IBM Explorer for Z/OS: Host Configuration Reference Guide RSE Daemon and Thread Pool Logging
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pcoip® Host Software for Linux User Guide
PCoIP® Host Software for Linux User Guide TER1104006 Issue 7 PCoIP® Host Software for Linux User Guide Teradici Corporation #101-4621 Canada Way, Burnaby, BC V5G 4X8 Canada phone +1.604.451.5800 fax +1.604.451.5818 www.teradici.com The information contained in this documentation represents the current view of Teradici Corporation as of the date of publication. Because Teradici must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Teradici, and Teradici cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. TERADICI MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Teradici Corporation. Teradici may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Teradici, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Visit Notice of Intellectual Property Rights for more information. © 2000-2015 Teradici Corporation. All rights reserved. Teradici, PC-over-IP, and PCoIP are trademarks of Teradici Corporation and may be registered in the United States and/or other countries. -

AEDIT Text Editor Iii Notational Conventions This Manual Uses the Following Conventions: • Computer Input and Output Appear in This Font
Quick Contents Chapter 1. Introduction and Tutorial Chapter 2. The Editor Basics Chapter 3. Editing Commands Chapter 4. AEDIT Invocation Chapter 5. Macro Commands Chapter 6. AEDIT Variables Chapter 7. Calc Command Chapter 8. Advanced AEDIT Usage Chapter 9. Configuration Commands Appendix A. AEDIT Command Summary Appendix B. AEDIT Error Messages Appendix C. Summary of AEDIT Variables Appendix D. Configuring AEDIT for Other Terminals Appendix E. ASCII Codes Index AEDIT Text Editor iii Notational Conventions This manual uses the following conventions: • Computer input and output appear in this font. • Command names appear in this font. ✏ Note Notes indicate important information. iv Contents 1 Introduction and Tutorial AEDIT Tutorial ............................................................................................... 2 Activating the Editor ................................................................................ 2 Entering, Changing, and Deleting Text .................................................... 3 Copying Text............................................................................................ 5 Using the Other Command....................................................................... 5 Exiting the Editor ..................................................................................... 6 2 The Editor Basics Keyboard ......................................................................................................... 8 AEDIT Display Format .................................................................................. -
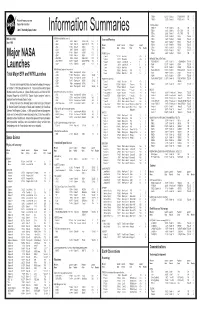
Information Summaries
TIROS 8 12/21/63 Delta-22 TIROS-H (A-53) 17B S National Aeronautics and TIROS 9 1/22/65 Delta-28 TIROS-I (A-54) 17A S Space Administration TIROS Operational 2TIROS 10 7/1/65 Delta-32 OT-1 17B S John F. Kennedy Space Center 2ESSA 1 2/3/66 Delta-36 OT-3 (TOS) 17A S Information Summaries 2 2 ESSA 2 2/28/66 Delta-37 OT-2 (TOS) 17B S 2ESSA 3 10/2/66 2Delta-41 TOS-A 1SLC-2E S PMS 031 (KSC) OSO (Orbiting Solar Observatories) Lunar and Planetary 2ESSA 4 1/26/67 2Delta-45 TOS-B 1SLC-2E S June 1999 OSO 1 3/7/62 Delta-8 OSO-A (S-16) 17A S 2ESSA 5 4/20/67 2Delta-48 TOS-C 1SLC-2E S OSO 2 2/3/65 Delta-29 OSO-B2 (S-17) 17B S Mission Launch Launch Payload Launch 2ESSA 6 11/10/67 2Delta-54 TOS-D 1SLC-2E S OSO 8/25/65 Delta-33 OSO-C 17B U Name Date Vehicle Code Pad Results 2ESSA 7 8/16/68 2Delta-58 TOS-E 1SLC-2E S OSO 3 3/8/67 Delta-46 OSO-E1 17A S 2ESSA 8 12/15/68 2Delta-62 TOS-F 1SLC-2E S OSO 4 10/18/67 Delta-53 OSO-D 17B S PIONEER (Lunar) 2ESSA 9 2/26/69 2Delta-67 TOS-G 17B S OSO 5 1/22/69 Delta-64 OSO-F 17B S Pioneer 1 10/11/58 Thor-Able-1 –– 17A U Major NASA 2 1 OSO 6/PAC 8/9/69 Delta-72 OSO-G/PAC 17A S Pioneer 2 11/8/58 Thor-Able-2 –– 17A U IMPROVED TIROS OPERATIONAL 2 1 OSO 7/TETR 3 9/29/71 Delta-85 OSO-H/TETR-D 17A S Pioneer 3 12/6/58 Juno II AM-11 –– 5 U 3ITOS 1/OSCAR 5 1/23/70 2Delta-76 1TIROS-M/OSCAR 1SLC-2W S 2 OSO 8 6/21/75 Delta-112 OSO-1 17B S Pioneer 4 3/3/59 Juno II AM-14 –– 5 S 3NOAA 1 12/11/70 2Delta-81 ITOS-A 1SLC-2W S Launches Pioneer 11/26/59 Atlas-Able-1 –– 14 U 3ITOS 10/21/71 2Delta-86 ITOS-B 1SLC-2E U OGO (Orbiting Geophysical -

Asa R-/ 130090
rl),,; ASA R-/130090 The University of Texas at Dallas Final Technical Report NASA Contract NAS 5-9075 on Measurement of the Degree of Anisotropy of the Cosmic Radiation Using the IMP Space Vehicle by R. A. R. Palmeira and F. R. Allum The University of Texas at Dallas Dallas, Texas This report was prepared for submission to NASA/Goddard Space Flight Center in partial fulfillment of the terms of the Contract NAS 5-9075. October 1972 (NASA-CR-130090 ) MEASUREMENT OF THE DEGREE N72-3376 OF ANISOTROPY OF THE COSMIC RADIATION USING 8 THE IMP SPACE VEHICLE Final Technical Report R.A.R. Palmeira, et al (Texas Unclas Univ.) Oct. 1972 31 p CSCL 03B G3/29 45262 The University of Texas at Dallas Final Technical Report on "Measurement of the Degree of Anisotropy of the Cosmic Radiation Using the IMP Space Vehicle" NASA Contract NAS 5-9075 by R.A.R. Palmeira and F. R. Allum The University of Texas at Dallas, Dallas, Texas INTRODUCTION This report describes the detector and data reduction techniques used in connection with the UTD cosmic-ray experiments designed for and flown on board the Explorer 34 and 41 satellites. It is intended to supplement and summarize the more detailed information supplied during the course of the program, including but not restricted to the information contained in the contractually required Monthly Technical Reports submitted throughout the duration of the program. This final technical report is divided into three categories: i) a brief history of the UTD program development; ii) a description of the particle detectors and the methods of data analysis; and iii) present status of data processing. -

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

1. Run Nslookup to Obtain the IP Address of a Web Server in Europe
1. Run nslookup to obtain the IP address of a Web server in Europe. frigate:Desktop drb$ nslookup home.web.cern.ch Server: 130.215.32.18 Address: 130.215.32.18#53 Non-authoritative answer: home.web.cern.ch canonical name = drupalprod.cern.ch. Name: drupalprod.cern.ch Address: 137.138.76.28 Note that the #53 denotes the DNS service is running on port 53. 2. Run nslookup to determine the authoritative DNS servers for a university in Asia. frigate:Desktop drb$ nslookup -type=NS tsinghua.edu.cn Server: 130.215.32.18 Address: 130.215.32.18#53 Non-authoritative answer: tsinghua.edu.cn nameserver = dns2.tsinghua.edu.cn. tsinghua.edu.cn nameserver = dns.tsinghua.edu.cn. tsinghua.edu.cn nameserver = dns2.edu.cn. tsinghua.edu.cn nameserver = ns2.cuhk.edu.hk. Authoritative answers can be found from: dns2.tsinghua.edu.cn internet address = 166.111.8.31 ns2.cuhk.edu.hk internet address = 137.189.6.21 ns2.cuhk.edu.hk has AAAA address 2405:3000:3:6::15 dns2.edu.cn internet address = 202.112.0.13 dns.tsinghua.edu.cn internet address = 166.111.8.30 Note that there can be multiple authoritative servers. The response we got back was from a cached record. To confirm the authoritative DNS servers, we perform the same DNS query of one of the servers that can provide authoritative answers. frigate:Desktop drb$ nslookup -type=NS tsinghua.edu.cn dns.tsinghua.edu.cn Server: dns.tsinghua.edu.cn Address: 166.111.8.30#53 tsinghua.edu.cn nameserver = dns2.edu.cn. -

Photographs Written Historical and Descriptive
CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY HAER FL-8-B BUILDING AE HAER FL-8-B (John F. Kennedy Space Center, Hanger AE) Cape Canaveral Brevard County Florida PHOTOGRAPHS WRITTEN HISTORICAL AND DESCRIPTIVE DATA HISTORIC AMERICAN ENGINEERING RECORD SOUTHEAST REGIONAL OFFICE National Park Service U.S. Department of the Interior 100 Alabama St. NW Atlanta, GA 30303 HISTORIC AMERICAN ENGINEERING RECORD CAPE CANAVERAL AIR FORCE STATION, MISSILE ASSEMBLY BUILDING AE (Hangar AE) HAER NO. FL-8-B Location: Hangar Road, Cape Canaveral Air Force Station (CCAFS), Industrial Area, Brevard County, Florida. USGS Cape Canaveral, Florida, Quadrangle. Universal Transverse Mercator Coordinates: E 540610 N 3151547, Zone 17, NAD 1983. Date of Construction: 1959 Present Owner: National Aeronautics and Space Administration (NASA) Present Use: Home to NASA’s Launch Services Program (LSP) and the Launch Vehicle Data Center (LVDC). The LVDC allows engineers to monitor telemetry data during unmanned rocket launches. Significance: Missile Assembly Building AE, commonly called Hangar AE, is nationally significant as the telemetry station for NASA KSC’s unmanned Expendable Launch Vehicle (ELV) program. Since 1961, the building has been the principal facility for monitoring telemetry communications data during ELV launches and until 1995 it processed scientifically significant ELV satellite payloads. Still in operation, Hangar AE is essential to the continuing mission and success of NASA’s unmanned rocket launch program at KSC. It is eligible for listing on the National Register of Historic Places (NRHP) under Criterion A in the area of Space Exploration as Kennedy Space Center’s (KSC) original Mission Control Center for its program of unmanned launch missions and under Criterion C as a contributing resource in the CCAFS Industrial Area Historic District. -

PPP Over Ethernet Client
PPP over Ethernet Client The PPP over Ethernet Client feature provides PPP over Ethernet (PPPoE) client support on routers. PPPoE is a commonly used application in the deployment of digital subscriber lines (DSLs). The PPP over Ethernet Client feature expands PPPoE functionality by providing support for PPPoE on the client and the server. • Finding Feature Information, page 1 • Prerequisites for PPP over Ethernet Client, page 1 • Restrictions for PPP over Ethernet Client, page 2 • Information About PPP over Ethernet Client, page 2 • How to Configure PPP over Ethernet Client, page 5 • Configuration Examples for the PPP over Ethernet Client, page 13 • Additional References, page 19 • Feature Information for PPP over Ethernet Client, page 20 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Prerequisites for PPP over Ethernet Client PPP connections must be established between two endpoints over a serial link. Broadband Access Aggregation and DSL Configuration Guide, Cisco IOS XE -

Profit Embedded PHD : Process Trend User's Guide
Uniformance 160 Process Trend (Profit Embedded PHD) User's Guide Uniformance 160 Process Trend (Profit Embedded PHD) User's Guide Copyright, Notices, and Trademarks Copyright, Notices, and Trademarks © Honeywell Inc. 1998 – 2001. All Rights Reserved. Release 160 – March 30, 2001 While this information is presented in good faith and believed to be accurate, Honeywell disclaims the implied warranties of merchantability and fitness for a particular purpose and makes no express warranties except as may be stated in its written agreement with and for its customers. In no event is Honeywell liable to anyone for any indirect, special or consequential damages. The information and specifications in this document are subject to change without notice. Honeywell, TotalPlant, Uniformance, and Business.FLEX are U.S. registered trademarks of Honeywell Inc. Other brand or product names are trademarks of their respective owners. Release Information Uniformance 160 Revision: 1 Revision Date: April 2001 Document Number: AP20-530PS Honeywell Inc. Industrial Automation and Control Automation College 2500 West Union Hills Drive Phoenix, AZ, 85027 ii • Uniformance Process Trend User Guide Contents Contents Copyright, Notices, and Trademarks ii Release Information ii Contents iii About Process Trend 9 Overview 9 About this Guide 10 Who Should Use this Guide 10 What's in this Guide 10 Conventions Used in this Guide 11 Contact Us 11 Getting Started 13 System Requirements 13 Starting Process Trend 13 Logging into Process Trend 13 Bypassing the PHD Login 14 Saving -

Avocent® ACS800/8000 Advanced Console System Command Reference Guide TABLE of CONTENTS
Avocent® ACS800/8000 Advanced Console System Command Reference Guide The information contained in this document is subject to change without notice and may not be suitable for all applications. While every precaution has been taken to ensure the accuracy and completeness of this document, Vertiv assumes no responsibility and disclaims all liability for damages resulting from use of this information or for any errors or omissions. Refer to other local practices or building codes as applicable for the correct methods, tools, and materials to be used in performing procedures not specifically described in this document. The products covered by this instruction manual are manufactured and/or sold by Vertiv. This document is the property of Vertiv and contains confidential and proprietary information owned by Vertiv. Any copying, use or disclosure of it without the written permission of Vertiv is strictly prohibited. Names of companies and products are trademarks or registered trademarks of the respective companies. Any questions regarding usage of trademark names should be directed to the original manufacturer. Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual to see if the issue can be resolved by following outlined procedures. Visit https://www.VertivCo.com/en-us/support/ for additional assistance. Vertiv™ | Avocent® ACS800/8000 Advanced Console System Command Reference Guide TABLE OF CONTENTS 1 Introduction, Navigation and Commands 1 1.1 AccessOptionsand -

Solar Parameters for Modeling Interplanetary Background
— 2 — Solar parameters for modeling interplanetary background M. Bzowski, J.M. Sokoł´ Space Research Center Polish Academy of Sciences, Warsaw, Poland M. Tokumaru,K.Fujiki Solar-Terrestrial Environment Laboratory, Nagoya University, Nagoya, Japan E. Quemerais,R.Lallement LATMOS-IPSL, Universite Versailles Saint-Quentin, Guyancourt, France S. Ferron ACRI-ST, Sophia Antipolis, France P. Bochsler Space Science Center & Department of Physics, University of New Hampshire, Durham NH Physikalisches Institut, University of Bern, Bern, Switzerland D.J. McComas Southwest Research Institute, San Antonio TX University of Texas at San Antonio, San Antonio, TX 78249, USA Abstract The goal of the Fully Online Datacenter of Ultraviolet Emissions (FONDUE) Work- ing Team of the International Space Science Institute (ISSI) in Bern, Switzerland, was to establish a common calibration of various UV and EUV heliospheric observations, both spectroscopic and photometric. Realization of this goal required a credible and up-to-date model of spatial distribution of neutral interstellar hydrogen in the heliosphere, and to that end, a credible model of the radiation pressure and ionization processes was needed. This chapter describes the latter part of the project: the solar factors responsible for shap- arXiv:1112.2967v1 [astro-ph.SR] 13 Dec 2011 ing the distribution of neutral interstellar H in the heliosphere. Presented are the solar Lyman-alpha flux and the question of solar Lyman-alpha resonant radiation pressure force acting on neutral H atoms in the heliosphere, solar EUV radiation and the process of pho- toionization of heliospheric hydrogen, and their evolution in time and the still hypothetical variation with heliolatitude. Further, solar wind and its evolution with solar activity is 1 2 2. -

UNIVERSITY of CALIFORNIA Los Angeles Charged
UNIVERSITY OF CALIFORNIA Los Angeles Charged Particle Energization and Transport in the Magnetotail during Substorms A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Physics by Qingjiang Pan 2015 ABSTRACT OF THE DISSERTATION Charged Particle Energization and Transport in the Magnetotail during Substorms by Qingjiang Pan Doctor of Philosophy in Physics University of California, Los Angeles, 2015 Professor Maha Ashour-Abdalla, Chair This dissertation addresses the problem of energization of particles (both electrons and ions) to tens and hundreds of keV and the associated transport process in the magnetotail during substorms. Particles energized in the magnetotail are further accelerated to even higher energies (hundreds of keV to MeV) in the radiation belts, causing space weather hazards to human activities in space and on ground. We develop an analytical model to quantitatively estimate flux changes caused by betatron and Fermi acceleration when particles are transported along narrow high-speed flow channels from the magnetotail to the inner magnetosphere. The model shows that energetic particle flux can be significantly enhanced by a modest compression of the magnetic field and/or ii shrinking of the distance between the magnetic mirror points. We use coordinated spacecraft measurements, global magnetohydrodynamic (MHD) simulations driven by measured upstream solar wind conditions, and large-scale kinetic (LSK) simulations to quantify electron local acceleration in the near-Earth reconnection region and nonlocal acceleration during plasma earthward transport. Compared to the analytical model, application of the LSK simulations is much less restrictive because trajectories of millions of test particles are calculated in the realistically determined global MHD fields and the results are statistical.