Unix Account
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vim for Humans Release 1.0
Vim for humans Release 1.0 Vincent Jousse August 12, 2015 CONTENTS 1 Preamble 1 1.1 Disclaimer .................... ..................... 1 1.2 Paid book but free price .................... ..................... 1 1.3 Free license .................... ..................... 1 1.4 Thanks .................... ..................... 1 2 Introduction 3 2.1 For who? .................... ..................... 4 2.2 What you will be learning .................... .................... 4 2.3 What you will not be learning .................... .................. 4 2.4 The hardest part is to get started .................... ................. 5 3 Having a usable Vim 7 3.1 Essential preamble: the insert mode .................... ............... 8 3.2 Modes: the powerful Vim secrets .................... 10 3.3 The lifesaver default configuration .................... 12 3.4 And now, the color! .................... ..................... 13 3.5 Ourfirst plugin: thefile explorer .................... 17 3.6 Here we go .................... ..................... 19 4 The text editor you’ve always dreamed of 23 4.1 Learning how to move: the copy/paste use case ..................... 23 4.2 Forgetting the directional keys .................... 26 4.3 Doing without the Esc key .................... .................... 29 4.4 Combining keys and moves .................... ................... 29 4.5 Search / Move quickly .................... ..................... 30 4.6 Visual mode .................... ..................... 31 4.7 It’s your turn! .................... .................... -

Release Notes (100 001420)
VERITAS File System™ 3.3.3 Release Notes Solaris January 2000 100-001420 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. Copyright Copyright © 2000 VERITAS Software Corporation. All rights reserved. VERITAS is a registered trademark of VERITAS Software Corporation in the US and other countries. The VERITAS logo and VERITAS File System are trademarks of VERITAS Software Corporation. All other trademarks or registered trademarks are the property of their respective owners. Printed in the USA, January 2000. VERITAS Software Corporation 1600 Plymouth St. Mountain View, CA 94043 Phone 650–335–8000 Fax 650–335–8050 www.veritas.com VERITAS File System Release Notes This guide provides information on VERITAS File System™ (VxFS) Release 3.3.3 for Solaris 2.5.1, Solaris 2.6, Solaris 7 (32-bit and 64-bit), and Solaris 8 (32-bit and 64-bit) operating systems. References in this document to VxFS 3.3 regarding new features, end of product support, compatibility, and software limitations apply to VxFS 3.3.3. Review this entire document before installing VxFS. The VERITAS File System packages include VxFS software, documentation, -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -

Linux Fundamentals (GL120) U8583S This Is a Challenging Course That Focuses on the Fundamental Tools and Concepts of Linux and Unix
Course data sheet Linux Fundamentals (GL120) U8583S This is a challenging course that focuses on the fundamental tools and concepts of Linux and Unix. Students gain HPE course number U8583S proficiency using the command line. Beginners develop a Course length 5 days solid foundation in Unix, while advanced users discover Delivery mode ILT, vILT patterns and fill in gaps in their knowledge. The course View schedule, local material is designed to provide extensive hands-on View now pricing, and register experience. Topics include basic file manipulation; basic and View related courses View now advanced filesystem features; I/O redirection and pipes; text manipulation and regular expressions; managing jobs and processes; vi, the standard Unix editor; automating tasks with Why HPE Education Services? shell scripts; managing software; secure remote • IDC MarketScape leader 5 years running for IT education and training* administration; and more. • Recognized by IDC for leading with global coverage, unmatched technical Prerequisites Supported distributions expertise, and targeted education consulting services* Students should be comfortable with • Red Hat Enterprise Linux 7 • Key partnerships with industry leaders computers. No familiarity with Linux or other OpenStack®, VMware®, Linux®, Microsoft®, • SUSE Linux Enterprise 12 ITIL, PMI, CSA, and SUSE Unix operating systems is required. • Complete continuum of training delivery • Ubuntu 16.04 LTS options—self-paced eLearning, custom education consulting, traditional classroom, video on-demand -

Assessmentof Open Source GIS Software for Water Resources
Assessment of Open Source GIS Software for Water Resources Management in Developing Countries Daoyi Chen, Department of Engineering, University of Liverpool César Carmona-Moreno, EU Joint Research Centre Andrea Leone, Department of Engineering, University of Liverpool Shahriar Shams, Department of Engineering, University of Liverpool EUR 23705 EN - 2008 The mission of the Institute for Environment and Sustainability is to provide scientific-technical support to the European Union’s Policies for the protection and sustainable development of the European and global environment. European Commission Joint Research Centre Institute for Environment and Sustainability Contact information Cesar Carmona-Moreno Address: via fermi, T440, I-21027 ISPRA (VA) ITALY E-mail: [email protected] Tel.: +39 0332 78 9654 Fax: +39 0332 78 9073 http://ies.jrc.ec.europa.eu/ http://www.jrc.ec.europa.eu/ Legal Notice Neither the European Commission nor any person acting on behalf of the Commission is responsible for the use which might be made of this publication. Europe Direct is a service to help you find answers to your questions about the European Union Freephone number (*): 00 800 6 7 8 9 10 11 (*) Certain mobile telephone operators do not allow access to 00 800 numbers or these calls may be billed. A great deal of additional information on the European Union is available on the Internet. It can be accessed through the Europa server http://europa.eu/ JRC [49291] EUR 23705 EN ISBN 978-92-79-11229-4 ISSN 1018-5593 DOI 10.2788/71249 Luxembourg: Office for Official Publications of the European Communities © European Communities, 2008 Reproduction is authorised provided the source is acknowledged Printed in Italy Table of Content Introduction............................................................................................................................4 1. -

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

FRESHMAN GUIDE to Successful College Planning
FRESHMAN GUIDE to Successful College Planning Artwork by: Serena Walkin Ballou Senior High School Class of 2001 Graduate COPYRIGHT © 2003 DISTRICT OF COLUMBIA COLLEGE ACCESS PROGRAM. ALL RIGHTS RESERVED. PRINTED IN THE UNITED STATES OF AMERICA. FRESHMAN GUIDE TO SUCCESSFUL COLLEGE PLANNING TABLE OF CONTENTS Introduction 2 How to Contact 3 Part I Student Guide to Freshman Year 6 Section I Selecting Your High School Courses 7 Section II Attendance, Time Management, & Study Skills 10 Section III Understanding Your GPA 12 Section IV Standardized Tests 13 Section V Activities for College Bound Freshman 14 Section VI Types of Colleges 15 Section VII Activity Worksheet 16 Part II Parental Guide to Financial Planning 19 Parent Agreement 22 INTRODUCTION Welcome to DC-CAP Freshman Guide to College Planning. The purpose of this guide is to assist students in the District of Columbia Public and Public Charter High Schools who are starting their Freshman Year of high school. We hope that this handbook will be useful to you and your parents as you set out to begin the journey of college planning during your high school years. Again, we encourage students to visit their DC- CAP advisor and register with our program. Congratulations!! Welcome to your first year of high school. Follow this guide step-by-step and you will guarantee yourself SUCCESS!!!!!!! Please read this handbook with your parents and return the signed agreement form to the DC-CAP Advisor assigned to your school. What is DC-CAP? The District of Columbia College Access Program (DC-CAP) is a non-profit organization funded by Washington Area corporations and foundations dedicated to encouraging and enabling District of Columbia public and public charter high school students to enter and graduate from college. -
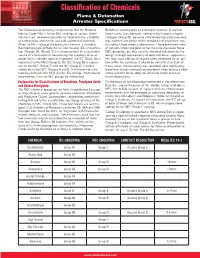
Classification of Chemicals
Classification of Chemicals Flame & Detonation Arrester Specifications PROTECTOSEAL ® The Protectoseal Company recommends that the National Butadiene would qualify as a Group D material. In each of Electric Code (NEC) Article 500, rankings of various chemi - these cases, the chemicals were primarly listed in a higher cals be used, whenever possible, to determine the suitability category (Group B), because of relatively high pressure read - of a detonation arrester for use with a particular chemical. ings noted in one phase of the standard test procedure con - When no NEC rating of the particular chemical is available, ducted by Underwriters Laboratories. These pressures were the International Electrotechnical Commission (IEC) classifica - of concern when categorizing the chemicals because these tion (Groups IIA, IIB and IIC) is recommended as a secondary NEC groupings are also used as standard indicators for the source of information for determining the suitability of an ar - design strength requirements of electrical boxes, apparatus, rester for its intended service. In general, the IEC Group IIA is etc. that must withstand the pressures generated by an igni - equivalent to the NEC Group D; the IEC Group IIB is equiva - tion within the container. It should be noted that, in each of lent to the NEC Group C; and the IEC Group IIC includes these cases, the test pressures recorded were significantly chemicals in the NEC Groups A and B. In the event of a dis - lower than those commonly encountered when testing a deto - crepancy between the NEC and the IEC ratings, Protectoseal nation arrester for its ability to withstand stable and over - recommends that the NEC groups be referenced. -

Introduction to Unix (PDF)
Introduction to… UNIX Bob Booth December 2004 AP-UNIX2 © University of Sheffield Contents 1. INTRODUCTION....................................................................................................................................... 3 1.1 THE SHELL ........................................................................................................................................... 3 1.2 FORMAT OF COMMANDS ...................................................................................................................... 4 1.3 ENTERING COMMANDS ......................................................................................................................... 4 2. ACCESSING UNIX MACHINES ............................................................................................................. 5 2.1 TERMINAL EMULATION SOFTWARE...................................................................................................... 5 2.2 LOGGING IN.......................................................................................................................................... 6 2.3 LOGGING OUT ...................................................................................................................................... 6 2.4 CHANGING YOUR PASSWORD............................................................................................................... 8 3. BASIC UNIX COMMANDS...................................................................................................................... 9 3.1 FILENAMES.......................................................................................................................................... -

UNIX Text Processing Tools—Programs for Sorting, Compar- Ing, and in Various Ways Examining the Contents of Text Files
UNIX® TEXT PROCESSING DALE DOUGHERTY AND TIM O’REILLY and the staffofO’Reilly & Associates, Inc. CONSULTING EDITORS: Stephen G. Kochan and PatrickH.Wood HAYDEN BOOKS ADivision of HowardW.Sams & Company 4300 West 62nd Street Indianapolis, Indiana 46268 USA Copyright © 1987 Dale Dougherty and Tim O’Reilly FIRST EDITION SECOND PRINTING — 1988 INTERNET "UTP Revival" RELEASE — 2004 The UTP RevivalRelease is distributed according to the terms of the Creative Commons Attribution License. A copyofthe license is available at http://creativecommons.org/licenses/by/1.0 International Standard Book Number: 0-672-46291-5 Library of Congress Catalog Card Number: 87-60537 Trademark Acknowledgements All terms mentioned in this book that are known to be trademarks or service marks are listed below. Nei- ther the authors nor the UTP Revivalmembers can attest to the accuracyofthis information. Use of a term in this book should not be regarded as affecting the validity of anytrademark or service mark. Apple is a registered trademark and Apple LaserWriter is a trademark of Apple Computer,Inc. devps is a trademark of Pipeline Associates, Inc. Merge/286 and Merge/386 are trademarks of Locus Computing Corp. DDL is a trademark of Imagen Corp. Helvetica and Times Roman are registered trademarks of Allied Corp. IBM is a registered trademark of International Business Machines Corp. Interpress is a trademark of Xerox Corp. LaserJet is a trademark of Hewlett-Packard Corp. Linotronic is a trademark of Allied Corp. Macintosh is a trademark licensed to Apple Computer,Inc. Microsoft is a registered trademark of Microsoft Corp. MKS Toolkit is a trademark of Mortice Kern Systems, Inc. -

Netcat − Network Connections Made Easy
Netcat − network connections made easy A lot of the shell scripting I do involves piping the output of one command into another, such as: $ cat /var/log/messages | awk '{print $4,$5,$6,$7,$8,$9,$10,$11,$12,$13,$14,$15}' | sed −e 's/\[[0−9]*\]:/:/' | sort | uniq | less which shows me the system log file after removing the timestamps and [12345] pids and removing duplicates (1000 neatly ordered unique lines is a lot easier to scan than 6000 mixed together). The above technique works well when all the processing can be done on one machine. What happens if I want to somehow send this data to another machine right in the pipe? For example, instead of viewing it with less on this machine, I want to somehow send the output to my laptop so I can view it there. Ideally, the command would look something like: $ cat /var/log/messages | awk '{print $4,$5,$6,$7,$8,$9,$10,$11,$12,$13,$14,$15}' | sed −e 's/\[[0−9]*\]:/:/' | sort | uniq | laptop That exact syntax won't work because the shell thinks it needs to hand off the data to a program called laptop − which doesn't exist. There's a way to do it, though. Enter Netcat Netcat was written 5 years ago to perform exactly this kind of magic − allowing the user to make network connections between machines without any programming. Let's look at some examples of how it works. Let's say that I'm having trouble with a web server that's not returning the content I want for some reason. -

PS TEXT EDIT Reference Manual Is Designed to Give You a Complete Is About Overview of TEDIT
Information Management Technology Library PS TEXT EDIT™ Reference Manual Abstract This manual describes PS TEXT EDIT, a multi-screen block mode text editor. It provides a complete overview of the product and instructions for using each command. Part Number 058059 Tandem Computers Incorporated Document History Edition Part Number Product Version OS Version Date First Edition 82550 A00 TEDIT B20 GUARDIAN 90 B20 October 1985 (Preliminary) Second Edition 82550 B00 TEDIT B30 GUARDIAN 90 B30 April 1986 Update 1 82242 TEDIT C00 GUARDIAN 90 C00 November 1987 Third Edition 058059 TEDIT C00 GUARDIAN 90 C00 July 1991 Note The second edition of this manual was reformatted in July 1991; no changes were made to the manual’s content at that time. New editions incorporate any updates issued since the previous edition. Copyright All rights reserved. No part of this document may be reproduced in any form, including photocopying or translation to another language, without the prior written consent of Tandem Computers Incorporated. Copyright 1991 Tandem Computers Incorporated. Contents What This Book Is About xvii Who Should Use This Book xvii How to Use This Book xvii Where to Go for More Information xix What’s New in This Update xx Section 1 Introduction to TEDIT What Is PS TEXT EDIT? 1-1 TEDIT Features 1-1 TEDIT Commands 1-2 Using TEDIT Commands 1-3 Terminals and TEDIT 1-3 Starting TEDIT 1-4 Section 2 TEDIT Topics Overview 2-1 Understanding Syntax 2-2 Note About the Examples in This Book 2-3 BALANCED-EXPRESSION 2-5 CHARACTER 2-9 058059 Tandem Computers