Camerashy CLOSING the APERTURE on CHINA’S UNIT 78020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
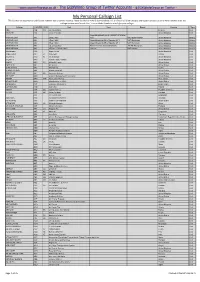
My Personal Callsign List This List Was Not Designed for Publication However Due to Several Requests I Have Decided to Make It Downloadable
- www.egxwinfogroup.co.uk - The EGXWinfo Group of Twitter Accounts - @EGXWinfoGroup on Twitter - My Personal Callsign List This list was not designed for publication however due to several requests I have decided to make it downloadable. It is a mixture of listed callsigns and logged callsigns so some have numbers after the callsign as they were heard. Use CTL+F in Adobe Reader to search for your callsign Callsign ICAO/PRI IATA Unit Type Based Country Type ABG AAB W9 Abelag Aviation Belgium Civil ARMYAIR AAC Army Air Corps United Kingdom Civil AgustaWestland Lynx AH.9A/AW159 Wildcat ARMYAIR 200# AAC 2Regt | AAC AH.1 AAC Middle Wallop United Kingdom Military ARMYAIR 300# AAC 3Regt | AAC AgustaWestland AH-64 Apache AH.1 RAF Wattisham United Kingdom Military ARMYAIR 400# AAC 4Regt | AAC AgustaWestland AH-64 Apache AH.1 RAF Wattisham United Kingdom Military ARMYAIR 500# AAC 5Regt AAC/RAF Britten-Norman Islander/Defender JHCFS Aldergrove United Kingdom Military ARMYAIR 600# AAC 657Sqn | JSFAW | AAC Various RAF Odiham United Kingdom Military Ambassador AAD Mann Air Ltd United Kingdom Civil AIGLE AZUR AAF ZI Aigle Azur France Civil ATLANTIC AAG KI Air Atlantique United Kingdom Civil ATLANTIC AAG Atlantic Flight Training United Kingdom Civil ALOHA AAH KH Aloha Air Cargo United States Civil BOREALIS AAI Air Aurora United States Civil ALFA SUDAN AAJ Alfa Airlines Sudan Civil ALASKA ISLAND AAK Alaska Island Air United States Civil AMERICAN AAL AA American Airlines United States Civil AM CORP AAM Aviation Management Corporation United States Civil -

深圳市华迅贸易有限公司 Shenzhen Huaxun Trading Co., Ltd
深圳市华迅贸易有限公司 Shenzhen Huaxun Trading Co., Ltd. 地址:深圳市福田区车公庙泰然九路海松大厦 A 座 1602 室 邮编:518040 电话:0755-23981008 传真:0755-82734068 Email:[email protected] 深圳市华迅贸易有限公司(以下简称“华迅”)自 2001 年成立伊始,就致力向中国航空工业提供高品质的航空化工产品和消耗材料, 经过多年来的努力和本着“诚信、专业、变革、进取”的宗旨,目前已与东航、南航、海航、深圳航空、上海航空、四川航空、山东 航空、厦门航空、中国货运航空、春秋航空、吉祥航空、上海国际货运航空、扬子江快运、东星航空、华夏航空、中国联合航空、 东海航空、通用航空等航空公司和北京飞机维修工程有限公司、广州飞机维修工程有限公司、上海科技宇航、上海波音航空改装维 修工程有限公司、上海东联、珠海摩天宇、四川斯奈克玛、厦门豪富太古飞机工程有限公司等飞机维修公司及中国民航飞行学院、 深圳鲲鹏国际飞行学院等飞行院校保持着良好的业务往来。 Since established in Jan 2001, Shenzhen Huaxun Trading Co., Ltd. (hereinafter called “Huaxun” for short) has applied herself to supply high-quality products and consumables for Chinese aviation industry. After making great efforts for many years and carrying out the tenet of “honesty , professionalism, innovation and enterprise”, Huaxun has become a qualified and dependable partner of domestic airlines such as China Eastern Airlines, China Southern Airlines, Hainan Airlines, Shenzhen Airlines, Shanghai Airlines, Sichuan Airlines, Shandong Airlines, Xiamen Airlines, China Cargo Airlines, Spring Airlines, Juneyao Airlines, Shanghai Airlines Cargo Intl, Yangtze River Express Airlines, East Star Airlines , China Express Airlines, China United Airlines, Donghai Airlines, General Airlines as well as aviation maintenance corporations such as AMECO, GAMECO, STARCO, BSAS, CEASA, MTU Maintenance Zhuhai, SSAMC, Goodrich TAECO and some civil aviation colleges as CAFUC, Shenzhen Kunpeng International Flight College etc. 华迅作为航化产品经销商,经营产品范围涵盖了润滑油、润滑脂、液压油、清洗剂、防腐剂、除锈剂、胶粘剂、密封胶、胶 带、油漆、无损探伤、复合材料、表面处理产品等。目前全球合作伙伴主要有埃克森美孚, 首诺, 壳牌, 汉高, LPS, 3M, ANDEROL, DOWCORNING, PPG, GE, ZIP-CHEM, ACHESON, HUNTSMAN, WD-40, HEXCEL, CYTEC, AKZONOBEL, ORCON, MILLER-STEPHENSON, MCGEAN-ROHCO, PERMACEL, BOSTIK 等。 As a domestic supplier of aviation chemicals, Huaxun’s products cover aviation lubricants, greases, hydraulic fluids, cleaners, anti-corrosions, anti-rusts, adhesives, sealants, tapes, paints, NDT, composite materials and surface treatment products etc. -

The Evolution of Chinese Bankruptcy Law: Challenges of a Growing Practice Area
The Evolution of Chinese Bankruptcy Law: Challenges of a Growing Practice Area Richard C. Pedone Partner Nixon Peabody LLP Henry H. Liu Partner DLA Piper LLP (U.S.) Bankruptcy Cases in China During 2009, approximately 2,900 bankruptcy cases were filed in China, which is down from 3,139 in 2008 and 3,810 in 2007.1 The number of bankruptcy filings in China is relatively low compared to the U.S., where, for example, in March 2009 alone, 8,162 business cases were filed.2 Rarity of Bankruptcy Cases in China and Explanations Therefore Some commentators have posited a number of theories for the relative rarity of bankruptcy cases, including the significant impact of local governments in deciding whether a business should enter bankruptcy and the incentives of not allowing companies to enter into bankruptcy.3 Brief History of Bankruptcy Practice in China. China has a relative short bankruptcy practice history. A bankruptcy law was first introduced in China in 1906, during the last years of the Qing Dynasty, which met its demise in 1911. Bankruptcy laws were later issued in 1915 and 1935 during the Republic of China period, which ended in 1949 when the People’s Republic of China was founded. For more than thirty years after 1949, there was no bankruptcy system in practice. In 1986, the first bankruptcy law for state-owned enterprises was promulgated. Bankruptcy and insolvency for private companies and foreign-invested companies continued to be governed by separate laws. The Enterprise Bankruptcy Law (EBL), which is more broadly applicable, became effective in 2007. -

Low Cost Carrier Competition and Route Entry in an Emerging but Regulated Aviation Market
Low Cost Carrier Competition and Route Entry in an Emerging but Regulated Aviation Market - the Case of China XIAOWEN FU Institute of Transport and Logistics Studies The University of Sydney E-mail: [email protected] ZHENG LEI* Centre for Aviation Research University of Surrey *Corresponding Author, E-mail: [email protected] KUN WANG Sauder School of Business University of British Columbia E-mail: [email protected] JIA YAN School of Economics Sciences Washington State University E-mail: [email protected] Acknowledgements: We would like to thank helpful comments provided by three anonymous referees, the editor of the special issue, and participants of the 17th ATRS (Air Transport Research Society) conference held in Bergamo, Italy. Financial supports from the University of Sydney Business School (General Research Grant) are gratefully acknowledged. All remaining errors are ours. 1 Low Cost Carrier Competition and Route Entry in an Emerging but Regulated Aviation Market - the Case of China Abstract Although China lags behind other liberalized aviation markets in low cost carrier (LCC) development, its largest LCC, Spring Airlines, has achieved rapid growth in traffic volume and revenue, as well as consistent profitability, since its inauguration in 2005. Our empirical study on the Chinese domestic market suggests that Spring adopts a “cream skimming” strategy to enter high-priced routes, allowing the carrier to achieve both a very high load factor and considerable profitability. Spring’s capacity and market share on individual routes are constrained to low levels, likely due to government regulation and/or a “puppy dog” strategy adopted by the carrier. -
INTERNATIONAL WOMEN PILOTS MAGAZINE*’ (ISSN 1548-565X) 99 NEWS INTERNATIONAL Published by the NINETY-NINES* INC
INTERNATIONAL 99 NEWS WOMEN PILOTS OFFICIAL PUBLICATION OF THE N I N ETY- NINES® INC "OONEY November/December 2004 PERPETUAL CALENDAR 2004 JULY 1 -3 NW Section Meeting, Spokane WA. DECEMBER 6-10 EAA Fly-In, Arlington, WA. 5 Mr. and Mrs. Santa Claus Fly-In, MAPS Air Museum, Akron/Canton (CAK) 26- EAA, Oshkosh, Wl. Regional Airport. Contact Patricia Synk, Aug. 1 330-945-7518, [email protected]. To list your 99s events on this calendar page, 9-12 Sun 'n Fun High Flying Holidays. Fami AUGUST lies will enjoy holiday/aviation themed send information to: 1 99 News Deadline - September/October activities. Contact: Phone 863-644-2431 issue. The 99 News or [email protected]. P.O. Box 950033 10-12 WAI, Dallas, TX. 20 Deadline for Professional Pilot Leader Oklahoma City, OK ship Initiative (PPLI) Applications. Con 21-26 International 73195 tact Laura Smith, PPLI Program Leader, at C o n fere n ce in New Zealand. Fun Em ail: [email protected] or www. n i nety-n i nes.org/careers/mentori ng. htm I. and Fellowship articles99News(<l'cs.com Down Under. Pre- 31 Deadline for submission of Bylaws and/ and Post-Confer Online Form: or Standing Rules amendments. Send to ence tours of North www.ninety-nines.org/ Jerry Anne Jurenka, Intl. Bylaws/Standing and South Island 99newsreports.html Rules Chair, 10 Oak Forest Drive, are available. For Longview, TX 75605, USA. Fax 903-663- additional informa Please indicate the 5808; email [email protected]. tion go to name and location www.ninety- of the event, the nines.org. -

Frontier Politics and Sino-Soviet Relations: a Study of Northwestern Xinjiang, 1949-1963
University of Pennsylvania ScholarlyCommons Publicly Accessible Penn Dissertations 2017 Frontier Politics And Sino-Soviet Relations: A Study Of Northwestern Xinjiang, 1949-1963 Sheng Mao University of Pennsylvania, [email protected] Follow this and additional works at: https://repository.upenn.edu/edissertations Part of the History Commons Recommended Citation Mao, Sheng, "Frontier Politics And Sino-Soviet Relations: A Study Of Northwestern Xinjiang, 1949-1963" (2017). Publicly Accessible Penn Dissertations. 2459. https://repository.upenn.edu/edissertations/2459 This paper is posted at ScholarlyCommons. https://repository.upenn.edu/edissertations/2459 For more information, please contact [email protected]. Frontier Politics And Sino-Soviet Relations: A Study Of Northwestern Xinjiang, 1949-1963 Abstract This is an ethnopolitical and diplomatic study of the Three Districts, or the former East Turkestan Republic, in China’s northwest frontier in the 1950s and 1960s. It describes how this Muslim borderland between Central Asia and China became today’s Yili Kazakh Autonomous Prefecture under the Xinjiang Uyghur Autonomous Region. The Three Districts had been in the Soviet sphere of influence since the 1930s and remained so even after the Chinese Communist takeover in October 1949. After the Sino- Soviet split in the late 1950s, Beijing transformed a fragile suzerainty into full sovereignty over this region: the transitional population in Xinjiang was demarcated, border defenses were established, and Soviet consulates were forced to withdraw. As a result, the Three Districts changed from a Soviet frontier to a Chinese one, and Xinjiang’s outward focus moved from Soviet Central Asia to China proper. The largely peaceful integration of Xinjiang into PRC China stands in stark contrast to what occurred in Outer Mongolia and Tibet. -

UNITED STATES BANKRUPTCY COURT Southern District of New York *SUBJECT to GENERAL and SPECIFIC NOTES to THESE SCHEDULES* SUMMARY
UNITED STATES BANKRUPTCY COURT Southern District of New York Refco Capital Markets, LTD Case Number: 05-60018 *SUBJECT TO GENERAL AND SPECIFIC NOTES TO THESE SCHEDULES* SUMMARY OF AMENDED SCHEDULES An asterisk (*) found in schedules herein indicates a change from the Debtor's original Schedules of Assets and Liabilities filed December 30, 2005. Any such change will also be indicated in the "Amended" column of the summary schedules with an "X". Indicate as to each schedule whether that schedule is attached and state the number of pages in each. Report the totals from Schedules A, B, C, D, E, F, I, and J in the boxes provided. Add the amounts from Schedules A and B to determine the total amount of the debtor's assets. Add the amounts from Schedules D, E, and F to determine the total amount of the debtor's liabilities. AMOUNTS SCHEDULED NAME OF SCHEDULE ATTACHED NO. OF SHEETS ASSETS LIABILITIES OTHER YES / NO A - REAL PROPERTY NO 0 $0 B - PERSONAL PROPERTY YES 30 $6,002,376,477 C - PROPERTY CLAIMED AS EXEMPT NO 0 D - CREDITORS HOLDING SECURED CLAIMS YES 2 $79,537,542 E - CREDITORS HOLDING UNSECURED YES 2 $0 PRIORITY CLAIMS F - CREDITORS HOLDING UNSECURED NON- YES 356 $5,366,962,476 PRIORITY CLAIMS G - EXECUTORY CONTRACTS AND UNEXPIRED YES 2 LEASES H - CODEBTORS YES 1 I - CURRENT INCOME OF INDIVIDUAL NO 0 N/A DEBTOR(S) J - CURRENT EXPENDITURES OF INDIVIDUAL NO 0 N/A DEBTOR(S) Total number of sheets of all Schedules 393 Total Assets > $6,002,376,477 $5,446,500,018 Total Liabilities > UNITED STATES BANKRUPTCY COURT Southern District of New York Refco Capital Markets, LTD Case Number: 05-60018 GENERAL NOTES PERTAINING TO SCHEDULES AND STATEMENTS FOR ALL DEBTORS On October 17, 2005 (the “Petition Date”), Refco Inc. -

Die Folgende Liste Zeigt Alle Fluggesellschaften, Die Über Den Flugvergleich Von Verivox Buchbar Sein Können
Die folgende Liste zeigt alle Fluggesellschaften, die über den Flugvergleich von Verivox buchbar sein können. Aufgrund von laufenden Updates einzelner Tarife, technischen Problemen oder eingeschränkten Verfügbarkeiten kann es vorkommen, dass einzelne Airlines oder Tarife nicht berechnet oder angezeigt werden können. 1 Adria Airways 2 Aegean Airlines 3 Aer Arann 4 Aer Lingus 5 Aeroflot 6 Aerolan 7 Aerolíneas Argentinas 8 Aeroméxico 9 Air Algérie 10 Air Astana 11 Air Austral 12 Air Baltic 13 Air Berlin 14 Air Botswana 15 Air Canada 16 Air Caraibes 17 Air China 18 Air Corsica 19 Air Dolomiti 20 Air Europa 21 Air France 22 Air Guinee Express 23 Air India 24 Air Jamaica 25 Air Madagascar 26 Air Malta 27 Air Mauritius 28 Air Moldova 29 Air Namibia 30 Air New Zealand 31 Air One 32 Air Serbia 33 Air Transat 34 Air Asia 35 Alaska Airlines 36 Alitalia 37 All Nippon Airways 38 American Airlines 39 Arkefly 40 Arkia Israel Airlines 41 Asiana Airlines 42 Atlasglobal 43 Austrian Airlines 44 Avianca 45 B&H Airlines 46 Bahamasair 47 Bangkok Airways 48 Belair Airlines 49 Belavia Belarusian Airlines 50 Binter Canarias 51 Blue1 52 British Airways 53 British Midland International 54 Brussels Airlines 55 Bulgaria Air 56 Caribbean Airlines 57 Carpatair 58 Cathay Pacific 59 China Airlines 60 China Eastern 61 China Southern Airlines 62 Cimber Sterling 63 Condor 64 Continental Airlines 65 Corsair International 66 Croatia Airlines 67 Cubana de Aviacion 68 Cyprus Airways 69 Czech Airlines 70 Darwin Airline 71 Delta Airlines 72 Dragonair 73 EasyJet 74 EgyptAir 75 -

Airliner Census Western-Built Jet and Turboprop Airliners
World airliner census Western-built jet and turboprop airliners AEROSPATIALE (NORD) 262 7 Lufthansa (600R) 2 Biman Bangladesh Airlines (300) 4 Tarom (300) 2 Africa 3 MNG Airlines (B4) 2 China Eastern Airlines (200) 3 Turkish Airlines (THY) (200) 1 Equatorial Int’l Airlines (A) 1 MNG Airlines (B4 Freighter) 5 Emirates (300) 1 Turkish Airlines (THY) (300) 5 Int’l Trans Air Business (A) 1 MNG Airlines (F4) 3 Emirates (300F) 3 Turkish Airlines (THY) (300F) 1 Trans Service Airlift (B) 1 Monarch Airlines (600R) 4 Iran Air (200) 6 Uzbekistan Airways (300) 3 North/South America 4 Olympic Airlines (600R) 1 Iran Air (300) 2 White (300) 1 Aerolineas Sosa (A) 3 Onur Air (600R) 6 Iraqi Airways (300) (5) North/South America 81 RACSA (A) 1 Onur Air (B2) 1 Jordan Aviation (200) 1 Aerolineas Argentinas (300) 2 AEROSPATIALE (SUD) CARAVELLE 2 Onur Air (B4) 5 Jordan Aviation (300) 1 Air Transat (300) 11 Europe 2 Pan Air (B4 Freighter) 2 Kuwait Airways (300) 4 FedEx Express (200F) 49 WaltAir (10B) 1 Saga Airlines (B2) 1 Mahan Air (300) 2 FedEx Express (300) 7 WaltAir (11R) 1 TNT Airways (B4 Freighter) 4 Miat Mongolian Airlines (300) 1 FedEx Express (300F) 12 AIRBUS A300 408 (8) North/South America 166 (7) Pakistan Int’l Airlines (300) 12 AIRBUS A318-100 30 (48) Africa 14 Aero Union (B4 Freighter) 4 Royal Jordanian (300) 4 Europe 13 (9) Egyptair (600R) 1 American Airlines (600R) 34 Royal Jordanian (300F) 2 Air France 13 (5) Egyptair (600R Freighter) 1 ASTAR Air Cargo (B4 Freighter) 6 Yemenia (300) 4 Tarom (4) Egyptair (B4 Freighter) 2 Express.net Airlines -

An Evolutionary Perspective on Tourism Area Development
Tourism Area Development from an Evolutionary Economic Geography Perspective —The Case of Guilin, China Doctoral dissertation The Faculty of Mathematics and Natural Sciences of Christian-Albrechts-Universität zu Kiel Submitted for the doctoral degree by Mulan Ma Kiel, 2013 DECLARATION I hereby declare that this submission is my own work and that, to the best of my knowledge and belief, it contains no material previously published or written by another person nor material which has been accepted for the award of any other degree or diploma of the university or other institute of higher learning, except where due acknowledgement has been made in the text. This thesis has been prepared subject to the Rules of Good Scientific Practice of the German Research Foundation. This thesis work was conducted from October 2009 to May 2013 under the supervision of Prof. Robert Hassink at Department of Geography, University of Kiel. Name: Mulan Ma Signature: Place: Kiel Date: Supervisors: Prof. Dr. Robert Hassink Jun.-Prof. Dr. Max-Peter Menzel Defense of doctoral dissertation: 4th July 2013 Approved for publication: 13th August 2013 gez. Prof. Dr. Wolfgang J. Duschl, Dekan The research project of this dissertation was conducted at the Department of Geography, Faculty of Mathematics and Natural Sciences at the Christian-Albrechts-Universtät zu Kiel. The project was funded by the Chinese Scholarship Council (CSC). Acknowledgements With the deepest gratitude I wish to thank every person who has inspired, illuminated, supported and encouraged me to make this dissertation possible. First and foremost I would like to thank my supervisor, Professor Robert Hassink. His vision, enthusiasm, kindness and patience guided me through the various stages of this process. -

Tailormade Tour Guide
CHINA tailormade tour guide contents China brief Introduction & Climate map & Traditional Festival Explore China Top 10 Recommended Destinations Major Airport in China Top Airlines in China Train station in Major cities Type of train in China Top 10 Recommended Historic Attractions Top 10 Recommended Natural Beauties Top 10 Recommended beautiful Towns Top Minority Cities Most Popular Chinese Dishes China Currency and Exchange Info Electricity and Voltage Helpful Numbers Visa for China Flexible, Time-saving, Fast & Easy Tailor-making Procedure Novaland Tours Clients’ Photos China Brief Introduction China, officially the People's Republic of China (PRC), is a unitary sovereign state in East Asia and the world's most populous country, with a population of over 1.381 billion.Covering approximately 9.6 million square kilometers (3.7 million square miles), it is the world's second-largest state by land area and third- or fourth-largest by total area. Governed by the Communist Party of China, it exer- cises jurisdiction over 22 provinces, five autonomous regions,four direct-controlled municipalities (Beijing, Tianjin, Shanghai, and Chongqing) and the Special Administrative Regions Hong Kong and Macau, also claiming sovereignty over Taiwan. China is a great power and a major regional power within Asia, and has been characterized as a potential superpower. China emerged as one of the world's earliest civilizations in the fertile basin of the Yellow River in the North China Plain. For millennia, China's political system was based on hereditary monarchies, or dynasties, beginning with the semi-legendary Xia dynasty. Since then, China has then expanded, fractured, and re-unified numerous times. -

Strategy Report Hong Kong Equity Research
Thursday, 3 December, 2020 China Merchants Securities (HK) Co., Ltd. Strategy Report Hong Kong Equity Research 2021 Outlook: Road towards restoration Jessie Guo, PhD +852 3189 6121 [email protected] “Lives of great men all remind us, we can make our lives sublime. Let Edith Qian, CFA +852 3189 6752 us, then, be up and doing. With a heart for any fate, still achieving, still [email protected] pursuing; learn to labour and to wait”. Harrington Zhang, PhD - Henry Wadsworth Longfellow, A Psalm of Life +852 3189 6751 [email protected] Tommy Wong View on economic recovery +852 3189 6634 [email protected] The outbreak of COVID-19 sent global economic growth deep into negative Johnny Wong territory in 2020. Synchronised large-scale fiscal and monetary policies +852 3189 6357 prevented major economies from sliding into perennial recession. [email protected] According to the IMF, global GDP will contract by 4.4% in 2020 and rebound Yonghuo Liang +86 755 8290 4571 by 5.2% in 2021, but the pace of recovery will be uneven across countries. [email protected] We expect the US economy to have a relatively muted start next year, and Kevin Chen then followed by a brighter second half, while the Fed’s monetary policy will +852 3189 6125 remain abundantly accommodative throughout the entire 2021. [email protected] Felix Luo, PhD +852 3189 6288 We stay positive on China’s economic outlook, mainly driven by domestic [email protected] consumption and manufacturing investment. We expect a rather neutral Yiding Jiao, CFA fiscal and monetary policy stance.