Comptia Security+ Pre-Approved Training for Comptia Security+ Continuing Education Units (Ceus)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
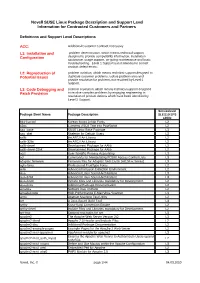
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP3 s390x 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-32bit An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 aalib-devel-32bit Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-32bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. L2 alsa-docs Additional Package Documentation. L2 amanda Network Disk Archiver L2 amavisd-new High-Performance E-Mail Virus Scanner L3 amtu Abstract Machine Test Utility L2 ant A Java-Based Build Tool L3 anthy Kana-Kanji Conversion Engine L2 anthy-devel Include Files and Libraries mandatory for Development. -

C:\Andrzej\PDF\ABC Nagrywania P³yt CD\1 Strona.Cdr
IDZ DO PRZYK£ADOWY ROZDZIA£ SPIS TREFCI Wielka encyklopedia komputerów KATALOG KSI¥¯EK Autor: Alan Freedman KATALOG ONLINE T³umaczenie: Micha³ Dadan, Pawe³ Gonera, Pawe³ Koronkiewicz, Rados³aw Meryk, Piotr Pilch ZAMÓW DRUKOWANY KATALOG ISBN: 83-7361-136-3 Tytu³ orygina³u: ComputerDesktop Encyclopedia Format: B5, stron: 1118 TWÓJ KOSZYK DODAJ DO KOSZYKA Wspó³czesna informatyka to nie tylko komputery i oprogramowanie. To setki technologii, narzêdzi i urz¹dzeñ umo¿liwiaj¹cych wykorzystywanie komputerów CENNIK I INFORMACJE w ró¿nych dziedzinach ¿ycia, jak: poligrafia, projektowanie, tworzenie aplikacji, sieci komputerowe, gry, kinowe efekty specjalne i wiele innych. Rozwój technologii ZAMÓW INFORMACJE komputerowych, trwaj¹cy stosunkowo krótko, wniós³ do naszego ¿ycia wiele nowych O NOWOFCIACH mo¿liwoYci. „Wielka encyklopedia komputerów” to kompletne kompendium wiedzy na temat ZAMÓW CENNIK wspó³czesnej informatyki. Jest lektur¹ obowi¹zkow¹ dla ka¿dego, kto chce rozumieæ dynamiczny rozwój elektroniki i technologii informatycznych. Opisuje wszystkie zagadnienia zwi¹zane ze wspó³czesn¹ informatyk¹; przedstawia zarówno jej historiê, CZYTELNIA jak i trendy rozwoju. Zawiera informacje o firmach, których produkty zrewolucjonizowa³y FRAGMENTY KSI¥¯EK ONLINE wspó³czesny Ywiat, oraz opisy technologii, sprzêtu i oprogramowania. Ka¿dy, niezale¿nie od stopnia zaawansowania swojej wiedzy, znajdzie w niej wyczerpuj¹ce wyjaYnienia interesuj¹cych go terminów z ró¿nych bran¿ dzisiejszej informatyki. • Komunikacja pomiêdzy systemami informatycznymi i sieci komputerowe • Grafika komputerowa i technologie multimedialne • Internet, WWW, poczta elektroniczna, grupy dyskusyjne • Komputery osobiste — PC i Macintosh • Komputery typu mainframe i stacje robocze • Tworzenie oprogramowania i systemów komputerowych • Poligrafia i reklama • Komputerowe wspomaganie projektowania • Wirusy komputerowe Wydawnictwo Helion JeYli szukasz ]ród³a informacji o technologiach informatycznych, chcesz poznaæ ul. -
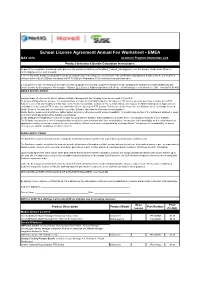
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.36 USD per enrollment or $35.70 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.25 plus 2 Additional products ($0.60 ea) = $3.45 total price x enrollment of 1,000 = Annual Fee $3,450. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. You may not use or allow the use of the Software other than for Your own internal purposes. -

Zenworks 2020 System Requirements October 2019
ZENworks 2020 System Requirements October 2019 The following sections provide the ZENworks 2020 system requirements for hardware and software: NOTE: For information about the platforms that are no longer supported by ZENworks 2020, refer to the ZENworks What’s New Reference Reference. “Primary Server Requirements” on page 1 “Virtual Appliance Requirements” on page 5 “Managed Device Requirements” on page 5 “Satellite Requirements” on page 15 “Database Requirements” on page 18 “Reporting Server Support” on page 19 “LDAP Directory Requirements” on page 20 “Inventoried-Only Device Requirements” on page 20 “Mobile Management Support” on page 23 “Administration Browser Requirements” on page 24 “Installation User Requirements” on page 24 “Supported Smart Cards and Smart Card Readers” on page 24 “Legal Notice” on page 24 Primary Server Requirements Ensure that the server where you install the Primary Server software meets the following requirements: NOTE: The operating systems listed below are the ones on which the ZENworks Primary Server software can be installed. The list does not necessarily represent the operating systems that ZENworks Patch Management can update. For this list, see the ZENworks Patch Management Content Report. ZENworks 2020 System Requirements 1 Item Requirements Additional Details Server Your server might be capable of handling tasks in For example, you might not want the Usage addition to the tasks that a Primary Server server to do the following: performs. However, we recommend that any server where you install the Primary Server Host NetIQ eDirectory software be used only for ZENworks. Host Active Directory Host Terminal Services Operating Windows 2012 Server x86_64 (Foundation, Installation on a server in a clustered System Essential, Standard, and Datacenter editions) environment is not supported. -

Novell® On-Demand Training
Library of Courses Anywhere, anytime access Updated: April 11, 2011 to valuable training at an incredible price. Novell® On-demand Training * Underlined titles have web links * Red titles are free learning site courses End-User Client Library • SUSE Linux Enterprise Server 10 Fundamentals (3071) First Look: • SUSE Linux Enterprise Server 10 Administration (3072) • SUSE Linux Enterprise Server 10 Advanced • SUSE® Linux Enterprise Desktop 10 Administration (3073) End User: • SUSE Linux Enterprise Server – Networking Services • Novell GroupWise® Client (PDFs) (3074) • Novell Teaming +Conferencing Client • SUSE Linux Enterprise Server – Security (PDFs) (3075) • SUSE Linux Enterprise Desktop 11 Administration (3104) • SUSE Linux Enterprise Desktop 11 Help Desk Administration (8009) • SUSE Linux Enterprise 11 for Solaris Data Center Library: Administration (9061) First Look: • Red Hat 5 to SUSE Linux Enterprise Server 11 Migration Overview • SUSE Linux Enterprise Server 11 • Migrating Red Hat 5 to SUSE Linux Enterprise 11 (8011) • SUSE Linux Enterprise Server 10 • PlateSpin® Workload Management Administration (8008) • SUSE Linux Enterprise Desktop 11 • PlateSpin Forge 2.5 • PlateSpin Recon 3.6 • Business Service Management: Introduction • PlateSpin Recon 3.5 to ITIL (8408) • PlateSpin Migrate 8.1 • Migrating from UNIX to SUSE Linux Enterprise • PlateSpin Migrate 8.0 Server (9052) • Introduction to Novell Cloud Manager (1404) • PlateSpin Recon: Consolidation Assessments and Data Center Management (8415) Quick Fix: • PlateSpin Migrate 8.1: The -

Novell Zenworks Mobile Management Datasheet
Data Sheet Endpoint Management Novell ZENworks Mobile Management Extend your endpoint management to all the mobile devices in your IT environment from a single administrative console. Protect yourself from risk with security policies and manage both employee-owned and company-owned devices. Product Overview If you answered yes to any of these questions, System Requirements Novell® ZENworks® Mobile Management pro- you already know how valuable ZENworks Please visit www.novell.com/zmm for detailed vides advanced device controls and policy Mo bile Management can be: It meets all of product specifications and system requirements. management for iOS and Android, and other these management challenges and many Ac tiveSync -enabled devices—all from a sin- more. track device use and the applications gle administrative console. The product ad- that users download onto their devices. dresses all of the pain points administrators Key Benefits BYOD support that helps you optimize and managers face to day, including bring- Novell ZENworks Mobile Management helps user productivity on a variety of device your-own-device policies (BYOD), security, your organization with: platforms—including iOS and Android, application management, asset and inventory and most other ActiveSync devices. management and compliance issues. Centralized management tools Security and compliance capabilities that make it easy to deploy new mobile that provide auditing and compliance Are your users bringing in their own iPads, devices in the workforce, whether the management tools so you know who is Androids and other devices, then asking devices are company issued or privately controlling what and how they are doing it. for access to corporate email? owned. -

School License Agreement Annual Fee Worksheet - USD DECEMBER 2017 Academic Program Information Link
School License Agreement Annual Fee Worksheet - USD DECEMBER 2017 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to EMEA_Contract_Admin@Micro Focus.com (for Europe, Middle East, Africa) or contractadmin@Micro Focus.com (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.50 USD per enrollment or $38.00 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.50 plus 2 Additional products ($0.60 ea) = $3.70 total price x enrollment of 1,000 = Annual Fee $3,700. MOBILE DEVICE LICENSE: Upon purchase of a license for ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. -

Common Package and Patch Management for SUSE Linux
ZYPP common package and patch management for SUSE Linux Duncan Mac-Vicar P. Software Engineer, YaST Agenda ZYPP • Package management • How was it done before • ZYPP • ZYPP features • What is new? • The future © March 9, 2007 Novell Inc. 2 Package management • Automatic resolving of dependencies • Automatic fetching of packages • Handling of different installation medias • Update system with latest software available. YaST pkg-manager, apt, smart... © March 9, 2007 Novell Inc. 3 Problems with old pkg-manager - Only knew about packages - Selections were handled by the YaST UI - Patches were handled by YOU Enterprise path: • ZenWorks used libredcarpet © March 9, 2007 Novell Inc. 4 ZYPP: Overview ZYPP • Abstract resolvables: • packages, patches, messages, scripts, selections, patterns, languages, system, etc. • Better solver • Modern extensible design • new targets, source types, resolvable types, capabilities © March 9, 2007 Novell Inc. 6 ZYPP solver Source (yum) Target (rpm) Source (DVD) Pool Target (modalias) Pool Target (storage) zypp YaST ZenWorks 7 Introducing Capabilities • Grouped in: • requires, conflicts, suggests, freshens, supplements, prerequires, obsoletes, etc • Are created from a resolvable kind, and a parseable string. • Most common case, a package, and a edition: • REQUIRES, package, “kdelibs > 3.2.1” • Crazy case: REQUIRES, system, “uptime:2 years” © March 9, 2007 Novell Inc. 8 Hardware capabilities Provides capabilities based on the running system, like hardware. system PROVIDES: modalias(pci:v0000104Cd0000840[01]sv*sd*bc*sc*i*) (at runtime!) wlan-kmp-default-1_2.6.16.11_4-13.i586.rpm SUPPLEMENTS: modalias(kernel-default:pci:v0000104Cd0000840[01]sv*sd*bc*sc*i*) modalias(kernel-default:pci:v0000104Cd00009066sv*sd*bc*sc*i*) modalias(kernel-default:pci:v000010B7d00006000sv*sd*bc*sc*i*) © March 9, 2007 Novell Inc. -

HTTP: IIS "Propfind" Rem HTTP:IIS:PROPFIND Minor Medium
HTTP: IIS "propfind"HTTP:IIS:PROPFIND RemoteMinor DoS medium CVE-2003-0226 7735 HTTP: IkonboardHTTP:CGI:IKONBOARD-BADCOOKIE IllegalMinor Cookie Languagemedium 7361 HTTP: WindowsHTTP:IIS:NSIISLOG-OF Media CriticalServices NSIISlog.DLLcritical BufferCVE-2003-0349 Overflow 8035 MS-RPC: DCOMMS-RPC:DCOM:EXPLOIT ExploitCritical critical CVE-2003-0352 8205 HTTP: WinHelp32.exeHTTP:STC:WINHELP32-OF2 RemoteMinor Buffermedium Overrun CVE-2002-0823(2) 4857 TROJAN: BackTROJAN:BACKORIFICE:BO2K-CONNECT Orifice 2000Major Client Connectionhigh CVE-1999-0660 1648 HTTP: FrontpageHTTP:FRONTPAGE:FP30REG.DLL-OF fp30reg.dllCritical Overflowcritical CVE-2003-0822 9007 SCAN: IIS EnumerationSCAN:II:IIS-ISAPI-ENUMInfo info P2P: DC: DirectP2P:DC:HUB-LOGIN ConnectInfo Plus Plus Clientinfo Hub Login TROJAN: AOLTROJAN:MISC:AOLADMIN-SRV-RESP Admin ServerMajor Responsehigh CVE-1999-0660 TROJAN: DigitalTROJAN:MISC:ROOTBEER-CLIENT RootbeerMinor Client Connectmedium CVE-1999-0660 HTTP: OfficeHTTP:STC:DL:OFFICEART-PROP Art PropertyMajor Table Bufferhigh OverflowCVE-2009-2528 36650 HTTP: AXIS CommunicationsHTTP:STC:ACTIVEX:AXIS-CAMERAMajor Camerahigh Control (AxisCamControl.ocx)CVE-2008-5260 33408 Unsafe ActiveX Control LDAP: IpswitchLDAP:OVERFLOW:IMAIL-ASN1 IMail LDAPMajor Daemonhigh Remote BufferCVE-2004-0297 Overflow 9682 HTTP: AnyformHTTP:CGI:ANYFORM-SEMICOLON SemicolonMajor high CVE-1999-0066 719 HTTP: Mini HTTP:CGI:W3-MSQL-FILE-DISCLSRSQL w3-msqlMinor File View mediumDisclosure CVE-2000-0012 898 HTTP: IIS MFCHTTP:IIS:MFC-EXT-OF ISAPI FrameworkMajor Overflowhigh (via -

Using Novell® Zenworks®
U NIVERSITY OF SOUTHERN CALIFORNIA USING NOVELL® ZENWORKS® USER’S GUIDE JULY 2013 U NIVERSITY OF SOUTHERN CALIFORNIA © 2013 UNIVERSITY OF SOUTHERN CALIFORNIA. All rights reserved. This manual, as well as the data and software implementation described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment on the part of the University of Southern California. Except as permitted by such license, no part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the prior written permission of the University of Southern California. The data and software implementation, as with all technical and computer-aided design software, is a tool intended to be used by trained professionals only. The data and the software implementation is not a substitute for the professional judgment of trained professionals. The software implementation is intended to assist with product design and is not a substitute for independent testing of product stress, safety and utility. The University of Southern California assumes no liability for any error or inaccuracies that may appear in this manual. The University of Southern California makes no warranties with respect to this manual and disclaims any implied warranties of merchantability and fitness for a particular purpose. Novell and Novell ZENworks are registered trademarks of the Novell Corporation. U.S. -

Novell Certificate Server Apis --- Overview Novdocx (ENU) 01 February 2006
NDK: Novell Certificate Server APIs --- Overview novdocx (ENU) 01 February 2006 February 01 (ENU) novdocx Novell Developer Kit www.novell.com NOVELL CERTIFICATE SERVER™ March 1, 2006 APIS — OVERVIEW novdocx (ENU) 01 February 2006 February 01 (ENU) novdocx Novell Trademarks AppNotes is a registered trademark of Novell, Inc. AppTester is a registered trademark of Novell, Inc. in the United States. ASM is a trademark of Novell, Inc. Beagle is a trademark of Novell, Inc. BorderManager is a registered trademark of Novell, Inc. BrainShare is a registered service mark of Novell, Inc. in the United States and other countries. C3PO is a trademark of Novell, Inc. Certified Novell Engineer is a service mark of Novell, Inc. Client32 is a trademark of Novell, Inc. CNE is a registered service mark of Novell, Inc. ConsoleOne is a registered trademark of Novell, Inc. Controlled Access Printer is a trademark of Novell, Inc. Custom 3rd-Party Object is a trademark of Novell, Inc. DeveloperNet is a registered trademark of Novell, Inc., in the United States and other countries. DirXML is a registered trademark of Novell, Inc. eDirectory is a trademark of Novell, Inc. Excelerator is a trademark of Novell, Inc. exteNd is a trademark of Novell, Inc. exteNd Director is a trademark of Novell, Inc. exteNd Workbench is a trademark of Novell, Inc. FAN-OUT FAILOVER is a trademark of Novell, Inc. GroupWise is a registered trademark of Novell, Inc., in the United States and other countries. Hardware Specific Module is a trademark of Novell, Inc. Hot Fix is a trademark of Novell, Inc. Hula is a trademark of Novell, Inc. -

Novell Administration on a Mac Suggestions by Johnnie Odom Macs on Novell Networks?
Novell Administration on a Mac Suggestions by Johnnie Odom Macs on Novell Networks? • I appreciate fine products, obviously. • Great servers (Novell) and great clients (Apple) • Also, like my machine to Just Work • Servers give me more than enough challenge without wrestling with sound card drivers. • And I think Macs now have the advantage when administering Attachmate products. Cheats: Web Interfaces • What's Hot? Mobile • What Powers Most Mobile Browsers? • WebKit! • Chrome, Safari, Opera, Konqueror all use WebKit. The world is no longer IE and Firefox. • GroupWise Windermere web administration officially supported on iPad • WebKit! • ZENworks Configuration Console complains in Safari, but works. Firefox is fine. • iManager, Remote Manager, iMonitor, Kanaka Admin work fine • Jury still out on File Reporter 2.0 Cheats: Windows Virtualization • VMWare Fusion runs Windows very nicely. • ZENworks Windows Policy Editor • But then, policies are always edited on the platform to which they apply • ZAV • ConsoleOne • Storage Manager and Legacy File Reporter • Designer with JClient (“Live” Button) • Full Mac support coming to Designer • And to run test eDir you will need to virtualize Windows or Linux. OS X as Unix • OS X certified Unix by the Open Group • Ironically Linux is not • OS X has a Unix layer, but most of its characteristic properties do not come from Unix. • Different networking, directory services, file system, windowing etc. • Also, many POSIX calls get translated as Mach kernel calls. • But enough Linux compatibility is present to make an OS X machine an attractive alternative to a SLED station. • Less screaming at workstation than most Linux distros. SSH and X-Windows • OS X has full SSH support in Terminal and OS • With XQuartz, supports remotely running X-Windows applications via tunnel • + "ssh -X user@servername" • + YaST works very well this way.