MI Reporting Requirements
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Polimetriche Per Linea STIBM Area Nord.Xlsx
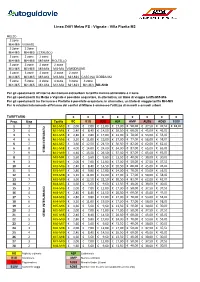
Linea Z401 Melzo FS - Vignate - Villa Fiorita M2 MELZO 2 zone Mi4-Mi5 VIGNATE 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 CERNUSCO 2 zone 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 Mi3-Mi4 PIOLTELLO 3 zone 3 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 VIMODRONE 3 zone 3 zone 2 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 5 zone 5 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi5 Mi1-Mi5 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Melzo e Vignate è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi5-Mi6 Per gli spostamenti tra Cernusco e Pioltello è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 -

A Visual Motion Detection Circuit Suggested by Drosophila Connectomics
ARTICLE doi:10.1038/nature12450 A visual motion detection circuit suggested by Drosophila connectomics Shin-ya Takemura1, Arjun Bharioke1, Zhiyuan Lu1,2, Aljoscha Nern1, Shiv Vitaladevuni1, Patricia K. Rivlin1, William T. Katz1, Donald J. Olbris1, Stephen M. Plaza1, Philip Winston1, Ting Zhao1, Jane Anne Horne2, Richard D. Fetter1, Satoko Takemura1, Katerina Blazek1, Lei-Ann Chang1, Omotara Ogundeyi1, Mathew A. Saunders1, Victor Shapiro1, Christopher Sigmund1, Gerald M. Rubin1, Louis K. Scheffer1, Ian A. Meinertzhagen1,2 & Dmitri B. Chklovskii1 Animal behaviour arises from computations in neuronal circuits, but our understanding of these computations has been frustrated by the lack of detailed synaptic connection maps, or connectomes. For example, despite intensive investigations over half a century, the neuronal implementation of local motion detection in the insect visual system remains elusive. Here we develop a semi-automated pipeline using electron microscopy to reconstruct a connectome, containing 379 neurons and 8,637 chemical synaptic contacts, within the Drosophila optic medulla. By matching reconstructed neurons to examples from light microscopy, we assigned neurons to cell types and assembled a connectome of the repeating module of the medulla. Within this module, we identified cell types constituting a motion detection circuit, and showed that the connections onto individual motion-sensitive neurons in this circuit were consistent with their direction selectivity. Our results identify cellular targets for future functional investigations, and demonstrate that connectomes can provide key insights into neuronal computations. Vision in insects has been subject to intense behavioural1,physiological2 neuroanatomy14. Given the time-consuming nature of such recon- and anatomical3 investigations, yet our understanding of its underlying structions, we wanted to determine the smallest medulla volume, neural computations is still far from complete. -

Michigan-Specific Reporting Requirements
Version: February 28, 2020 MEDICARE-MEDICAID CAPITATED FINANCIAL ALIGNMENT MODEL REPORTING REQUIREMENTS: MICHIGAN-SPECIFIC REPORTING REQUIREMENTS Issued February 28, 2020 MI-1 Version: February 28, 2020 Table of Contents Michigan-Specific Reporting Requirements Appendix ......................................... MI-3 Introduction ....................................................................................................... MI-3 Definitions .......................................................................................................... MI-3 Variations from the Core Reporting Requirements Document ..................... MI-4 Quality Withhold Measures .............................................................................. MI-5 Reporting on Assessments and IICSPs Completed Prior to First Effective Enrollment Date ................................................................................. MI-6 Guidance on Assessments and IICSPs for Members with a Break in Coverage ............................................................................................................ MI-6 Reporting on Passively Enrolled and Opt-In Enrolled Members .................. MI-8 Reporting on Disenrolled and Retro-disenrolled Members ........................... MI-9 Hybrid Sampling ................................................................................................ MI-9 Value Sets ........................................................................................................ MI-10 Michigan’s Implementation, Ongoing, -

UK Eyes Alpha by the Same Author UK Eyes Alpha Big Boys' Rules: the SAS and the Secret Struggle Against the IRA Lnside British Lntelligence
UK Eyes Alpha By the same author UK Eyes Alpha Big Boys' Rules: The SAS and the secret struggle against the IRA lnside British lntelligence Mark Urban tr firhrr anr/ fulrr' ft For Ruth and Edwin Contents lntroduction Part One The First published in I996 1 Coming Earthquake 3 and Faber Limited by Faber 2 A Dark and Curious Shadow 13 3 Queen Square London vcrN JAU 3 The Charm Offensive 26 Typeset by Faber and Faber Ltd Printed in England by Clays Ltd, St Ives plc 4 Most Ridiculed Service 42 All rights reserved 5 ZIRCON 56 O Mark Urban, 1996 6 Springtime for Sceptics 70 Mark Urbar-r is hereby identified as author of 7 A Brilliant Intelligence Operation 84 this work in accordance with Section 77 of the Copyright, Designs and Patents Act 1988 8 The \7all Comes Tumbling Down 101 A CIP rccord for this book is available from the Part Two British Library 9 Supergun LL7 tsnN o-57r-r7689-5 10 Black Death on the Nevsky Prospekt L29 ll Assault on Kuwait L43 12 Desert Shield 153 13 Desert Storm 165 14 Moscow Endgame LA2 Part Three l5 An Accidcnt of History L97 l(r Irrlo thc ll:rllirrn 2LO tt),)B / (,1,1 l, I Qulgrnirc 17 Time for Revenge 22L lntroduction 18 Intelligence, Power and Economic Hegemony 232 19 Very Huge Bills 245 How good is British intelligence? What kind of a return do ministers and officials get 20 The Axe Falls 2il for the hundreds of millions of pounds spent on espionage each year? How does this secret establishment find direction and purpose 2l Irish Intrigues 269 in an age when old certainties have evaporated? Very few people, even in Conclusion 286 Whitehall, would feel confident enough to answer these questions. -

Cambia Il Modo Di Viaggiare
Cambia il modo di viaggiare Nuovo sistema tariffario integrato dei mezzi pubblici www.trenord.it | App Trenord Indice 11 Il sistema tariffario integrato del bacino di mobilità (STIBM) 6 1.1 La suddivisione del territorio del bacino di mobilità in zone tariffarie 6 Tabella 1 Elenco in ordine alfabetico dei comuni ubicati nella zona tariffaria denominata Mi3 7 Tabella 2 Elenco in ordine alfabetico dei comuni ubicati nelle zone tariffarie Mi4, Mi5, Mi6, Mi7, Mi8, Mi9 8 Mappa del sistema tariffario integrato del bacino di mobilità (stibm) Milano - Monza Brianza 12 1.2 Il calcolo della tariffa 14 1.3 Le principali novità del nuovo sistema tariffario 15 22 Tipologie di spostamento e titoli di viaggio 16 2.1 Per spostarsi a Milano 16 2.2 Per spostarsi tra Milano e le località extraurbane 16 2.3 Per spostarsi tra località extraurbane senza attraversare i confini di Milano 17 2.4 Per spostarsi tra località extraurbane attraversando i confini di Milano 17 33 I nuovi titoli di viaggio 18 3.1 Titoli di viaggio ordinari 18 3.2 Titoli di viaggio agevolati e gratuità per ragazzi 19 3.3 Le informazioni presenti sul titolo di viaggio 20 3.4 Regole generali di utilizzo del titolo di viaggio 21 3.5 Il Biglietto Chip On Paper 22 44 Tariffe dei titoli di viaggio ordinari e dei titoli di viaggio agevolati 24 Tabella 3 Biglietti ordinari e altri titoli di viaggio occasionali 25 Tabella 4 Abbonamenti ordinari 26 Tabella 5 Abbonamenti agevolati 27 2 | IL NUOVO SISTEMA TARIFFARIO INTEGRATO - MILANO - MONZA BRIANZA 3 IL NUOVO SISTEMA Mi9 TARIFFARIO INTEGRATO MILANO -

How Intelligence Agencies Are Adapting to Cyber
http://researchcommons.waikato.ac.nz/ Research Commons at the University of Waikato Copyright Statement: The digital copy of this thesis is protected by the Copyright Act 1994 (New Zealand). The thesis may be consulted by you, provided you comply with the provisions of the Act and the following conditions of use: Any use you make of these documents or images must be for research or private study purposes only, and you may not make them available to any other person. Authors control the copyright of their thesis. You will recognise the author’s right to be identified as the author of the thesis, and due acknowledgement will be made to the author where appropriate. You will obtain the author’s permission before publishing any material from the thesis. Intelligence Agencies in Cyberspace: Adapting the Intelligence Cycle to Cyber Threats and Opportunities A thesis submitted in partial fulfilment of the requirements for the degree of Master of Social Sciences at The University of Waikato by Jedediah Warwick Greenwood 2020 1 Abstract Intelligence has grown and changed dramatically over the past hundred years with the advent of cyberspace. This thesis will begin by examining how the intelligence cycle has adapted to accommodate cyber threats and opportunities, before conducting three national case studies examining the organisational changes in the signals intelligence agencies in New Zealand, the United Kingdom, and the United States of America. It will utilise the analysis of how the intelligence cycle and States have grown to accommodate cyber phenomenon and will conduct two case studies on the recent events concerning Huawei and the hacking of the 2016 US Election. -

DEFENCE STRATEGIC COMMUNICATIONS the Official Journal of the NATO Strategic Communications Centre of Excellence
ISSN 2500-9478 Volume 1 | Number 1 | Winter 2015 DEFENCE STRATEGIC COMMUNICATIONS The official journal of the NATO Strategic Communications Centre of Excellence Russia’s 21st century information war. Moving past the ‘Funnel’ Model of Counterterrorism Communication. Assessing a century of British military Information Operations. Memetic warfare. The constitutive narratives of Daesh. Method for minimizing the negative consequences of nth order effects in StratCom. The Narrative and Social Media. Public Diplomacy and NATO. 2 ISSN 2500-9478 Defence Strategic Communications Editor-in-Chief Dr. Steve Tatham Editor Anna Reynolds Production and Copy Editor Linda Curika Editorial Board Matt Armstrong, MA Dr. Emma Louise Briant Dr. Nerijus Maliukevicius Thomas Elkjer Nissen, MA Dr. Žaneta Ozolina Dr. Agu Uudelepp Dr. J. Michael Waller Dr. Natascha Zowislo-Grünewald “Defence Strategic Communications” is an international peer-reviewed journal. The journal is a project of the NATO Strategic Communications Centre of Excellence (NATO StratCom COE). It is produced for NATO, NATO member countries, NATO partners, related private and public institutions, and related individuals. It does not represent the opinions or policies of NATO or NATO StratCom COE. The views presented in the following articles are those of the authors alone. © All rights reserved by the NATO StratCom COE. Articles may not be copied, reproduced, distributed or publicly displayed without reference to the NATO StratCom COE and the academic journal. NATO Strategic Communications Centre of Excellence Riga, Kalnciema iela 11b, Latvia LV1048 www.stratcomcoe.org Ph.: 0037167335463 [email protected] 3 INTRODUCTION I am delighted to welcome you to the first edition of ‘Defence Strategic Communications’ Journal. -

Room 40 and German Intrigues in Morocco: Re-Assessing the Operational Impact of Diplomatic Cryptanalysis During World War I
Room 40 and German intrigues in Morocco: re-assessing the operational impact of diplomatic cryptanalysis during World War I Harry Richards University of Portsmouth ABSTRACT During World War I, Germany sought to provoke numerous insurrections throughout the British and French Empires. Examining the influence of signals intelligence within one of these colonial settings provides an opportunity to measure the operational importance of wartime cryptanalysis. Through a careful analysis of the original intercepts, this article reconstructs the responses of Room 40, the Admiralty’s cryptology department, to Germany’s Moroccan intrigues and highlights the development of intelligence practices. It argues that strategies to deploy diplomatic intelligence emerged gradually, but that Germany’s enduring support for Moroccan dissidents suggests diplomatic cryptanalysis only secured modest results within an operational context. In the autumn of 1915, the Director of Naval Intelligence, Captain (later Admiral Sir) William Reginald Hall, commissioned George Young to lead a political section within Room 40 that was designed to break Germany’s diplomatic codes. Despite Room 40’s early progress against Germany’s naval communications, their diplomatic codes were unsystematic, which made them far more difficult to penetrate since the numerical order of the figure group was entirely unrelated to the alphabetical order of the vocabulary. The political branch secured some minor success against Germany’s Foreign Office codes in the winter of 1915, but with the -

MI6: the History of the Secret Intelligence Service 1909-1949 Free
FREE MI6: THE HISTORY OF THE SECRET INTELLIGENCE SERVICE 1909-1949 PDF Keith Jeffery | 864 pages | 06 Jun 2011 | Bloomsbury Publishing PLC | 9781408810057 | English | London, United Kingdom The Secret History of MI6 by Keith Jeffery Goodreads helps you keep track of books you want to read. Want to Read saving…. Want to Read Currently Reading Read. Other editions. Enlarge cover. Error rating book. Refresh and try again. Open Preview See a Problem? Details if other :. Thanks for telling us about the problem. Return to Book Page. The authorized history of the world's oldest foreign intelligence service, drawing on hitherto secret documents. Britain's Secret Intelligence Service MI6 was born a century ago amid fears of the rising power of other countries, especially Germany. This revelatory account The authorized history of the world's oldest foreign intelligence service, drawing on hitherto secret documents. This revelatory account draws on a wealth of archival materials never before seen by outsiders to unveil the inner workings of the world's 1st spy agency. MI6's early days were haphazard but it was quickly forged into an effective organization during WWI. During the war years, MI6 also formed ties with the USA--harbingers of a relationship that would become vital to both. The interwar years were nominally peaceful, but Britain perceived numerous threats, all of which MI6 was expected to keep tabs on. The aftermath of WWII was as dramatic as the war itself had been, because saw not only the end of the British Empire but also the MI6: The History of the Secret Intelligence Service 1909-1949 of a new sort of conflict--the Cold War. -

2021 Game Schedule
Mooresville Baseball League - 2021 Game Schedule Baseball MINOR ROOKIE PEEWEE INSTRUCTIONAL MAJOR Softball STB 7-8U (CP) 9-10U (KP) 11-12U (S) Opening Day - April 17 May 17 - May 22 Diamond Diamond Date Day Time Date Day Time 1 2 3 4 5 6 1 2 3 4 5 6 9:00 IN1-IN2 IN3-IN8 MA1-MA2 MA3-MA5 IN4-IN7 17-May Mon 6:00 S1-S2 IN2-IN7 MA5-MA1 MA2-MA4 MI2 - MI5 11:00 MI2 - MI1 MI3 - MI8 MI4 - MI7 MI5 - MI6 STB1-STB2 18-May Tue 6:00 MI2 - MI1 MI3 - MI8 MI4 - MI7 MI5 - MI6 17-Apr Sat 1:00 PW1-PW2 PW3-PW10 PW4-PW9 PW5-PW8 PW6-PW7 19-May Wed 6:00 S2-S3 IN3-IN6 MA2-MA5 MA4-MA3 PW2-PW9 3:00 R1-R4 R2-R3 CP1-CP2 CP3-CP4 KP1-KP2 20-May Thu 6:00 MI3 - MI4 MI1 - MI7 MI8 - MI6 MI2 - MI5 5:00 KP3-KP4 IN5-IN6 STB3-STB4 STB5-STB6 21-May Fri 6:00 CP2-CP3 CP4-CP1 KP1-KP2 KP3-KP4 9:00 IN4-IN5 IN8-IN1 STB3-STB6 STB4-STB1 April 19 - April 24 11:00 R3-R1 R4-R2 STB2-STB5 Diamond 22-May Sat 1:00 PW3-PW8 PW1-PW10 PW5-PW6 PW4-PW7 Date Day Time 1 2 3 4 5 6 3:00 19-Apr Mon 6:00 S1-S2 R1-R4 MA3-MA2 MA4-MA1 5:00 20-Apr Tue 6:00 Cancel Cancel Cancel Cancel 21-Apr Wed 6:00 Cancel Cancel Cancel Cancel May 24 - May 29 22-Apr Thu 6:00 S2-S3 R2-R3 MA1-MA3 MA5-MA4 IN8-IN6 Diamond Date Day Time 23-Apr Fri 6:00 PW2-PW3 PW1-PW7 PW8-PW6 PW9-PW5 PW10-PW4 1 2 3 4 5 6 9:00 IN3-IN4 IN2-IN5 STB1-STB6 STB2-STB4 IN1-IN7 24-May Mon 6:00 S3-S1 KP2-KP3 MA1-MA2 MA3-MA5 STB2-STB4 11:00 R1-R2 R3-R4 STB3-STB5 PW7-PW8 PW5-PW10 25-May Tue 6:00 MI6 - MI2 MI7 - MI8 MI4 - MI1 MI5 - MI3 STB1-STB6 24-Apr Sat 1:00 CP3-CP1 CP2-CP4 PW3-PW1 PW4-PW2 26-May Wed 6:00 S1-S2 KP4-KP1 MA3-MA2 MA4-MA1 3:00 27-May Thu 6:00 -

A Connectome Based Hexagonal Lattice Convolutional Network Model of the Drosophila Visual System
A Connectome Based Hexagonal Lattice Convolutional Network Model of the Drosophila Visual System Fabian David Tschopp Michael B. Reiser Institute of Neuroinformatics Janelia Research Campus University of Zurich and ETH Zurich Howard Hughes Medical Instutute [email protected] [email protected] Srinivas C. Turaga Janelia Research Campus Howard Hughes Medical Instutute [email protected] Abstract What can we learn from a connectome? We constructed a simplified model of the first two stages of the fly visual system, the lamina and medulla. The resulting hexagonal lattice convolutional network was trained using backpropagation through time to perform object tracking in natural scene videos. Networks initialized with weights from connectome reconstructions automatically discovered well-known orientation and direction selectivity properties in T4 neurons and their inputs, while networks initialized at random did not. Our work is the first demonstration, that knowledge of the connectome can enable in silico predictions of the functional properties of individual neurons in a circuit, leading to an understanding of circuit function from structure alone. 1 Introduction Universal function approximation results for artificial neural networks [1, 2] imply that many possible neural network architectures, with different connectivity matrices and different activation functions, can compute the same function. This suggests that it is difficult to predict the precise neural circuitry underlying a given neural computation. For this reason, we have many different proposals for instance, for how visual motion is computed through elementary motion detectors (EMD) such as arXiv:1806.04793v2 [q-bio.NC] 24 Jun 2018 Barlow-Levick [3] and Hassenstein-Reichardt [4], and how neural signals might be integrated [5, 6]. -

CRS Coordinators Manual
320 MAP INFORMATION SERVICE—Summary Maximum credit: 90 points 322 Elements a. Basic FIRM information (MI1): 30 points for providing basic information found on a Flood Insurance Rate Map (FIRM) that is needed to write a flood insurance policy. b. Additional FIRM information (MI2): 20 points for providing information that is shown on most FIRMs, such as protected coastal barriers, floodways, or lines demarcating wave action. c. Problems not shown on the FIRM (MI3): Up to 20 points for providing information about flood problems other than those shown on the FIRM. d. Flood depth data (MI4): Up to 20 points for providing information about flood depths. e. Special flood-related hazards (MI5): Up to 20 points for providing information about special flood-related hazards, such as erosion, ice jams, or tsunamis. f. Historical flood information (MI6): Up to 20 points for providing information about past flooding at or near the site in question. g. Natural floodplain functions (MI7): Up to 20 points for providing information about areas that should be protected because of their natural floodplain functions. Credit Criteria Credit criteria for this activity are described in Section 321.b. Each element has additional criteria specific to that element. Impact Adjustment There is no impact adjustment for this activity. Documentation Provided by the Community The documentation needed for this activity is described in Section 325. CRS Coordinator’s Manual 320-1 Edition: 2017 Map Information Service 320 MAP INFORMATION SERVICE The OBJECTIVE of this activity is to provide inquirers with information about the local flood hazard and about flood-prone areas that need special protection because of their natural functions.