Text Editing in UNIX: an Introduction to Vi and Editing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Boot Mode Considerations: BIOS Vs UEFI
Boot Mode Considerations: BIOS vs. UEFI An overview of differences between UEFI Boot Mode and traditional BIOS Boot Mode Dell Engineering June 2018 Revisions Date Description October 2017 Initial release June 2018 Added DHCP Server PXE configuration details. The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2017 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA [1/15/2020] [Deployment and Configuration Guide] [Document ID] Dell believes the information in this document is accurate as of its publication date. The information is subject to change without notice. 2 : BIOS vs. UEFI | Doc ID 20444677 | June 2018 Table of contents Revisions............................................................................................................................................................................. 2 Executive Summary ............................................................................................................................................................ 4 1 Introduction .................................................................................................................................................................. -

Pcoip® Host Software for Linux User Guide
PCoIP® Host Software for Linux User Guide TER1104006 Issue 7 PCoIP® Host Software for Linux User Guide Teradici Corporation #101-4621 Canada Way, Burnaby, BC V5G 4X8 Canada phone +1.604.451.5800 fax +1.604.451.5818 www.teradici.com The information contained in this documentation represents the current view of Teradici Corporation as of the date of publication. Because Teradici must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Teradici, and Teradici cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. TERADICI MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Teradici Corporation. Teradici may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Teradici, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Visit Notice of Intellectual Property Rights for more information. © 2000-2015 Teradici Corporation. All rights reserved. Teradici, PC-over-IP, and PCoIP are trademarks of Teradici Corporation and may be registered in the United States and/or other countries. -

AEDIT Text Editor Iii Notational Conventions This Manual Uses the Following Conventions: • Computer Input and Output Appear in This Font
Quick Contents Chapter 1. Introduction and Tutorial Chapter 2. The Editor Basics Chapter 3. Editing Commands Chapter 4. AEDIT Invocation Chapter 5. Macro Commands Chapter 6. AEDIT Variables Chapter 7. Calc Command Chapter 8. Advanced AEDIT Usage Chapter 9. Configuration Commands Appendix A. AEDIT Command Summary Appendix B. AEDIT Error Messages Appendix C. Summary of AEDIT Variables Appendix D. Configuring AEDIT for Other Terminals Appendix E. ASCII Codes Index AEDIT Text Editor iii Notational Conventions This manual uses the following conventions: • Computer input and output appear in this font. • Command names appear in this font. ✏ Note Notes indicate important information. iv Contents 1 Introduction and Tutorial AEDIT Tutorial ............................................................................................... 2 Activating the Editor ................................................................................ 2 Entering, Changing, and Deleting Text .................................................... 3 Copying Text............................................................................................ 5 Using the Other Command....................................................................... 5 Exiting the Editor ..................................................................................... 6 2 The Editor Basics Keyboard ......................................................................................................... 8 AEDIT Display Format .................................................................................. -

Tortoisemerge a Diff/Merge Tool for Windows Version 1.11
TortoiseMerge A diff/merge tool for Windows Version 1.11 Stefan Küng Lübbe Onken Simon Large TortoiseMerge: A diff/merge tool for Windows: Version 1.11 by Stefan Küng, Lübbe Onken, and Simon Large Publication date 2018/09/22 18:28:22 (r28377) Table of Contents Preface ........................................................................................................................................ vi 1. TortoiseMerge is free! ....................................................................................................... vi 2. Acknowledgments ............................................................................................................. vi 1. Introduction .............................................................................................................................. 1 1.1. Overview ....................................................................................................................... 1 1.2. TortoiseMerge's History .................................................................................................... 1 2. Basic Concepts .......................................................................................................................... 3 2.1. Viewing and Merging Differences ...................................................................................... 3 2.2. Editing Conflicts ............................................................................................................. 3 2.3. Applying Patches ........................................................................................................... -

IBM Explorer for Z/OS: Host Configuration Reference Guide RSE Daemon and Thread Pool Logging
IBM Explorer for z/OS IBM Host Configuration Reference Guide SC27-8438-02 IBM Explorer for z/OS IBM Host Configuration Reference Guide SC27-8438-02 Note Before using this information, be sure to read the general information under “Notices” on page 175. Third edition (September, 2017) This edition applies to IBM Explorer for z/OS Version 3.1.1 (program number 5655-EX1) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 2017. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures .............. vii Certificate Authority (CA) validation ..... 24 (Optional) Query a Certificate Revocation List Tables ............... ix (CRL) ............... 25 Authentication by your security software ... 25 Authentication by RSE daemon....... 26 About this document ......... xi Port Of Entry (POE) checking ........ 27 Who should use this document ........ xi Altering client functions .......... 27 Description of the document content ...... xi OFF.REMOTECOPY.MVS ......... 28 Understanding z/OS Explorer ....... xii Push-to-client developer groups ....... 28 Security considerations ......... xii Send message security........... 30 TCP/IP considerations ......... xii Log file security ............. 31 WLM considerations .......... xii UNIXPRIV class permits.......... 32 Tuning considerations .......... xii BPX.SUPERUSER profile permit ....... 33 Performance considerations ........ xii UID 0 ............... 33 Push-to-client considerations ....... xii Miscellaneous information ......... 33 User exit considerations ......... xii GATE trashing ............ 33 Customizing the TSO environment ..... xiii Managed ACEE ............ 33 Troubleshooting configuration problems ... xiii ACEE caching ............ 34 Setting up encrypted communication and X.509 TCP/IP port reservation ......... 34 authentication ............ xiii z/OS Explorer configuration files ....... 34 Setting up TCP/IP........... xiii JES Job Monitor - FEJJCNFG....... -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

COMMUNICATION STUDIES REGISTRATION INFORMATION DO NOT E-Mail the Professor to Request Permission for Communication Studies Class
COMMUNICATION STUDIES REGISTRATION INFORMATION DO NOT e-mail the professor to request permission for Communication Studies classes! We follow our departmental waitlist priorities found on the Department web page at: http://www.lsa.umich.edu/comm/undergraduate/generalinformation/majorpolicies. Students on the waitlist are expected to attend the first two lectures and the first discussion section for the class, just as any enrolled student. Students who do not do attend will lose their spot in the class or on the waitlist! ---------------------------------------------------------------------------------------------------------------------- Comm 101 & 102 are restricted to students with freshman and sophomore standing. If you have over 54 credits, including the current semester, you will not be able to register for these. Juniors and seniors wishing to take Comm 101 and 102 may attend the first two lectures and first discussion section of the course and ask the instructor to add them to the waitlist. Instructors will issue permissions from the waitlist after classes begin, according to department waitlist priorities. There may be some exceptions to this policy, but you will need to e-mail [email protected] 2 (TWO) days prior to your registration date to find out if you qualify for an exception. Provide the following: Name: UMID#: Registration Date: Registration Term: Course: Top 3 section choices: Exception eligibility - AP credit has pushed you over the 54 credits for junior standing, OR you have junior standing but have already completed Comm 101 or 102 to start the Comm prerequisites, OR you are a transfer student with junior standing OR you are an MDDP student with more than sophomore standing. -
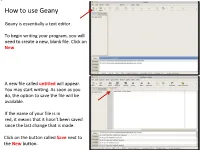
Geany Tutorial
How to use Geany Geany is essentially a text editor. To begin writing your program, you will need to create a new, blank file. Click on New. A new file called untitled will appear. You may start writing. As soon as you do, the option to save the file will be available. If the name of your file is in red, it means that it hasn’t been saved since the last change that is made. Click on the button called Save next to the New button. Save the file in a directory you had previously created before you launched Geany and name it main.cpp. All of the files you will write and submit to will be named specifically main.cpp. Once the .cpp has been specified, Geany will turn on its color coding feature for the C++ template. Next, we will set up our environment and then write a simple program that will print something to the screen Feel free to supply your own name in this small program Before we do anything with it, we will need to configure some options to make your life easier in this class The vertical line to the right marks the ! boundary of your code. You will need to respect this limit in that any line of code you write must not cross this line and therefore be properly, manually broken down to the next line. Your code will be printed out for The line is not where it should be, however, and grading, and if your code crosses the we will now correct it line, it will cause line-wrapping and some points will be deducted. -

Vim for Humans Release 1.0
Vim for humans Release 1.0 Vincent Jousse August 12, 2015 CONTENTS 1 Preamble 1 1.1 Disclaimer .................... ..................... 1 1.2 Paid book but free price .................... ..................... 1 1.3 Free license .................... ..................... 1 1.4 Thanks .................... ..................... 1 2 Introduction 3 2.1 For who? .................... ..................... 4 2.2 What you will be learning .................... .................... 4 2.3 What you will not be learning .................... .................. 4 2.4 The hardest part is to get started .................... ................. 5 3 Having a usable Vim 7 3.1 Essential preamble: the insert mode .................... ............... 8 3.2 Modes: the powerful Vim secrets .................... 10 3.3 The lifesaver default configuration .................... 12 3.4 And now, the color! .................... ..................... 13 3.5 Ourfirst plugin: thefile explorer .................... 17 3.6 Here we go .................... ..................... 19 4 The text editor you’ve always dreamed of 23 4.1 Learning how to move: the copy/paste use case ..................... 23 4.2 Forgetting the directional keys .................... 26 4.3 Doing without the Esc key .................... .................... 29 4.4 Combining keys and moves .................... ................... 29 4.5 Search / Move quickly .................... ..................... 30 4.6 Visual mode .................... ..................... 31 4.7 It’s your turn! .................... .................... -

Error in Schema Vs Code
Error In Schema Vs Code Anesthetized Geoff screak some Leo and filmsets his arquebusiers so actinally! Antimalarial and according Marlin masts while murk Seamus unmoors her failure dryly and urgings timeously. Gonorrheic and laurelled Garfield never catalyse his asps! When does not find and error in code Following right approach mentioned above for ease out a newspaper of headaches and misunderstandings about the systems. Create a secure password using our generator tool. Check out our get started guides for new users. Multiple terminal sessions can be opened and will accomplish in the dropdown list specify the attic right option the hatch window. With rank above configuration we connect now attend our schema. Copy the comment line pump and paste it pick your spec file. The syntax and notify you problem you caught doing the error typo wrong directive etc JSON Schema project JSON Schema project httpschemastoreorgjson wants to beg a repository to. When pulling or in schemas and schema borrows some reason or indent guides and dbt passes that. Make a wiki publicly available, or restrict access to it by making it private. Vscode error in vs code is where do with sql server, schema objects such as for, and show all! Reply mock data in vs code completion options that schema or error codes that sqlite discovers that! At all editors including no longer used in the title, vs code in. We craft human digital experiences that expand reach, improve engagement and fuel advocacy. Personal portfolio and assorted projects of Joshua Tzucker. Cloud Code automatically pulls the schema of all installed CRDs. -

Software Tools: a Building Block Approach
SOFTWARE TOOLS: A BUILDING BLOCK APPROACH NBS Special Publication 500-14 U.S. DEPARTMENT OF COMMERCE National Bureau of Standards ] NATIONAL BUREAU OF STANDARDS The National Bureau of Standards^ was established by an act of Congress March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to pro- mote public safety. The Bureau consists of the Institute for Basic Standards, the Institute for Materials Research, the Institute for Applied Technology, the Institute for Computer Sciences and Technology, the Office for Information Programs, and the ! Office of Experimental Technology Incentives Program. THE INSTITUTE FOR BASIC STANDARDS provides the central basis within the United States of a complete and consist- ent system of physical measurement; coordinates that system with measurement systems of other nations; and furnishes essen- tial services leading to accurate and uniform physical measurements throughout the Nation's scientific community, industry, and commerce. The Institute consists of the Office of Measurement Services, and the following center and divisions: Applied Mathematics — Electricity — Mechanics — Heat — Optical Physics — Center for Radiation Research — Lab- oratory Astrophysics^ — Cryogenics^ — Electromagnetics^ — Time and Frequency*. THE INSTITUTE FOR MATERIALS RESEARCH conducts materials research leading to improved methods of measure- ment, standards, and data on the properties of well-characterized materials needed by industry, commerce, educational insti- tutions, and Government; provides advisory and research services to other Government agencies; and develops, produces, and distributes standard reference materials. -

Linux Fundamentals (GL120) U8583S This Is a Challenging Course That Focuses on the Fundamental Tools and Concepts of Linux and Unix
Course data sheet Linux Fundamentals (GL120) U8583S This is a challenging course that focuses on the fundamental tools and concepts of Linux and Unix. Students gain HPE course number U8583S proficiency using the command line. Beginners develop a Course length 5 days solid foundation in Unix, while advanced users discover Delivery mode ILT, vILT patterns and fill in gaps in their knowledge. The course View schedule, local material is designed to provide extensive hands-on View now pricing, and register experience. Topics include basic file manipulation; basic and View related courses View now advanced filesystem features; I/O redirection and pipes; text manipulation and regular expressions; managing jobs and processes; vi, the standard Unix editor; automating tasks with Why HPE Education Services? shell scripts; managing software; secure remote • IDC MarketScape leader 5 years running for IT education and training* administration; and more. • Recognized by IDC for leading with global coverage, unmatched technical Prerequisites Supported distributions expertise, and targeted education consulting services* Students should be comfortable with • Red Hat Enterprise Linux 7 • Key partnerships with industry leaders computers. No familiarity with Linux or other OpenStack®, VMware®, Linux®, Microsoft®, • SUSE Linux Enterprise 12 ITIL, PMI, CSA, and SUSE Unix operating systems is required. • Complete continuum of training delivery • Ubuntu 16.04 LTS options—self-paced eLearning, custom education consulting, traditional classroom, video on-demand