Reverse Engineering and the Rise of Electronic Vigilantism: Intellectual Property Implications of "Lock-Out" Programs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A History of Video Game Consoles Introduction the First Generation
A History of Video Game Consoles By Terry Amick – Gerald Long – James Schell – Gregory Shehan Introduction Today video games are a multibillion dollar industry. They are in practically all American households. They are a major driving force in electronic innovation and development. Though, you would hardly guess this from their modest beginning. The first video games were played on mainframe computers in the 1950s through the 1960s (Winter, n.d.). Arcade games would be the first glimpse for the general public of video games. Magnavox would produce the first home video game console featuring the popular arcade game Pong for the 1972 Christmas Season, released as Tele-Games Pong (Ellis, n.d.). The First Generation Magnavox Odyssey Rushed into production the original game did not even have a microprocessor. Games were selected by using toggle switches. At first sales were poor because people mistakenly believed you needed a Magnavox TV to play the game (GameSpy, n.d., para. 11). By 1975 annual sales had reached 300,000 units (Gamester81, 2012). Other manufacturers copied Pong and began producing their own game consoles, which promptly got them sued for copyright infringement (Barton, & Loguidice, n.d.). The Second Generation Atari 2600 Atari released the 2600 in 1977. Although not the first, the Atari 2600 popularized the use of a microprocessor and game cartridges in video game consoles. The original device had an 8-bit 1.19MHz 6507 microprocessor (“The Atari”, n.d.), two joy sticks, a paddle controller, and two game cartridges. Combat and Pac Man were included with the console. In 2007 the Atari 2600 was inducted into the National Toy Hall of Fame (“National Toy”, n.d.). -

The Game's the Thing: Properties, Priorities and Perceptions in the Video Games Industries
The game's the thing: properties, priorities and perceptions in the video games industries Mac Sithigh, D. (2017). The game's the thing: properties, priorities and perceptions in the video games industries. In M. Richardson, & S. Ricketson (Eds.), Research Handbook on Intellectual Property in Media and Entertainment (pp. 344-366). Edward Elgar Publishing. https://doi.org/10.4337/9781784710798 Published in: Research Handbook on Intellectual Property in Media and Entertainment Document Version: Peer reviewed version Queen's University Belfast - Research Portal: Link to publication record in Queen's University Belfast Research Portal Publisher rights Copyright 2017, the Author. This work is made available online in accordance with the publisher’s policies. Please refer to any applicable terms of use of the publisher. General rights Copyright for the publications made accessible via the Queen's University Belfast Research Portal is retained by the author(s) and / or other copyright owners and it is a condition of accessing these publications that users recognise and abide by the legal requirements associated with these rights. Take down policy The Research Portal is Queen's institutional repository that provides access to Queen's research output. Every effort has been made to ensure that content in the Research Portal does not infringe any person's rights, or applicable UK laws. If you discover content in the Research Portal that you believe breaches copyright or violates any law, please contact [email protected]. Download date:25. Sep. 2021 The Game’s the Thing: Property, Priorities and Perceptions in the Video Games Industries Daithí Mac Síthigh* Published in Richardson and Ricketson (eds), Research Handbook on Intellectual Property in Media and Entertainment (Edward Elgar 2017) I. -

Online Software Copyright Infringement and Criminal Enforcement
Online Software Copyright Infringement and Criminal Enforcement Submitted: May 14, 2005 Randy K. Baldwin American University Washington College of Law What are Warez and Who Trades Them? This paper will discuss infringement of software copyrights with a focus on criminal ‘warez trading‘ of copyrighted software on the Internet. Warez are infringing electronic, digital copies of copyrighted works whose copy protection measures have been removed.1 Warez are most often ‘cracked’ software programs whose digital rights management (DRM) and copy control measures have been circumvented. Once DRM controls have been disabled, warez are subsequently distributed and traded on the Internet, usually without any direct financial gain to the distributors and traders.2 Distribution of warez usually starts as small-scale deployments from password- protected file transfer protocol (FTP) servers and encrypted and/or password-protected web sites run by warez groups. Warez are then traded on the Internet among broader groups via direct peer-to-peer (P2P) connections, and encrypted emails with warez attachments. Trading and downloading of warez is coordinated via closed, invite-only Internet Relay Chat (IRC) channels, Pretty Good Privacy (PGP) encrypted email, Instant Messaging (IM), private chat rooms, direct connect P2P networks, and messages posted to Usenet groups under pseudonyms.3 Servers and sites hosting warez and communications means used by warez traders are designed to avoid detection and identification by law enforcement.4 File and directory names are intentionally 1 Goldman, Eric, A Road to No Warez: The No Electronic Theft Act and Criminal Copyright Infringement. 82 Or. L. Rev. 369, 370-371 (2003). [hereinafter Road to No Warez], available at http://ssrn.com/abstract=520122 (last visited May 9, 2005) (on file with author) (Defines warez and warez trading. -

Copyleft, -Right and the Case Law on Apis on Both Sides of the Atlantic 5
Less may be more: copyleft, -right and the case law on APIs on both sides of the Atlantic 5 Less may be more: copyleft, -right and the case law on APIs on both sides of the Atlantic Walter H. van Holst Senior IT-legal consultant at Mitopics, The Netherlands (with thanks to the whole of the FTF-legal mailinglist for contributing information and cases that were essential for this article) DOI: 10.5033/ifosslr.v5i1.72 Abstract Like any relatively young area of law, copyright on software is surrounded by some legal uncertainty. Even more so in the context of copyleft open source licenses, since these licenses in some respects aim for goals that are the opposite of 'regular' software copyright law. This article provides an analysis of the reciprocal effect of the GPL- family of copyleft software licenses (the GPL, LGPL and the AGPL) from a mostly copyright perspective as well as an analysis of the extent to which the SAS/WPL case affects this family of copyleft software licenses. In this article the extent to which the GPL and AGPL reciprocity clauses have a wider effect than those of the LGPL is questioned, while both the SAS/WPL jurisprudence and the Oracle vs Google case seem to affirm the LGPL's “dynamic linking” criterium. The net result is that the GPL may not be able to be more copyleft than the LGPL. Keywords Law; information technology; Free and Open Source Software; case law; copyleft, copyright; reciprocity effect; exhaustion; derivation; compilation International Free and Open Source Software Law Review Vol. -

Accolade-Catalog2
Introduction • • Jack Nicklaus Golf & Course • Design: Signature Edition'" • AI Michaels Announces ~ • HardBall III'" • T • Road & Track®Presents Grand Prix Unlimited'" • • Science Fiction Role-Playing: • Star Control II'" • ® SNOOPY's Game Club'" • • Accolade in Motion • • Sports: Mike Ditka Ultimate • Footbalr & Winter Challenge • • Driving: A Test Drive III: The Passion'" 1 L 0 Role Playing: Elvira®Mistress (J • of the Dark'" & Elvira II the ~ • Jaws of Cerberus'" Graphic Adventure: Les Manley in: Lost in LA'" Science Fiction: Hoverforce'" & Star Contror o Ordering Information Macintosh Titles All Time Favorites Product Availability s 1 Accolade In Motion •••••• From the moment hen it comes to entertainment software, you'll find a game IS Accolade in motion creating the finest and most conceived imaginative computer games on the market today. through design, Whether your favorite genre is sports, driving, role-playing, science fiction or graphic adventure, Accolade has a great ... production, game for you. and meticulous From the soaring drives of Jack Nicklaus to the towering home testing, we runs of HardBall 111- from the blazingly fast Formula One work hard to cars of Grand Prix Unlimited to the white-hot space combat of Star Control 11- Accolade pours on the excitement. produce the We pour out our hearts, too, with children's games like our very finest warm and funny SNOOPY's Game Club. games Accolade is proud that so many of the titles in our constantly possible. growing library have won critical acclaim for their realistic simulations, graphic excellence and absorbing gameplay. Yet it is our minds in motion - the creativity and dedication of our Accolade staff - that is our greatest pride. -

Case History
Page 1 of 15 Case History: Yinjie Soon STS 145, Winter 2002 Page 2 of 15 Yinjie Soon STS145: History of Computer Game Design Final Paper 12 February 2002 Case History Star Control II: The Ur-Quan Masters In July 1990, the two partners who formed the software company Toys for Bob released their first game, Star Control, under game publisher Accolade for the personal computer system. These two men – Paul Reiche III and Fred Ford – were big fans of science fiction, and in Reiche’s case, fantasy role playing games (especially Dungeons and Dragons). Unsurprisingly, the game had a strong science fiction theme and heavy doses of traditional role-playing elements, wherein the player controlled one of two sides in an effort to either take over the universe as the marauding conquerors of the Ur-Quan Hierarchy, or save the universe as the brave defenders of the Alliance of Free Stars. Star Control effectively interleaved elements of strategy and action; the player tried to outwit the opposing forces in various turn-based inter-planetary strategic scenarios, and subsequently engaged enemy ships in real-time “space melee” one-on-one spaceship dogfights, similar in style to Spacewar, the earliest of video games (Derrenbacker). Many of the sequel’s most interesting elements, such as the unique characteristics of each race’s ships and behaviors, were established in this game and would carry on to Star Control 2. Figures 1a and 1b show some scenes from Star Control, illustrating how advanced some of the graphics from the game were for the time (figure 1a is also an early manifestation of the creators’ sense of humor – the ship shown in the middle of the picture is the flagship of an all-female race of humanoids; the explanation behind the visual is left to the reader’s imagination.). -

Paolo Guarda Faculty of Law – University of Trento 1 Image Courtesy of Jscreationzs at Freedigitalphotos.Net
University of Trento Crash Course Copyright software protection: proprietary vs. open source licenses May 8, 2018 Paolo Guarda Faculty of Law – University of Trento 1 Image courtesy of jscreationzs at FreeDigitalPhotos.net CC_CopyrightSoftware_Guarda_18 2 Overview of intellectual property Legal right What for? How? Application and Patents New inventions examination Original creative or artistic Copyright Exists automatically forms Distinctive identification of Use and/or Trade marks products or services registration Registered designs External appearance Registration* Valuable information not known Reasonable efforts to Trade secrets to the public keep secret From EPO, Patent teaching kit CC_CopyrightSoftware_Guarda_18 3 Some IP found in a mobile Trade marks: • Made by "Nokia" phone • Product "N95" • Software "Symbian", "Java" Patents: • Data-processing methods • Semiconductor circuits © Nokia • Chemical compounds • … Trade secrets: ? Copyrights: • Software code Designs (some of them registered): • Instruction manual • Form of overall phone • Ringtone • Arrangement of buttons in oval shape • … • Three-dimensional wave form of buttons • … From EPO, Patent teaching kit CC_CopyrightSoftware_Guarda_18 4 IPRs Rationale § The Statute of Anne (1710): “An act for the encouragement of learning, by vesting the copies of printed books in the authors or purchasers of such copies, during the times therein mentioned” § U.S. CONST. art. I, Sec. 8, cl. 8 “The Congress shall have Power . To promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries” CC_CopyrightSoftware_Guard 5 a_18 Copyright CC_CopyrightSoftware_Guarda_18 6 Psychological pressure CC_CopyrightSoftware_Guarda_18 7 CC_CopyrightSoftware_Guarda_18 8 A recent law § Unlike the property on material things (which dates back to the dawn of time, which means the earliest forms of human legal organization). -
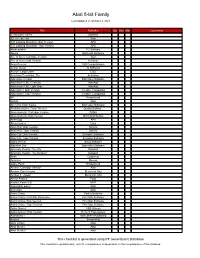
Atari 8-Bit Family
Atari 8-bit Family Last Updated on October 2, 2021 Title Publisher Qty Box Man Comments 221B Baker Street Datasoft 3D Tic-Tac-Toe Atari 747 Landing Simulator: Disk Version APX 747 Landing Simulator: Tape Version APX Abracadabra TG Software Abuse Softsmith Software Ace of Aces: Cartridge Version Atari Ace of Aces: Disk Version Accolade Acey-Deucey L&S Computerware Action Quest JV Software Action!: Large Label OSS Activision Decathlon, The Activision Adventure Creator Spinnaker Software Adventure II XE: Charcoal AtariAge Adventure II XE: Light Gray AtariAge Adventure!: Disk Version Creative Computing Adventure!: Tape Version Creative Computing AE Broderbund Airball Atari Alf in the Color Caves Spinnaker Software Ali Baba and the Forty Thieves Quality Software Alien Ambush: Cartridge Version DANA Alien Ambush: Disk Version Micro Distributors Alien Egg APX Alien Garden Epyx Alien Hell: Disk Version Syncro Alien Hell: Tape Version Syncro Alley Cat: Disk Version Synapse Software Alley Cat: Tape Version Synapse Software Alpha Shield Sirius Software Alphabet Zoo Spinnaker Software Alternate Reality: The City Datasoft Alternate Reality: The Dungeon Datasoft Ankh Datamost Anteater Romox Apple Panic Broderbund Archon: Cartridge Version Atari Archon: Disk Version Electronic Arts Archon II - Adept Electronic Arts Armor Assault Epyx Assault Force 3-D MPP Assembler Editor Atari Asteroids Atari Astro Chase Parker Brothers Astro Chase: First Star Rerelease First Star Software Astro Chase: Disk Version First Star Software Astro Chase: Tape Version First Star Software Astro-Grover CBS Games Astro-Grover: Disk Version Hi-Tech Expressions Astronomy I Main Street Publishing Asylum ScreenPlay Atari LOGO Atari Atari Music I Atari Atari Music II Atari This checklist is generated using RF Generation's Database This checklist is updated daily, and it's completeness is dependent on the completeness of the database. -

DRAGEN V3.2 EULA and Readme
Software Copyright Notice Software: DRAGEN v3.2 © Illumina, Inc. 2018 This Software is licensed for use under an End User Software License Agreement: ILLUMINA END-USER SOFTWARE LICENSE AGREEMENT IMPORTANT-READ CAREFULLY. THIS IS A LICENSE AGREEMENT THAT YOU ARE REQUIRED TO ACCEPT BEFORE INSTALLING AND USING ILLUMINA, INC. SOFTWARE. CAREFULLY READ ALL THE TERMS AND CONDITIONS OF THIS LICENSE AGREEMENT BEFORE PROCEEDING WITH THE DOWNLOADING AND/OR INSTALLATION OF THIS SOFTWARE. YOU ARE NOT PERMITTED TO DOWNLOAD AND/OR INSTALL THIS SOFTWARE UNTIL YOU HAVE AGREED TO BE BOUND BY ALL OF THE TERMS AND CONDITIONS OF THIS LICENSE AGREEMENT. BY DOWNLOADING, INSTALLING, OR OTHERWISE ACCESING OR USING THE SOFTWARE, YOU ACKNOWLEDGE THAT YOU HAVE REVIEWED AND ACCEPTED THIS LICENSE AGREEMENT, AND AGREE TO BE BOUND BY THE TERMS OF THIS LICENSE AGREEMENT. YOU ALSO REPRESENT AND WARRANT THAT YOU ARE DULY AUTHORIZED TO ACCEPT THE TERMS AND CONDITIONS OF THIS LICENSE AGREEMENT ON BEHALF OF YOUR EMPLOYER. This End User License Agreement (“Agreement”) is made and entered into by and between Illumina, Inc., a Delaware corporation, having offices at 5200 Illumina Way, San Diego, CA 92122 (“Illumina”) and you as the end-user of the Software (hereinafter, “Licensee” or “you”). All computer programs identified above, software, firmware, and associated media, printed materials and online and electronic documentation, including any updates or upgrades thereof (collectively, “Software”) provided to Licensee are for use solely by Licensee and the provisions herein shall apply with respect to such Software. By using the Software, you indicate your acceptance of these terms and conditions, at which point this Agreement will become a legally binding agreement between you and Illumina. -

Sega Enterprises LTD. V. Accolade, Inc.: What's So Fair About Reverse Engineering?
Loyola of Los Angeles Entertainment Law Review Volume 14 Number 3 Article 3 3-1-1994 Sega Enterprises LTD. v. Accolade, Inc.: What's so Fair about Reverse Engineering? David C. MacCulloch Follow this and additional works at: https://digitalcommons.lmu.edu/elr Part of the Law Commons Recommended Citation David C. MacCulloch, Sega Enterprises LTD. v. Accolade, Inc.: What's so Fair about Reverse Engineering?, 14 Loy. L.A. Ent. L. Rev. 465 (1994). Available at: https://digitalcommons.lmu.edu/elr/vol14/iss3/3 This Notes and Comments is brought to you for free and open access by the Law Reviews at Digital Commons @ Loyola Marymount University and Loyola Law School. It has been accepted for inclusion in Loyola of Los Angeles Entertainment Law Review by an authorized administrator of Digital Commons@Loyola Marymount University and Loyola Law School. For more information, please contact [email protected]. NOTES SEGA ENTERPRISES LTD. v. ACCOLADE, INC.: WHAT'S SO FAIR ABOUT REVERSE ENGINEERING? I. INTRODUCTION You are the president of a major corporation that develops and distributes computer video game cartridges and the consoles on which the games can be played. Your company has maintained a majority of the market share by remaining at the forefront of the game cartridges field. Your company's ability to be the first to incorporate all the latest enhance- ments is due to the efforts of one man-your chief designer of game concepts. If he were to leave, your company's position as number one in the industry would be jeopardized. One day, your chief designer demands that if he is not made an executive vice-president and equity shareholder in the company he will resign and take with him a new concept he has been privately developing at home that will take video game technology to the next level. -

Software Reverse Engineering and Copyright: Past, Present and Future, 31 J
UIC Law Review Volume 31 Issue 1 Article 1 Fall 1997 Legal Aspects - Software Reverse Engineering and Copyright: Past, Present and Future, 31 J. Marshall L. Rev. 1 (1997) Brian C. Behrens Reuven R. Levary Follow this and additional works at: https://repository.law.uic.edu/lawreview Part of the Computer Law Commons, Intellectual Property Law Commons, Legislation Commons, and the Science and Technology Law Commons Recommended Citation Brian C. Behrens & Reuven R. Levary, Legal Aspects - Software Reverse Engineering and Copyright: Past, Present and Future, 31 J. Marshall L. Rev. 1 (1997) https://repository.law.uic.edu/lawreview/vol31/iss1/1 This Article is brought to you for free and open access by UIC Law Open Access Repository. It has been accepted for inclusion in UIC Law Review by an authorized administrator of UIC Law Open Access Repository. For more information, please contact [email protected]. ARTICLES LEGAL ASPECTS - SOFTWARE REVERSE ENGINEERING AND COPYRIGHT: PAST, PRESENT AND FUTURE BRIAN C. BEHRENS*& REUVEN R. LEVARY** With technological advances in the field of computers, the le- gal world is discovering that the laws that apply to this field must advance as well. Copyright laws that currently govern the devel- opment of computer software are still quite ambiguous, with diffi- culties in their application and debates over the scope of the law. In light of conflicting case law, it is troublesome for an attorney to give clients advice on whether certain software development tech- niques violate copyright laws or carry other legal consequences. What is certain is that the courts are deciding more and more computer software cases.' As a result, future law regarding copy- right infringement in this area is still subject to change. -

Organization of Computer Programs Organization of Computer Programs
Organization of Computer Programs Organization of Computer Programs Hardware Organization of Computer Programs Operating System Hardware Organization of Computer Programs Application Application Program Program Operating System Hardware Interoperability Application Application Program Program Operating System Hardware Interoperability Application Application Program Program Operating System Hardware Interoperability Strategy #1 (e.g., Microsoft, Apple) Borland Microsoft Free access Microsoft Dell Interoperability Strategy #2 (e.g., Sega, Nintendo) Licensee Nintendo License fees Nintendo Nintendo Interoperability Strategy #3 (e.g., MAI Systems Corp.) MAI MAI No licenses MAI MAI Sega (CA9 1992) Licensed Sega Games Games License fees TMSS Sega Genesis III Sega (CA9 1992) Licensed Sega Games Games Accolade Games License fees TMSS Lock-out Sega Genesis III Sega (CA9 1992) Microcode (copied by Accolade) Licensed Sega Games Games Accolade Games License fees TMSS Lock-out Sega Genesis III Sega (CA9 1992) Licensed Sega Games Games Accolade Games License fees TMSS TMSS initialization Lock-out code Sega Genesis III Sega (CA9 1992) Licensed Sega Games Games Accolade Games License fees TMSS Sega Genesis III Reverse Engineering for Interoperability • Courts finding this to be fair use: – CAFC (Atari 1992 [dictum]; Bowers 2003 [dictum]) – CA5 (DSC Communications 1996) – CA 9 (Sega 1992; Sony 2000) – CA11 (Bateman 1996) • EC Directive 91/250, Art. 6, takes same position Fair Use Doctrine • Purpose and Character of the Use – commercial use – transformative uses – parody – propriety of defendant’s conduct • Nature of the Copyrighted Work – fictional works/factual works – unpublished/published • Amount of the portion used • Impact on Potential Market – rival definitions of “market” – only substitution effects are cognizable Fair Use Doctrine -- as applied in Sega • Purpose and Character of the Use – commercial use: purpose of A’s copying was “study” (noncom) – transformative uses: concede no transformative use – parody: n.a.