OES 2018 - What’S New
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Novell® File Reporter 實現智慧儲存
Business White Paper 檔案與網路服務 Novell® File Reporter 實現智慧 儲存、最佳化和安全性 目錄 頁 儲存分析與規劃的詳細檔案報告 . 2 儲存於網路的檔案數量漸增 . 2 資料儲存、法規遵循和成本 . 2 認識 Novell File Reporter . 3 Novell File Reporter 的運作方式 . 3 透過報告,克服檔案管理的挑戰 . 4 Novell File Reporter 的獨特優勢 . 4 總結 . 6 檔案與網路服務企業白皮書 Novell File Reporter 實現智慧儲存、最佳化和安全性 儲存分析與規劃的詳細檔案報告 Novell® File Reporter 能清點網路檔案系統,並提供您鉅細 靡遺的智慧檔案儲存,讓網路效能最佳化、保護網路安全、 實現高效率並符合法規標準。 儲存於網路的檔案數量漸增 器影像、雲端資料的重複副本,以及 時間長短 - 在某些情況下必須保存 基於種種理由,組織所儲存的檔案式 供行動智慧型手機使用者使用的文件 20 年以上。因此,能夠有效搜尋並找 資料量呈指數成長。我們知道,組織 和應用程式副本。 出所保留的文件,便成為組織必備的 必須遵循業界、政府和企業的法規與 首要能力。 規定,因此需要長期保存檔案。隨著 綜合這些因素,不難想見即使是規模 另一項法規遵循重點則是安全性。組 儲存裝置的價格越來越平易近人,IT 極小的組織,也可能儲存了以 TB 為單 織必須保護機密資料,遏止未經授權 便能給予使用者更多的網路磁碟空間 位的大量檔案式資料。 的存取。因此,網路管理員需要瞭解 配額,讓使用者可在網路上儲存更多 哪些人有權限存取網路上的哪些區 個人檔案。在應用程式方面,由於具 資料儲存、法規遵循和成本 域,以及這些權限源自何處。網路管 備諸多增強功能,因此每每隨著新版 日漸龐大的儲存量通常伴隨著可觀的 理員也需要掌握每一位使用者有權限 本推出而變得越來越龐大,且都必須 管理挑戰,其中之一就是檔案庫存的 存取的所有文件。 經由檔案方式 (而非資料庫) 來儲存與 問題。簡單來說,當貴組織內的使用 存取。 者在網路上儲存的檔案越來越多,要 最後,則是有關成本的問題。若對於 尋找檔案所在位置和辨識使用者所儲 貴組織資料儲存量的多寡、應儲存在 諸如虛擬伺服器、桌面系統虛擬化、 存的檔案也就更加困難。 主要或次要儲存裝置、是否儲存重複 雲端運算專案和行動運算等增強功 的檔案等問題,都缺乏基本認知的 能,使得資料中心的檔案數量倍增; 法規遵循的其中一項關鍵要素在於資 話,那又如何能確定每分錢都花在刀 這些檔案的形式包括已儲存的虛擬機 料保留,其中規定了必須保存資料的 口上呢? 2 儲存成本不只和儲存磁碟容量有關, 幫您計算部門或個人的儲存成本,甚 用者是否曾複製檔案、複製的檔案位 同時也攸關下列項目的開銷:儲存配 至能識別資料夾的存取權限,從而辨 於何處、使用者建立檔案的時間、使 置、耗電量、維護、額外硬體、漸增 認資料夾中包含的檔案。 用者上次修改檔案的時間、檔案所在 的管理成本、備份系統日益增加的成 之資料夾的許可資料等等。 本和複雜性,以及新添硬體所增加的 Novell File Reporter 的運作方式 佔地面積等。 在構成您網路的各種儲存裝置中,分 Novell File Reporter 會收集來自 NFR 佈著成千上萬個檔案、資料夾和磁碟 Agent 的掃描結果,進行壓縮後傳 由於遽增的儲存需求帶來了許多問 區所組成的大量資料 (以 TB 為單位), 送至 NFR Engine,並由其儲存至 題,因此在每個產業中,各種規模的 而我們所開發的 Novell -

General Specs Copying Connectivity
General Specs Part no. 27X0128 Packaged Size (mm - H x 24 x 178 x 191 mm W x D) Packaged Weight, kg 0.099 kg Copying Network Type IEEE 802.11 b/g/n Wireless SISO 1x1 Connectivity Network Type IEEE 802.11 b/g/n Wireless SISO 1x1 Connectors One USB port (Type B) for Configuration Network Protocol Support TCP/IP IPv6, TCP/IP IPv4, AppleTalk™, TCP, UDP Network Printing Methods LPR/LPD, Function may vary by printer or MFP., Direct IP (Port 9100), HTTP, Telnet, FTP, TFTP, Enhanced IP (Port 9400), ThinPrint .print integration, IPP 1.0, 1.1, 2.0 (Internet Printing Protocol) Network Management DHCP, APIPA (AutoIP), BOOTP, RARP, mDNS, IGMP, SLPv1, Bonjour, WINS, DDNS, SNMPv3, Function may Protocols vary by printer or MFP., SNMPv2c, Telnet, NTP, ICMP, DNS, ARP, HTTPs (SSL1 /TLS), Finger Network Security IPSec, SNMPv3, 802.1x Authentication: MD5, MSCHAPv2, LEAP, PEAP, TLS, TTLS Wireless Network WEP Encryption (64- and 128-bit key), 1x1 802.11i b/g/n 72Mbps, WPA2™ - Enterprise with Certificate Management, WPA2™ - Personal Supported Operating Systems Microsoft Windows Windows Server 2008 x64 running Terminal Services, Windows Server 2008 x64, Windows Server 2008 running Operating Systems Terminal Services, Windows 8.1, Windows Server 2008 R2 Supported running Terminal Services, Windows 8, Windows Server 2008, Windows Server 2008 R2, Windows 8 x64, Windows 7 x64, Windows Server 2012, Windows RT 8.1, Windows XP x64, Windows Server 2003 x64, Windows RT, Windows Server 2003, Windows Server 2012 R2, Windows XP, Windows Server 2003 x64 running -

Groupwise Mobility Quick Start for Microsoft Outlook Users
GroupWise Mobility Quick Start for Microsoft Outlook Users August 2016 GroupWise Mobility Service 2014 R2 allows the Microsoft Outlook client for Windows to run against a GroupWise backend via Microsoft ActiveSync 14.1 protocol. This document helps you set up your Outlook client to access your GroupWise account and provides known limitations you should be aware of while using Outlook against GroupWise. Supported Microsoft Outlook Clients CREATING THE GROUPWISE PROFILE MANUALLY Microsoft Outlook 2013 or 21016 for Windows 1 On the machine, open Control Panel > User Accounts and Family Safety. Microsoft Outlook Mobile App Adding a GroupWise Account to the Microsoft Outlook Client You must configure the Microsoft Outlook client in order to access your GroupWise account. The following instructions assume that the Outlook client is already installed on your machine. You can use the GroupWise Profile Setup utility to set the profile up automatically or you can manually create the GroupWise profile for Outlook. Using the GroupWise Profile Setup Utility Creating the GroupWise Profile Manually 2 Click Mail. 3 (Conditional) If a Mail Setup dialog box is displayed, USING THE GROUPWISE PROFILE SETUP UTILITY click Show Profiles to display the Mail dialog box. You must first obtain a copy of the GWProfileSetup.zip from If GroupWise is installed on the machine, the Profiles your system administrator before following the steps below list includes a GroupWise profile, as shown in the to create the profile on your workstation. following screenshot. You need to keep this profile and create a new profile. 1 Extract the GWProfileSetup.zip to a temporary location on your workstation. -

Micro Focus File Reporter 3.6 Installation Guide
Micro Focus File Reporter 3.6 Installation Guide January 6, 2020 Legal Notices Condrey Corporation makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Condrey Corporation reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Condrey Corporation makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Condrey Corporation reserves the right to make changes to any and all parts of the software at any time, without obligation to notify any person or entity of such revisions or changes. See the Software EULA for full license and warranty information with regard to the Software. Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classification to export, re-export, or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. Condrey Corporation assumes no responsibility for your failure to obtain any necessary export approvals. -

March/April 2006
The newsletter for IPFW computer users Information Technology Services March-April 2006 By Joseph McCormick Manager of Client Support his spring, most Indiana counties T will observe Daylight Savings Time Data Security and Your Workstation (DST) for the first time since 1970. In 2006, DST begins at 2 a.m. on the first Sunday in April (April 2) and ends at 2 option involves a reboot which With recent security incidents at a.m. on the last Sunday in October refreshes your workstation, and the (October 29). other campuses and businesses, it has next time you log in to the network, become imperative that we all take Because of modifications to the Trend OfficeScan antivirus steps to protect data accessed through GroupWise, to accommodate the software installed on your Windows our computers. Precautions should change to Daylight Savings Time, your workstation automatically updates. also be taken to protect data stored on calendar items scheduled between April Keep your workstation up-to- any portable devices such as laptops, 2 at 2:00 a.m. and October 29 at 2:00 date with vendor patches and virus disks or flash drives. Here are a few a.m. are now showing up an hour later protection by activating updates key steps that we can all do quickly to than originally scheduled. Unfortunately, promptly when you are signaled that increase security significantly. this problem was unavoidable as we they are ready. Windows XP/2000 adjusted the system to recognize Daylight users: when you see the “msg”. at the Savings time. bottom of your tool bar that says you Your cooperation is key to The only way to correct this have new updates, please click on the providing overall campus problem is to manually change your button and add your updates. -

Netbackup ™ Enterprise Server and Server 8.0 - 8.X.X OS Software Compatibility List Created on September 08, 2021
Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List Created on September 08, 2021 Click here for the HTML version of this document. <https://download.veritas.com/resources/content/live/OSVC/100046000/100046611/en_US/nbu_80_scl.html> Copyright © 2021 Veritas Technologies LLC. All rights reserved. Veritas, the Veritas Logo, and NetBackup are trademarks or registered trademarks of Veritas Technologies LLC in the U.S. and other countries. Other names may be trademarks of their respective owners. Veritas NetBackup ™ Enterprise Server and Server 8.0 - 8.x.x OS Software Compatibility List 2021-09-08 Introduction This Software Compatibility List (SCL) document contains information for Veritas NetBackup 8.0 through 8.x.x. It covers NetBackup Server (which includes Enterprise Server and Server), Client, Bare Metal Restore (BMR), Clustered Master Server Compatibility and Storage Stacks, Deduplication, File System Compatibility, NetBackup OpsCenter, NetBackup Access Control (NBAC), SAN Media Server/SAN Client/FT Media Server, Virtual System Compatibility and NetBackup Self Service Support. It is divided into bookmarks on the left that can be expanded. IPV6 and Dual Stack environments are supported from NetBackup 8.1.1 onwards with few limitations, refer technote for additional information <http://www.veritas.com/docs/100041420> For information about certain NetBackup features, functionality, 3rd-party product integration, Veritas product integration, applications, databases, and OS platforms that Veritas intends to replace with newer and improved functionality, or in some cases, discontinue without replacement, please see the widget titled "NetBackup Future Platform and Feature Plans" at <https://sort.veritas.com/netbackup> Reference Article <https://www.veritas.com/docs/100040093> for links to all other NetBackup compatibility lists. -
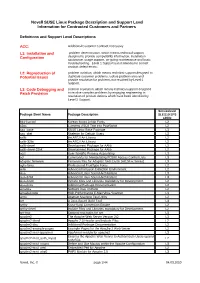
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP3 s390x 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-32bit An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 aalib-devel-32bit Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-32bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. L2 alsa-docs Additional Package Documentation. L2 amanda Network Disk Archiver L2 amavisd-new High-Performance E-Mail Virus Scanner L3 amtu Abstract Machine Test Utility L2 ant A Java-Based Build Tool L3 anthy Kana-Kanji Conversion Engine L2 anthy-devel Include Files and Libraries mandatory for Development. -

Freebsd Opengroupware - English
FreeBSD OpenGroupware - English FreeBSD As Basis For OpenGroupware.org PostgreSQL As Database FreeBSD can currently look back on a history of over 30 PostgreSQL, like BSD, originated at the University of Ca- years. It originated at the University of Berkeley and lifornia and is also distributed under the BSD license. It's FreeBSD evolved over a few intermediate steps into the project one of the oldest and most advanced object-relational founded in 1993 called FreeBSD. The supported architec- database management systems (ORDBMS) in the realm tures are the following: i386, amd64, Alpha, Itanium, of free software and looks back on a development of OpenGroupware.org SPARC, PPC (Mac) and others. over 15 years. PostgreSQL is largely conforming to the FreeBSD has very good support for multiprocessor sys- SQL92/SQL99 standards, that means that all functions in The ideal solution for professional the standards are available and behave as defined; that tems (SMP) and is distributed under the BSD license team communication on the Internet, which grants the user nearly every freedom and is free is not always the case with some commercial and non- commercial SQL database systems. of cost. Apart from having to name the origins of the with FreeBSD and PostgreSQL code, the user may use it in any which way he or she pleases. FreeBSD is a gift to humanity, we are pleased when you use it! FreeBSD has not only got many features, it also has a What is a groupware solution? huge amount of free and open software in its so-called Ports Collection. -

Relevé Des Frais Annuels De L'entente De Licence Destinée À L
Relevé des frais annuels de l’entente de licence destinée à l’enseignement postsecondaire AOÛT 2016 Les Informations de Programme scolaire Relient Les Instructions de Sélection de produit : As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). Sélectionnez un seul modèle : ___ Modèle ETP; ___ Modèle par poste de travail; ___ Modèle par poste de travail de service EMBALLER CALCUL INSTRUCTIONS : A. Place une marque dans le Modèle de colonne A Choisi la boîte des produits que vous souhaitez acheter OU choisir un Paquet de Valeur. Si un Paquet de Valeur n'est pas choisi, au moins quatre (4) les produits doivent être choisis. B. Calcule le Total A Emballé le Prix (TBP) en ajoutant les prix appropriés des produits choisis et le modèle d'évaluation approprié. C. Le Total A Emballé le Prix sera utilisé pour calculer les Frais annuels. Vous ne pouvez pas utiliser le modèle de FTE dans calculer vos Frais annuels à moins que votre population de FTE dépasse votre compte de poste de travail. POUR EMPECHER DES RETARDS DANS TRAITER VOTRE ORDRE DE RENOUVELLEMENT, S'IL VOUS PLAIT SOUMETTRE VOTRE FACTURE D'ACHAT ET VOTRE FEUILLE DE TRAVAIL COMPLETEE ENSEMBLE MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your ALA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. -

Designing a User Interface for the Innovative E-Mail Client Semester Thesis
Designing a User Interface for the Innovative E-mail Client Semester Thesis Student: Alexandra Burns Supervising Professor: Prof. Bertrand Meyer Supervising Assistants: Stephanie Balzer, Joseph N. Ruskiewicz December 2005 - April 2006 1 Abstract Email Clients have become a crucial application, both in business and for per- sonal use. The term information overload refers to the time consuming issue of keeping up with large amounts of incoming and stored email. Users face this problem on a daily basis and therefore benefit from an email client that allows them to efficiently search, display and store their email. The goal of this thesis is to build a graphical user interface for the innovative email client developed in a previous master thesis. It also explores the possibilities of designing a user interface outside of the business rules that apply for commercial solutions. 1 Contents 1 Introduction 4 2 Existing Work 6 2.1 ReMail ................................. 6 2.1.1 Methods ............................ 6 2.1.2 Problems Identified ...................... 7 2.1.3 Proposed Solutions ...................... 7 2.1.4 Assessment .......................... 8 2.2 Inner Circle .............................. 8 2.2.1 Methods ............................ 8 2.2.2 Problems Identified ...................... 9 2.2.3 Proposed Solutions ...................... 9 2.2.4 Assessment .......................... 10 2.3 TaskMaster .............................. 10 2.3.1 Methods ............................ 10 2.3.2 Problems Identified ...................... 11 2.3.3 Proposed Solution ...................... 11 2.3.4 Assessment .......................... 12 2.4 Email Overload ............................ 12 2.4.1 Methods ............................ 12 2.4.2 Problems Identified ...................... 13 2.4.3 Proposed Solutions ...................... 13 2.4.4 Assessment .......................... 14 3 Existing Solutions 16 3.1 Existing Email Clients ....................... -

Groupwise Internet Agent
GroupWise Internet Agent April 7, 2000 Novell Confidential Manual Rev 99a24 8 February 00 Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc. makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to notify any person or entity of such changes. This product may require export authorization from the U.S. Department of Commerce prior to exporting from the U.S. or Canada. Copyright © 1993-1999 Novell, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted without the express written consent of the publisher. U.S. Patent Nos. 4,555,775; 4,580,218; 5,412,772; 5,701,459; 5,717,912; 5,760,772; 5,870,739; 5,873,079; 5,884,304; 5,903,755; 5,913,209; 5,924,096; 5,946,467; D393,457 and U.S. Patents Pending. Novell, Inc. 122 East 1700 South Provo, UT 84606 U.S.A. www.novell.com GroupWise Internet Agent February 2000 104-001304-001 Online Documentation: To access the online documentation for this and other Novell products, and to get updates, see www.novell.com/documentation. -

OES 2015 SP1: Installation Guide Is Available at the Open Enterprise Server 2015 SP1 Documentation Website
Open Enterprise Server 2015 SP1 Installation Guide June 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy, and FIPS compliance, see https://www.novell.com/company/legal/. Copyright © 2016 Novell, Inc., a Micro Focus company. All Rights Reserved. Contents About This Guide 9 1 What’s New or Changed in the OES Install 11 1.1 What’s New (Update 28-OES 2015 SP1). .11 1.2 What’s New (OES 2015 SP1) . 11 1.3 What’s New (January 2016 eDirectory 8.8 SP8 Patch 6 Hot Patch 1). 12 1.4 What’s New (OES 2015) . 12 2 Preparing to Install OES 2015 SP1 15 2.1 Before You Install . 15 2.2 Meeting All Server Software and Hardware Requirements . 15 2.2.1 Server Software . 15 2.2.2 Server Hardware . 16 2.3 NetIQ eDirectory Rights Needed for Installing OES. 17 2.3.1 Rights to Install the First OES Server in a Tree . 17 2.3.2 Rights to Install the First Three Servers in an eDirectory Tree . 17 2.3.3 Rights to Install the First Three Servers in any eDirectory Partition . 17 2.4 Installing and Configuring OES as a Subcontainer Administrator . 17 2.4.1 Rights Required for Subcontainer Administrators . 18 2.4.2 Providing Required Rights to the Subcontainer Administrator for Installing and Managing Samba. 20 2.4.3 Starting a New Installation as a Subcontainer Administrator . 22 2.4.4 Adding/Configuring OES Services as a Different Administrator.