A Hunting Story: What’S Hiding in Powershell Scripts and Pastebin Code? Saudi Actors
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trident Development Framework
Trident Development Framework Tom MacAdam Jim Covill Kathleen Svendsen Martec Limited Prepared By: Martec Limited 1800 Brunswick Street, Suite 400 Halifax, Nova Scotia B3J 3J8 Canada Contractor's Document Number: TR-14-85 (Control Number: 14.28008.1110) Contract Project Manager: David Whitehouse, 902-425-5101 PWGSC Contract Number: W7707-145679/001/HAL CSA: Malcolm Smith, Warship Performance, 902-426-3100 x383 The scientific or technical validity of this Contract Report is entirely the responsibility of the Contractor and the contents do not necessarily have the approval or endorsement of the Department of National Defence of Canada. Contract Report DRDC-RDDC-2014-C328 December 2014 © Her Majesty the Queen in Right of Canada, as represented by the Minister of National Defence, 2014 © Sa Majesté la Reine (en droit du Canada), telle que représentée par le ministre de la Défense nationale, 2014 Working together for a safer world Trident Development Framework Martec Technical Report # TR-14-85 Control Number: 14.28008.1110 December 2014 Prepared for: DRDC Atlantic 9 Grove Street Dartmouth, Nova Scotia B2Y 3Z7 Martec Limited tel. 902.425.5101 1888 Brunswick Street, Suite 400 fax. 902.421.1923 Halifax, Nova Scotia B3J 3J8 Canada email. [email protected] www.martec.com REVISION CONTROL REVISION REVISION DATE Draft Release 0.1 10 Nov 2014 Draft Release 0.2 2 Dec 2014 Final Release 10 Dec 2014 PROPRIETARY NOTICE This report was prepared under Contract W7707-145679/001/HAL, Defence R&D Canada (DRDC) Atlantic and contains information proprietary to Martec Limited. The information contained herein may be used and/or further developed by DRDC Atlantic for their purposes only. -

Wireless GPON ONT
GPON 4 Ethernet Ports | 1 PON | VoIP | 802.11n | 802.11ac GRG-4260us Wireless GPON ONT The GRG-4260us is an advanced GPON ONT gateway with 1 GPON WAN port, 4 Gigabit Ethernet LAN ports, 2 FXS ports, 1 USB2.0 Host and IEEE802.11 series Wi-Fi. The Wi-Fi not only provides an 802.11n 2T2R 2.4GHz Band which is backward compatible with 802.11g/b but also supports high performance 802.11ac with 3T3R design at 5GHz band. GRG-4260us provides powerful functions which telephone companies have applied on the xDSL CPE IAD device, and remote management utilities (such as TR-069) for network management and maintenance. FEATURES .UPnP, IPv6 compliant .WPA and 802.1x/ WPS 2.0/ Radius Client .PhyR and G.INP .NAT/PAT .Supports TR-069/TR-098/TR-181i2 .IGMP Proxy/ Fast Leave/ Snooping/ Proxy .Configuration backup and restoration .DHCP Server/Client .Web-based management (HTTPS/HTTP) .Embedded SNMP agent .Supports remote administration, automatic .IP/MAC address filtering firmware upgrade and configuration .Static route/ RIP/ RIP v2 routing functions .Integrated 802.11ac AP (backward compatible .DNS Proxy/Relay with 802.11a/n) www.comtrend.com GRG-4260us 4 Ethernet Ports | 1 PON | VoIP | 802.11n | 802.11ac SPECIFICATIONS Hardware Networking Protocols .PPPoE pass-through, Multiple PPPoE sessions on single WAN .GPON X 1 Bi-directional Optical (1310nm/1490nm) .RJ-45 X 4 for LAN, (10/100/1000 Base T) interface .RJ-11 X 2 for FXS (optional) .PPPoE filtering of non-PPPoE packets between WAN and LAN .USB2.0 host X 1 .Transparent bridging between all LAN and WAN interfaces -

Understanding the Attack Surface and Attack Resilience of Project Spartan’S (Edge) New Edgehtml Rendering Engine
Understanding the Attack Surface and Attack Resilience of Project Spartan’s (Edge) New EdgeHTML Rendering Engine Mark Vincent Yason IBM X-Force Advanced Research yasonm[at]ph[dot]ibm[dot]com @MarkYason [v2] © 2015 IBM Corporation Agenda . Overview . Attack Surface . Exploit Mitigations . Conclusion © 2015 IBM Corporation 2 Notes . Detailed whitepaper is available . All information is based on Microsoft Edge running on 64-bit Windows 10 build 10240 (edgehtml.dll version 11.0.10240.16384) © 2015 IBM Corporation 3 Overview © 2015 IBM Corporation Overview > EdgeHTML Rendering Engine © 2015 IBM Corporation 5 Overview > EdgeHTML Attack Surface Map & Exploit Mitigations © 2015 IBM Corporation 6 Overview > Initial Recon: MSHTML and EdgeHTML . EdgeHTML is forked from Trident (MSHTML) . Problem: Quickly identify major code changes (features/functionalities) from MSHTML to EdgeHTML . One option: Diff class names and namespaces © 2015 IBM Corporation 7 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Method) © 2015 IBM Corporation 8 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests change in image support: . Suggests new DOM object types: © 2015 IBM Corporation 9 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Examples) . Suggests ported code from another rendering engine (Blink) for Web Audio support: © 2015 IBM Corporation 10 Overview > Initial Recon: Diffing MSHTML and EdgeHTML (Notes) . Further analysis needed –Renamed class/namespace results into a new namespace plus a deleted namespace . Requires availability -

Integrated Voice Evacuation System Vx-3000 Series
SETTING SOFTWARE INSTRUCTIONS For Authorized Advanced End User INTEGRATED VOICE EVACUATION SYSTEM VX-3000 SERIES Tip In this manual, the VX-3004F/3008F/3016F Voice Evacuation Frames are collectively referred to as "VX-3000F." Thank you for purchasing TOA’s Integrated Voice Evacuation System. Please carefully follow the instructions in this manual to ensure long, trouble-free use of your equipment. TABLE OF CONTENTS 1. SOFTWARE OUTLINE ................................................................................... 3 2. NOTES ON PERFORMING SETTINGS .............................................. 3 2.1. System Requirements .......................................................................................... 3 2.2. Notes .................................................................................................................... 3 3. SOFTWARE SETUP ........................................................................................ 4 3.1. Setting Software Installation ................................................................................. 4 3.2. Uninstallation ....................................................................................................... 6 4. STARTING THE VX-3000 SETTING SOFTWARE ....................... 7 5. SETTING ITEMS ................................................................................................ 8 5.1. Setting Item Button Configuration ........................................................................ 8 5.2. Menu Bar ............................................................................................................. -

Nessus 8.3 User Guide
Nessus 8.3.x User Guide Last Updated: September 24, 2021 Table of Contents Welcome to Nessus 8.3.x 12 Get Started with Nessus 15 Navigate Nessus 16 System Requirements 17 Hardware Requirements 18 Software Requirements 22 Customize SELinux Enforcing Mode Policies 25 Licensing Requirements 26 Deployment Considerations 27 Host-Based Firewalls 28 IPv6 Support 29 Virtual Machines 30 Antivirus Software 31 Security Warnings 32 Certificates and Certificate Authorities 33 Custom SSL Server Certificates 35 Create a New Server Certificate and CA Certificate 37 Upload a Custom Server Certificate and CA Certificate 39 Trust a Custom CA 41 Create SSL Client Certificates for Login 43 Nessus Manager Certificates and Nessus Agent 46 Install Nessus 48 Copyright © 2021 Tenable, Inc. All rights reserved. Tenable, Tenable.io, Tenable Network Security, Nessus, SecurityCenter, SecurityCenter Continuous View and Log Correlation Engine are registered trade- marks of Tenable,Inc. Tenable.sc, Tenable.ot, Lumin, Indegy, Assure, and The Cyber Exposure Company are trademarks of Tenable, Inc. All other products or services are trademarks of their respective Download Nessus 49 Install Nessus 51 Install Nessus on Linux 52 Install Nessus on Windows 54 Install Nessus on Mac OS X 56 Install Nessus Agents 58 Retrieve the Linking Key 59 Install a Nessus Agent on Linux 60 Install a Nessus Agent on Windows 64 Install a Nessus Agent on Mac OS X 70 Upgrade Nessus and Nessus Agents 74 Upgrade Nessus 75 Upgrade from Evaluation 76 Upgrade Nessus on Linux 77 Upgrade Nessus on Windows 78 Upgrade Nessus on Mac OS X 79 Upgrade a Nessus Agent 80 Configure Nessus 86 Install Nessus Home, Professional, or Manager 87 Link to Tenable.io 88 Link to Industrial Security 89 Link to Nessus Manager 90 Managed by Tenable.sc 92 Manage Activation Code 93 Copyright © 2021 Tenable, Inc. -
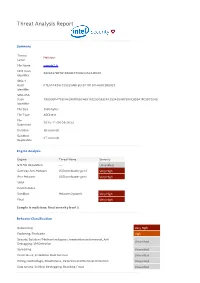
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -

Windows Live
Microsoft Your potential. Our passion,"' Windows Live MICROSOFT ONLINE SERVICES •Lsw-EMerccmcnt Use Onty- Law Enforcement Hotline: (425) 722-1299 MSN & windows Live Services: Hotmail & Passport Requests: FAX: (425) 727-3490 FAX: (650) 693-7061 Microsoft Corporation Microsoft Corporation Attention: Attention: Online Services Custodian of Records online Services custodian of Records One Microsoft Way 1065 la Avenida, Building 4 Redmond, WA 98052-6399 Mountain View, CA 94043 Summary of Record Retention Policies Hotmail & MSN E-mail IP Logs 60 days + initial sign in MSN internet Access Connection Logs 60 da\s MSN Groups—US (IP) Logs 60 days MSN Groups — inactive Status 30 days of non-activity MSN Groups — Content Deletion 30 days (!>i)5!~iu:«:iiv[- or ilbaDk'U) MSN Spaces — IIS (IP) Logs 60 days MSN Spaces — Content Deletion 90 days (after ifis;il>leil) Windows Live Messenger Conversations None Passport Varies depending on connection and date range EMERGENCY REQUESTS Microsoft online Services will respond to emergency requests outside of normal business hours if the emergency involves "the immediate danger of death or physical injury to any person..." as defined in 18 u.S.C. § 2702(c)(4) and (b)(8). Emergencies are limited to situations like kidnapping, murder threats, bomb threats, terrorist threats, etc. Legal Documentation Required for Customer Account information and content The Electronic communications Privacy Act (ECPAi (18 u.S.c. § 2701 through 2712) governs what legal documentation is required in order for Microsoft's online services records custodians to disclose customer account information and e-mail content. For most Microsoft Online services: Basic Subscriber information may be Disclosed with a Subpoena. -

Microsoft Corporation
Before the Federal Trade Commission Washington, DC In the Matter of ) ) Microsoft Corporation. ) _____________________________ ) Complaint and Request for Injunction, Request For Investigation and for Other Relief INTRODUCTION 1. This complaint concerns the privacy implications of the Microsoft XP operating system that is expected to become the primary means of access for consumers in the United States to the Internet. As is set forth in detail below, Microsoft has engaged, and is engaging, in unfair and deceptive trade practices intended to profile, track, and monitor millions of Internet users. Central to the scheme is a system of services, known collectively as “.NET,” which incorporate “Passport,” “Wallet,” and “HailStorm” that are designed to obtain personal information from consumers in the United States unfairly and deceptively. The public interest requires the Commission to investigate these practices and to enjoin Microsoft from violating Section 5 of the Federal Trade Commission Act, as alleged herein. PARTIES 2. The Electronic Privacy Information Center (“EPIC”) is a non-profit, public interest research organization incorporated in the District of Columbia. EPIC’s activities include the review of government and private sector polices and practices to determine their possible impact on the privacy interests of the American public. Among its other activities, EPIC has prepared reports and presented testimony before Congress and administrative agencies on the Internet and privacy issues. 3. The Center for Digital Democracy (“CDD”) is a non-profit organization that represents the interests of citizens and consumers with respect to new media technologies. 4. The Center for Media Education (“CME”) is a national nonprofit, nonpartisan organization dedicated to creating a quality electronic media culture for children, their families, and the community. -

Automated Malware Analysis Report For
ID: 310931 Sample Name: 44S5D444F55G8222Y55UU44S4S.vbs Cookbook: default.jbs Time: 07:32:12 Date: 07/11/2020 Version: 31.0.0 Red Diamond Table of Contents Table of Contents 2 Analysis Report 44S5D444F55G8222Y55UU44S4S.vbs 4 Overview 4 General Information 4 Detection 4 Signatures 4 Classification 4 Startup 4 Malware Configuration 4 Yara Overview 4 Sigma Overview 4 Signature Overview 4 AV Detection: 5 Data Obfuscation: 5 Persistence and Installation Behavior: 5 Malware Analysis System Evasion: 5 HIPS / PFW / Operating System Protection Evasion: 5 Mitre Att&ck Matrix 5 Behavior Graph 6 Screenshots 6 Thumbnails 6 Antivirus, Machine Learning and Genetic Malware Detection 7 Initial Sample 7 Dropped Files 7 Unpacked PE Files 7 Domains 7 URLs 7 Domains and IPs 8 Contacted Domains 8 Contacted URLs 8 URLs from Memory and Binaries 8 Contacted IPs 8 Public 9 General Information 9 Simulations 10 Behavior and APIs 10 Joe Sandbox View / Context 10 IPs 10 Domains 10 ASN 10 JA3 Fingerprints 11 Dropped Files 11 Created / dropped Files 11 Static File Info 11 General 11 File Icon 12 Network Behavior 12 TCP Packets 12 HTTP Request Dependency Graph 12 HTTP Packets 12 Code Manipulations 13 Statistics 13 Behavior 13 System Behavior 14 Analysis Process: wscript.exe PID: 6124 Parent PID: 3388 14 Copyright null 2020 Page 2 of 15 General 14 File Activities 14 File Created 14 File Written 14 Registry Activities 15 Analysis Process: wscript.exe PID: 5560 Parent PID: 6124 15 General 15 File Activities 15 Disassembly 15 Code Analysis 15 Copyright null 2020 Page 3 of -

Graduate Nursing Student Handbook 2020-2021
Graduate Nursing Student Handbook 2021-2022 Chair’s Welcome ............................................................................................................................ 6 Program Director’s Welcome ......................................................................................................... 7 Graduate Nursing Program Learning Objectives……………..…………………………………...8 Masters Essentials ………………………………………………………………………...8 Doctorate Essentials …………………………………………………………….………..9 SALVE REGINA UNIVERSITY DEPARTMENT OF NURSING ............................................ 10 The Mission of the Department of Nursing .......................................................................... …10 Accreditation………………………………………………………………..………………….10 Accessibility of Programs and Services .................................................................................... 11 Student Rights and Responsibilities .......................................................................................... 11 SALVE REGINA ACADEMIC POLICIES ............................................................................... 122 Academic Honor Code ............................................................................................................ 122 Academic Conduct .................................................................................................................. 122 Intellectual Property ................................................................................................................ 133 Plagiarism ............................................................................................................................... -

Secrets of Powershell Remoting
Secrets of PowerShell Remoting The DevOps Collective, Inc. This book is for sale at http://leanpub.com/secretsofpowershellremoting This version was published on 2018-10-28 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. © 2016 - 2018 The DevOps Collective, Inc. Also By The DevOps Collective, Inc. Creating HTML Reports in Windows PowerShell A Unix Person’s Guide to PowerShell The Big Book of PowerShell Error Handling DevOps: The Ops Perspective Ditch Excel: Making Historical and Trend Reports in PowerShell The Big Book of PowerShell Gotchas The Monad Manifesto, Annotated Why PowerShell? Windows PowerShell Networking Guide The PowerShell + DevOps Global Summit Manual for Summiteers Why PowerShell? (Spanish) Secrets of PowerShell Remoting (Spanish) DevOps: The Ops Perspective (Spanish) The Monad Manifesto: Annotated (Spanish) Creating HTML Reports in PowerShell (Spanish) The Big Book of PowerShell Gotchas (Spanish) The Big Book of PowerShell Error Handling (Spanish) DevOps: WTF? PowerShell.org: History of a Community Contents Secrets of PowerShell Remoting ..................................... 1 Remoting Basics ................................................ 3 What is Remoting? ............................................ 3 Examining Remoting Architecture .................................. 3 Enabling -

Luno Tools Run Command Documentation Page 1/6
Luno Tools Run Command documentation Page 1/6 Luno Tools Run Command Description Run Command aims to be a user-friendly way to run command line applications, command line system calls and single line shell scripts. Setup 1. Build a working command outside Switch It is important to start with a command which achieves your task and which needs to work outside Switch. On Mac, this means you build and test the command in the Terminal App. On Windows, you build the command in “Command Prompt” (Cmd.exe) or “Windows Powershell”. By example, we can build a command which retrieves the permissions of one file and stores it in another file. On mac we can achieve this using the following command: ls -l /path/to/inputfile.txt > /path/to/outputfolder/filename.txt And on Windows Command Prompt using this command : icacls -l C:\path\to\inputfile.txt > C:\path\to\outputfolder\filename.txt If you have issues with your command at this stage (you don’t achieve the output you want, you have errors, …), then the issue is not related to the “Run Command” app itself. The people with the most knowledge about your issue are the people who are expert at the command line application, command line system call or shell script you are trying to use. Usually, there are help pages, support forums, support people specific for these applications who can help you. Alternatively, you can also ask help on the Enfocus forums. 2. Handle spaces correctly When working with these kinds of commands a space is used to separate different parts of the command, by example a space is placed between the command name and the path to the inputfile.