Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

Towards a Verified Range Analysis for Javascript Jits
Towards a Verified Range Analysis for JavaScript JITs Fraser Brown John Renner Andres Nötzli Stanford, USA UC San Diego, USA Stanford, USA Sorin Lerner Hovav Shacham Deian Stefan UC San Diego, USA UT Austin, USA UC San Diego, USA Abstract Earlier this year, Google’s Threat Analysis Group identi- We present VeRA, a system for verifying the range analysis fied websites, apparently aimed at people “born in a certain pass in browser just-in-time (JIT) compilers. Browser devel- geographic region” and “part of a certain ethnic group,” that opers write range analysis routines in a subset of C++, and would install a malicious spyware implant on any iPhone verification developers write infrastructure to verify custom used to visit them. Two bugs exploited in this campaign, analysis properties. Then, VeRA automatically verifies the according to analysis by Google’s Project Zero [41, 68], were range analysis routines, which browser developers can in- in the JIT component of Safari’s JavaScript engine [5, 34]. tegrate directly into the JIT. We use VeRA to translate and The JavaScript JITs shipped in modern browsers are ma- verify Firefox range analysis routines, and it detects a new, ture, sophisticated systems developed by compilers experts. confirmed bug that has existed in the browser for six years. Yet bugs in JIT compilers have emerged in recent months as the single largest threat to Web platform security, and the CCS Concepts: • Security and privacy ! Browser se- most dangerous attack surface of Web-connected devices. curity; • Software and its engineering ! Just-in-time Unlike other compilers, browser JITs are exposed to adver- compilers; Software verification and validation; Domain sarial program input. -

Platform Support Matrix for SAP Business
Platform Support Matrix PUBLIC SAP Business One Document Version: 1.28 – 2021-05-07 SAP Business One Platform Support Matrix Release 9.0 and higher Typographic Conventions Type Style Description Example Words or characters quoted from the screen. These include field names, screen titles, pushbuttons labels, menu names, menu paths, and menu options. Textual cross-references to other documents. Example Emphasized words or expressions. EXAMPLE Technical names of system objects. These include report names, program names, transaction codes, table names, and key concepts of a programming language when they are surrounded by body text, for example, SELECT and INCLUDE. Example Output on the screen. This includes file and directory names and their paths, messages, names of variables and parameters, source text, and names of installation, upgrade and database tools. Example Exact user entry. These are words or characters that you enter in the system exactly as they appear in the documentation. <Example> Variable user entry. Angle brackets indicate that you replace these words and characters with appropriate entries to make entries in the system. EXAMPLE Keys on the keyboard, for example, F2 or ENTER. PUBLIC © 2021 SAP SE or an SAP affiliate company. All SAP Business One Platform Support Matrix 2 rights reserved. Typographic Conventions Document History Version Date Change 1.0 2014-02-12 Release Version 1.01 2014-05-08 SAP Note 1787431 link added on XL Reporter platform support restrictions 1.02 2014-07-08 SAP Business One 9.1 added to the overview -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -

Ricki-Lee - Edge of Glory (LIVE Piano Version)
ai - edgeum - Ricki-Lee - Edge Of Glory (LIVE Piano Version) Select a Language - Microsoft Edge, now available on Android, creates one continuous browsing experience for Windows 10 users across their devices. Content and data sync seamlessly in the background, so users can browse across devices, without skipping a beat. Business Grants For Scottish Entrepreneurs | Scottish EDGE Inspired by the NAAEE mission, Microsoft Edge worked with the NAAEE to develop a web experience for innovators in environmental education and literacy to demonstrate the positive impact they have h... Microsoft Support My saves. My interests / All saves 0. Recipes Images Videos News My places. Collections + New. Help. All saves. 1/2. See all of your saved results, starting with the most recent. Next Close. All saves. Moderate. You haven't saved anything yet. From the Bing search results, select the to save a result here. Samsung Galaxy S7 and S7 edge - The Official Samsung ... The Microsoft Edge DevTools are built with TypeScript, powered by open source, optimized for modern front-end workflows, and now available as a standalone Windows 10 app in the Microsoft Store! For more on the latest features, check out DevTools in the latest update of Windows 10 (EdgeHTML 18). Test ... 2018 Ford Edge SUV | Sporty Utility for Unstoppable ... Noun. They peered over the edge of the roof. The fabric was frayed at the edge. He made us all nervous by standing so close to the edge of the cliff. She sat on the edge of the counter, swinging her legs. the edge of an ax His voice had a sarcastic edge. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -
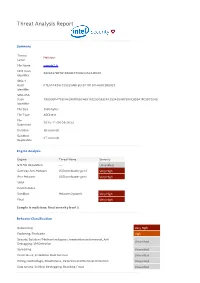
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

(RUNTIME) a Salud Total
Windows 7 Developer Guide Published October 2008 For more information, press only: Rapid Response Team Waggener Edstrom Worldwide (503) 443-7070 [email protected] Downloaded from www.WillyDev.NET The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This guide is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form, by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft. Microsoft may have patents, patent applications, trademarks, copyrights or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place or event is intended or should be inferred. -

Download Har File Viewer
download har file viewer Download har file viewer. Если вы не знаете, как получить HAR-файл, ознакомьтесь с инструкцией на странице загрузки для трех самых распространенных браузеров: Chrome, Firefox и Internet Explorer. Нажмите кнопку выбора файла. Выберите HAR-файл для анализа. Воспользуйтесь ей, чтобы выбрать файл для анализа. Записи могут быть показаны вместе или с разбивкой по страницам. Временные метки записей в таблице могут быть относительными или абсолютными. В первом режиме метки, которые соответствуют каждой записи, располагаются на временной шкале обработки страницы, а во втором метка каждой записи занимает всю ширину столбца. Относительный режим используется только при группировке записей по страницам. – полезный инструмент, позволяющий выполнять сложный поиск в HAR-записях. Самый простой способ поиска – ввести несколько поисковых слов, например [получить диск]. В результате будут найдены записи, содержащие все эти слова в ответе и запросе. Обратите внимание, что словосочетания в кавычках обрабатываются как единый поисковый запрос, поэтому для запроса [неделя "количество событий"] будут показаны результаты, где есть фраза "количество событий". Кроме того, поисковые запросы могут быть представлены парами "поле – поисковая фраза", например [requst.url:поисковая_фраза request.method:поисковая_фраза response.status:поисковая_фраза]. Для более сложного поиска можно использовать операторы, создавать группы и указывать поля. Оператор влияет на непосредственно следующую за ним поисковую фразу, изменяя способ ее поиска в целой группе или запросе. Поддерживаемые операторы: & : оператор по умолчанию, выполняющий операцию AND для результатов следующего поискового запроса и результатов всех предыдущих операций. | : выполняет операцию OR для результатов следующего поискового запроса и результатов всех предыдущих операций. ^ : выполняет операцию XOR для результатов следующего поискового запроса и результатов всех предыдущих операций. - : исключает результаты следующего поискового запроса. Выберите HAR-файл. -

Automated Malware Analysis Report For
ID: 310931 Sample Name: 44S5D444F55G8222Y55UU44S4S.vbs Cookbook: default.jbs Time: 07:32:12 Date: 07/11/2020 Version: 31.0.0 Red Diamond Table of Contents Table of Contents 2 Analysis Report 44S5D444F55G8222Y55UU44S4S.vbs 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Startup 4 Malware Configuration 4 Yara Overview 4 Sigma Overview 4 Signature Overview 4 AV Detection: 5 Data Obfuscation: 5 Persistence and Installation Behavior: 5 Malware Analysis System Evasion: 5 HIPS / PFW / Operating System Protection Evasion: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 7 URLs 7 Domains and IPs 8 Contacted Domains 8 Contacted URLs 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 9 General Information 9 Simulations 10 Behavior and APIs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 11 General 11 File Icon 12 Network Behavior 12 TCP Packets 12 HTTP Request Dependency Graph 12 HTTP Packets 12 Code Manipulations 13 Statistics 13 Behavior 13 System Behavior 14 Analysis Process: wscript.exe PID: 6124 Parent PID: 3388 14 Copyright null 2020 Page 2 of 15 General 14 File Activities 14 File Created 14 File Written 14 Registry Activities 15 Analysis Process: wscript.exe PID: 5560 Parent PID: 6124 15 General 15 File Activities 15 Disassembly 15 Code Analysis 15 Copyright null 2020 Page 3 of -

Windows Tweaks Guide
Windows Tweaks Guide For By Windows Geeks Team Introduction .......................................................................................................................................... 5 Important Notes on This Guide........................................................................................................... 5 Usage Instruction.................................................................................................................................. 5 No Warranty .......................................................................................................................................... 5 Hosting, Distribution & Translation ................................................................................................... 6 Tweaks for Windows XP ...................................................................................................................... 6 Before You Begin Tweaking XP ................................................................................................. 6 Tweaks for Startup ..................................................................................................................... 8 Tweaks for Shutdown .............................................................................................................. 10 Tweaks for Mouse .................................................................................................................... 10 Tweaks for Start Menu ............................................................................................................ -

Directx 11 Extended to the Implementation of Compute Shader
DirectX 1 DirectX About the Tutorial Microsoft DirectX is considered as a collection of application programming interfaces (APIs) for managing tasks related to multimedia, especially with respect to game programming and video which are designed on Microsoft platforms. Direct3D which is a renowned product of DirectX is also used by other software applications for visualization and graphics tasks such as CAD/CAM engineering. Audience This tutorial has been prepared for developers and programmers in multimedia industry who are interested to pursue their career in DirectX. Prerequisites Before proceeding with this tutorial, it is expected that reader should have knowledge of multimedia, graphics and game programming basics. This includes mathematical foundations as well. Copyright & Disclaimer Copyright 2019 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at [email protected]