1984 Telecommunications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Videotex/Teletext Presentation Level Protocol Syntax (North American PIPS) I
American Canadian National Adopted for Use by the Federal Government REFERENCE | NBS PUBLICATIONS r i(/. f 1 1 wS\3 No.121 1986 | North American PLPS i Government use. pederai d has been adopted l°'Fe " , Government are c0™e„,ation Level This standard within ,hc Federal ^^eUrie*■*.ca,ions available concerning 'ts . ds Publication . list the P . Processing Deta''S °n Processing Standards for a cornet the Standards Qf SSSCU-*- American <C !ri b Canadian National CL'UCX IJ A- Standards Standard Association .110-1983 T500-1983 NBS RESEARCH INFORMATION Videotex/Teletext CENTER Presentation Level Protocol Syntax North American PLPS Published in December, 1983 by American National Standards Institute, Inc. Canadian Standards Association 1430 Broadway 178 Rexdale Boulevard New York, NY 10018 Rexdale (Toronto), Ontario M9W 1R3 (Approved November 3, 1983) (Approved October 3, 1983) American National Standards and Canadian Standards Standards approved by the American National Standards Institute (ANSI) and the Canadian Standards Association (CSA) imply a consensus of those substantially concerned with their scope and provisions. These standards are intended as guides to aid the manufacturer, the consumer, and the general public. The existence of a standard does not in any respect preclude any of the above groups, whether they have approved the standard or not, from manufacturing, marketing, purchasing, or using products, processes, or procedures not conforming to the standard. These standards are subject to periodic review and users are cautioned to obtain the latest editions. In this standard, the words ''shall/' "should,” and "may" represent requirements, recommendations, and options, respectively, as specified in ANSI and CSA policy and style guides. -
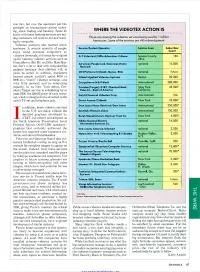
WHERE the VIDEOTEX ACTION IS Price-The Rest of the Industry Will
vice mix, but now the operators put the spotlight on transactions-airline ticket- ing, stock trading and banking. Some 40 WHERE THE VIDEOTEX ACTION IS banks with home banking services are bet- ting customers will want to do their bank- These are among the videotex services being used by 1 million ing by computer. Americans. Some of the services are still in develcpment. Videotex pioneers also learned about hardware: A certain minority of people Service/System Operator Service Area Subscribe enjoy using personal computers as Count videotex terminals, and many have signed A -T Videotext/Tiffin Advertiser-Tribune Seneca County, 150 up for national videotex services such as Ohio Mrs. Mass CompuServe. But Mr. and Mar- American People Link/American Home national 16,000 ket don't want to deal with computerlike Network gadgets (perhaps their children will, in years to come). In addition, marketers CNt Partners/Citibank, Nynex, RCA national future learned people wouldn't spend $600 or Citiret/Applied Videotex Systems Boston 20,000 $900 on a "dumb" videotex terminal-one with little memory and no computing CompuServe/H & R Block international 280,000 capacity. In its New York debut, Cov- Coridea (Target)/AT&T, Chemical Bank, New York, 45,000- idea's Target service is subsidizing by at Time Inc., Bank of America California least $100 the $49.95 price of each termi- Del 3hi/General Videotex Corp. international NA nal, which is designed to be attached to the user's TV set and telephone jack. Direct Access/Citibank New York 22,000' Dow Jones News-Retrieval/Dow Jones international 250,000' n addition, home videotex services in the U.S. -

Afterword: Omissions,Additions, and Corrections
Afterword: Omissions,Additions, and Corrections The astute reader will notice that I’ve omitted a few online services. Some were so short-lived or of so little consequence that they would be meaningless to most readers. Others are beyond the theme or time frame of this book. Some of the omissions: ABI/INFORM (Abstracted Business Information), a database of abstracted information from selected business publications, hosted by ORBIT, Dialog, and eventually UMI/ProQuest Data Courier, a small online service hosted by the Louisville Courier- Journal (the owners of which bought ABI/INFORM under the company name “Data Courier”) EasyLink, Western Union’s now-defunct email/FAX/mail system Easynet, a front end for more than 700 database services EasyPlex, a specialized CompuServe email service E-COM, the United States Postal Service’s electronic messaging service (EMS) Freenet, free BBSs in cities such as Cleveland and Rochester that used the same software and were designed to serve as community centers Info-Look, a gateway to online services hosted by Nynex Internet Relay Chat (IRC), the first implementation of real-time chatting via the Internet (Jarkko Oikarinen, 1988) Knowledge Index (KI), a subset of Dialog databases The Microsoft Network (MSN), more an ISP than online service that started after Bill Gates decided that the Internet was going to be important, after all 177 178 Afterword MIX, the McGraw-Hill Information Exchange, a CoSy-based service for educators NABU Network, a Canadian online service that operated -

History - Ieee Ottawa Section1
HISTORY - IEEE OTTAWA SECTION1 The history of the IEEE in Ottawa is the story of the people and institutions and industries that created one of the largest concentrations of information communications technology in the world. For example, the IEEE Canada Showcase of Canadian Engineering Achievements2 includes the following projects that were based in the Ottawa area, and involved many IEEE members. Radar3, radio4, electronic music5, Telidon6, the Crash Position Indicator7, the Alouette8, Anik9 and ISIS10 satellites, the pacemaker11, and the Sudbury Neutrino Observatory 12. According to the Ottawa Centre for Research and Innovation (OCRI) “Ottawa boasts the highest percentage of university graduates in Canada and the second largest concentration of science and technology employment of 316 North American cities, surpassed only by California's Silicon Valley”13. The development of the “high tech” community, which some termed “Silicon Valley North” is outlined in the book “Silicon Valley North: A High-Tech Cluster of Innovation and Entrepreneurship”, edited by Larisa V. Shavina14. Institutions Ottawa is the location of a number of Engineering and Scientific Research and Development Institutions in which IEEE members have played a large role.15 These Institutions consist of: • the Communications Research Centre, or CRC, located in the west end of Ottawa; • the Bell Northern Research Laboratories (BNR) located nearby; • the National Research Council16, located in the east end of Ottawa; • Carleton University and The University of Ottawa, each -

11836337-MIT.Pdf
• STRATEGIC OPPORTUNITIES FOR SYSTEM OPERATORS • AND INFORMATION PROVIDERS IN THE ELECTRONIC INFORMATION SERVICES INDUSTRY by • SHARON BETH SINSKY 'l B.A., JOHNS HOPKINS UNIVERSITY (1980) Submitted to the Sloan School of Management in Partial Fulfillment of • the Requirements of the Degree of Master of Science in Management at the • Massachusetts Institute of Technology May 1984 © Massachusetts Institute of Technology The author hereby grants to MIT permission to reproduce and to • distribute copies of this thesis document in whole or in part. Signature redacted Signature of Author ._ uc.v• _ ,.,,_,...,..- .•sTo~·;•-vhool 1 of Management • May 11, 198t / 1/1 I\ • Signature redacted Cert i f i e d by----------• b11,r <6 ,.., v 'k£, &<-----------M-1 ~ c, _, , \\K ......, c_h_a_e_l, - , , v__0 S_. _S_c_o_t_t_M_o_r_t_o_n Thesis Supervisor /\ /) . • Signature redacted Accepted by I , •c...,1-v '"l.~ --------+---+-1-----+----------------------J e ff re y A. Barks Director of the Master's Program • ·· ~- ARCHIVES f~·,r•.~~ liCfii i.,~:.,.·:- -·· .. ... OF TECHNriL0b}TiTUT£ JUN 2 6 1984 LIBRARIES STRATEGIC OPPORTUNITIES FOR SYSTEM OPERATORS AND INFORMATION PROVIDERS IN THE ELECTRONIC INFORMATION SERVICES INDUSTRY by SHARON BETH SINSKY Submitted to the Sloan School of Management on 11 May 1984 in partial fulfillment of the requirements for the Degree of Master of Science in Management ABSTRACT This thesis explores the actions and motivations of firms pursuing opportunities as system operators and information providers in the United States electronic information services industry. Although few companies have yet to make money in this industry, it has attracted the attention of both small and large United States firms. By electronic information services, I am referring to the combination of computer and communications technology that allows users at personal computers, terminals, or modified television sets to access remote data bases and information services. -

History of Virtual Learning Environments 1 History of Virtual Learning Environments
History of virtual learning environments 1 History of virtual learning environments A virtual learning environment (VLE) is a system that creates an environment designed to facilitate teachers in the management of educational courses for their students, especially a system using computer hardware and software, which involves distance learning. In North America, a virtual learning environment is often referred to as a "learning management system" (LMS). Pre-1940s • 1728: March 20, Boston Gazette contains an advertisement from Caleb Phillipps, "Teacher of the New Method of Short Hand," advising that any "Persons in the Country desirous to Learn this Art, may by having the several Lessons sent weekly to them, be as perfectly instructed as those that live in Boston."[1] • 1840: Isaac Pitman begins teaching shorthand, using Great Britain's Penny Post.[1] • 1874: Institutionally sponsored distance education began in the United States in 1874 at the Illinois Wesleyan University.[1] • 1890: International Correspondence Schools (ICS) is launched by Pressey Testing Machine (exterior) newspaperman Thomas J. Foster in Scranton, Pennsylvania and becomes the world's largest study-at-home school. • 1883: The Correspondence University of Ithaca, New York (a correspondence school) was founded in 1883.[1] • 1892: The term “distance education” was first used in a University of Wisconsin–Madison catalog for the 1892 school year.[2] • 1906-7: The University of Wisconsin–Extension[3] was founded;[4] the first true distance learning institution. • 1909: The Machine Stops a short story by E. M. Forster, which describes an audio/visual communication network being used to deliver a lecture on Pressey Testing Machine (interior) Australian music to a remote audience.[5] • 1920s: Sidney Pressey, an educational psychology professor at Ohio State University, develops the first "teaching machine."[6] This device offered drill and practice exercises, and multiple choice questions. -

Acronyms and Abbreviations*
APPENDIX A Acronyms and Abbreviations* a atto (10-18) A ampere A angstrom AAR automatic alternate routing AARTS automatic audio remote test set AAS aeronautical advisory station AB asynchronous balanced (mode) (Link Layer OSI-RM) ABCA American, British, Canadian, Australian armies abs absolute ABS aeronautical broadcast station ABSBH average busy season busy hour ac alternating current AC absorption coefficient access charge access code ACA automatic circuit assurance ACC automatic callback calling ACCS associated common-channel signaling ACCUNET AT&T switched 56-kbps service ACD automatic call distributing automatic call distributor *Alphabetized letter by letter. Uppercase letters follow lowercase letters. All other symbols are ignored, including superscripts and subscripts. Numerals follow Z and Greek letters are at the very end. 1127 Appendix A 1128 ac-dc alternating-current direct-current (ringing) ACE automatic cross-connection equipment ACF/VTAM advanced communications facility (VT AM) ACK acknowledge character acknowledgement ACK/NAK acknowledgement/negative acknowledgement ACS airport control station asynchronous communications system ACSE association control service element ACTS advanced communications technology satellite ACU automatic calling unit AD addendum AID analog to digital A-D analog to digital ADAPT architectures design, analysis, and planning tool ADC analog-to-digital converter automatic digital control ADCCP Advanced Data Communications Control Procedure (ANSI) ADH automatic data handling ADP automatic data processing -

Nordic Positions Before the Internet Tomas Ohlin
The Baby Networks: Nordic Positions Before the Internet Tomas Ohlin To cite this version: Tomas Ohlin. The Baby Networks: Nordic Positions Before the Internet. 3rd History of Nordic Computing (HiNC), Oct 2010, Stockholm, Sweden. pp.278-286, 10.1007/978-3-642-23315-9_31. hal- 01564661 HAL Id: hal-01564661 https://hal.inria.fr/hal-01564661 Submitted on 19 Jul 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License The Baby Networks: Nordic Positions Before the Internet Tomas Ohlin Formerly of Linköping University and Stockholm University [email protected] Abstract. This paper discusses the computer network situation immediately before the arrival of the internet. In various countries, there were a number of isolated network “islands,” following different standards of technical characteristics called videotex. The paper discusses the different regional standards that were used and what types of services were made available, and asks what role the Nordic countries played in this development and in the transition to the internet. Keywords: CEPT-3, internet, Minitel, Prestel, standards, TCP/IP, TeleGuide, videotex, Viewdata 1 The International Background One does not have to be religious to be challenged about how it all started. -
3.3 Graphics Processor
SR PT01 Form 1 WAIVER THE UNIVERSITY OF NEW SOUTH WALES DECLARATION RELATING TO DISPOSITION OF PROJECT REPORT /THESIS This is to certify that I .. cQ/t:J6 ; .."ZH~Io.Jf! . being a candidate for the degree oL ... MA-S..tet'. c>F ... SC~III.C..~ .. am fully aware of the policy of the University relating to the retention and use of higher degree project reports and theses, namely that the University retains the copies submitted for examination and is free to allow them to be consulted or borrowed. Subject to the provisions of the Copyright Act, 1968, the University may issue a project report or thesis in whole or in part, in photostat or microfilm or other copying medium. In the light of these provisions I grant the University Librarian permission to publish, or to authorize the publication of my project report/thesis, in whole or in part. l also authorize the publication by University Microfilms of a 350 word abstract in Dissertation Abstracts International (applicable to doctorates only). SiJ,:nature Witness v Date ..../'t-4 .......... -Zl9 THE DEVELOPMENT OF A HIGH-PERFORMANCE NAPLPS VIDEOTEX DECODER A THESIS SUBMITTED TO THE DEPARTMENT OF COMPUTER SCIENCE UNIVERSITY COLLEGE THE UNIVERSITY OF NEW SOUTH WALES AUSTRALIAN DEFENCE FORCE ACADEMY FOR THE DEGREE OF MASTER OF SCIENCE By Qing Zhong April1988 2 OMAR 1989 USRARY SR.P.TlO CERTIFICATE OF ORIGINALITY I hereby declare that this thesis is my own work and that, to the best of my knowledge and belief, it contains no material previously published or written by another person nor material which to a substantial extent has been accepted for the award of any other degree or diploma of a university or other institute of higher learning, except where due acknowledgement is made in the text of the thesis. -
Community Computer Networks: Building Electronic Greenbelts
STEVE CISLER Senior Scientist Apple Library Apple Computer Cupertino, California Community Computer Networks: Building Electronic Greenbelts INTRODUCTION What are community networks? I am writing as a librarian and network user who has been involved in using telecommunications to communicate with other people and to provide information on a wide range of subjects. I have encouraged people in various towns and counties to use this technology to start and use networks that can strengthen the community. Many individuals, organizations, and institutions are becoming involved in these networks. Whether you are a technical expert, information professional, government official, busi- nessperson, or interested citizen, there is a role for you to play in incubating, growing, maintaining, and using these systems. A community network consists of one or more computers providing services to people using computers and terminals to gain access to those services and to each other. While many of these networks tie together geographically separated individuals linked by a common interest or profession (senior citizens, pilots, ecologists, librarians), this essay will not cover scholarly or affinity group networks. Other models and systems exist but have been described elsewhere (Rheingold, 1993). Instead, "community" will be used in the sense of a mu- nicipality, county, regional area, or Indian nation. The information contained in such networks as well as the relationships that form among the participants make up what I call an electronic greenbelt to reinforce and add value to the community. These communities do include a variety of other interest groups whose needs and interests transcend the geographic boundaries of the town, region, or state. -

IPR2016-01520 Patent No.: 8,559,635
PATENT OWNER’S UPDATED EXHIBIT LIST Case No.: IPR2016-01520 Patent No.: 8,559,635 Ex. No. Description 2001. Declaration of Alfred Weaver, Ph.D. Pursuant to 37 C.F.R. § 1.68 2002. Curriculum Vitae of Alfred Weaver 2003. Ex. Parte Personalized Media Commc’ns, LLC, No. 2009-6825, 2010 WL 200346 (B.P.A.I. Jan. 19, 2010) 2004. Excerpt of Special Master’s Report and Recommendation, Personalized Media Commc’ns, LLC v. Scientific-Atlanta, Inc. et al., No. 1:02-CV-824 (N.D. Ga. Mar. 1 2005) 2005. Ex Parte Personalized Media Commc’ns, No. 2008-4228, 2008 WL 5373184 (B.P.A.I. Dec. 19, 2008) 2006. Anthony Wechselberger, Encryption: A Cable TV Primer (Oak Communications Inc. 1983) 2007. Transcript of Deposition of Mr. Wechselberger, Amazon, Inc. v. Personalized Media Commc’ns, LLC, IPR2014-01532 (June 9, 2015) 2008. Appeal Brief (Reexam No. 90/006,536 of U.S. Patent No. 4,965,825) 2009. Order dated May 15, 2003, from Judge Gregory Sleet in Personalized Media Commc’ns, LLC v. DirecTV, et al. (D. Del. C.A. No. 00-1020) 2010. Expert Declaration Of Anthony J. Wechselberger dated September 16, 2002 in Broadcast Innovation, LLC v. Echostar Communications Corp (D. CO: 01-WY-2201 AJ) 2011. Excerpt of IEEE Standard Dictionary of Electrical and Electronics Terms (1984) (Definition of “execution (software)”) 2012. Prosecution History of U.S. Patent Appl. No. 08/449,431 2013. Claim Construction Order, Personalized Media Commc’ns, LLC v. Apple, Inc. 2:15-cv-01366-JRG-RSP, Dkt. No. 246 (October 25, 2016) 2014. -

Technical Standards and Technological Change
Technical Standards and Technological Change in the Telecommunications Industry by Sanford V. Berg August 19, 1988 (Revised) ABSTRACT Innovations often involve complex networks or systems. Components of an interdependent technological system require interface standards or "gateway technologies" for the attachment of basic equipment and/or use of inputs. Alternatively, standardization (interchangeability among components) also yields compatibility. The emergence of standardization or gateway protocols both have implications for market demand, production costs and the strategies of pioneering innovators and their followers. Here we analyze the role of standards specification in the telecommunications industry. Graphics protocol standards for videotex, compatibility standards for microcomputers, and technical standards for computer networks are used to illustrate how competition, cooperation, and coercion can affect efficiency and innovation in telecommunications. Public Utility Research Center University of Florida Gainesville, Florida Technical Standards and Technological Change in the Telecommunications Industry* by Sanford V. Berg** I. Introduction While OPEC and the energy crisis symbolize the economic forces of change in the U.S. during the 1970s, the AT&T divestiture and the associated telecommunications revolution may well be chronicled as the major economic developments of the 1980s. Innovations in the telecommunications industry have given rise to a number of major technological developments, especially in signal delivery systems.' Components of such complex technological systems require compatibility (interface) standards for the attachment of basic equipment and the use of inputs. However, with telecommunications opened to new entry for voice, video, and digital transmission, and with the traditional links between the provision of local telephone service and other services cut, the potential for incompatibilities is serious.