Media Access Control (MAC) (With Some IEEE 802 Standards)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Part 2: Packet Transmission
Mesh networks LAN technologies and network topology • Early local networks used dedicated links between each pair of computers LANs and shared media • Some useful properties Locality of reference – hardware and frame details can be tailored for Star, bus and ring topologies each link Medium access control protocols – easy to enforce security and privacy Disadvantages of meshes Links between rooms/buildings • Poor scalability • Many links would follow the same physical path Shared Communication Channels Locality of reference • Shared LANs invented in the 1960s • LANs now connect more computers than any other form of network • Rely on computers sharing a single medium • The reason LANs are so popular is due to • Computers coordinate their access the principle of locality of reference • Low cost – physical locality of reference - computers more • But not suitable for wide area - likely to communicate with those nearby communication delays inhibit coordination – temporal locality of reference - computer is more likely to communicate with the same computers repeatedly 1 LAN topologies • LANs may be categorised according to topology ring bus star Pros and cons Example bus network: Ethernet • Star is more robust but hub may be a • Single coaxial cable - the ether - to which bottleneck computers connect • Ring enables easy coordination but is • IEEE standard specifies details sensitive to a cable being cut – data rates • Bus requires less wiring but is also sensitive – maximum length and minimum separation to a cable being cut – frame formats -

Implementing MACA and Other Useful Improvements to Amateur Packet Radio for Throughput and Capacity
Implementing MACA and Other Useful Improvements to Amateur Packet Radio for Throughput and Capacity John Bonnett – KK6JRA / NCS820 Steven Gunderson – CMoLR Project Manager TAPR DCC – 15 Sept 2018 1 Contents • Introduction – Communication Methodology of Last Resort (CMoLR) • Speed & Throughput Tests – CONNECT & UNPROTO • UX.25 – UNPROTO AX.25 • Multiple Access with Collision Avoidance (MACA) – Hidden Terminals • Directed Packet Networks • Brevity – Directory Services • Trunked Packet • Conclusion 2 Background • Mission County – Proverbial: – Coastline, Earthquake Faults, Mountains & Hills, and Missions – Frequent Natural Disasters • Wildfires, Earthquakes, Floods, Slides & Tsunamis – Extensive Packet Networks • EOCs – Fire & Police Stations – Hospitals • Legacy 1200 Baud Packet Networks • Outpost and Winlink 2000 Messaging Software 3 Background • Mission County – Proverbial: – Coastline, Earthquake Faults, Mountains & Hills, and Missions – Frequent Natural Disasters • Wildfires, Earthquakes, Floods, Slides & Tsunamis – Extensive Packet Networks • EOCs – Fire & Police Stations – Hospitals • Legacy 1200 Baud Packet Networks • Outpost and Winlink 2000 Messaging Software • Community Emergency Response Teams: – OK Drills – Neighborhood Surveys OK – Triage Information • CERT Form #1 – Transmit CERT Triage Data to Public Safety – Situational Awareness 4 Background & Objectives (cont) • Communication Methodology of Last Resort (CMoLR): – Mission County Project: 2012 – 2016 – Enable Emergency Data Comms from CERT to Public Safety 5 Background & -

Upcoming Standards in Wireless Local Area Networks
Preprint: http://arxiv.org/abs/1307.7633 Original Publication: UPCOMING STANDARDS IN WIRELESS LOCAL AREA NETWORKS Sourangsu Banerji Department of Electronics & Communication Engineering, RCC-Institute of Information Technology, India Email: [email protected] ABSTRACT: Network technologies are However out of every one of these standards, traditionally centered on wireline solutions. WLAN and recent developments in WLAN Wireless broadband technologies nowadays technology will be our main subject of study in this particular paper. The IEEE 802.11 is the most provide unlimited broadband usage to users widely deployed WLAN technology as of today. that have been previously offered simply to Another renowned counterpart is the HiperLAN wireline users. In this paper, we discuss some of standard by ETSI. These two technologies are the upcoming standards of one of the emerging united underneath the Wireless Fidelity (Wi-fi) wireless broadband technology i.e. IEEE alliance. In literature though, IEEE802.11 and Wi- 802.11. The newest and the emerging standards fi is used interchangeably and we will also continue with the same convention in this fix technology issues or add functionality that particular paper. A regular WLAN network is will be expected to overcome many of the associated with an Access Point (AP) in the current standing problems with IEEE 802.11. middle/centre and numerous stations (STAs) are connected to this central Access Point (AP).Now, Keywords: Wireless Communications, IEEE there are just two modes in which communication 802.11, WLAN, Wi-fi. normally takes place. 1. Introduction Within the centralized mode of communication, The wireless broadband technologies were communication to/from a STA is actually carried developed with the objective of providing services across by the APs. -

Reservation - Time Division Multiple Access Protocols for Wireless Personal Communications
tv '2s.\--qq T! Reservation - Time Division Multiple Access Protocols for Wireless Personal Communications Theodore V. Buot B.S.Eng (Electro&Comm), M.Eng (Telecomm) Thesis submitted for the degree of Doctor of Philosophy 1n The University of Adelaide Faculty of Engineering Department of Electrical and Electronic Engineering August 1997 Contents Abstract IY Declaration Y Acknowledgments YI List of Publications Yrt List of Abbreviations Ylu Symbols and Notations xi Preface xtv L.Introduction 1 Background, Problems and Trends in Personal Communications and description of this work 2. Literature Review t2 2.1 ALOHA and Random Access Protocols I4 2.1.1 Improvements of the ALOHA Protocol 15 2.1.2 Other RMA Algorithms t6 2.1.3 Random Access Protocols with Channel Sensing 16 2.1.4 Spread Spectrum Multiple Access I7 2.2Fixed Assignment and DAMA Protocols 18 2.3 Protocols for Future Wireless Communications I9 2.3.1 Packet Voice Communications t9 2.3.2Reservation based Protocols for Packet Switching 20 2.3.3 Voice and Data Integration in TDMA Systems 23 3. Teletraffic Source Models for R-TDMA 25 3.1 Arrival Process 26 3.2 Message Length Distribution 29 3.3 Smoothing Effect of Buffered Users 30 3.4 Speech Packet Generation 32 3.4.1 Model for Fast SAD with Hangover 35 3.4.2Bffect of Hangover to the Speech Quality 38 3.5 Video Traffic Models 40 3.5.1 Infinite State Markovian Video Source Model 41 3.5.2 AutoRegressive Video Source Model 43 3.5.3 VBR Source with Channel Load Feedback 43 3.6 Summary 46 4. -

A Survey on Aloha Protocol for Iot Based Applications
ISSN: 2277-9655 [Badgotya * et al., 7(5): May, 2018] Impact Factor: 5.164 IC™ Value: 3.00 CODEN: IJESS7 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY A SURVEY ON ALOHA PROTOCOL FOR IOT BASED APPLICATIONS Shikha Badgotya*1 & Prof.Deepti Rai2 *1M.Tech Scholar, Department of EC, Alpine Institute of Technology,, Ujjain (India) 2H.O.D, Department of EC, Alpine Institute of Technology, Ujjain (India) DOI: 10.5281/zenodo.1246995 ABSTRACT With the emergence of IoT based applications in industries and automation, protocols for effective data transfer was the foremost need. The natural choice was a random access protocol like ALOHA which could be incorporated in the ultra narrowband ISM band framework because of its simplicity and lack of overhead. Pure ALOHA faced the limitation of greater rate of collisions among the packets of data and also there was higher level of frame delays. Slotted ALOHA overcame these limitations to some extent in which the transfer of data takes place after channel polling. Though the drawbacks of PURE ALOHA are somewhat resolved in Slotted ALOHA, still some redundant transmissions and delay of frames exist. The present proposed work puts forth an efficient mechanism for Slotted ALOHA which implements polling of channel that is non persistent in nature to reduce the probability of collisions considerably. Further it presents a channel sensing methodology also for prevention of burst errors. Interleaving serves to be useful in case of burst errors and helps in preserving useful information. The survey should pave the path for IoT based applications working on an ultra narrowband architecture. -

The Design of PROFIBUS-DP HUB Based on FPGA
International Conference on Computer Science and Service System (CSSS 2014) The Design of PROFIBUS-DP HUB based on FPGA Jiao Ping Zhou Tong Lab. of Networked Control Systems Lab. of Networked Control Systems Shenyang Institute of Automation (SIA), Chinese Shenyang Institute of Automation (SIA), Chinese Academy of Sciences China, Shenyang Academy of Sciences China, Shenyang [email protected] [email protected] Abstract—This paper analyzes the PROFIBUS-DP and specified the standard EIA RS-485, and the traffic rate is physical layer signals states, DP time series and other from 9.6kbps to 12Mbps [2, 3, 6]. characteristics. In the past, PROFIBUS-DP HUB common IEC 1158-2 specified the station number of problems of poor universal apply, shape communication is PROFIBUS-DP is 126 (station address from 0 to 125 contain more time-consuming, required message analysis, Drop frame master and slave station) [4]. In the one segment of etc, this paper propose a new design of PROFIBUS-DP HUB PROFIBUS-DP, the maximum station is 32. DP HUB or DP which based on FPGA. The design contain a detector which Repeater device requires the use, if want to connect more used to monitor the physical layer signal state of the DP bus, stations or change the network topology. As figure shown, use of FPGA synthesis logic signal, could control the direction DP HUB or DP Repeater divided the DP network into many of data flow in the physical layer, and Unrelated with the subnet segments [7]. Each interface of DP HUB is a upper layer protocol, without message analysis, compliance the protocol which used the standard RS-485, and Repeater, which can independently drive a PROFIBUS baudrate-adaptive. -

Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Volume6•Issue5 SEPTEMBER–OCTOBER 2005 © 2005 Contemporary Control Systems, Inc. Introduction to Spanning Tree Protocol By George Thomas, Contemporary Controls Introduction powered and its memory cleared (Bridge 2 will be added later). In an industrial automation application that relies heavily Station 1 sends a message to on the health of the Ethernet network that attaches all the station 11 followed by Station 2 controllers and computers together, a concern exists about sending a message to Station 11. what would happen if the network fails? Since cable failure is These messages will traverse the the most likely mishap, cable redundancy is suggested by bridge from one LAN to the configuring the network in either a ring or by carrying parallel other. This process is called branches. If one of the segments is lost, then communication “relaying” or “forwarding.” The will continue down a parallel path or around the unbroken database in the bridge will note portion of the ring. The problem with these approaches is the source addresses of Stations that Ethernet supports neither of these topologies without 1 and 2 as arriving on Port A. This special equipment. However, this issue is addressed in an process is called “learning.” When IEEE standard numbered 802.1D that covers bridges, and in Station 11 responds to either this standard the concept of the Spanning Tree Protocol Station 1 or 2, the database will (STP) is introduced. note that Station 11 is on Port B. IEEE 802.1D If Station 1 sends a message to Figure 1. The addition of Station 2, the bridge will do ANSI/IEEE Std 802.1D, 1998 edition addresses the Bridge 2 creates a loop. -
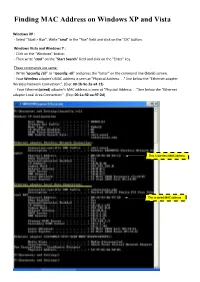
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Field Networking Solutions
Field Networking Solutions Courtesy of Steven Engineering, Inc. ! 230 Ryan Way, South San Francisco, CA 94080-6370 ! Main Office: (650) 588-9200 ! Outside Local Area: (800) 258-9200 ! www.stevenengineering.com TYPES OF FIELDBUS NETWORKS* Field Networking 101 Features and Benefits of Fieldbus Networks The combination of intelligent field devices, digital bus networks, and various open communications protocols Fieldbus networks provide an array of features and benefits that make them an excellent choice is producing extraordinary results at process plants in nearly all process control environments. around the world. Compared to conventional technology, fieldbus networks deliver the following benefits: Just as our ability to retrieve, share, and analyze data Reduced field wiring costs has increased tremendously by use of the Internet and - Two wires from the control room to many devices PC network technology in our homes and at our desk- Reduced commissioning costs tops, so has our ability to control and manage our - Less time and personnel needed to perform process plants improved. Digital connectivity in process I/O wiring checkouts - No time spent calibrating intermediate signals manufacturing plants provides an infrastructure for the (such as 4-20mA signals) - Digital values are delivered directly from field flow of real-time data from the process level, making it devices, increasing accuracy available throughout our enterprise networks. This data Reduced engineering/operating costs is being used at all levels of the enterprise to provide - Much smaller space required for panels, I/O racks, and connectivity boxes increased process monitoring and control, inventory and - Fewer I/O cards and termination panels for materials planning, advanced diagnostics, maintenance control system equipment - Lower power consumption by control system planning, and asset management. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Efficiently Triggering, Debugging and Decoding Low-Speed Serial Buses
Efficiently Triggering, Debugging and Decoding Low-Speed Serial Buses Hello, my name is Jerry Mark, I am a Product Marketing Engineer at Tektronix. The following presentation discusses aspects of embedded design techniques for “Efficiently Triggering, Debugging, and Decoding Low-Speed Serial Buses”. 1 Agenda Introduction – Parallel Interconnects – Transition from Parallel to Serial Buses – High-Speed versus Low-Speed Serial Data Buses Low-Speed Serial Data Buses – Challenges – Technology Reviews – Measurement Solutions Summary 2 In this presentation we will begin by taking a glance at the transition from parallel-to-serial data and the challenges this presents to engineers. Then we will briefly review some of the most widely used low-speed serial buses in industry today and some of their key characteristics. We will turn our attention to the key measurements on these buses. Subsequently, we will present by example how the low-speed serial solution from Tektronix addresses these challenges. 2 Parallel Interconnects Traditional way to connect digital devices used parallel buses Advantages – Simple point-to-point connections – All signals are transmitted in parallel, simultaneously – Easy to capture state of bus (if you have enough channels!) – Decoding the bus is relatively easy Disadvantages – Occupies a lot of circuit board space – All high-speed connections must be the same length – Many connections limit reliability – Connectors may be very large 3 Parallel buses present all of the bits in parallel, as shown in the logic analyzer display. A parallel connection between two ICs can be as simple as point-to-point circuit board traces for each of the data lines. If you can physically probe these lines, it is easy to display the bus state on a logic analyzer or mixed signal oscilloscope. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001