Integrated Baseboard Management Controller Firmware
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Release Notes (100 001420)
VERITAS File System™ 3.3.3 Release Notes Solaris January 2000 100-001420 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. Copyright Copyright © 2000 VERITAS Software Corporation. All rights reserved. VERITAS is a registered trademark of VERITAS Software Corporation in the US and other countries. The VERITAS logo and VERITAS File System are trademarks of VERITAS Software Corporation. All other trademarks or registered trademarks are the property of their respective owners. Printed in the USA, January 2000. VERITAS Software Corporation 1600 Plymouth St. Mountain View, CA 94043 Phone 650–335–8000 Fax 650–335–8050 www.veritas.com VERITAS File System Release Notes This guide provides information on VERITAS File System™ (VxFS) Release 3.3.3 for Solaris 2.5.1, Solaris 2.6, Solaris 7 (32-bit and 64-bit), and Solaris 8 (32-bit and 64-bit) operating systems. References in this document to VxFS 3.3 regarding new features, end of product support, compatibility, and software limitations apply to VxFS 3.3.3. Review this entire document before installing VxFS. The VERITAS File System packages include VxFS software, documentation, -
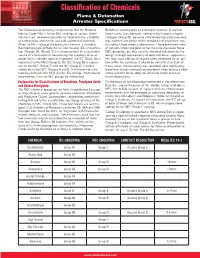
Classification of Chemicals
Classification of Chemicals Flame & Detonation Arrester Specifications PROTECTOSEAL ® The Protectoseal Company recommends that the National Butadiene would qualify as a Group D material. In each of Electric Code (NEC) Article 500, rankings of various chemi - these cases, the chemicals were primarly listed in a higher cals be used, whenever possible, to determine the suitability category (Group B), because of relatively high pressure read - of a detonation arrester for use with a particular chemical. ings noted in one phase of the standard test procedure con - When no NEC rating of the particular chemical is available, ducted by Underwriters Laboratories. These pressures were the International Electrotechnical Commission (IEC) classifica - of concern when categorizing the chemicals because these tion (Groups IIA, IIB and IIC) is recommended as a secondary NEC groupings are also used as standard indicators for the source of information for determining the suitability of an ar - design strength requirements of electrical boxes, apparatus, rester for its intended service. In general, the IEC Group IIA is etc. that must withstand the pressures generated by an igni - equivalent to the NEC Group D; the IEC Group IIB is equiva - tion within the container. It should be noted that, in each of lent to the NEC Group C; and the IEC Group IIC includes these cases, the test pressures recorded were significantly chemicals in the NEC Groups A and B. In the event of a dis - lower than those commonly encountered when testing a deto - crepancy between the NEC and the IEC ratings, Protectoseal nation arrester for its ability to withstand stable and over - recommends that the NEC groups be referenced. -

UNIX (Solaris/Linux) Quick Reference Card Logging in Directory Commands at the Login: Prompt, Enter Your Username
UNIX (Solaris/Linux) QUICK REFERENCE CARD Logging In Directory Commands At the Login: prompt, enter your username. At the Password: prompt, enter ls Lists files in current directory your system password. Linux is case-sensitive, so enter upper and lower case ls -l Long listing of files letters as required for your username, password and commands. ls -a List all files, including hidden files ls -lat Long listing of all files sorted by last Exiting or Logging Out modification time. ls wcp List all files matching the wildcard Enter logout and press <Enter> or type <Ctrl>-D. pattern Changing your Password ls dn List files in the directory dn tree List files in tree format Type passwd at the command prompt. Type in your old password, then your new cd dn Change current directory to dn password, then re-enter your new password for verification. If the new password cd pub Changes to subdirectory “pub” is verified, your password will be changed. Many systems age passwords; this cd .. Changes to next higher level directory forces users to change their passwords at predetermined intervals. (previous directory) cd / Changes to the root directory Changing your MS Network Password cd Changes to the users home directory cd /usr/xx Changes to the subdirectory “xx” in the Some servers maintain a second password exclusively for use with Microsoft windows directory “usr” networking, allowing you to mount your home directory as a Network Drive. mkdir dn Makes a new directory named dn Type smbpasswd at the command prompt. Type in your old SMB passwword, rmdir dn Removes the directory dn (the then your new password, then re-enter your new password for verification. -

Unix Programmer's Manual
There is no warranty of merchantability nor any warranty of fitness for a particu!ar purpose nor any other warranty, either expressed or imp!ied, a’s to the accuracy of the enclosed m~=:crials or a~ Io ~helr ,~.ui~::~::.j!it’/ for ~ny p~rficu~ar pur~.~o~e. ~".-~--, ....-.re: " n~ I T~ ~hone Laaorator es 8ssumg$ no rO, p::::nS,-,,.:~:y ~or their use by the recipient. Furln=,, [: ’ La:::.c:,:e?o:,os ~:’urnes no ob~ja~tjon ~o furnish 6ny a~o,~,,..n~e at ~ny k:nd v,,hetsoever, or to furnish any additional jnformstjcn or documenta’tjon. UNIX PROGRAMMER’S MANUAL F~ifth ~ K. Thompson D. M. Ritchie June, 1974 Copyright:.©d972, 1973, 1974 Bell Telephone:Laboratories, Incorporated Copyright © 1972, 1973, 1974 Bell Telephone Laboratories, Incorporated This manual was set by a Graphic Systems photo- typesetter driven by the troff formatting program operating under the UNIX system. The text of the manual was prepared using the ed text editor. PREFACE to the Fifth Edition . The number of UNIX installations is now above 50, and many more are expected. None of these has exactly the same complement of hardware or software. Therefore, at any particular installa- tion, it is quite possible that this manual will give inappropriate information. The authors are grateful to L. L. Cherry, L. A. Dimino, R. C. Haight, S. C. Johnson, B. W. Ker- nighan, M. E. Lesk, and E. N. Pinson for their contributions to the system software, and to L. E. McMahon for software and for his contributions to this manual. -

Unix Commands (09/04/2014)
Unix Commands (09/04/2014) • Access control – login <login_name> – exit – passwd <login_name> – yppassswd <loginname> – su – • Login as Super user – su <login> • Login as user <login> • Root Prompt – [root@localhost ~] # • User Prompt – [bms@raxama ~] $ On Line Documentation – man <command/topic> – info <command/topic> • Working with directories – mkdir –p <subdir> ... {-p create all directories in path if not present} mkdir –p /2015/Jan/21/14 will create /2015, Jan, 21 & 14 in case any of these is absent – cd <dir> – rm -r <subdir> ... Man Pages • 1 Executable programs or shell commands • 2 System calls (functions provided by the kernel) • 3 Library calls (functions within program libraries) • 4 Special files (usually found in /dev) • 5 File formats and conventions eg /etc/passwd • 6 Games • 7 Miscellaneous (including macro packages and conventions), e.g. man(7), groff(7) • 8 System administration commands (usually only for root) • 9 Kernel routines [Non standard] – man grep, {awk,sed,find,cut,sort} – man –k mysql, man –k dhcp – man crontab ,man 5 crontab – man printf, man 3 printf – man read, man 2 read – man info Runlevels used by Fedora/RHS Refer /etc/inittab • 0 - halt (Do NOT set initdefault to this) • 1 - Single user mode • 2 - Multiuser, – without NFS (The same as 3, if you do not have networking) • 3 - Full multi user mode w/o X • 4 - unused • 5 - X11 • 6 - reboot (Do NOT set init default to this) – init 6 {Reboot System} – init 0 {Halt the System} – reboot {Requires Super User} – <ctrl> <alt> <del> • in tty[2-7] mode – tty switching • <ctrl> <alt> <F1-7> • In Fedora 10 tty1 is X. -

Final Project Forum Commands
Final Project For the final project you will be writing custom front-ends to your favorite Linux commands. To do this you will write a shell script that interacts with the user to get input, then use that input to call a Linux command. You will start with a template that you can modify and extend. Forum Use the forum to brainstorm script ideas, clarify requirements, and get help if you are stuck. When you have tested your script and think it is bug free then use the forum to ask others to test it some more. Post any valuable tips or lessons learned as well. Forum is at: http://opus-ii.cis.cabrillo.edu/forum/ Commands . echo lpstat sort at env ls spell banner exit mail su bash export man tail bc file mesg tee cal find mkdir touch cancel finger more type cat grep mv umask cd head passwd uname chgrp history ps unset chmod id pwd vi chown jobs rm wc clear kill rmdir who cp ln set write date lp/lpr sleep xxd Commands by Categories Type Commands Simple: banner, date, cal, finger, uname, type, ls, tree, cd, pwd, hostname Status: jobs, ps, who, id, env, lpstat, umask, mesg, history, tty File: file, cp, mv, ln, rm, rmdir, mkdir, touch, chmod, chgrp, xxd, head, tail, stat Filters: cat, sort, spell, grep, wc, tee Misc: bc, mail, vi, lp, cancel, at, kill, find, passwd The Template #!/bin/bash # # menu: A simple menu template # while true do clear echo -n " CIS 90 Final Project 1) Task 1 2) Task 2 3) Task 3 4) Task 4 5) Task 5 6) Exit Enter Your Choice: " read response case $response in 1) # Commands for Task 1 ;; 2) # Commands for Task 2 ;; 3) # Commands for Task 3 ;; 4) # Commands for Task 4 ;; 5) # Commands for Task 5 ;; 6) exit 0 ;; *) echo "Please enter a number between 1 and 6" ;; esac echo -n "Hit the Enter key to return to menu " read response done Procedure Copy the template text to a file in your own bin directory named myscript. -

Systems Supplement for COP 3601
Systems Guide for COP 3601: Introduction to Systems Software Charles N. Winton Department of Computer and Information Sciences University of North Florida 2010 Chapter 1 A Basic Guide for the Unix Operating System 1. 1 Using the Unix On-line Manual Pages Facility The following are some of the Unix commands for which you may display manual pages: cal cat cd chmod cp cut date echo egrep ex fgrep file find gcc gdb grep kill less ln locate ls mail make man mesg mkdir mv nohup nl passwd pr ps pwd rm rmdir set sleep sort stty tail tee time touch tr tty uname umask unset vim wall wc which who whoami write For example, to display the manual pages for the command "cp" enter man cp Note that you may also enter man man to find out more about the "man" command. In addition there may be commands unique to the local environment with manual pages; e.g., man turnin accesses a manual page for a project submission utility named Aturnin@ that has been added to the system. If you enter a command from the Unix prompt that requires an argument, the system will recognize that the command is incomplete and respond with an error message. For example, if the command "cp" had been entered at the Unix prompt the system would respond with the information such as shown below: cp: missing file arguments Try `cp --help' for more information. The "cp" command is a copy command. If the arguments which tell the command which file to copy and where to locate the copied file are missing, then the usage error message is generated. -

Working with Oracle® Solaris 11.4 Directory and Naming Services: LDAP
® Working With Oracle Solaris 11.4 Directory and Naming Services: LDAP Part No: E61012 November 2020 Working With Oracle Solaris 11.4 Directory and Naming Services: LDAP Part No: E61012 Copyright © 2002, 2020, Oracle and/or its affiliates. License Restrictions Warranty/Consequential Damages Disclaimer This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. Warranty Disclaimer The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Restricted Rights Notice If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users -

Unix Account
USING YOUR FAS UNIX ACCOUNT Copyright © 1999 The President and Fellows of Harvard College All Rights Reserved TABLE OF CONTENTS COMPUTING AT HARVARD ........................................................................................ 1 An Introduction to Unix ................................................................................................ 1 The FAS Unix Systems ............................................................................................... 1 CONNECTING TO YOUR FAS UNIX ACCOUNT .............................................................. 2 SECURITY & PRIVACY ON FAS UNIX SYSTEMS........................................................... 2 Your FAS Unix Account’s Password............................................................................ 2 USING THE UNIX COMMAND SHELL ........................................................................... 3 Managing Multiple Programs under Unix. .................................................................... 3 FILES AND DIRECTORIES IN UNIX ............................................................................... 4 Your Home Directory .................................................................................................. 4 Your Home Directory’s Disk Space Quota .................................................................. 4 Using ls to List Files in Your Home Directory ............................................................... 5 Managing Your Files .................................................................................................. -

Business Plan Summary
Business Plan Summary Table of contents Introduction and History 3 ● Vision ● Mission ● Values ● Goals to reach by 2020 Market Research 5 ● The Industry ● MESG’s Competition ● Competitive Landscape ● Market Differentiation ● Target Market Business Model 10 Financial Plan 11 ● Startup Costs ● Funding ● Token Listing ● Token Distribution Marketing Mix 14 Company and Management 16 ● Products and Services ● Market Opportunities ● Competitive Advantages ● Business Model 2 Introduction and History MESG was conceived in 2017 by developers Anthony Estebe and Nicolas Mahé after they discovered that no existing system enabled free-flowing communication between traditional web services and Ethereum. They set out to build a prototype that would enable “old world” technologies to communicate with this new and different kind of data/network. After months of experimentation and refinement, they had succeeded. Impressed by the potential, MESG’s third co-founder, Alexis Sirkia, expanded the team and brought MESG into the Yellow Incubator, offering financial support, business mentorship, and marketing expertise. In mid-2018 they released MESG Engine v1.0, an event-driven architecture-based platform offering developers and businesses tools enabling free communication between virtually any networked technologies, including, for the first time, technologies from the new blockchain frontier. The next phase of MESG Engine, anticipated in mid-2019, will enable communication between any networked technologies via an open and decentralized network, unlocking the enormous business value inherent in new and unique properties of blockchain technology. The MESG development platform is fully open source and encourages the sharing and reuse of components of applications and services, which can dramatically reduce development and maintenance costs by 50% or more. -

National Fire Protection Association Report
National Fire Protection Association Report http://submittals.nfpa.org/TerraViewWeb/ContentFetcher?commentPara... Public Input No. 12-NFPA 497-2014 [ Chapter 2 ] Chapter 2 Referenced Publications 2.1 General. The documents or portions thereof listed in this chapter are referenced within this recommended practice and should be considered part of the recommendations of this document. 2.2 NFPA Publications. National Fire Protection Association, 1 Batterymarch Park, Quincy, MA 02169-7471. NFPA 30, Flammable and Combustible Liquids Code, 2012 edition. NFPA 33, Standard for Spray Application Using Flammable or Combustible Materials, 2011 edition . NFPA 34, Standard for Dipping, Coating, and Printing Processes Using Flammable or Combustible Liquids, 2011 edition . NFPA 35, Standard for the Manufacture of Organic Coatings, 2011 edition . NFPA 36, Standard for Solvent Extraction Plants, 2009 edition 2013 . NFPA 45, Standard on Fire Protection for Laboratories Using Chemicals, 2011 edition . NFPA 55, Compressed Gases and Cryogenic Fluids Code, 2010 edition 2013 . NFPA 58, Liquefied Petroleum Gas Code, 2011 edition 2014 . NFPA 59A, Standard for the Production, Storage, and Handling of Liquefied Natural Gas (LNG), 2009 edition 2013 . ® ® NFPA 70 , National Electrical Code , 2011 edition 2014 . 2.3 Other Publications. 2.3.1 ANSI Publications. American National Standards Institute, Inc., 25 West 43rd Street, 4th Floor, New York, NY 10036. ANSI/ISA-RP12.12.03, Recommended Practice for Portable Electronic Products Suitable for Use in Class I and II, Division 2, Class I, Zone 2 and Class III, Division 1 and 2 Hazardous (Classified) Locations , 2002. 2.3.2 API Publications. American Petroleum Institute, 1220 L Street, NW, Washington, DC 20005-4070. -

UNIX System Servicesuser's Guide
z/OS Version 2 Release 3 UNIX System Services User's Guide IBM SA23-2279-30 Note Before using this information and the product it supports, read the information in “Notices” on page 321. This edition applies to Version 2 Release 3 of z/OS (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2019-02-16 © Copyright International Business Machines Corporation 1996, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Figures...................................................................................................... xv List of Tables......................................................................................................xvii About this document...........................................................................................xix Who should use z/OS UNIX System Services User's Guide?....................................................................xix What is in z/OS UNIX System Services User's Guide?........................................................................ xix Tasks that can be performed in more than one environment.............................................................xix z/OS information.................................................................................................................................. xix How to send your comments to IBM.....................................................................xxi If you