How Intelligence Agencies Are Adapting to Cyber
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Threat Defense: Cyber Deception Approach and Education for Resilience in Hybrid Threats Model
S S symmetry Article Threat Defense: Cyber Deception Approach and Education for Resilience in Hybrid Threats Model William Steingartner 1,* , Darko Galinec 2 and Andrija Kozina 3 1 Faculty of Electrical Engineering and Informatics, Technical University of Košice, Letná 9, 042 00 Košice, Slovakia 2 Department of Informatics and Computing, Zagreb University of Applied Sciences, Vrbik 8, 10000 Zagreb, Croatia; [email protected] 3 Dr. Franjo Tudman¯ Croatian Defence Academy, 256b Ilica Street, 10000 Zagreb, Croatia; [email protected] * Correspondence: [email protected] Abstract: This paper aims to explore the cyber-deception-based approach and to design a novel conceptual model of hybrid threats that includes deception methods. Security programs primarily focus on prevention-based strategies aimed at stopping attackers from getting into the network. These programs attempt to use hardened perimeters and endpoint defenses by recognizing and blocking malicious activities to detect and stop attackers before they can get in. Most organizations implement such a strategy by fortifying their networks with defense-in-depth through layered prevention controls. Detection controls are usually placed to augment prevention at the perimeter, and not as consistently deployed for in-network threat detection. This architecture leaves detection gaps that are difficult to fill with existing security controls not specifically designed for that role. Rather than using prevention alone, a strategy that attackers have consistently succeeded against, defenders Citation: Steingartner, W.; are adopting a more balanced strategy that includes detection and response. Most organizations Galinec, D.; Kozina, A. Threat Defense: Cyber Deception Approach deploy an intrusion detection system (IDS) or next-generation firewall that picks up known attacks and Education for Resilience in or attempts to pattern match for identification. -
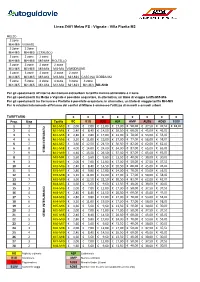
Polimetriche Per Linea STIBM Area Nord.Xlsx
Linea Z401 Melzo FS - Vignate - Villa Fiorita M2 MELZO 2 zone Mi4-Mi5 VIGNATE 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 CERNUSCO 2 zone 2 zone 2 zone Mi4-Mi5 Mi4-Mi5 Mi3-Mi4 PIOLTELLO 3 zone 3 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 VIMODRONE 3 zone 3 zone 2 zone 2 zone 2 zone Mi3-Mi5 Mi3-Mi5 Mi3-Mi4 Mi3-Mi4 Mi3-Mi4 CASCINA GOBBA M2 5 zone 5 zone 4 zone 4 zone 3 zone 3 zone Mi1-Mi5 Mi1-Mi5 Mi1-Mi4 Mi1-Mi4 Mi1-Mi3 Mi1-Mi3 MILANO Per gli spostamenti all'interno dei Comuni extraurbani la tariffa minima utilizzabile è 2 zone Per gli spostamenti tra Melzo e Vignate è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi5-Mi6 Per gli spostamenti tra Cernusco e Pioltello è possibile acquistare, in alternativa, un titolo di viaggio tariffa Mi4-Mi5 Per le relazioni interamente all'interno dei confini di Milano è ammesso l'utilizzo di mensili e annuali urbani TARIFFARIO €€€€€€€€ Prog. Ring Tariffa BO B1G B3G ASP AMP AU26 AO65 B10V 1 3 Mi1-Mi3 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 € 37,50 € 18,00 2 4 Mi1-Mi4 € 2,40 € 8,40 € 14,50 € 20,50 € 60,00 € 45,00 € 45,00 3 5 Mi1-Mi5 € 2,80 € 9,80 € 17,00 € 24,00 € 70,00 € 53,00 € 53,00 4 6 Mi1-Mi6 € 3,20 € 11,00 € 19,00 € 27,00 € 77,00 € 58,00 € 58,00 5 7 Mi1-Mi7 € 3,60 € 12,50 € 21,50 € 30,50 € 82,00 € 62,00 € 62,00 6 8 Mi1-Mi8 € 4,00 € 14,00 € 24,00 € 34,00 € 87,00 € 65,00 € 65,00 7 9STIBM INTEGRATO Mi1-Mi9€ 4,40 € 15,50 € 26,50 € 37,50 € 87,00 € 65,00 € 65,00 8 2 MI3-MI4 € 1,60 € 5,60 € 9,60 € 13,50 € 40,00 € 30,00 € 30,00 9 3 MI3-MI5 € 2,00 € 7,00 € 12,00 € 17,00 € 50,00 € 37,50 -

Trend Micro Incorporated Research Paper 2012
Trend Micro Incorporated Research Paper 2012 Detecting APT Activity with Network Traffic Analysis Nart Villeneuve and James Bennett Contents About This Paper .................................................................................................................................. 1 Introduction ........................................................................................................................................... 1 Detecting Remote Access Trojans ................................................................................................... 3 GhostNet......................................................................................................................................... 3 Nitro and RSA Breach .................................................................................................................4 Detecting Ongoing Campaigns .........................................................................................................5 Taidoor ............................................................................................................................................5 IXESHE ............................................................................................................................................5 Enfal aka Lurid ..............................................................................................................................6 Sykipot ........................................................................................................................................... -

Introducing Traffic Analysis
Introducing Traffic Analysis George Danezis and Richard Clayton January 26, 2007 1 Introduction In the Second World War, traffic analysis was used by the British at Bletchley Park to assess the size of Germany's air-force, and Japanese traffic analysis countermeasures contributed to the surprise of their 1941 attack on Pearl Harbour. Nowadays, Google uses the incidence of links to assess the relative importance of web pages, credit card companies examine transactions to spot fraudulent patterns of spending, and amateur plane-spotters revealed the CIA's `extraordinary rendition' programme. Diffie and Landau, in their book on wiretapping, went so far as to say that “traffic analysis, not cryptanalysis, is the backbone of communications intelligence" [1]. However, until recently the topic has been neglected by Computer Science academics. A rich literature discusses how to secure the confidentiality, integrity and availability of communication content, but very little work has considered the information leaked from communications ‘traffic data' and how these compromises might be minimised. Traffic data records the time and duration of a communication, and traffic analysis examines this data to determine the detailed shape of the communication streams, the identities of the parties communicating, and what can be established about their locations. The data may even be sketchy or incomplete { simply knowing what `typical' communication patterns look like can be used to infer information about a particular observed communication. Civilian infrastructures, on which state and economic actors are increasingly reliant, are ever more vulnerable to traffic analysis: wireless and GSM telephony are replacing traditional systems, routing is transparent and protocols are overlaid over others { giving plenty of opportunity to observe, and take advantage of the traffic data. -

Mass Surveillance
Mass Surveillance Mass Surveillance What are the risks for the citizens and the opportunities for the European Information Society? What are the possible mitigation strategies? Part 1 - Risks and opportunities raised by the current generation of network services and applications Study IP/G/STOA/FWC-2013-1/LOT 9/C5/SC1 January 2015 PE 527.409 STOA - Science and Technology Options Assessment The STOA project “Mass Surveillance Part 1 – Risks, Opportunities and Mitigation Strategies” was carried out by TECNALIA Research and Investigation in Spain. AUTHORS Arkaitz Gamino Garcia Concepción Cortes Velasco Eider Iturbe Zamalloa Erkuden Rios Velasco Iñaki Eguía Elejabarrieta Javier Herrera Lotero Jason Mansell (Linguistic Review) José Javier Larrañeta Ibañez Stefan Schuster (Editor) The authors acknowledge and would like to thank the following experts for their contributions to this report: Prof. Nigel Smart, University of Bristol; Matteo E. Bonfanti PhD, Research Fellow in International Law and Security, Scuola Superiore Sant’Anna Pisa; Prof. Fred Piper, University of London; Caspar Bowden, independent privacy researcher; Maria Pilar Torres Bruna, Head of Cybersecurity, Everis Aerospace, Defense and Security; Prof. Kenny Paterson, University of London; Agustín Martin and Luis Hernández Encinas, Tenured Scientists, Department of Information Processing and Cryptography (Cryptology and Information Security Group), CSIC; Alessandro Zanasi, Zanasi & Partners; Fernando Acero, Expert on Open Source Software; Luigi Coppolino,Università degli Studi di Napoli; Marcello Antonucci, EZNESS srl; Rachel Oldroyd, Managing Editor of The Bureau of Investigative Journalism; Peter Kruse, Founder of CSIS Security Group A/S; Ryan Gallagher, investigative Reporter of The Intercept; Capitán Alberto Redondo, Guardia Civil; Prof. Bart Preneel, KU Leuven; Raoul Chiesa, Security Brokers SCpA, CyberDefcon Ltd.; Prof. -

The Origination and Evolution of Radio Traffic Analysis: the World War I Era
UNCLASSI Fl ED The Origination and Evolution of Radio Traffic Analysis: The World War I Era (b )(3)-P. L. 86-36 Not unlike the telegraph and ita influence on the American Civil War, the invention of radio had a profound affect on World War I military operations and in all conflicts since 1901. Signals intelligence, a new form. of intelligence produced from. the intercept of radio traffic, developed on a parallel course with radio during the early years of the twentieth century. Although signals intelligence was identified as a method to produce useful and critical information during war, it did not mature as a significant tool until after the ,.War to End All Wars." Radio traffic analysis, a branch of signals intelligence, was not even recognized as a separate technique until long after the First World War ended. Nevertheless, traffic analysis, or TIA, existed as a function in that era and made significant contributions to military operations and to the development ofsignals intelligence. For the American signals intelligence service, radio traffic analysis originated as a technique in the codebreaking section and with the clerks in the goniometric or Direction Finding (DF) service of the American Expeditionary Force. The early cryptanalysts developed TIA techniques to identify the originator and receiver of radio messages and to determine the more important encoded or enciphered messages to attack. TIA also evolved in the DF service with the clerks who discovered ways to produce intelligence from analysis of the externals of messages and from the location ofthe radio transmitters. The increasingly more complex communications systems which defied cryptanalytic attack provided the impetus for these developments. -

Ten Strategies of a World-Class Cybersecurity Operations Center Conveys MITRE’S Expertise on Accumulated Expertise on Enterprise-Grade Computer Network Defense
Bleed rule--remove from file Bleed rule--remove from file MITRE’s accumulated Ten Strategies of a World-Class Cybersecurity Operations Center conveys MITRE’s expertise on accumulated expertise on enterprise-grade computer network defense. It covers ten key qualities enterprise- grade of leading Cybersecurity Operations Centers (CSOCs), ranging from their structure and organization, computer MITRE network to processes that best enable effective and efficient operations, to approaches that extract maximum defense Ten Strategies of a World-Class value from CSOC technology investments. This book offers perspective and context for key decision Cybersecurity Operations Center points in structuring a CSOC and shows how to: • Find the right size and structure for the CSOC team Cybersecurity Operations Center a World-Class of Strategies Ten The MITRE Corporation is • Achieve effective placement within a larger organization that a not-for-profit organization enables CSOC operations that operates federally funded • Attract, retain, and grow the right staff and skills research and development • Prepare the CSOC team, technologies, and processes for agile, centers (FFRDCs). FFRDCs threat-based response are unique organizations that • Architect for large-scale data collection and analysis with a assist the U.S. government with limited budget scientific research and analysis, • Prioritize sensor placement and data feed choices across development and acquisition, enteprise systems, enclaves, networks, and perimeters and systems engineering and integration. We’re proud to have If you manage, work in, or are standing up a CSOC, this book is for you. served the public interest for It is also available on MITRE’s website, www.mitre.org. more than 50 years. -

A Visual Motion Detection Circuit Suggested by Drosophila Connectomics
ARTICLE doi:10.1038/nature12450 A visual motion detection circuit suggested by Drosophila connectomics Shin-ya Takemura1, Arjun Bharioke1, Zhiyuan Lu1,2, Aljoscha Nern1, Shiv Vitaladevuni1, Patricia K. Rivlin1, William T. Katz1, Donald J. Olbris1, Stephen M. Plaza1, Philip Winston1, Ting Zhao1, Jane Anne Horne2, Richard D. Fetter1, Satoko Takemura1, Katerina Blazek1, Lei-Ann Chang1, Omotara Ogundeyi1, Mathew A. Saunders1, Victor Shapiro1, Christopher Sigmund1, Gerald M. Rubin1, Louis K. Scheffer1, Ian A. Meinertzhagen1,2 & Dmitri B. Chklovskii1 Animal behaviour arises from computations in neuronal circuits, but our understanding of these computations has been frustrated by the lack of detailed synaptic connection maps, or connectomes. For example, despite intensive investigations over half a century, the neuronal implementation of local motion detection in the insect visual system remains elusive. Here we develop a semi-automated pipeline using electron microscopy to reconstruct a connectome, containing 379 neurons and 8,637 chemical synaptic contacts, within the Drosophila optic medulla. By matching reconstructed neurons to examples from light microscopy, we assigned neurons to cell types and assembled a connectome of the repeating module of the medulla. Within this module, we identified cell types constituting a motion detection circuit, and showed that the connections onto individual motion-sensitive neurons in this circuit were consistent with their direction selectivity. Our results identify cellular targets for future functional investigations, and demonstrate that connectomes can provide key insights into neuronal computations. Vision in insects has been subject to intense behavioural1,physiological2 neuroanatomy14. Given the time-consuming nature of such recon- and anatomical3 investigations, yet our understanding of its underlying structions, we wanted to determine the smallest medulla volume, neural computations is still far from complete. -

New Directions in Automated Traffic Analysis
New Directions in Automated Traffic Analysis Jordan Holland1, Paul Schmitt1, Nick Feamster2, Prateek Mittal1 1 Princeton University 2 University of Chicago https://nprint.github.io/nprint ABSTRACT This paper reconsiders long-held norms in applying machine Despite the use of machine learning for many network traffic anal- learning to network traffic analysis; namely, we seek to reduce ysis tasks in security, from application identification to intrusion reliance upon human-driven feature engineering. To do so, we detection, the aspects of the machine learning pipeline that ulti- explore whether and how a single, standard representation of a mately determine the performance of the model—feature selection network packet can serve as a building block for the automation of and representation, model selection, and parameter tuning—remain many common traffic analysis tasks. Our goal is not to retread any manual and painstaking. This paper presents a method to auto- specific network classification problem, but rather to argue that mate many aspects of traffic analysis, making it easier to apply many of these problems can be made easier—and in some cases, machine learning techniques to a wider variety of traffic analysis completely automated—with a unified representation of traffic that tasks. We introduce nPrint, a tool that generates a unified packet is amenable for input to existing automated machine learning (Au- representation that is amenable for representation learning and toML) pipelines [14]. To demonstrate this capability, we designed a model training. We integrate nPrint with automated machine learn- standard packet representation, nPrint, that encodes each packet in ing (AutoML), resulting in nPrintML, a public system that largely an inherently normalized, binary representation while preserving eliminates feature extraction and model tuning for a wide variety the underlying semantics of each packet. -

Michigan-Specific Reporting Requirements
Version: February 28, 2020 MEDICARE-MEDICAID CAPITATED FINANCIAL ALIGNMENT MODEL REPORTING REQUIREMENTS: MICHIGAN-SPECIFIC REPORTING REQUIREMENTS Issued February 28, 2020 MI-1 Version: February 28, 2020 Table of Contents Michigan-Specific Reporting Requirements Appendix ......................................... MI-3 Introduction ....................................................................................................... MI-3 Definitions .......................................................................................................... MI-3 Variations from the Core Reporting Requirements Document ..................... MI-4 Quality Withhold Measures .............................................................................. MI-5 Reporting on Assessments and IICSPs Completed Prior to First Effective Enrollment Date ................................................................................. MI-6 Guidance on Assessments and IICSPs for Members with a Break in Coverage ............................................................................................................ MI-6 Reporting on Passively Enrolled and Opt-In Enrolled Members .................. MI-8 Reporting on Disenrolled and Retro-disenrolled Members ........................... MI-9 Hybrid Sampling ................................................................................................ MI-9 Value Sets ........................................................................................................ MI-10 Michigan’s Implementation, Ongoing, -

UK Eyes Alpha by the Same Author UK Eyes Alpha Big Boys' Rules: the SAS and the Secret Struggle Against the IRA Lnside British Lntelligence
UK Eyes Alpha By the same author UK Eyes Alpha Big Boys' Rules: The SAS and the secret struggle against the IRA lnside British lntelligence Mark Urban tr firhrr anr/ fulrr' ft For Ruth and Edwin Contents lntroduction Part One The First published in I996 1 Coming Earthquake 3 and Faber Limited by Faber 2 A Dark and Curious Shadow 13 3 Queen Square London vcrN JAU 3 The Charm Offensive 26 Typeset by Faber and Faber Ltd Printed in England by Clays Ltd, St Ives plc 4 Most Ridiculed Service 42 All rights reserved 5 ZIRCON 56 O Mark Urban, 1996 6 Springtime for Sceptics 70 Mark Urbar-r is hereby identified as author of 7 A Brilliant Intelligence Operation 84 this work in accordance with Section 77 of the Copyright, Designs and Patents Act 1988 8 The \7all Comes Tumbling Down 101 A CIP rccord for this book is available from the Part Two British Library 9 Supergun LL7 tsnN o-57r-r7689-5 10 Black Death on the Nevsky Prospekt L29 ll Assault on Kuwait L43 12 Desert Shield 153 13 Desert Storm 165 14 Moscow Endgame LA2 Part Three l5 An Accidcnt of History L97 l(r Irrlo thc ll:rllirrn 2LO tt),)B / (,1,1 l, I Qulgrnirc 17 Time for Revenge 22L lntroduction 18 Intelligence, Power and Economic Hegemony 232 19 Very Huge Bills 245 How good is British intelligence? What kind of a return do ministers and officials get 20 The Axe Falls 2il for the hundreds of millions of pounds spent on espionage each year? How does this secret establishment find direction and purpose 2l Irish Intrigues 269 in an age when old certainties have evaporated? Very few people, even in Conclusion 286 Whitehall, would feel confident enough to answer these questions. -

Cambia Il Modo Di Viaggiare
Cambia il modo di viaggiare Nuovo sistema tariffario integrato dei mezzi pubblici www.trenord.it | App Trenord Indice 11 Il sistema tariffario integrato del bacino di mobilità (STIBM) 6 1.1 La suddivisione del territorio del bacino di mobilità in zone tariffarie 6 Tabella 1 Elenco in ordine alfabetico dei comuni ubicati nella zona tariffaria denominata Mi3 7 Tabella 2 Elenco in ordine alfabetico dei comuni ubicati nelle zone tariffarie Mi4, Mi5, Mi6, Mi7, Mi8, Mi9 8 Mappa del sistema tariffario integrato del bacino di mobilità (stibm) Milano - Monza Brianza 12 1.2 Il calcolo della tariffa 14 1.3 Le principali novità del nuovo sistema tariffario 15 22 Tipologie di spostamento e titoli di viaggio 16 2.1 Per spostarsi a Milano 16 2.2 Per spostarsi tra Milano e le località extraurbane 16 2.3 Per spostarsi tra località extraurbane senza attraversare i confini di Milano 17 2.4 Per spostarsi tra località extraurbane attraversando i confini di Milano 17 33 I nuovi titoli di viaggio 18 3.1 Titoli di viaggio ordinari 18 3.2 Titoli di viaggio agevolati e gratuità per ragazzi 19 3.3 Le informazioni presenti sul titolo di viaggio 20 3.4 Regole generali di utilizzo del titolo di viaggio 21 3.5 Il Biglietto Chip On Paper 22 44 Tariffe dei titoli di viaggio ordinari e dei titoli di viaggio agevolati 24 Tabella 3 Biglietti ordinari e altri titoli di viaggio occasionali 25 Tabella 4 Abbonamenti ordinari 26 Tabella 5 Abbonamenti agevolati 27 2 | IL NUOVO SISTEMA TARIFFARIO INTEGRATO - MILANO - MONZA BRIANZA 3 IL NUOVO SISTEMA Mi9 TARIFFARIO INTEGRATO MILANO