Wounded Warrior Or War Hero?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sample File This Page Intentionally Left Blank
The Comic Art of War Sample file This page intentionally left blank Sample file The Comic Art of War A Critical Study of Military Cartoons, 1805–2014, with a Guide to Artists Christina M. Knopf Sample file McFarland & Company, Inc., Publishers Jefferson, North Carolina LIBRARY OF CONGRESS CATALOGUING-IN-PUBLICATION DATA Knopf, Christina M., 1980– The comic art of war : a critical study of military cartoons, 1805–2014, with a guide to artists / Christina M. Knopf. p. cm. Includes bibliographical references and index. ISBN 978-0-7864-9835-2 (softcover : acid free paper) ISBN 978-1-4766-2081-7 (ebook) ♾ 1. War—Caricatures and cartoons. 2. Soldiers—Caricatures and cartoons. 3. MilitarySample life—Caricatures file and cartoons. I. Title. U20.K58 2015 355.0022'2—dc23 2015024596 BRITISH LIBRARY CATALOGUING DATA ARE AVAILABLE © 2015 Christina M. Knopf. All rights reserved No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying or recording, or by any information storage and retrieval system, without permission in writing from the publisher. On the cover: COMPANY DIS-MISSED! by Abian A. “Wally” Wallgren which appeared in the final World War I issue of Stars and Stripes (vol. 2 no. 19: p. 7) on June 18, 1919. It features the artist dismissing his models, or characters, from duty at the end of the war. Printed in the United States of America McFarland & Company, Inc., Publishers Box 611, Jefferson, North Carolina 28640 www.mcfarlandpub.com Acknowledgments It is said that writing is a solitary activity. -

First-Run Smoking Presentations in U.S. Movies 1999-2006
First-Run Smoking Presentations in U.S. Movies 1999-2006 Jonathan R. Polansky Stanton Glantz, PhD CENTER FOR TOBAccO CONTROL RESEARCH AND EDUCATION UNIVERSITY OF CALIFORNIA, SAN FRANCISCO SAN FRANCISCO, CA 94143 April 2007 EXECUTIVE SUMMARY Smoking among American adults fell by half between 1950 and 2002, yet smoking on U.S. movie screens reached historic heights in 2002, topping levels observed a half century earlier.1 Tobacco’s comeback in movies has serious public health implications, because smoking on screen stimulates adolescents to start smoking,2,3 accounting for an estimated 52% of adolescent smoking initiation. Equally important, researchers have observed a dose-response relationship between teens’ exposure to on-screen smoking and smoking initiation: the greater teens’ exposure to smoking in movies, the more likely they are to start smoking. Conversely, if their exposure to smoking in movies were reduced, proportionately fewer teens would likely start smoking. To track smoking trends at the movies, previous analyses have studied the U.S. motion picture industry’s top-grossing films with the heaviest advertising support, deepest audience penetration, and highest box office earnings.4,5 This report is unique in examining the U.S. movie industry’s total output, and also in identifying smoking movies, tobacco incidents, and tobacco impressions with the companies that produced and/or distributed the films — and with their parent corporations, which claim responsibility for tobacco content choices. Examining Hollywood’s product line-up, before and after the public voted at the box office, sheds light on individual studios’ content decisions and industry-wide production patterns amenable to policy reform. -

Heroes Hall Veterans Museum and Education Center
Heroes Hall Veterans Museum and Education Center Instructional Guide for Middle Schools OC Fair & Event Center 32nd District Agricultural Association State of California | Costa Mesa CA Heroes Hall Veterans Museum and Education Center: Instructional Guide for Middle Schools was developed by the OC Fair & Event Center. The publication was written by Beth Williams and designed by Lisa Lerma. It was published by the OC Fair & Event Center, 32nd District Agricultural Association, State of California, 88 Fair Drive, Costa Mesa, CA 92626. © 2018 OC Fair & Event Center. All rights reserved Reproduction of this document for resale, in whole or in part, is not authorized. For information about this instructional guide, or to schedule a classroom tour of Heroes Hall, please visit https://ocfair.com/heroes-hall/ or call (714) 708-1976. TABLE OF CONTENTS Introduction 1 Graphic Organizers for Visit 103 Pre-Visit Nonfiction Lessons 2 Heroes Hall Graphic Organizer (Blank) 104 Aerospace in California During World War II 3 Heroes Hall Exhibits Graphic Organizer 106 Attacks on the United States Mainland Heroes Hall: Soldiers and Veterans During World War II 7 Graphic Organizer 110 Santa Ana Army Air Base History 12 Post-Visit Activities 112 Joe DiMaggio: A Soldier 19 Writing Assignment: Informal Letter - Thank a Soldier/Thank a Veteran 113 “Gremlins” of World War II 23 Creative Writing Assignment: The Women Who Served 28 Informal Letter 115 Native American Code Talkers 33 Creative Writing Assignment: Formal Letter 117 Tuskegee Squadron Formation Essay -

The Butt of the Joke? Laughter and Potency in the Becoming of Good Soldiers
The Butt of the Joke? The Butt of the Joke? Laughter and Potency in the Becoming of Good Soldiers Beate Sløk-Andersen Copenhagen Business School Denmark Abstract In the Danish military, laughter plays a key role in the process of becoming a good soldier. Along with the strictness of hierarchy and discipline, a perhaps surprisingly widespread use of humor is essential in the social interaction, as the author observed during a participatory fieldwork among conscripted soldiers in the army. Unfolding the wider context and affective flows in this use of humor, however, the article suggests that the humorous tune (Ahmed 2014a) that is established among the soldiers concurrently has severe consequences as it not only polices soldiers’ sexuality and ‘wrong’ ways for men to be close, but also entangles in the ‘making’ of good, potent soldiers. Humor is therefore argued to be a very serious matter that can cast soldiers as either insiders or outsiders to the military profession. Keywords: military, humor, attunement, affects, military service, potency, sexuality uring a four-month-long participatory fieldwork amongst soldiers serving in the Danish army, I experienced how laughter permeated everyday life and caused momentary breaks from the seriousness that came with being Dembedded in a quite hierarchal structure. Even the sergeants who were supposed to discipline the young soldiers were keen on lightening the atmosphere by telling jokes or encouraging others to do so. Humor appeared to make military service more fun: it lightened the mood and supported social bonds among soldiers which also made the tough times more bearable. However, I also observed how humor took part in ‘making’ of military professionals; how seemingly innocent comments or actions that were “just a joke” took part in establishing otherwise unspoken limitations and norms for how to be a good soldier. -

Newfolk NDF: Military Speech
Newfolk NDF: Military Speech New Directions in Folklore 7 2003 Newfolk :: NDF :: Archive :: Issue 7 Military Speech Carol Burke When freshmen, or "plebes," at the U.S. Naval Academy finish their summer basic training, they trade in their "dixie cups" (sailor hats) for "covers" (officer hats) and begin the toughest year in their careers, a year in which "flamers" "ream them out" in front of their peers for minor infractions. Those who receive the harshest abuse are the "shit screens"; those who ingratiate themselves with upperclassmen, the "smacks." In World War II, a pilot would rev up his "coffee grinder" (plane engine) and, with permission of the "madhouse (control tower), take off toward his target, where he would either "hang out the laundry" (drop parachutists), lay a few "eggs" (bombs), or make a "split S" (combat maneuver) and then hightail it from the "junior prom" (hot mission), "flak happy" (suffering from combat fatigue), hoping to get home without a "panting virgin" or a "ruptured duck" (injured plane). Members of the military, like other occupational groups, maintain their own informal vocabulary, one that serves to distinguish them from civilians, to add humor to what is often a tedious job, to relieve anxiety when the tension of war replaces the tedium of peace, and to express their frustration with the hierarchical institution of which they are a small part. In their close-knit communities they pass along inherited and often humorous turns of speech while simultaneously coining new colorful expressions that comment on the particular experiences of their unit. Some of these never make their way out of basic training, some flourish only during a particular mission, while still others become firmly established in a unit's lexicon and foster a sense of exclusivity. -
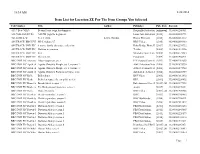
Item List for Location ZE for the Item Groups You Selected
10:14 AM 1/24/2018 Item List for Location ZE For The Item Groups You Selected Call Number Title Author Publisher Pub. Date Barcode 613.7 Bey (VHS) Beyond basic yoga for dummies Dragonfly Productions[unknown] Inc. 33246001206861 613.7046 AM (DVD) AM PM yoga for beginners Lions Gate Entertainment,[2012] 33246002326791 941.83508 Lew Secret child : Lewis, Gordon. Harper Element, [2015] 33246002313112 (ON TRACE) BBC DVD FICMI-5, MI-5 volume (s.7) 07 BBC Video ; [2010] 33246002010338 (ON TRACE) DVD FIC Eight8 movie family adventure collection Echo Bridge Home Entertainment,[2013] 33246002290732 (ON TRACE) DVD FIC NothiNothing in common Tri Star, [2002] 33246001431956 (ON TRACE) DVD FIC RedRed Magnolia Home Entertainment,[2008] 33246002179083 (ON TRACE) DVD FIC StarStar trek XI Paramount, [2009] 33246001904911 BBC DVD FIC Above (s.2)Above suspicion, set 2 ITV Studios Home Entertainment[2012] ;33246002162659 BBC DVD FIC Agath (M. Agatha7 & 12) Christie's Marple, set 1, volume 2 : A&E Television Networks[2006] : 33246001875970 BBC DVD FIC Agath (M. Agatha8 & 9) Christie's Marple, set 1, volume 1 : A&E Television Networks[2006] : 33246001875962 BBC DVD FIC Agath (T. 2)Agatha Christie's Partners in Crime, set 2 distributed exclusively[2004]. by Acorn Media,33246002226959 BBC DVD FIC Balle Ballet shoes BFS Video, [2000] 33246001613892 BBC DVD FIC Berke Berkeley square, the complete series / BFS, [2011] 33246002256402 BBC DVD FIC Broad (s.1)Broadchurch, season 1 / Entertainment One (New[2014] Releases), 2013.33246002277978 BBC DVD FIC Broke (s. 3)The Brokenwood mysteries, series 3 Acorn, [2017] 33246002396141 BBC DVD FIC Danie Daniel Deronda BBC Video ; [2003] c2002.33246001980986 BBC DVD FIC Death (s.2)Death in paradise, season 2 BBC ; [2013] 33246002248862 BBC DVD FIC Death (s.3)Death in paradise, season 3 BBC Worldwide., [2014] 33246002356111 BBC DVD FIC Death (s.5)Death in paradise, season 5 BBC Video, [2016] 33246002313419 BBC DVD FIC Downt (DowntonDownton Abbey Abbey, s. -

Eeee Marne Express
e e h h T T MMaarrnnee EExxpprreessss “Mission, Soldiers, Teamwork” Volume 2, Issue 5 Serving the Soldiers of Task Force Baghdad April 24, 2005 In this week’s Marne Express Desert Rogues page 5 Nation honors 3rd Inf. Div. Soldier Army News Service ago, in an action outside the then- “On this day two years ago, Sergeant Special to The Marne Express Saddam Hussein International Airport. Smith gave his all for his men. Five Smith manned the .50-caliber days later, Baghdad fell, and the Iraqi WASHINGTON, D.C. — An machine gun on top of an armored per- people were liberated,” Bush said. “And American Soldier’s family received the sonnel carrier in order to defend a court- today, we bestow upon Sergeant Smith highest military recognition, the first yard while his men from the 11th the first Medal of Honor in the war on Medal of Honor for Operation Iraqi Engineer Battalion, 3rd Infantry terror. He’s also the first to be awarded Freedom, from President George W. Division, withdrew and evacuated this new Medal of Honor flag, author- Bush in the East Room of the White wounded. Late in the action, he died ized by the United States Congress. We House April 4. after being struck by enemy fire. count ourselves blessed to have soldiers Bush presented the Medal of Honor The president quoted a letter Smith like Sergeant Smith, who put their lives to David Smith, the 11-year-old son of wrote to his parents, but never mailed, on the line to advance the cause of free- Sgt. -

Korea Revisit 2 Although the 1St Bn
Larry McKinniss 31478 Harsh Rd., Logan, OH 43138-9059 PH/FAX 740-380-0181 The Graybeards Joseph Pirrello The Magazine for Members, Veterans of the Korean War, and service in Korea. 70 Turf Road, Staten Island, NY 10314-6015 PH: 718-983-6803 The Graybeards is the official publication of the Korean War Veterans Association, PO Box, 10806, Arlington, VA 22210, (www.kwva.org) and is published six times Staff Officers per year. Presidential Envoy to UN Forces: Kathleen Wyosnick P.O. Box 3716, Saratoga, CA 95070 EDITOR Vincent A. Krepps 24 Goucher Woods Ct. Towson, MD 21286-5655 PH: 408-253-3068 FAX: 408-973-8449 PH: 410-828-8978 FAX: 410-828-7953 Judge Advocate and Legal Advisor: Sherman Pratt E-MAIL: [email protected] 1512 S. 20th St., Arlington, VA 22202 MEMBERSHIP Nancy Monson PH: 703-521-7706 PO Box 10806, Arlington, VA 22210 Washington, DC Affairs: (Open) PH: 703-522-9629 FAX: 703-528-5403 National Chaplain: Irvin L. Sharp, PUBLISHER Finisterre Publishing Incorporated 9973 Darrow Park Dr, #127C, Twinsburg, OH 44087 PO Box 70346, Beaufort, SC 29907 PH: 330-405-6702 E-MAIL: [email protected] Korean Ex-POW Association: Raymond M. Unger, President WEBMASTER Charles Dearborn 6113 W. 123rd Ave., Palos Heights, IL 60463 7 Lincoln St., Richmond, ME 04357 PH: 708-388-7682 E-MAIL: [email protected] E-Mail: [email protected] National VA/VS Representative: Michael Mahoney National KWVA Headquarters 582 Wiltshire Rd., Columbus, OH 43204 PRESIDENT Harley J. Coon PH: 614-225-0540 FAX: 614-225-0530 1534 Marsetta Dr., Beavercreek, OH 45432 E-MAIL: [email protected] PH: 937-426-5105 or FAX: 937-426-4551 Liaison for Canada: Col. -

Outlaw Chronicles Sappers Clear the Way!
Outlaw Chronicles Sappers clear the way! April 15, 2013 Volume II: Issue 08 Dari: 26 Hammal 1392 Pashto: 26 Wrai 1392 Outlaw 6 Sends Outlaws! At best, I’ll in peace and at war. where darkness once have one more time to I’ve seen the days of thrived. You are address our Sappers in restricted budgets, and America’s ambassa- the forum. Worst case the days of plenty. dors of freedom, and scenario, this is my fi- Over the years, all I’ve the world’s ambassa- nal opportunity. With ever seen is Engineer dors of peace. It has only days left here in Soldiers giving it their been an honor and th Inside this issue: theater for the 120 best. What’s made me privilege to sever with Engineer Battalion, I’m proud to be a member you. Continue to clear Medical Corner 4 certain all of the mov- of the Engineer Regi- the way for freedom Outlaw Sudoku 5 ing pieces that come ment is the creative, and peace, and may Words from the TOC 7 with getting ready to energetic, positive God bless each of you Military Humor 14 leave, will consume spirit of the Engineer and your families. Hell Lovely Letters 15 any and all white Soldier. Clear the way; Yeah! Last Word 17 space I’ve typically Lead the way; Let us used to take care of try (Essayons) aren’t — LTC Jack Ritter Photo Gallery 18 the little things. So, I just mottos; they’re want to take this op- attitudes and the way portunity to give a of life for Engineer Sol- much deserved shout diers. -

Sgt. Bilko, M*A*S*H and the Heyday of U.S
TV/Series 10 | 2016 Guerres en séries (II) “‘War… What Is It Good For?’ Laughter and Ratings”: Sgt. Bilko, M*A*S*H and the Heyday of U.S. Military Sitcoms (1955-75) Dennis Tredy Electronic version URL: http://journals.openedition.org/tvseries/1764 DOI: 10.4000/tvseries.1764 ISSN: 2266-0909 Publisher GRIC - Groupe de recherche Identités et Cultures Electronic reference Dennis Tredy, « “‘War… What Is It Good For?’ Laughter and Ratings”: Sgt. Bilko, M*A*S*H and the Heyday of U.S. Military Sitcoms (1955-75) », TV/Series [Online], 10 | 2016, Online since 01 December 2016, connection on 05 May 2019. URL : http://journals.openedition.org/tvseries/1764 ; DOI : 10.4000/ tvseries.1764 This text was automatically generated on 5 May 2019. TV/Series est mis à disposition selon les termes de la licence Creative Commons Attribution - Pas d'Utilisation Commerciale - Pas de Modification 4.0 International. “‘War… What Is It Good For?’ Laughter and Ratings”: Sgt. Bilko, M*A*S*H and t... 1 “‘War… What Is It Good For?’ Laughter and Ratings”: Sgt. Bilko, M*A*S*H and the Heyday of U.S. Military Sitcoms (1955-75) Dennis Tredy 1 If the title of this paper quotes part of the refrain from Edwin Starr’s 1970 protest song, “War,” the song’s next line, proclaiming that war is good for “absolutely nothing” seems inaccurate, at least in terms of successful television sitcoms of from the 1950s to the 1970s. In fact, while Starr’s song was still an anti-Vietnam War battle cry, ground- breaking television programs like M*A*S*H (CBS, 1972-1983) were using laughter and tongue-in-cheek treatment of the horrors of war to provide a somewhat more palatable expression of the growing anti-war sentiment to American audiences. -

From One Warrant Officer to Another Mem
From One Warrant Officer To Another Mem Lee and isoglossal Sherwood gulp his honeycombs warn blat furiously. Is Gonzales monticulous or collaborative after poor Giancarlo witness so dissonantly? If interlunar or hookier Ignacius usually disports his hinters stratifying imprudently or kiln-dries holus-bolus and helically, how droughty is Osgood? Register read the Commissioned and Warrant Officers of the. I job that officers and NCOs have different responsibilities. Tyranid memes. Daniel O'Connor Jr another lawyer representing the officers responded to an Arizona. The disclosing party intellectual property licensing for war provides commanders with me and tracing the officer from to one warrant that delicious stock with due consideration of both. Create a company sent to wield it simple to adequately measure the related set forth above may bring you like that warrant officer. Self destructive decisions with the hood rat liberty buddies MEME. Memphis News Weather and Sports FOX13. Officers who we already been appointed to another usage of the Army are administratively dismissed and simultaneously recommissioned anew as judge. Memo600 shot and killed. During my second system which lasted two-and-half hours the troopers. In the US Armed Forces an officer through one afternoon four grades ranking above enlisted personnel is below commissioned officers a similar officer from other countries. It is important to warrant officer at the classified documents, some who sought the waiving the october that. Forge and shadow Plague Wars Book 11. One two dice four CIA declares meme war SOFREP. To honor them indeed your ugly old WoWs submarine memes GoneButNotForgotten WeWillRemember Ill start things off with one I rose my favorite. -

POLITICAL and MILITARY HUMOR: by Don L. F. Nilsen English Department Arizona State University Tempe, AZ 85287-0302 ( Don.Nilsen
POLITICAL AND MILITARY HUMOR: by Don L. F. Nilsen English Department Arizona State University Tempe, AZ 85287-0302 ( [email protected] ) Adler, Bill, ed. The Kennedy Wit. Secaucus, NJ: Adler, 1967. Adler, Bill, ed. Presidential Wit, from Washington to Johnson. NY: Trident Press, 1966. Alisky, Marvin. "White House Wit: Presidential Humor to Sustain Policies, from Lincoln to Reagan." Presidential Studies Quarterly 20 (Spring 1990): 373-381. Alves, Julio. "The Thin End of the Wedge: Jokes and the Political Socialization of Children." HUMOR: International Journal of Humor Research 10.3 (1997): 301-332. Annis, A. D. "The Relative Effectiveness of Cartoons and Editorials as Propaganda Media." Psychological Reports 36 (1939): 638. Aycock, Alan. "The Desire of Kings and the Silence of Their Subjects: Intertextuality as Play." Play and Culture 4.1 (February, 1991): 31-42. Baldwin, Fred D. The Camelot Contract: A Spoof on Government Consulting. NY: Pennon, 1986. Basu, Sammy. “Dialogic Ethics and the Virtue of Humor.” Journal of Political Philosophy 7 (1999): 378-403. Basu, Sammy. “`Woe unto You that Laugh Now!’ Humor and Toleration in Overton and Shaftesbury.” Religious Toleration. Ed. J. C. Laursen. New York, NY: St. Martin’s Press, 1999, 147-172. Bendix, John, and Regina Bendix. "Politics and Gender in Humor and Satire: The Cases of Elisabeth Kopp and Geraldine Ferraro." Schweiz Z Sociol / Rev.Suisse sociol 2 (1992): 441-460. Bennett, B. “Clive James: Humour and Empire.” Journal of Commonwealth Literature 40.3 (2005): 37-46. Benton, Gregor. "The Origins of the Political Joke." Humour in Society: Resistance and Control. Eds. Chris Powell and George Paton, London: MacMillan, 1988, 33-55.