Military Intelligence Professional Bulletin, April-June 2010
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Nuclear Technology
Nuclear Technology Joseph A. Angelo, Jr. GREENWOOD PRESS NUCLEAR TECHNOLOGY Sourcebooks in Modern Technology Space Technology Joseph A. Angelo, Jr. Sourcebooks in Modern Technology Nuclear Technology Joseph A. Angelo, Jr. GREENWOOD PRESS Westport, Connecticut • London Library of Congress Cataloging-in-Publication Data Angelo, Joseph A. Nuclear technology / Joseph A. Angelo, Jr. p. cm.—(Sourcebooks in modern technology) Includes index. ISBN 1–57356–336–6 (alk. paper) 1. Nuclear engineering. I. Title. II. Series. TK9145.A55 2004 621.48—dc22 2004011238 British Library Cataloguing in Publication Data is available. Copyright © 2004 by Joseph A. Angelo, Jr. All rights reserved. No portion of this book may be reproduced, by any process or technique, without the express written consent of the publisher. Library of Congress Catalog Card Number: 2004011238 ISBN: 1–57356–336–6 First published in 2004 Greenwood Press, 88 Post Road West, Westport, CT 06881 An imprint of Greenwood Publishing Group, Inc. www.greenwood.com Printed in the United States of America The paper used in this book complies with the Permanent Paper Standard issued by the National Information Standards Organization (Z39.48–1984). 10987654321 To my wife, Joan—a wonderful companion and soul mate Contents Preface ix Chapter 1. History of Nuclear Technology and Science 1 Chapter 2. Chronology of Nuclear Technology 65 Chapter 3. Profiles of Nuclear Technology Pioneers, Visionaries, and Advocates 95 Chapter 4. How Nuclear Technology Works 155 Chapter 5. Impact 315 Chapter 6. Issues 375 Chapter 7. The Future of Nuclear Technology 443 Chapter 8. Glossary of Terms Used in Nuclear Technology 485 Chapter 9. Associations 539 Chapter 10. -
![Arxiv:2103.00242V1 [Cs.CL] 27 Feb 2021 Media-Platforms-Peak-Points.Html Aint Ohr.Ti Silsrtdi H Entosof Definitions the in Illustrated Is This Disinfo of Harm](https://docslib.b-cdn.net/cover/1967/arxiv-2103-00242v1-cs-cl-27-feb-2021-media-platforms-peak-points-html-aint-ohr-ti-silsrtdi-h-entosof-de-nitions-the-in-illustrated-is-this-disinfo-of-harm-31967.webp)
Arxiv:2103.00242V1 [Cs.CL] 27 Feb 2021 Media-Platforms-Peak-Points.Html Aint Ohr.Ti Silsrtdi H Entosof Definitions the in Illustrated Is This Disinfo of Harm
A Survey on Stance Detection for Mis- and Disinformation Identification Momchil Hardalov1,2∗ , Arnav Arora1,3 , Preslav Nakov1,4 and Isabelle Augenstein1,3 1CheckStep Research 2Sofia University “St. Kliment Ohridski”, Bulgaria 3University of Copenhagen, Denmark 4Qatar Computing Research Institute, HBKU, Doha, Qatar {momchil, arnav, preslav.nakov, isabelle}@checkstep.com Abstract these notions by Claire Wardle from First Draft,2 misinforma- tion is “unintentional mistakes such as inaccurate photo cap- Detecting attitudes expressed in texts, also known tions, dates, statistics, translations, or when satire is taken as stance detection, has become an important task seriously.”, and disinformation is “fabricated or deliberately for the detection of false information online, be it manipulated audio/visual context, and also intentionally cre- misinformation (unintentionally false) or disinfor- ated conspiracy theories or rumours.”. While the intent to do mation (intentionally false, spread deliberately with harm is very important, it is also very hard to prove. Thus, the malicious intent). Stance detection has been framed vast majority of work has focused on factuality, thus treating in different ways, including: (a) as a component misinformation and disinformation as part of the same prob- of fact-checking, rumour detection, and detecting lem: spread of false information (regardless of whether this is previously fact-checked claims; or (b) as a task in done with harmful intent). This is also the approach we will its own right. While there have -

PDF Van Tekst
Onze Taal. Jaargang 73 bron Onze Taal. Jaargang 73. Genootschap Onze Taal, Den Haag 2004 Zie voor verantwoording: https://www.dbnl.org/tekst/_taa014200401_01/colofon.php Let op: werken die korter dan 140 jaar geleden verschenen zijn, kunnen auteursrechtelijk beschermd zijn. 1 [Nummer 1] Onze Taal. Jaargang 73 4 Vervlakt de intonatie? Ouderen en jongeren met elkaar vergeleken Vincent J. van Heuven - Fonetisch Laboratorium, Universiteit Leiden Ouderen kunnen jongeren vaak maar moeilijk verstaan. Ze praten te snel, te slordig en vooral te monotoon, zo luidt de klacht. Zou dat wijzen op een verandering? Wordt de Nederlandse zinsmelodie inderdaad steeds vlakker? Twee onderzoeken bieden meer duidelijkheid. Ik heb twee zoons in de adolescente leeftijdsgroep, zo tussen de 16 en de 20. Toen ik ze nog dagelijks om me heen had (ze zijn inmiddels technisch gesproken volwassen en het huis uit), mocht ik graag luistervinken als ze in gesprek waren met hun vrienden. Dan viel op dat alle jongens, niet alleen de mijne, snel spraken, met weinig stemverheffing, en vooral met weinig melodie. Het leek wel of ze het erom deden. Een Amerikaanse collega, die elk jaar een paar weken bij mij logeert om zijn Nederlands bij te houden, gaf ongevraagd toe dat hij in het algemeen weinig moeite heeft om Nederlanders te verstaan, behalve dan mijn zoons en hun vrienden. Een paar jaar eerder was ik in een onderzoek beoordelaar van de uitspraak van 120 Nederlanders, in leeftijd variërend van puber tot bejaarde. Mij viel op dat de bejaarden zo veel prettiger waren om naar te luisteren. Niet alleen spraken ze langzamer dan de jongeren, maar vooral maakten ze veel beter gebruik van de mogelijkheden die onze taal biedt om de boodschap met behulp van het stemgebruik te structureren. -
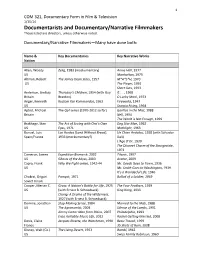
Documentarists and Documentary/Narrative Filmmakers Those Listed Are Directors, Unless Otherwise Noted
1 COM 321, Documentary Form in Film & Television 1/15/14 Documentarists and Documentary/Narrative Filmmakers Those listed are directors, unless otherwise noted. Documentary/Narrative Filmmakers—Many have done both: Name & Key Documentaries Key Narrative Works Nation Allen, Woody Zelig, 1983 (mockumentary) Annie Hall, 1977 US Manhattan, 1979 Altman, Robert The James Dean Story, 1957 M*A*S*H, 1970 US The Player, 1992 Short Cuts, 1993 Anderson, Lindsay Thursday’s Children, 1954 (with Guy if. , 1968 Britain Brenton) O Lucky Man!, 1973 Anger, Kenneth Kustom Kar Kommandos, 1963 Fireworks, 1947 US Scorpio Rising, 1964 Apted, Michael The Up! series (1970‐2012 so far) Gorillas in the Mist, 1988 Britain Nell, 1994 The World is Not Enough, 1999 Brakhage, Stan The Act of Seeing with One’s Own Dog Star Man, 1962 US Eyes, 1971 Mothlight, 1963 Bunuel, Luis Las Hurdes (Land Without Bread), Un Chien Andalou, 1928 (with Salvador Spain/France 1933 (mockumentary?) Dali) L’Age D’Or, 1930 The Discreet Charm of the Bourgeoisie, 1972 Cameron, James Expedition Bismarck, 2002 Titanic, 1997 US Ghosts of the Abyss, 2003 Avatar, 2009 Capra, Frank Why We Fight series, 1942‐44 Mr. Deeds Goes to Town, 1936 US Mr. Smith Goes to Washington, 1939 It’s a Wonderful Life, 1946 Chukrai, Grigori Pamyat, 1971 Ballad of a Soldier, 1959 Soviet Union Cooper, Merian C. Grass: A Nation’s Battle for Life, 1925 The Four Feathers, 1929 US (with Ernest B. Schoedsack) King Kong, 1933 Chang: A Drama of the Wilderness, 1927 (with Ernest B. Schoedsack) Demme, Jonathan Stop Making Sense, -

Michael Moore: a Man on a Mission Or How Far A
Michael Moore: A Man on a Mission or How Far a Reinvigorated Populism Can Take Us Garry Watson (Cineaction 70) My focus in this essay will be on Michael Mooreʼs four documentaries – Roger and Me (1989), The Big One (1997), Bowling for Columbine (2002) and Fahrenheit 9/11 (2004) – with most of my attention being given to the first and third of these, and least to the second. These four films are significant and worth studying for a number of reasons: (i) The size of the audiences they have succeeded in reaching; (ii) the political impact they have had (on which, among other things, see Robert Brent Toplinʼs useful book on Michael Mooreʼs “Fahreneit 9/11”: How One Film Divided A Nation [2006]); (iii) and the extent to which they helped prepare the reception for such recent political documentaries as, for example, Errol Morrisʼs The Fog of War (2004), Mark Achbar and Jennifer Abbottʼs The Corporation (2005), Alex Gibneyʼs Enron: The Smartest Guys in the Room (2005), Eugene Jareckiʼs Why We Fight (2005), David Guggenheimʼs An Inconvenient Truth (2006), and Chris Paineʼs Who Killed the Electric Car? (2006). It may not be redundant to rehearse some of the facts. If Roger and Me was more successful at the box office than any documentary that preceded it, Moore went on to break the same record on two subsequent occasions – first with Bowling for Columbine, then with Fahrenheit 9/11. And as far as the latter is concerned, we get some sense of the excitement that was generated when it first screened in the US by the Foreword that John Berger wrote in 2004 for The Official “Fahrenheit 9/11” Reader (while the film was “still playing in hundreds of theaters across America”1). -

Exploring the Utility of Memes for US Government Influence Campaigns
Exploring the Utility of Memes for U.S. Government Influence Campaigns Vera Zakem, Megan K. McBride, Kate Hammerberg April 2018 Cleared for Public Release DISTRIBUTION STATEMENT A. Approved for public release: distribution unlimited. D RM-2018-U-017433-Final This document contains the best opinion of CNA at the time of issue. It does not necessarily represent the opinion of the sponsor. Distribution DISTRIBUTION STATEMENT A. Approved for public release: distribution unlimited. SPECIFIC AUTHORITY: N00014-16-D-5003 4/17/2018 Request additional copies of this document through [email protected]. Photography Credit: Toy Story meme created via imgflip Meme Generator, available at https://imgflip.com/memegenerator, accessed March 24, 2018. Approved by: April 2018 Dr. Jonathan Schroden, Director Center for Stability and Development Center for Strategic Studies This work was performed under Federal Government Contract No. N00014-16-D-5003. Copyright © 2018 CNA Abstract The term meme was coined in 1976 by Richard Dawkins to explore the ways in which ideas spread between people. With the introduction of the internet, the term has evolved to refer to culturally resonant material—a funny picture, an amusing video, a rallying hashtag—spread online, primarily via social media. This CNA self-initiated exploratory study examines memes and the role that memetic engagement can play in U.S. government (USG) influence campaigns. We define meme as “a culturally resonant item easily shared or spread online,” and develop an epidemiological model of inoculate / infect / treat to classify and analyze ways in which memes have been effectively used in the online information environment. Further, drawing from our discussions with subject matter experts, we make preliminary observations and identify areas for future research on the ways that memes and memetic engagement may be used as part of USG influence campaigns. -

Operation Overlord James Clinton Emmert Louisiana State University and Agricultural and Mechanical College
Louisiana State University LSU Digital Commons LSU Master's Theses Graduate School 2002 Operation overlord James Clinton Emmert Louisiana State University and Agricultural and Mechanical College Follow this and additional works at: https://digitalcommons.lsu.edu/gradschool_theses Part of the Arts and Humanities Commons Recommended Citation Emmert, James Clinton, "Operation overlord" (2002). LSU Master's Theses. 619. https://digitalcommons.lsu.edu/gradschool_theses/619 This Thesis is brought to you for free and open access by the Graduate School at LSU Digital Commons. It has been accepted for inclusion in LSU Master's Theses by an authorized graduate school editor of LSU Digital Commons. For more information, please contact [email protected]. OPERATION OVERLORD A Thesis Submitted to the Graduate Faculty of the Louisiana State University and Agricultural and Mechanical College in partial fulfillment of the requirements for the degree of Master of Arts in Liberal Arts in The Interdepartmental Program in Liberal Arts by James Clinton Emmert B.A., Louisiana State University, 1996 May 2002 ACKNOWLEDGEMENTS This thesis could not have been completed without the support of numerous persons. First, I would never have been able to finish if I had not had the help and support of my wife, Esther, who not only encouraged me and proofed my work, but also took care of our newborn twins alone while I wrote. In addition, I would like to thank Dr. Stanley Hilton, who spent time helping me refine my thoughts about the invasion and whose editing skills helped give life to this paper. Finally, I would like to thank the faculty of Louisiana State University for their guidance and the knowledge that they shared with me. -

Law Enforcement Intelligence: a Guide for State, Local, and Tribal Law Enforcement Agencies Second Edition
U. S. Department of Justice Office of Community Oriented Policing Services Law Enforcement Intelligence: A Guide for State, Local, and Tribal Law Enforcement Agencies Second Edition David L. Carter, Ph.D. School of Criminal Justice, Michigan State University Law Enforcement Intelligence: A Guide for State, Local, and Tribal Law Enforcement Agencies Second Edition David L. Carter, Ph.D. School of Criminal Justice, Michigan State University This project was supported by Cooperative Agreement #2007-CK-WX-K015 by the U.S. Department of Justice Office of Community Oriented Policing Services. Points of view or opinions contained in this publication are those of the author and do not necessarily represent the official position or policies of the U.S. Department of Justice or Michigan State University. References to specific agencies, companies, products, or services should not be considered an endorsement by the author or the U.S. Department of Justice. Rather, the references are illustrations to supplement discussion of the issues. Letter from the COPS Office January 2009 Dear Colleague: This second edition of Law Enforcement Intelligence: A Guide for State, Local, and Tribal Law Enforcement captures the vast changes that have occurred in the 4 years since the first edition of the guide was published in 2004 after the watershed events of September 11, 2001. At that time, there was no Department of Homeland Security, Office of the Director of National Intelligence, Information-Sharing Environment, or Fusion Centers. Since the advent of these new agencies to help fight the war on terror, emphasis has been placed on cooperation and on sharing information among local, state, tribal, and federal agencies. -

The First Americans the 1941 US Codebreaking Mission to Bletchley Park
United States Cryptologic History The First Americans The 1941 US Codebreaking Mission to Bletchley Park Special series | Volume 12 | 2016 Center for Cryptologic History David J. Sherman is Associate Director for Policy and Records at the National Security Agency. A graduate of Duke University, he holds a doctorate in Slavic Studies from Cornell University, where he taught for three years. He also is a graduate of the CAPSTONE General/Flag Officer Course at the National Defense University, the Intelligence Community Senior Leadership Program, and the Alexander S. Pushkin Institute of the Russian Language in Moscow. He has served as Associate Dean for Academic Programs at the National War College and while there taught courses on strategy, inter- national relations, and intelligence. Among his other government assignments include ones as NSA’s representative to the Office of the Secretary of Defense, as Director for Intelligence Programs at the National Security Council, and on the staff of the National Economic Council. This publication presents a historical perspective for informational and educational purposes, is the result of independent research, and does not necessarily reflect a position of NSA/CSS or any other US government entity. This publication is distributed free by the National Security Agency. If you would like additional copies, please email [email protected] or write to: Center for Cryptologic History National Security Agency 9800 Savage Road, Suite 6886 Fort George G. Meade, MD 20755 Cover: (Top) Navy Department building, with Washington Monument in center distance, 1918 or 1919; (bottom) Bletchley Park mansion, headquarters of UK codebreaking, 1939 UNITED STATES CRYPTOLOGIC HISTORY The First Americans The 1941 US Codebreaking Mission to Bletchley Park David Sherman National Security Agency Center for Cryptologic History 2016 Second Printing Contents Foreword ................................................................................ -

MILITARY INTELLIGENCE PB 34-09-2 Volume 35 Number 2 April - June 2009
MIPB April - June 2009 PB 34-O9-2 Operations in OEF Afghanistan FROM THE EDITOR In this issue, three articles offer perspectives on operations in Afghanistan. Captain Nenchek dis- cusses the philosophy of the evolving insurgent “syndicates,” who are working together to resist the changes and ideas the Coalition Forces bring to Afghanistan. Captain Beall relates his experiences in employing Human Intelligence Collection Teams at the company level in both Iraq and Afghanistan. Lieutenant Colonel Lawson provides a look into the balancing act U.S. Army chaplains as non-com- batants in Afghanistan are involved in with regards to Information Operations. Colonel Reyes discusses his experiences as the MNF-I C2 CIOC Chief, detailing the problems and solutions to streamlining the intelligence effort. First Lieutenant Winwood relates her experiences in integrating intelligence support into psychological operations. From a doctrinal standpoint, Lieutenant Colonels McDonough and Conway review the evolution of priority intelligence requirements from a combined operations/intelligence view. Mr. Jack Kem dis- cusses the constructs of assessment during operations–measures of effectiveness and measures of per- formance, common discussion threads in several articles in this issue. George Van Otten sheds light on a little known issue on our southern border, that of the illegal im- migration and smuggling activities which use the Tohono O’odham Reservation as a corridor and offers some solutions for combined agency involvement and training to stem the flow. Included in this issue is nomination information for the CSM Doug Russell Award as well as a biogra- phy of the 2009 winner. Our website is at https://icon.army.mil/ If your unit or agency would like to receive MIPB at no cost, please email [email protected] and include a physical address and quantity desired or call the Editor at 520.5358.0956/DSN 879.0956. -

Is America Prepared for Meme Warfare?
EN MEMES Is America Prepared for Meme Warfare? Jacob Siegel Jan 31 2017, 10:00am Memes function like IEDs. Memes, as any alt-right Pepe sorcerer will tell you, are not just frivolous entertainment. They are magic, the stu by which reality is made and manipulated. What's perhaps surprising is that this view is not so far o from one within the US defense establishment, where a growing body of research explores how memes can be used to win wars. This recent election proved that memes, some of which have been funded by politically motivated millionaires and foreign governments, can be potent weapons, but they pose a particular challenge to a superpower like the United States. Memes appear to function like the IEDs of information warfare. They are natural tools of an insurgency; great for blowing things up, but likely to sabotage the desired eects when handled by the larger actor in an asymmetric conict. Just think back to the NYPD's hashtag SHARE TWEET EN boondoggle for an example of how quickly things can go wrong when big institutions try to control messaging on the internet. That doesn't mean research should be abandoned or memes disposed of altogether, but as the NYPD case and other examples show, the establishment isn't really built for meme warfare. For a number of reasons, memetics are likely to become more important in the new White House. To understand this issue, we rst have to dene what a meme is because that is a subject of some controversy and confusion in its own right. -

Acronyms Abbreviations &Terms
Acronyms Abbreviations &Terms A Capability Assurance Job Aid FEMA P-524 / July 2009 FEMA Acronyms Abbreviations and Terms Produced by the National Preparedness Directorate, National Integration Center, Incident Management Systems Integration Division Please direct requests for additional copies to: FEMA Publications (800) 480-2520 Or download the document from the Web: www.fema.gov/plan/prepare/faat.shtm U.S. Department of Homeland Security Federal Emergency Management Agency The FEMA Acronyms, Abbreviations & Terms (FAAT) List is not designed to be an authoritative source, merely a handy reference and a living document subject to periodic updating. Inclusion recognizes terminology existence, not legitimacy. Entries known to be obsolete (see new “Obsolete or Replaced” section near end of this document) are included because they may still appear in extant publications and correspondence. Your comments and recommendations are welcome. Please electronically forward your input or direct your questions to: [email protected] Please direct requests for additional copies to: FEMA Publications (800) 480-2520 Or download the document from the Web: www.fema.gov/plan/prepare/faat.shtm 2SR Second Stage Review ABEL Agent Based Economic Laboratory 4Wd Four Wheel Drive ABF Automatic Broadcast Feed A 1) Activity of Isotope ABHS Alcohol Based Hand Sanitizer 2) Ampere ABI Automated Broker Interface 3) Atomic Mass ABIH American Board of Industrial Hygiene A&E Architectural and Engineering ABIS see IDENT A&FM Aviation and Fire Management ABM Anti-Ballistic Missile