Nessus 8.3 User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CIS Debian Linux 7 Benchmark V1.0.0 - 12-31-2015
CIS Debian Linux 7 Benchmark v1.0.0 - 12-31-2015 http://benchmarks.cisecurity.org The CIS Security Benchmarks division provides consensus-oriented information security products, services, tools, metrics, suggestions, and recommendations (the “SB Products”) as a public service to Internet users worldwide. Downloading or using SB Products in any way signifies and confirms your acceptance of and your binding agreement to these CIS Security Benchmarks Terms of Use. CIS SECURITY BENCHMARKS TERMS OF USE BOTH CIS SECURITY BENCHMARKS DIVISION MEMBERS AND NON-MEMBERS MAY: Download, install, and use each of the SB Products on a single computer, and/or Print one or more copies of any SB Product that is in a .txt, .pdf, .doc, .mcw, or .rtf format, but only if each such copy is printed in its entirety and is kept intact, including without limitation the text of these CIS Security Benchmarks Terms of Use. UNDER THE FOLLOWING TERMS AND CONDITIONS: SB Products Provided As Is. CIS is providing the SB Products “as is” and “as available” without: (1) any representations, warranties, or covenants of any kind whatsoever (including the absence of any warranty regarding: (a) the effect or lack of effect of any SB Product on the operation or the security of any network, system, software, hardware, or any component of any of them, and (b) the accuracy, utility, reliability, timeliness, or completeness of any SB Product); or (2) the responsibility to make or notify you of any corrections, updates, upgrades, or fixes. Intellectual Property and Rights Reserved. You are not acquiring any title or ownership rights in or to any SB Product, and full title and all ownership rights to the SB Products remain the exclusive property of CIS. -

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

1 Introduction
Technical report, IDE1202, February 2012 Enhancing Network Security in Linux Environment Master Thesis in Computer Network Engineering By Ali Mohammed, Sachin Sama and Majeed Mohammed School of Information Science, Computer and Electrical Engineering Halmstad University i Enhancing Network Security in Linux Environment Master Thesis in Computer Network Engineering School of Information Science, Computer and Electrical Engineering Halmstad University Box 823, S-301 18 Halmstad, Sweden February 2012 ii Preface First of all, we would like to express our sincere gratitude to our Supervisor Philip Heimer and Professor Tony Larsson for their supervision and assistance in the entire thesis work. We are also thankful to IDE department, Halmstad University for providing this opportunity to complete this thesis. Ali Mohammed Sachin Sama Majeed Mohammed iii iv Abstract Designing a secured network is the most important task in any enterprise or organization development. Securing a network mainly involves applying policies and procedures to protect different network devices from unauthorized access. Servers such as web servers, file servers, mail servers, etc., are the important devices in a network. Therefore, securing these servers is the first and foremost step followed in every security implementation mechanism. To implement this, it is very important to analyse and study the security mechanisms provided by the operating system. This makes it easier for security implementation in a network. This thesis work demonstrates the tasks needed to enhance the network security in Linux environment. The various security modules existing in Linux makes it different from other operating systems. The security measures which are mainly needed to enhance the system security are documented as a baseline for practical implementation. -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Access Control Framework
This material is based on work supported by the National Science Foundation under Grant No. 0802551 Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author (s) and do not necessarily reflect the views of the National Science Foundation C5L1S1 When working for an institution as a Linux Administrator, you may be required to protect certain information based on its sensitivity. For instance, most organizations will have an internal network in which data contained in certain directories or drives are made public—employees can access the contents. However, certain kinds of information such as employee salaries, classified research, secret prototypes, health information, military secrets, and private communications are considered highly sensitive and are usually restrictedU the from everyone except very few people authorized to access the data. In this lesson, we will explore processes, tools, and control lists that make it possible to limit access to sensitive data on a Linux-based system. Understanding this topic is important for any system administrator configuring systems in the workplace that require access control mechanisms. C5L1S2 You should know what will be expected of you when you complete this lesson. These expectations are presented as objectives. Objectives are short statements of expectations that tell you what you must be able to do, perform, learn, or adjust after reviewing the lesson. Lesson Objective: U the Given the need to secure a Linux server, the student will recommend a set of standard Linux tools such as PAM, Access Control Lists, and TCP Wrappers to effectively secure a Linux system and demonstrate the use of one set of tools for system lock-down. -

My Name Is Robert Kudyba and I Am the System Administrator for The
My name is Robert Kudyba and I am the System Administrator for the Department of Computer Science here at Fordham University and a recent graduate of the Master’s in Cybersecurity. The lab will require you to install VirtualBox with Ubuntu preferable from osboxes.org. The commands listed in the lab will assume you have installed this image. Any Ubuntu version will work but if you installed from ubuntu.com then you will have to substitute the username you created for every place I reference osboxes. If you use Kali, you will be using the root user and there may be other issues as I’ve only confirmed everything works on Ubuntu. 1 In this lab, I will be gong over Linux remote access protocols Telnet and SSH, providing a history, the various encryption methods used, the concept of security through obscurity, a program called Fail2ban, how to use a Certificate Authority in OpenSSH, TCPWrapper, and Port Knocking. 2 • Telnet is a simple, text-based network protocol that is used for accessing remote computers over TCP/IP networks like the Internet. Telnet was created and launched in 1969. • Prior to telnet, you had to physically walk to a server in order to access its data. This meant, among other things, that you had to spend some time arriving at the server's location and then you had to wait for your turn to work with the server. Even if the server had the hardware power to do multiple things at the same time, you were blocked from using if someone was before you so you had to wait for others to finish their work first. -

Nessus 8.11 User Guide
Nessus 8.11.x User Guide Last Updated: October 29, 2020 Table of Contents Welcome to Nessus 8.11.x 13 Get Started with Nessus 16 Navigate Nessus 18 System Requirements 19 Hardware Requirements 20 Software Requirements 23 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Manage SSL Certificates 33 Custom SSL Certificates 34 SSL Client Certificate Authentication 35 Create a New Custom CA and Server Certificate 36 Upload a Custom CA Certificate 38 Add a Root CA 39 Create Nessus SSL Certificates for Login 40 Enable Connections with Smart Card or CAC Card 43 Connect with Certificate or Card Enabled Browser 44 Copyright © 2020 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Install Nessus and Nessus Agents 46 Download Nessus 47 Install Nessus 49 Install Nessus on Linux 50 Install Nessus on Windows 52 Install Nessus on Mac OS X 54 Install Nessus Agents 56 Retrieve the Linking Key 57 Install a Nessus Agent on Linux 58 Install a Nessus Agent on Windows 62 Install a Nessus Agent on Mac OS X 66 Link an Agent to Nessus Manager 70 Upgrade Nessus and Nessus Agents 73 Upgrade Nessus 74 Upgrade from Evaluation 75 Update Nessus Software 76 Upgrade Nessus on Linux 79 Upgrade Nessus on Windows 80 Upgrade Nessus on Mac OS X 81 Upgrade a Nessus Agent 82 Downgrade Nessus Software 85 Configure Nessus 86 Install Nessus Essentials, Professional, or Manager 87 Link to Tenable.io 89 Copyright © 2020 Tenable, Inc. -

I386-Engine™ Technical Manual
i386-Engine™ C/C++ Programmable, 32-bit Microprocessor Module Based on the Intel386EX Technical Manual 1950 5 th Street, Davis, CA 95616, USA Tel: 530-758-0180 Fax: 530-758-0181 Email: [email protected] http://www.tern.com Internet Email: [email protected] http://www.tern.com COPYRIGHT i386-Engine, VE232, A-Engine, A-Core, C-Engine, V25-Engine, MotionC, BirdBox, PowerDrive, SensorWatch, Pc-Co, LittleDrive, MemCard, ACTF, and NT-Kit are trademarks of TERN, Inc. Intel386EX and Intel386SX are trademarks of Intel Coporation. Borland C/C++ are trademarks of Borland International. Microsoft, MS-DOS, Windows, and Windows 95 are trademarks of Microsoft Corporation. IBM is a trademark of International Business Machines Corporation. Version 2.00 October 28, 2010 No part of this document may be copied or reproduced in any form or by any means without the prior written consent of TERN, Inc. © 1998-2010 1950 5 th Street, Davis, CA 95616, USA Tel: 530-758-0180 Fax: 530-758-0181 Email: [email protected] http://www.tern.com Important Notice TERN is developing complex, high technology integration systems. These systems are integrated with software and hardware that are not 100% defect free. TERN products are not designed, intended, authorized, or warranted to be suitable for use in life-support applications, devices, or systems, or in other critical applications. TERN and the Buyer agree that TERN will not be liable for incidental or consequential damages arising from the use of TERN products. It is the Buyer's responsibility to protect life and property against incidental failure. TERN reserves the right to make changes and improvements to its products without providing notice. -

Absolute BSD—The Ultimate Guide to Freebsd Table of Contents Absolute BSD—The Ultimate Guide to Freebsd
Absolute BSD—The Ultimate Guide to FreeBSD Table of Contents Absolute BSD—The Ultimate Guide to FreeBSD............................................................................1 Dedication..........................................................................................................................................3 Foreword............................................................................................................................................4 Introduction........................................................................................................................................5 What Is FreeBSD?...................................................................................................................5 How Did FreeBSD Get Here?..................................................................................................5 The BSD License: BSD Goes Public.......................................................................................6 The Birth of Modern FreeBSD.................................................................................................6 FreeBSD Development............................................................................................................7 Committers.........................................................................................................................7 Contributors........................................................................................................................8 Users..................................................................................................................................8 -
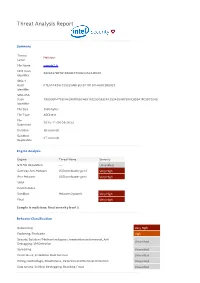
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

DOS Virtualized in the Linux Kernel
DOS Virtualized in the Linux Kernel Robert T. Johnson, III Abstract Due to the heavy dominance of Microsoft Windows® in the desktop market, some members of the software industry believe that new operating systems must be able to run Windows® applications to compete in the marketplace. However, running applications not native to the operating system generally causes their performance to degrade significantly. When the application and the operating system were written to run on the same machine architecture, all of the instructions in the application can still be directly executed under the new operating system. Some will only need to be interpreted differently to provide the required functionality. This paper investigates the feasibility and potential to speed up the performance of such applications by including the support needed to run them directly in the kernel. In order to avoid the impact to the kernel when these applications are not running, the needed support was built as a loadable kernel module. 1 Introduction New operating systems face significant challenges in gaining consumer acceptance in the desktop marketplace. One of the first realizations that must be made is that the majority of this market consists of non-technical users who are unlikely to either understand or have the desire to understand various technical details about why the new operating system is “better” than a competitor’s. This means that such details are extremely unlikely to sway a large amount of users towards the operating system by themselves. The incentive for a consumer to continue using their existing operating system or only upgrade to one that is backwards compatible is also very strong due to the importance of application software. -

Enclave Security and Address-Based Side Channels
Graz University of Technology Faculty of Computer Science Institute of Applied Information Processing and Communications IAIK Enclave Security and Address-based Side Channels Assessors: A PhD Thesis Presented to the Prof. Stefan Mangard Faculty of Computer Science in Prof. Thomas Eisenbarth Fulfillment of the Requirements for the PhD Degree by June 2020 Samuel Weiser Samuel Weiser Enclave Security and Address-based Side Channels DOCTORAL THESIS to achieve the university degree of Doctor of Technical Sciences; Dr. techn. submitted to Graz University of Technology Assessors Prof. Stefan Mangard Institute of Applied Information Processing and Communications Graz University of Technology Prof. Thomas Eisenbarth Institute for IT Security Universit¨atzu L¨ubeck Graz, June 2020 SSS AFFIDAVIT I declare that I have authored this thesis independently, that I have not used other than the declared sources/resources, and that I have explicitly indicated all material which has been quoted either literally or by content from the sources used. The text document uploaded to TUGRAZonline is identical to the present doctoral thesis. Date, Signature SSS Prologue Everyone has the right to life, liberty and security of person. Universal Declaration of Human Rights, Article 3 Our life turned digital, and so did we. Not long ago, the globalized commu- nication that we enjoy today on an everyday basis was the privilege of a few. Nowadays, artificial intelligence in the cloud, smartified handhelds, low-power Internet-of-Things gadgets, and self-maneuvering objects in the physical world are promising us unthinkable freedom in shaping our personal lives as well as society as a whole. Sadly, our collective excitement about the \new", the \better", the \more", the \instant", has overruled our sense of security and privacy.