Enhanced Mitigation Experience Toolkit 5.5 User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -
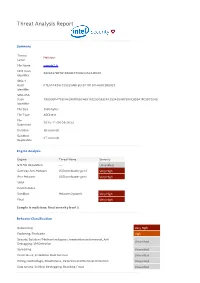
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Vmware Vrealize Configuration Manager Installation Guide Vrealize Configuration Manager 5.8
VMware vRealize Configuration Manager Installation Guide vRealize Configuration Manager 5.8 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document, see http://www.vmware.com/support/pubs. EN-001815-00 vRealize Configuration Manager Installation Guide You can find the most up-to-date technical documentation on the VMware Web site at: Copyright http://www.vmware.com/support/ The VMware Web site also provides the latest product updates. If you have comments about this documentation, submit your feedback to: [email protected] © 2006–2015 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. VMware products are covered by one or more patents listed at http://www.vmware.com/go/patents. VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com 2 VMware, Inc. Contents About This Book 5 Preparing to Install VCM 7 Typical or Advanced Installation 7 VCM Installation Configurations 8 Create VCM Domain Accounts 8 VCM Account Configuration 9 VCM Administrator Account 10 VCM User Accounts 10 Service Accounts 10 Network Authority Account 11 ECMSRSUser Account 12 SQL Server Permissions and Constructs 12 Gather Supporting Software -

Detecting and Analyzing Insecure Component Integration
Taeho Kwon December 2011 Computer Science Detecting and Analyzing Insecure Component Integration Abstract Component technologies have been widely adopted for designing and engineering software ap- plications and systems, which dynamically integrate software components to achieve desired func- tionalities. Engineering software in a component-based style has significant benefits, such as im- proved programmer productivity and software reliability. To support component integration, oper- ating systems allow an application to dynamically load and use a component. Although developers have frequently utilized such a system-level mechanism, programming errors can lead to insecure component integration and serious security vulnerabilities. The security and reliability impact of component integration has not yet been much explored. This dissertation systematically investigates security issues in dynamic component integration and their impact on software security. On the conceptual level, we formulate two types of insecure component integration—unsafe component loading and insecure component usage—and present practical, scalable techniques to detect and analyze them. Our techniques operate directly on soft- ware binaries and do not require source code. On the practical level, we have used them to discover new vulnerabilities in popular, real-world software, and show that insecure component integration is prevalent and can be exploited by attackers to subvert important software and systems. Our research has had substantial practical impact and helped -

Automated Malware Analysis Report For
ID: 310931 Sample Name: 44S5D444F55G8222Y55UU44S4S.vbs Cookbook: default.jbs Time: 07:32:12 Date: 07/11/2020 Version: 31.0.0 Red Diamond Table of Contents Table of Contents 2 Analysis Report 44S5D444F55G8222Y55UU44S4S.vbs 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Startup 4 Malware Configuration 4 Yara Overview 4 Sigma Overview 4 Signature Overview 4 AV Detection: 5 Data Obfuscation: 5 Persistence and Installation Behavior: 5 Malware Analysis System Evasion: 5 HIPS / PFW / Operating System Protection Evasion: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 7 URLs 7 Domains and IPs 8 Contacted Domains 8 Contacted URLs 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 9 General Information 9 Simulations 10 Behavior and APIs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 11 General 11 File Icon 12 Network Behavior 12 TCP Packets 12 HTTP Request Dependency Graph 12 HTTP Packets 12 Code Manipulations 13 Statistics 13 Behavior 13 System Behavior 14 Analysis Process: wscript.exe PID: 6124 Parent PID: 3388 14 Copyright null 2020 Page 2 of 15 General 14 File Activities 14 File Created 14 File Written 14 Registry Activities 15 Analysis Process: wscript.exe PID: 5560 Parent PID: 6124 15 General 15 File Activities 15 Disassembly 15 Code Analysis 15 Copyright null 2020 Page 3 of -

Curriculum Vitae Di Tommaso Cucinotta
Curriculum Vitae: Prof. Tommaso Cucinotta Personal data Birth date and place: April 1974, Potenza (Italy) Phone: +39 (0)50 882 028 Skype Id: t.cucinotta E-mail: Home page: http:// retis . santannapisa .it/~tommaso Current status Dec 2015 to date: Associate Professor at the Real-Time Systems Laboratory (ReTiS) of Scuola Superiore Sant'Anna RESEARCH TOPICS & COMPETENCIES ❑ Real-time and reliable NoSQL Database systems for cloud services ❑ Adaptive resource management and scheduling in Cloud Computing & Network Function Virtualization infrastructures ❑ Artificial Intelligence and Machine Learning to support Data Center Operations in Cloud & NFV infrastructures ❑ Platforms for real-time data streaming and analytics ❑ Quality of service control for adaptive soft real-time applications, including multimedia and IMS systems ❑ Operating Systems for real-time and embedded applications and many-core and massively distributed systems ❑ Trusted computing and confidentiality in cloud computing ❑ Smart-cards: interoperability, protocols and architectures ❑ Digital signatures, biometrics identification, multicast security Experience highlights (details below) ❑ 7 Granted and 25 Filed EU and US Patents in the areas of security, resource management and scheduling ❑ 25 International Journal Publications, including IEEE Transaction on Computers, IEEE Transaction on Industrial Informatics and ACM Transactions on Embedded and Computing Systems ❑ 65 International Conference and Workshop Peer-reviewed Publications and 13 Book Chapters ❑ 3 EU Projects scientific -

Microsoft Windows Server 2008 PKI and Deploying the Ncipher Hardware Security Module
This is a joint nCipher and IdentIT authored whitepaper Microsoft Windows Server 2008 PKI and Deploying the nCipher Hardware Security Module Abstract This paper discusses the benefits that are unique to deploying the integrated solution of the Windows Server 2008 PKI and the nCipher nShield and netHSM hardware security modules (HSM). This includes the essential concepts and technologies used to deploy a PKI and the best practice security and life cycle key management features provided by nCipher HSMs.. MicrosofT WIndoWs server 2008 PKI and dePloyIng The nCipher hardWare seCurity Module Introduction...............................................................................................................................................................................................3 PKI – A Crucial Component to Securing e-commerce ......................................................................................................................4 Microsoft Windows Server 2008 ...............................................................................................................................................................4 nCipher Hardware Security Modules ......................................................................................................................................................4 Best.Practice.Security.–.nCipher.HSMs.with.Windows.Server.2008.PKI................................................................................5 Overview...............................................................................................................................................................................................................5 -

What Are Kernel-Mode Rootkits?
www.it-ebooks.info Hacking Exposed™ Malware & Rootkits Reviews “Accessible but not dumbed-down, this latest addition to the Hacking Exposed series is a stellar example of why this series remains one of the best-selling security franchises out there. System administrators and Average Joe computer users alike need to come to grips with the sophistication and stealth of modern malware, and this book calmly and clearly explains the threat.” —Brian Krebs, Reporter for The Washington Post and author of the Security Fix Blog “A harrowing guide to where the bad guys hide, and how you can find them.” —Dan Kaminsky, Director of Penetration Testing, IOActive, Inc. “The authors tackle malware, a deep and diverse issue in computer security, with common terms and relevant examples. Malware is a cold deadly tool in hacking; the authors address it openly, showing its capabilities with direct technical insight. The result is a good read that moves quickly, filling in the gaps even for the knowledgeable reader.” —Christopher Jordan, VP, Threat Intelligence, McAfee; Principal Investigator to DHS Botnet Research “Remember the end-of-semester review sessions where the instructor would go over everything from the whole term in just enough detail so you would understand all the key points, but also leave you with enough references to dig deeper where you wanted? Hacking Exposed Malware & Rootkits resembles this! A top-notch reference for novices and security professionals alike, this book provides just enough detail to explain the topics being presented, but not too much to dissuade those new to security.” —LTC Ron Dodge, U.S. -

Download “The Spy Who Encrypted Me” Case Study
April, 2020 APT41 The Spy Who Encrypted Me Contents APT41 – A spy who steals or a thief who spies ......................................................... 3 The investigation .................................................................................................. 3 The base .......................................................................................................... 4 The toolkit ........................................................................................................ 5 The point of entry .............................................................................................. 6 The initial vector of compromise .......................................................................... 8 Indicators of Compromise .................................................................................... 10 References ......................................................................................................... 11 244 Fifth Avenue, Suite 2035, New York, NY 10001 LIFARS.com (212) 222-7061 [email protected] APT41 – A SPY WHO STEALS OR A THIEF WHO SPIES An advanced persistent threat (“APT”) is, typically, either a nation-state actor and aims at benefiting its state through sabotage, espionage, or industrial espionage; or a cybercriminal and its aims are to steal money through theft, fraud, ransom or blackmail. The Chinese-based threat actor APT41 blurs the lines: known to have run financially- motivated operations against the videogame industry as early as 2012, it got its notoriety in 2013 when -

Invisimole: the Hidden Part of the Story Unearthing Invisimole’S Espionage Toolset and Strategic Cooperations
ESET Research white papers TLP: WHITE INVISIMOLE: THE HIDDEN PART OF THE STORY UNEARTHING INVISIMOLE’S ESPIONAGE TOOLSET AND STRATEGIC COOPERATIONS Authors: Zuzana Hromcová Anton Cherepanov TLP: WHITE 2 InvisiMole: The hidden part of the story CONTENTS 1 EXECUTIVE SUMMARY � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 2 ATTACKS AND INVESTIGATION � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 4 2.1 InvisiMole’s toolset ������������������������������������������������������������������������������������������������������������������������ 5 2.2 Cooperation between InvisiMole and Gamaredon . 5 3 BUILDING BLOCKS � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � � 6 3.1 Structure ������������������������������������������������������������������������������������������������������������������������������������������6 3.1.1 InvisiMole blobs . 6 3.1.2 Execution guardrails with DPAPI ���������������������������������������������������������������������������������7 3.2 Payload ��������������������������������������������������������������������������������������������������������������������������������������������8 3.2.1 TCP downloader ��������������������������������������������������������������������������������������������������������������9 3.2.2 DNS downloader . 9 3.2.3 RC2CL backdoor �������������������������������������������������������������������������������������������������������������13