Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Requirements and Installation
SCAD Office System Requirements and I nstallation SCAD Soft Contents System Requirements ...................................................................................................................... 3 Recommendations on Optimization of an Operational Environment ............................................. 4 Turn on (or off) the Indexing Service .......................................................................................... 4 Defragment Regularly ................................................................................................................. 4 Start Word and Excel once before Starting SCAD Office .......................................................... 4 Memory Fragmentation by the Service Programs ....................................................................... 4 Settings of the PDF-printing ........................................................................................................ 4 SCAD Office Installation ................................................................................................................ 5 Program Installation .................................................................................................................... 5 English Versions of Windows ..................................................................................................... 5 Privileges ..................................................................................................................................... 5 Network Licensing ..................................................................................................................... -

Copy on Write Based File Systems Performance Analysis and Implementation
Copy On Write Based File Systems Performance Analysis And Implementation Sakis Kasampalis Kongens Lyngby 2010 IMM-MSC-2010-63 Technical University of Denmark Department Of Informatics Building 321, DK-2800 Kongens Lyngby, Denmark Phone +45 45253351, Fax +45 45882673 [email protected] www.imm.dtu.dk Abstract In this work I am focusing on Copy On Write based file systems. Copy On Write is used on modern file systems for providing (1) metadata and data consistency using transactional semantics, (2) cheap and instant backups using snapshots and clones. This thesis is divided into two main parts. The first part focuses on the design and performance of Copy On Write based file systems. Recent efforts aiming at creating a Copy On Write based file system are ZFS, Btrfs, ext3cow, Hammer, and LLFS. My work focuses only on ZFS and Btrfs, since they support the most advanced features. The main goals of ZFS and Btrfs are to offer a scalable, fault tolerant, and easy to administrate file system. I evaluate the performance and scalability of ZFS and Btrfs. The evaluation includes studying their design and testing their performance and scalability against a set of recommended file system benchmarks. Most computers are already based on multi-core and multiple processor architec- tures. Because of that, the need for using concurrent programming models has increased. Transactions can be very helpful for supporting concurrent program- ming models, which ensure that system updates are consistent. Unfortunately, the majority of operating systems and file systems either do not support trans- actions at all, or they simply do not expose them to the users. -

Windows Kernel Hijacking Is Not an Option: Memoryranger Comes to The
WINDOWS KERNEL HIJACKING IS NOT AN OPTION: MEMORYRANGER COMES TO THE RESCUE AGAIN Igor Korkin, PhD Independent Researcher Moscow, Russian Federation [email protected] ABSTRACT The security of a computer system depends on OS kernel protection. It is crucial to reveal and inspect new attacks on kernel data, as these are used by hackers. The purpose of this paper is to continue research into attacks on dynamically allocated data in the Windows OS kernel and demonstrate the capacity of MemoryRanger to prevent these attacks. This paper discusses three new hijacking attacks on kernel data, which are based on bypassing OS security mechanisms. The first two hijacking attacks result in illegal access to files open in exclusive access. The third attack escalates process privileges, without applying token swapping. Although Windows security experts have issued new protection features, access attempts to the dynamically allocated data in the kernel are not fully controlled. MemoryRanger hypervisor is designed to fill this security gap. The updated MemoryRanger prevents these new attacks as well as supporting the Windows 10 1903 x64. Keywords: hypervisor-based protection, Windows kernel, hijacking attacks on memory, memory isolation, Kernel Data Protection. 1. INTRODUCTION the same high privilege level as the OS kernel, and they also include a variety The security of users’ data and of vulnerabilities. Researchers applications depends on the security of consider that “kernel modules (drivers) the OS kernel code and data. Modern introduce additional attack surface, as operating systems include millions of they have full access to the kernel’s lines of code, which makes it address space” (Yitbarek and Austin, impossible to reveal and remediate all 2019). -

SLDXA /T /L1 – SLX Component List
SLDXA /T /L1 – SLX Component List SLDXA.exe ver 1.0 Copyright (c) 2004-2006 SJJ Embedded Micro Solutions, LLC All Rights Reserved SLXDiffC.exe ver 2.0 / SLXtoTXTC.exe ver 2.0 www.sjjmicro.com Processing... File1 to TXT file. Opening XSL File Reading RTF for final conversion F:\SLXTEST\LOCKDOWN_DEMO2.SLX has the following Components Total Count is: 577 -------------------------------------------------- .NET Framework 1.1 - Security Update KB887998 Accessibility Control Panel Accessibility Core ACPI Fixed Feature Button Active Directory Service Interface (ADSI) Core Active Directory Service Interface (ADSI) LDAP Provider Active Directory Service Interface (ADSI) Windows NT Provider Active Template Library (ATL) Add Hardware Control Panel Add/Remove Programs Control Panel Administration Support Tools Administrator Account Advanced Configuration and Power Interface (ACPI) PC Analog TV Application Compatibility Core Audio Codecs Audio Control Panel Base Component Base Performance Counters Base Support Binaries CD-ROM Drive Certificate Request Client & Certificate Autoenrollment Certificate User Interface Services Class Install Library - Desk Class Install Library - Mdminst Class Install Library - Mmsys Class Install Library - Msports Class Install Library - Netcfgx Class Install Library - Storprop Class Install Library - System Devices Class Installer - Computer Class Installer - Disk drives Class Installer - Display adapters Class Installer - DVD/CD-ROM drives Class Installer - Floppy disk controllers Class Installer - Floppy disk drives -

Leveraging Forticlient with Microsoft Defender: 6 Use Cases
SOLUTION BRIEF Leveraging FortiClient with Microsoft Defender: 6 Use Cases Executive Overview A compromised endpoint can quickly infect an entire enterprise network—which FortiClient Features Include: is why endpoint devices are now a favorite target for cyber criminals. More than an endpoint protection platform that provides automated, next-generation threat nnSecurity Fabric Connector. protection, FortiClient connects endpoints with the Security Fabric. It enables Enables endpoint visibility and endpoint visibility and compliance throughout the Security Fabric architecture. compliance throughout the Combining FortiClient with OS-embedded protection, such as Microsoft Security Fabric architecture. Defender or Microsoft Defender ATP, enhances these capabilities, providing nnVulnerability scanning. an integrated endpoint and network security solution that reinforces enterprise Detects and patches endpoint defenses, reduces complexity, and enhances the end-user experience. vulnerabilities. nn Improving Protection of Endpoint Devices Anti-malware protection. Employs machine learning (ML), FortiClient provides automated threat protection and endpoint vulnerability scanning to help artificial intelligence (AI), and maintain endpoint security hygiene and deliver risk-based visibility across the Fortinet Security cloud-based threat detection Fabric architecture. As a result, organizations can identify and remediate vulnerabilities or in addition to pattern-based compromised hosts across the entire attack surface. malware detection. In some cases, customers may wish to take advantage of certain FortiClient features while nnAnti-exploit engine. Uses leaving existing third-party protections in place. For example, in instances where there are signatureless, behavior-based policies in an organization that require two different antivirus (AV) vendors on an endpoint protection against memory and for governance or compliance reasons, the need for FortiClient alongside a third-party AV fileless attacks; detects exploit solution such as Microsoft Defender is necessitated. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

How to Change Your Browser Preferences So It Uses Acrobat Or Reader PDF Viewer
How to change your browser preferences so it uses Acrobat or Reader PDF viewer. If you are unable to open the PDF version of the Emergency Action Plan, please use the instructions below to configure your settings for Firefox, Google Chrome, Apple Safari, Internet Explorer, and Microsoft Edge. Firefox on Windows 1. Choose Tools > Add-ons. 2. In the Add-ons Manager window, click the Plugins tab, then select Adobe Acrobat or Adobe Reader. 3. Choose an appropriate option in the drop-down list next to the name of the plug-in. 4. Always Activate sets the plug-in to open PDFs in the browser. 5. Ask to Activate prompts you to turn on the plug-in while opening PDFs in the browser. 6. Never Activate turns off the plug-in so it does not open PDFs in the browser. Select the Acrobat or Reader plugin in the Add-ons Manager. Firefox on Mac OS 1. Select Firefox. 2. Choose Preferences > Applications. 3. Select a relevant content type from the Content Type column. 4. Associate the content type with the application to open the PDF. For example, to use the Acrobat plug-in within the browser, choose Use Adobe Acrobat NPAPI Plug-in. Reviewed 2018 How to change your browser preferences so it uses Acrobat or Reader PDF viewer. Chrome 1. Open Chrome and select the three dots near the address bar 2. Click on Settings 3. Expand the Advanced settings menu at the bottom of the page 4. Under the Privacy and security, click on Content Settings 5. Find PDF documents and click on the arrow to expand the menu 6. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -
Quick Guide Page | 1
Quick Guide Page | 1 Contents Welcome to Windows 10 ................................................................................................................................................................................................... 3 Key innovations ...................................................................................................................................................................................................................... 3 Cortana ................................................................................................................................................................................................................................. 3 Microsoft Edge .................................................................................................................................................................................................................. 4 Gaming & Xbox ................................................................................................................................................................................................................ 5 Built-in apps ....................................................................................................................................................................................................................... 7 Enterprise-grade secure and fast ................................................................................................................................................................................... -
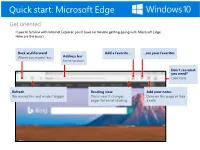
Quick Start: Microsoft Edge
Quick start: Microsoft Edge Get oriented If you’re familiar with Internet Explorer, you’ll have no trouble getting going with Microsoft Edge. Here are the basics. Back and Forward Add a favorite... ...see your favorites Where you expect ‘em. Address bar Same location. Don’t see what you need? Look here. Refresh Reading view Add your notes We moved this and made it bigger. This is new. It changes Draw on this page or take pages for easier reading. a note. Quick start: Microsoft Edge Microsoft Edge makes finding the needles in the internet’s haystack faster and easier. Find answers quickly by typing your question in the address bar. If we’ve got the answer, we’ll show it to you or make a suggestion. 1. Ask your question in the Address bar 2. Find your answer here 3. See other options here Quick start: Microsoft Edge If you’ve got a lot of web reading to do, switch to Reading view and give your eyes a break. Before After Need more contrast or a bigger font? To change settings, select More in the upper-right corner, select Settings, scroll to the Reading section and play with the options. Quick start: Microsoft Edge If you don’t always have internet access, add webpages that you want to read later to your Reading List and you’ll be able to get to them offline, too. 1. Add things to the list 2. Open the list Open a webpage > select the Favorites Hub button > Reading list . button > Reading list > Add. -

(RUNTIME) a Salud Total
Windows 7 Developer Guide Published October 2008 For more information, press only: Rapid Response Team Waggener Edstrom Worldwide (503) 443-7070 [email protected] Downloaded from www.WillyDev.NET The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This guide is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form, by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft. Microsoft may have patents, patent applications, trademarks, copyrights or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place or event is intended or should be inferred.