IBM Tivoli Netview for Z/OS: Programming: REXX and The
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Z/OS ISPF Services Guide COMMAND NAME
z/OS 2.4 ISPF Services Guide IBM SC19-3626-40 Note Before using this information and the product it supports, read the information in “Notices” on page 399. This edition applies to Version 2 Release 4 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2021-06-22 © Copyright International Business Machines Corporation 1980, 2021. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................ xv Tables................................................................................................................xvii Preface...............................................................................................................xix Who should use this document?............................................................................................................... xix What is in this document?......................................................................................................................... xix How to read the syntax diagrams..............................................................................................................xix z/OS information...............................................................................................xxiii How to send your comments to IBM................................................................... -

TSO/E Programming Guide
z/OS Version 2 Release 3 TSO/E Programming Guide IBM SA32-0981-30 Note Before using this information and the product it supports, read the information in “Notices” on page 137. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-02-16 © Copyright International Business Machines Corporation 1988, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures....................................................................................................... ix List of Tables........................................................................................................ xi About this document...........................................................................................xiii Who should use this document.................................................................................................................xiii How this document is organized............................................................................................................... xiii How to use this document.........................................................................................................................xiii Where to find more information................................................................................................................ xiii How to send your comments to IBM......................................................................xv -

Introduction to Tivoli Enterprise Data Warehouse
Front cover Introduction to Tivoli Enterprise Data Warehouse Insider’s guide to Tivoli Enterpise Data Warehouse Best practices for creating data marts Integration with all major OLAP tools Vasfi Gucer William Crane Chris Molloy Sven Schubert Roger Walker ibm.com/redbooks International Technical Support Organization Introduction to Tivoli Enterprise Data Warehouse May 2002 SG24-6607-00 Take Note! Before using this information and the product it supports, be sure to read the general information in “Notices” on page xvii. First Edition (May 2002) This edition applies to Tivoli Enterprise Data Warehouse Version 1.1. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. JN9B Building 003 Internal Zip 2834 11400 Burnet Road Austin, Texas 78758-3493 When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. © Copyright International Business Machines Corporation 2002. All rights reserved. Note to U.S Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Figures . .ix Tables . xv Notices . xvii Trademarks . xviii Preface . xix The team that wrote this redbook. xx Notice . xxi Comments welcome. xxii Chapter 1. Introducing building blocks. 1 1.1 Business Intelligence. 2 1.2 Business driving forces . 2 1.3 Main Business Intelligence terms . 3 1.3.1 Operational databases . 4 1.3.2 Online transaction processing (OLTP) . 4 1.3.3 Data warehouse . 5 1.3.4 Data mart . -

IBM Tivoli Endpoint Manager for Patch Management Continuous Patch Compliance Visibility and Enforcement
IBM Software Data Sheet Tivoli IBM Tivoli Endpoint Manager for Patch Management Continuous patch compliance visibility and enforcement With software and the threats against that software constantly evolving, Highlights organizations need an effective way to assess, deploy and manage a con- stant flow of patches for the myriad operating systems and applications in ● Automatically manage patches for multi- their heterogeneous environments. For system administrators responsible ple operating systems and applications across hundreds of thousands of end- for potentially tens or hundreds of thousands of endpoints running vari- points regardless of location, connection ous operating systems and software applications, patch management type or status can easily overwhelm already strained budgets and staff. IBM Tivoli® ● Reduce security and compliance risk by Endpoint Manager for Patch Management balances the need for fast slashing remediation cycles from weeks deployment and high availability with an automated, simplified patching to days or hours process that is administered from a single console. ● Gain greater visibility into patch compli- ance with flexible, real-time monitoring Tivoli Endpoint Manager for Patch Management, built on BigFix® and reporting technology, gives organizations access to comprehensive capabilities ● Provide up-to-date visibility and control for delivering patches for Microsoft® Windows®, UNIX®, Linux® and from a single management console Mac operating systems, third-party applications from vendors including Adobe®, Mozilla, Apple and Java™, and customer-supplied patches to endpoints—regardless of their location, connection type or status. Endpoints can include servers, laptops, desktops, and specialized equip- ment such as point-of-sale (POS) devices, ATMs, and self-service kiosks. Apply only the correct patches to the correct endpoint One approach to patch management is to create large patch files with a large update “payload” and distribute them to all of the endpoints, regardless of whether they already have all of the patches or not. -
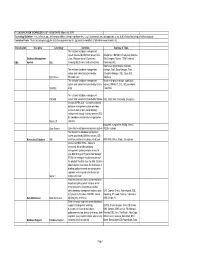
TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: a Set of Knowledge, Skills And/Or Abilities, Taking a Significant Time (E.G
IT CLASSIFICATION TECHNOLOGY LIST - ISSUE DATE: March 18, 2019 Technology Definition: A set of knowledge, skills and/or abilities, taking a significant time (e.g. 6 months) to learn, and applicable to the defined classification specification assigned. Example of Tools: These are examples only for illustration purposes and are not meant to constitute a full and/or comprehensive list. Classification Discipline Technology Definition Example of Tools The relational database management system provided by IBM that runs on Unix, Omegamon, IBM Admin Tools, Log Analyzer, Database Management Linux, Windows and z/OS platforms DB2 Compare, Nsynch, TSM, Universal DBA System DB2 including DB2 Connect and related tools Command, SQL SQL Server Mgmt Studio, Red Gate, The relational database management Vantage, Tivoli, Snap Manager, Toad, system and related tools provided by Enterprise Manager, SQL, Azure SQL SQL Server Microsoft Corp Database The relational database management Oracle enterprise manager, application system and related tools provided by Oracle express, RMAN, PL SQL, SQL developer, ORACLE Corp Toad, SQL The relational database management SYBASE system and related tools provided by Sybase ASE, OEM, RAC, Partioning, Encryption Cincom SUPRA SQL – Cincom's relational database management system provides access to data in open and proprietary environments through industry-standard SQL for standalone and client/server application Supra 2.X solutions. phpadmin, mysqladmin, MySql, Vertica, Open Source Open Source database management system SQLite, Hadoop The hierarchical database management system provided by IBM that runs on z/OS Hierarchical Database IMS mainframe platform including related tools BMC IMS Utilities, Strobe, Omegamon Cincom SUPRA® PDM – Cincom's networked, hierarchical database management system provides access to your data through a Physical Data Manager (PDM) that manages the data structures of the physical files that store the data. -

Computer Performance Evaluation Users Group (CPEUG)
COMPUTER SCIENCE & TECHNOLOGY: National Bureau of Standards Library, E-01 Admin. Bidg. OCT 1 1981 19105^1 QC / 00 COMPUTER PERFORMANCE EVALUATION USERS GROUP CPEUG 13th Meeting NBS Special Publication 500-18 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards 3-18 NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following -

Tivoli Monitoring for Microsoft Applications V6.1.1
IBM United States Announcement 208-122, dated May 20, 2008 Tivoli Monitoring for Microsoft Applications V6.1.1 Ordering information ..................................7 Overview Terms and conditions ................................ 9 IBM Electronic Services ...........................10 The IBM Tivoli® Monitoring for Microsoft® Applications Entry V6.1.1 Prices .......................................................10 offering provides a limited use entitlement for the Windows® operating system agent in IBM Tivoli Monitoring for Microsoft Applications. IBM Tivoli Monitoring for Microsoft Applications Advanced V6.1.1 is a Microsoft system and application monitoring tool that provides the capabilities to comprehensively monitor, alert, and report on the availability of Microsoft applications and the environment they run on. For additional information, refer to Software Announcement 208-065, dated March 25, 2008. Planned availability date • May 23, 2008: Electronic software delivery • May 23, 2008: Media and documentation IBM United States Announcement 208-122 IBM is a registered trademark of International Business Machines Corporation 1 IBM Tivoli Enhanced Value-Based Pricing terminology IBM Tivoli® Enhanced Value-Based Pricing: IBM Tivoli software products are priced using IBM Tivoli's Enhanced Value-Based Pricing. The Enhanced Value-Based Pricing system is based upon the IBM Tivoli Environment-Managed Licensing Model, which uses a managed-environment approach — whereby price is determined by what is managed rather than the number and type -

Monitoring: Become More Proactive Through Effective Historical Analysis
1 IBM Software Group | Tivoli Software Monitoring: Become More Proactive Through Effective Historical Analysis Ed Woods Session 9633 Consulting IT Specialist Tuesday, August 9 th IBM Corporation 1:30-2:30 PM © 2011 IBM Corporation IBM Software Group | Tivoli Software Agenda How can you use history to improve your real-time monitoring strategy? Are you getting the most from your investment in monitoring and management solutions? How can you leverage history to improve your overall performance and availability? What are the most effective ways to use history to solve common problems? What are the optimal ways to collect historical information? How can you use history to become more proactive with real-time monitoring and management? Become More Proactive Through Effective Historical Analysis © 2011 IBM Corporation 2 IBM Software Group | Tivoli Software The Importance Of History Data Why History Can Be Essential To Your Overall Strategy Not all problems or events can be seen and analyzed in real time – Inevitably some analysis will need to be done after the fact using such functions as Near Term History, snapshot history, or report analysis History provides an understanding of what happened in the past – History of application performance and response time – CICS/IMS response time, DB2 thread activity, z/OS batch activity – History of resource utilization and resource issues – DASD, memory/paging, CPU, pools – History of alerts and issues – What alerts fired and how often History can be used to help visualize what may happen in the -

Resource Measurement Facility User's Guide
z/OS Version 2 Release 3 Resource Measurement Facility User's Guide IBM SC34-2664-30 Note Before using this information and the product it supports, read the information in “Notices” on page 381. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-02-16 © Copyright International Business Machines Corporation 1990, 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures..................................................................................................... xiii List of Tables........................................................................................................xv About this document.......................................................................................... xvii Who should use this document................................................................................................................xvii How this document is organized.............................................................................................................. xvii z/OS information...................................................................................................................................... xviii How to read syntax diagrams.................................................................................................................. xviii Symbols................................................................................................................................................xix -

IBM Tivoli Monitoring: Implementation and Performance Optimization for Large Scale Environments
Front cover IBM Tivoli Monitoring: Implementation and Performance Optimization for Large Scale Environments Best practices - large scale deployment of IBM Tivoli Monitoring V6.1 and V6.2 Performance, scalability and high availability considerations Includes CCMDB integration Vasfi Gucer Naeem Altaf Erik D Anderson Dirk-Gary Boldt Murtuza Choilawala Isabel Escobar Scott A Godfrey Mauricio Morilha Sokal Christopher Walker ibm.com/redbooks International Technical Support Organization IBM Tivoli Monitoring: Implementation and Performance Optimization for Large Scale Environments February 2008 SG24-7443-00 Note: Before using this information and the product it supports, read the information in “Notices” on page xi. First Edition (February 2008) This edition applies to IBM Tivoli Monitoring Version 6.1.0 and Version 6.2.0, IBM Tivoli OMEGAMON XE Version 4.1.0. © Copyright International Business Machines Corporation 2008. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . xi Trademarks . xii Preface . xv The team that wrote this book . xv Become a published author . xviii Comments welcome. xviii Chapter 1. Introduction to IBM Tivoli Monitoring V6.1. 1 1.1 IBM Tivoli at a glance . 2 1.2 IBM Service Management . 2 1.2.1 IBM Process Management products . 4 1.2.2 IBM Operational Management products . 4 1.2.3 IBM Service Management platform. 5 1.3 Enterprise management challenges . 5 1.3.1 Business driving forces . 6 1.4 IBM Tivoli Monitoring solutions . 7 1.5 IBM Tivoli Monitoring V6.1 components . 9 1.5.1 Tivoli Enterprise Monitoring Server (monitoring server) . -

System Automation for Z/OS: User S Guide
System Automation for z/OS IBM User’s Guide Version 3 Release 5 SC34-2718-00 System Automation for z/OS IBM User’s Guide Version 3 Release 5 SC34-2718-00 Note Before using this information and the product it supports, be sure to read the general information under Appendix E, “Notices,” on page 263. Editions This edition applies to IBM Tivoli System Automation for z/OS (Program Number 5698-SA3) Version 3 Release 5, an IBM licensed program, and to all subsequent releases and modifications until otherwise indicated in new editions or technical newsletters. This edition replaces SC34-2647-00. © Copyright IBM Corporation 1996, 2014. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures .............. vii | Operating Groups ........... 29 | Moving MOVE Groups ......... 29 Tables ............... ix Controlling Application Move and Server Management .............. 29 Move Functions ............ 29 Accessibility ............ xi Controlling Application Move with Preference Using assistive technologies ......... xi Values ............... 31 Keyboard navigation of the user interface .... xi SA z/OS Automation Flags ......... 40 Automation Agent Flags ......... 40 Dotted decimal syntax diagrams ... xiii The Automation Manager Global Automation Flag ................ 42 How to send your comments to IBM .. xv Setting Automation Flags ......... 43 Relationship Between Automation Flags and About this publication ....... xvii Resource Status ............ 43 Automation Flags and Minor Resource Flags .. 44 Who Should Use This Publication ...... xvii Statuses Supplied by the Automation Manager .. 44 Where to Find More Information....... xvii Observed Status ............ 46 The System Automation for z/OS Library... xvii Automation Status ........... 47 Related Product Information ....... xviii Desired Status ............ 48 Related Online Information ....... -

IBM Tivoli Configuration Manager for Automated Teller Machines: Release Notes Preface
IBM Tivoli Configuration Manager for Automated Teller Machines Release Notes Ve r s i o n 2 .1 SC32-1254-00 IBM Tivoli Configuration Manager for Automated Teller Machines Release Notes Ve r s i o n 2 .1 SC32-1254-00 Note Before using this information and the product it supports, read the information in “Notices” on page 9. First Edition (June 2003) This edition applies to Version 2, release 1, modification level 0 of IBM Tivoli Configuration Manager for Automated Teller Machines (program number 5724-E50) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2000, 2003. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Preface ...............v Compatibility ..............1 Publications ..............v IBM Tivoli Configuration Manager for Automated Chapter 2. Installation and upgrade Teller Machines ............v notes ................3 Prerequisite publications .........v Supported operating systems .........3 Related publications ..........vi Supported databases............4 Accessing publications online .......vii Component installation requirements ......4 Ordering publications ..........vii Hardware Requirements .........4 Contacting software support ........vii Software Requirements ..........5 Conventions used in this guide .......viii Installing and upgrading to IBM Tivoli Configuration Typeface conventions ..........viii Manager for