Introduction to Spanning Tree Protocol by George Thomas, Contemporary Controls
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Transparent LAN Service Over Cable
Transparent LAN Service over Cable This document describes the Transparent LAN Service (TLS) over Cable feature, which enhances existing Wide Area Network (WAN) support to provide more flexible Managed Access for multiple Internet service provider (ISP) support over a hybrid fiber-coaxial (HFC) cable network. This feature allows service providers to create a Layer 2 tunnel by mapping an upstream service identifier (SID) to an IEEE 802.1Q Virtual Local Area Network (VLAN). Finding Feature Information Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the Feature Information Table at the end of this document. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://tools.cisco.com/ITDIT/CFN/. An account on http:// www.cisco.com/ is not required. Contents • Hardware Compatibility Matrix for Cisco cBR Series Routers, page 2 • Prerequisites for Transparent LAN Service over Cable, page 2 • Restrictions for Transparent LAN Service over Cable, page 3 • Information About Transparent LAN Service over Cable, page 3 • How to Configure the Transparent LAN Service over Cable, page 6 • Configuration Examples for Transparent LAN Service over Cable, page 8 • Verifying the Transparent LAN Service over Cable Configuration, page 10 • Additional References, page 11 • Feature Information for Transparent LAN Service over Cable, page 12 Cisco Converged Broadband Routers Software Configuration Guide For DOCSIS 1 Transparent LAN Service over Cable Hardware Compatibility Matrix for Cisco cBR Series Routers Hardware Compatibility Matrix for Cisco cBR Series Routers Note The hardware components introduced in a given Cisco IOS-XE Release are supported in all subsequent releases unless otherwise specified. -

How to Set up IP Camera by Using a Macintosh Computer
EDIMAX COMPUTER INC. Edimax IP Camera series How to set up IP Camera by using a Macintosh computer 2011 Edimax Computer 3350 Scott Blvd., Building #15 Santa Clara, California 95054, USA Phone 408-496-1105 • Fax 408-980-1530 www.edimax.us How to setup Edimax IP Camera by a Macintosh computer Introduction The most important thing to setup IP Camera is to assign a static IP address so the camera can work with your network. So far the Edimax IP Cam Admin utility is Windows based only and the program can not work for Macintosh computers. Macintosh users can follow this guide to set up Edimax IP camera. Step 1. Understand the IP address used in your network. Have your Macintosh computer operate as usual. Go into System Preferences. In System Preferences, Go to Network. Select the adapter you are using. It could be an Airport card, a third- party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We have a usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses used in the network are 10.0.1.x. All the devices in the network have the first three octets the same, but the last octet number must be different. We decide to give our new camera an IP address 10.0.1.100 because no other computer device use 10.0.1.100. We temporarily disconnect the wireless adapter. You can turn off your Airport adapter if you use it to get on Internet. -

Ieee 802.1 for Homenet
IEEE802.org/1 IEEE 802.1 FOR HOMENET March 14, 2013 IEEE 802.1 for Homenet 2 Authors IEEE 802.1 for Homenet 3 IEEE 802.1 Task Groups • Interworking (IWK, Stephen Haddock) • Internetworking among 802 LANs, MANs and other wide area networks • Time Sensitive Networks (TSN, Michael David Johas Teener) • Formerly called Audio Video Bridging (AVB) Task Group • Time-synchronized low latency streaming services through IEEE 802 networks • Data Center Bridging (DCB, Pat Thaler) • Enhancements to existing 802.1 bridge specifications to satisfy the requirements of protocols and applications in the data center, e.g. • Security (Mick Seaman) • Maintenance (Glenn Parsons) IEEE 802.1 for Homenet 4 Basic Principles • MAC addresses are “identifier” addresses, not “location” addresses • This is a major Layer 2 value, not a defect! • Bridge forwarding is based on • Destination MAC • VLAN ID (VID) • Frame filtering for only forwarding to proper outbound ports(s) • Frame is forwarded to every port (except for reception port) within the frame's VLAN if it is not known where to send it • Filter (unnecessary) ports if it is known where to send the frame (e.g. frame is only forwarded towards the destination) • Quality of Service (QoS) is implemented after the forwarding decision based on • Priority • Drop Eligibility • Time IEEE 802.1 for Homenet 5 Data Plane Today • 802.1Q today is 802.Q-2011 (Revision 2013 is ongoing) • Note that if the year is not given in the name of the standard, then it refers to the latest revision, e.g. today 802.1Q = 802.1Q-2011 and 802.1D -

IEEE 802.1Aq Standard, Is a Computer Networking Technology Intended to Simplify the Creation and Configuration of Networks, While Enabling Multipath Routing
Brought to you by: Brian Miller Yuri Spillman - Specified in the IEEE 802.1aq standard, is a computer networking technology intended to simplify the creation and configuration of networks, while enabling multipath routing. - Link State Protocol - Based on IS-IS -The standard is the replacement for the older spanning tree protocols such as IEEE 802.1D, IEEE 802.1w, and IEEE 802.1s. These blocked any redundant paths that could result in layer 2(Data Link Layer), whereas IEEE 802.1aq allows all paths to be active with multiple equal cost paths, and provides much larger layer 2 topologies. 802.1aq is an amendment to the "Virtual Bridge Local Area Networks“ and adds Shortest Path Bridging (SPB). Shortest path bridging, which is undergoing IEEE’s standardization process, is meant to replace the spanning tree protocol (STP). STP was created to prevent bridge loops by allowing only one path between network switches or ports. When a network segment goes down, an alternate path is chosen and this process can cause unacceptable delays in a data center network. The ability to use all available physical connectivity, because loop avoidance uses a Control Plane with a global view of network topology Fast restoration of connectivity after failure, again because of Link State routing's global view of network topology Under failure, the property that only directly affected traffic is impacted during restoration; all unaffected traffic just continues Ideas are rejected by IEEE 802.1. accepted by the IETF and the TRILL WG is formed. Whoops, there is a problem. They start 802.1aq for spanning tree based shortest path bridging Whoops, spanning tree doesn’t hack it. -

Linear Algebraic Techniques for Spanning Tree Enumeration
LINEAR ALGEBRAIC TECHNIQUES FOR SPANNING TREE ENUMERATION STEVEN KLEE AND MATTHEW T. STAMPS Abstract. Kirchhoff's Matrix-Tree Theorem asserts that the number of spanning trees in a finite graph can be computed from the determinant of any of its reduced Laplacian matrices. In many cases, even for well-studied families of graphs, this can be computationally or algebraically taxing. We show how two well-known results from linear algebra, the Matrix Determinant Lemma and the Schur complement, can be used to elegantly count the spanning trees in several significant families of graphs. 1. Introduction A graph G consists of a finite set of vertices and a set of edges that connect some pairs of vertices. For the purposes of this paper, we will assume that all graphs are simple, meaning they do not contain loops (an edge connecting a vertex to itself) or multiple edges between a given pair of vertices. We will use V (G) and E(G) to denote the vertex set and edge set of G respectively. For example, the graph G with V (G) = f1; 2; 3; 4g and E(G) = ff1; 2g; f2; 3g; f3; 4g; f1; 4g; f1; 3gg is shown in Figure 1. A spanning tree in a graph G is a subgraph T ⊆ G, meaning T is a graph with V (T ) ⊆ V (G) and E(T ) ⊆ E(G), that satisfies three conditions: (1) every vertex in G is a vertex in T , (2) T is connected, meaning it is possible to walk between any two vertices in G using only edges in T , and (3) T does not contain any cycles. -

Teacher's Guide for Spanning and Weighted Spanning Trees
Teacher’s Guide for Spanning and weighted spanning trees: a different kind of optimization by sarah-marie belcastro 1TheMath. Let’s talk about spanning trees. No, actually, first let’s talk about graph theory,theareaof mathematics within which the topic of spanning trees lies. 1.1 Graph Theory Background. Informally, a graph is a collection of vertices (that look like dots) and edges (that look like curves), where each edge joins two vertices. Formally, A graph is a pair G =(V,E), where V is a set of dots and E is a set of pairs of vertices. Here are a few examples of graphs, in Figure 1: e b f a Figure 1: Examples of graphs. Note that the word vertex is singular; its plural is vertices. Two vertices that are joined by an edge are called adjacent. For example, the vertices labeled a and b in the leftmost graph of Figure 1 are adjacent. Two edges that meet at a vertex are called incident. For example, the edges labeled e and f in the leftmost graph of Figure 1 are incident. A subgraph is a graph that is contained within another graph. For example, in Figure 1 the second graph is a subgraph of the fourth graph. You can see this at left in Figure 2 where the subgraph in question is emphasized. Figure 2: More examples of graphs. In a connected graph, there is a way to get from any vertex to any other vertex without leaving the graph. The second graph of Figure 2 is not connected. -
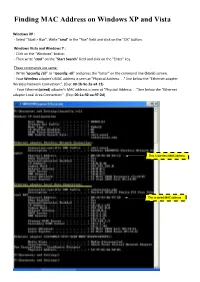
Finding MAC Address on Windows XP and Vista
Finding MAC Address on Windows XP and Vista Windows XP : - Select "Start > Run". Write "cmd" in the "Run" field and click on the "OK" button. Windows Vista and Windows 7 : - Click on the "Windows" button. - Then write "cmd" on the "Start Search" field and click on the "Enter" key. These commands are same: - Write "ipconfig /all" or "ipconfig -all" and press the "Enter" on the command line (blank) screen. - Your Wireless adapter’s MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Wireless Network Connection:”. (Exp: 00-1b-9e-2a-a4-13) - Your Ethernet(wired) adapter's MAC address is seen at "Physical Address. ." line below the “Ethernet adapter Local Area Connection:”. (Exp: 00-1a-92-aa-97-2d) This is wireless MAC address This is wired MAC address Finding MAC Address on Linux root@test:/ > ifconfig –a eth0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:85 <----- This is wired MAC address inet addr:10.92.52.10 Bcast:10.92.255.255 Mask:255.255.248.0 inet6 addr: fe80::1:2ae:9a85/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a85/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 wlan0 Link encap:Ethernet HWaddr 00:01:02:AE:9A:95 <----- This is wireless MAC address inet addr:10.80.2.94 Bcast:10.80.255.255 Mask:255.255.252.0 inet6 addr: fe80::1:2ae:9a95/10 Scope:Link inet6 addr: fe80::201:2ff:feae:9a95/10 Scope:Link UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1 Finding MAC Address on Macintosh OS 10.1 - 10.4 Please note: Wired and Wireless MAC addresses are different. -

Sampling Random Spanning Trees Faster Than Matrix Multiplication
Sampling Random Spanning Trees Faster than Matrix Multiplication David Durfee∗ Rasmus Kyng† John Peebles‡ Anup B. Rao§ Sushant Sachdeva¶ Abstract We present an algorithm that, with high probability, generates a random spanning tree from an edge-weighted undirected graph in Oe(n4/3m1/2 + n2) time 1. The tree is sampled from a distribution where the probability of each tree is proportional to the product of its edge weights. This improves upon the previous best algorithm due to Colbourn et al. that runs in matrix ω multiplication time, O(n ). For the special case of unweighted√ graphs, this improves upon the best previously known running time of O˜(min{nω, m n, m4/3}) for m n5/3 (Colbourn et al. ’96, Kelner-Madry ’09, Madry et al. ’15). The effective resistance metric is essential to our algorithm, as in the work of Madry et al., but we eschew determinant-based and random walk-based techniques used by previous algorithms. Instead, our algorithm is based on Gaussian elimination, and the fact that effective resistance is preserved in the graph resulting from eliminating a subset of vertices (called a Schur complement). As part of our algorithm, we show how to compute -approximate effective resistances for a set S of vertex pairs via approximate Schur complements in Oe(m + (n + |S|)−2) time, without using the Johnson-Lindenstrauss lemma which requires Oe(min{(m + |S|)−2, m + n−4 + |S|−2}) time. We combine this approximation procedure with an error correction procedure for handing edges where our estimate isn’t sufficiently accurate. -

Power Over Ethernet
How To | Power over Ethernet Introduction Power over Ethernet (PoE) is a technology allowing devices such as IP telephones to receive power over existing LAN cabling. This technical note is in four parts as follows: • PoE Technology • How PoE works • Allied Telesyn PoE implementation • Command Reference What information will you find in this document? The first two parts of this document describe the PoE technology, and the installation and management advantages that PoE can provide. This is followed by an overview of how PoE works, Power Device(PD) discovery, PD classification, and the delivery of power to PD data cables. The third part of this document focuses on Allied Telesyn’s implementation of PoE on the AT-8624PoE switch. The document concludes with a list of configuration and monitoring commands. Which product and software version does this information apply to? The information provided here applies to: • Products: AT8624PoE switch • Software version: 2.6.5 C613-16048-00 REV C www.alliedtelesyn.com PoE Technology Power over Ethernet is a mechanism for supplying power to network devices over the same cabling used to carry network traffic. PoE allows devices that require power, called Powered Devices (PDs), such as IP telephones, wireless LAN Access Points, and network cameras to receive power in addition to data, over existing infrastructure without needing to upgrade it. This feature can simplify network installation and maintenance by using the switch as a central power source for other network devices. A device that can source power such as an Ethernet switch is termed Power Sourcing Equipment (PSE). Power Sourcing Equipment can provide power, along with data, over existing LAN cabling to Powered Devices. -

Modular Embedded PC's with Intel® Atom™ E3800 Top Side The
QSys Modular Embedded PC’s with Intel® Atom™ E3800 The Qseven mainboard (carrier board) MB-Q7-2 in combination with The highlights: a standard Qseven 2.0 (x86) module forms an ultra compact hardware kit. By use of the new Intel® Atom™ family E3800 (BayTrail“) a very Based on Intel® Atom™ E3800 („BayTrail“) economical and extremely powerful embedded PC is available. The Optimized for ultra low power integrated Intel® HD Graphics Engine (Generation 7) raises the bar also Extended temperature in graphic intensive low power applications. High speed interfaces like Gigabit Ethernet, USB 3.0 and eSATAp The compact design with only 10 cm x 10 cm x 2,3 cm and the huge DisplayPort and LVDS amount of interfaces and functionalities allows the user to create high Extendable with 2x Mini PCIe incl. SIM card socket performant but passive cooled solutions like BoxPCs, PanelPCs and Onboard eMMC and mSATA socket custom specific devices in a very fast and convenient way. Integrated security features Audio with integrated amplifier Another key aspect is security which is supported by TPM 1.2/2.0, Ultra compact design (10cm x 10 cm x 2,3 cm) a Sentinel HL security controller and an integrated secure EEPROM Longevity support which allows the user to realize a very secure embedded device. Also usable as embedded alternative for Intel® NUC Standard boards (eNUC) Top side Bottom side Technical data hardware kit Performance/configurations Microprocessor (CPU module) With extended temperature support: CPU: Intel® Atom™ E3800 („BayTrail-I“) 5 variants from 1,46 GHz Single Core up to E3815: 1x 1,46 GHz, 512 KB L2-Cache, HD Gfx 400/400 MHz, 1,91 GHz Quad Core 5 W TDP, 2 GB Single-Ch. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Layer 2 Virtual Private Networks CM-SP-L2VPN-I11-130808
Data-Over-Cable Service Interface Specifications Business Services over DOCSIS® Layer 2 Virtual Private Networks CM-SP-L2VPN-I11-130808 ISSUED Notice This DOCSIS specification is the result of a cooperative effort undertaken at the direction of Cable Television Laboratories, Inc. for the benefit of the cable industry and its customers. This document may contain references to other documents not owned or controlled by CableLabs®. Use and understanding of this document may require access to such other documents. Designing, manufacturing, distributing, using, selling, or servicing products, or providing services, based on this document may require intellectual property licenses from third parties for technology referenced in this document. Neither CableLabs nor any member company is responsible to any party for any liability of any nature whatsoever resulting from or arising out of use or reliance upon this document, or any document referenced herein. This document is furnished on an "AS IS" basis and neither CableLabs nor its members provides any representation or warranty, express or implied, regarding the accuracy, completeness, noninfringement, or fitness for a particular purpose of this document, or any document referenced herein. Cable Television Laboratories, Inc., 2006-2013 CM-SP-L2VPN-I11-130808 Data-Over-Cable Service Interface Specifications DISCLAIMER This document is published by Cable Television Laboratories, Inc. ("CableLabs®"). CableLabs reserves the right to revise this document for any reason including, but not limited to, changes in laws, regulations, or standards promulgated by various agencies; technological advances; or changes in equipment design, manufacturing techniques, or operating procedures described, or referred to, herein. CableLabs makes no representation or warranty, express or implied, with respect to the completeness, accuracy, or utility of the document or any information or opinion contained in the report.