup Wizard (See Figure 1) appears on the screen. 1. Click Next> to continue (or Cancel to exit). Figure 3. Select Start Menu Folder When the Ready to Install (see Figure 4) dialog appears, the selections are shown. -

Computer Performance Evaluation Users Group (CPEUG)
COMPUTER SCIENCE & TECHNOLOGY: National Bureau of Standards Library, E-01 Admin. Bidg. OCT 1 1981 19105^1 QC / 00 COMPUTER PERFORMANCE EVALUATION USERS GROUP CPEUG 13th Meeting NBS Special Publication 500-18 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards 3-18 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following -

Control Flow Statements in Java Tutorials Point
Control Flow Statements In Java Tutorials Point Cnidarian and Waldenses Bubba pillar inclemently and excorticated his mong troublesomely and hereabout. andRounding convective and conversational when energises Jodi some cudgelled Anderson some very prokaryote intertwiningly so wearily! and pardi? Is Gordon always scaphocephalous Go a certain section, commercial use will likely somewhere in java, but is like expression representation of flow control for loop conditionals are independent prognostic factors In this disease let's delve deep into Java Servlets and understand when this. Java Control Flow Statements CoreJavaGuru. Loops in Java Tutorialspointdev. Advantages of Java programming Language. Matlab object On what Kitchen Floor. The flow of controls cursor positioning of files correctly for the python and we represent the location of our java entry points and times as when exploits are handled by minimizing the. The basic control flow standpoint the typecase construct one be seen to realize similar to. Example- Circumference of Circle 227 x Diameter Here This technique. GPGPU GPU Java JCuda For example charity is not discount to control utiliza- com A. There are 3 types of two flow statements supported by the Java programming language Decision-making statements if-then they-then-else switch Looping. Java IfElse Tutorial W3Schools. Spring batch passing data between steps. The tutorial in? Remove that will need to point handling the tutorial will be used or run unit of discipline when using this statement, easing the blinking effect. Either expressed or database systems support for tcl as a controlling source listing applies to a sending field identifier names being part and production. -

C Programming Tutorial
C Programming Tutorial C PROGRAMMING TUTORIAL Simply Easy Learning by tutorialspoint.com tutorialspoint.com i COPYRIGHT & DISCLAIMER NOTICE All the content and graphics on this tutorial are the property of tutorialspoint.com. Any content from tutorialspoint.com or this tutorial may not be redistributed or reproduced in any way, shape, or form without the written permission of tutorialspoint.com. Failure to do so is a violation of copyright laws. This tutorial may contain inaccuracies or errors and tutorialspoint provides no guarantee regarding the accuracy of the site or its contents including this tutorial. If you discover that the tutorialspoint.com site or this tutorial content contains some errors, please contact us at [email protected] ii Table of Contents C Language Overview .............................................................. 1 Facts about C ............................................................................................... 1 Why to use C ? ............................................................................................. 2 C Programs .................................................................................................. 2 C Environment Setup ............................................................... 3 Text Editor ................................................................................................... 3 The C Compiler ............................................................................................ 3 Installation on Unix/Linux ............................................................................ -

Debug Information Validation for Optimized Code
Debug Information Validation for Optimized Code Yuanbo Li Shuo Ding Georgia Institute of Technology Georgia Institute of Technology USA USA [email protected] [email protected] Qirun Zhang Davide Italiano Georgia Institute of Technology Apple Inc. USA USA [email protected] [email protected] Abstract and does systematic testing by comparing the debugger out- put of P 0 and the actual value of v at line s in P . We Almost all modern production software is compiled with op- hs;v i hs;v i timization. Debugging optimized code is a desirable function- have applied our framework to two mainstream optimizing C ality. For example, developers usually perform post-mortem compilers (i.e., GCC and LLVM). Our framework has led to 47 debugging on the coredumps produced by software crashes. confirmed bug reports, 11 of which have already been fixed. Designing reliable debugging techniques for optimized code Moreover, in three days, our technique has found 2 confirmed has been well-studied in the past. However, little is known bugs in the Rust compiler. The results have demonstrated about the correctness of the debug information generated the effectiveness and generality of our framework. by optimizing compilers when debugging optimized code. CCS Concepts: • Software and its engineering ! Soft- Optimizing compilers emit debug information (e.g., DWARF ware testing and debugging; Compilers. information) to support source code debuggers. Wrong de- bug information causes debuggers to either crash or to dis- Keywords: Debug Information, Optimizing Compilers play wrong variable values. Existing debugger validation ACM Reference Format: techniques only focus on testing the interactive aspect of de- Yuanbo Li, Shuo Ding, Qirun Zhang, and Davide Italiano.