Working with Oracle® Solaris 11.4 Directory and Naming Services: LDAP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open Directory & Openldap
Open Directory & OpenLDAP David M. O’Rourke Engineering Manager Overview • Background on Apple’s Open Directory Technology (8 minutes) – What is it – What is Directory Services • How has Apple integrated OpenLDAP (20 minutes or less) – what has Apple added to OpenLDAP? • Questions and Answers (remaining time) Open Directory • Open Directory is a technology name – Covers both client access technologies and server technologies – Integrates and promotes industry standard technologies • Open Directory is built into Mac OS X & Mac OS X Server – Been there since 10.0 • Open Sourced as part of Darwin – http://developer.apple.com/darwin/projects/ opendirectory/ What Is Directory Services • Abstraction API for read/write access to system configuration and management data – Users, groups, mount records and others – Authentication abstraction Mac OS X Software Directory Services NetInfo LDAP BSD Files Other… Directory Services in 10.3 • Includes – LDAPv3 (read/write), Native Active Directory, NetInfo, NIS, BSD/etc files – Service Discovery: Rendezvous, SMB, AppleTalk, and SLP – LDAPv3 client support replication fail over • Documented Access API and plug-in API – SDK posted – Sample code, sample plug-in, notes – Directory Services Headers are installed in – /System/Library/Frameworks/DirectoryService.framework – Command line tool for directory editing ‘dscl’ 10.3 Usage of Directory Services • Login Window uses Directory Services for all user authentication – Managed Desktop • All Security Framework authentication uses Directory Services • Legacy Unix -

The Lightning Memory-Mapped Database
The Lightning Memory-Mapped Database Howard Chu CTO, Symas Corp. [email protected] Chief Architect, OpenLDAP [email protected] 2015-09-21 OpenLDAP Project ● Open source code project ● Founded 1998 ● Three core team members ● A dozen or so contributors ● Feature releases every 12-18 months ● Maintenance releases as needed 2 A Word About Symas ● Founded 1999 ● Founders from Enterprise Software world – platinum Technology (Locus Computing) – IBM ● Howard joined OpenLDAP in 1999 – One of the Core Team members – Appointed Chief Architect January 2007 ● No debt, no VC investments: self-funded 3 Intro ● Howard Chu – Founder and CTO Symas Corp. – Developing Free/Open Source software since 1980s ● GNU compiler toolchain, e.g. "gmake -j", etc. ● Many other projects... – Worked for NASA/JPL, wrote software for Space Shuttle, etc. 4 Topics (1) Background (2) Features (3) Design Approach (4) Internals (5) Special Features (6) Results 5 (1) Background ● API inspired by Berkeley DB (BDB) – OpenLDAP has used BDB extensively since 1999 – Deep experience with pros and cons of BDB design and implementation – Omits BDB features that were found to be of no benefit ● e.g. extensible hashing – Avoids BDB characteristics that were problematic ● e.g. cache tuning, complex locking, transaction logs, recovery 6 (2) Features LMDB At A Glance ● Key/Value store using B+trees ● Fully transactional, ACID compliant ● MVCC, readers never block ● Uses memory-mapped files, needs no tuning ● Crash-proof, no recovery needed after restart ● Highly optimized, extremely compact – under 40KB object code, fits in CPU L1 I$ ● Runs on most modern OSs – Linux, Android, *BSD, MacOSX, iOS, Solaris, Windows, etc.. -

Overview and Frequently Asked Questions
Overview and Frequently Asked Questions OVERVIEW Oracle Buys Open Source Software Company Sleepycat - Expands Embedded Database Product Line with Berkeley DB Oracle has expanded its embedded Oracle’s portfolio of embedded database technologies provide database offerings through the customers with a range of technical options to meet their diverse needs, with the backing of a global support organization. Oracle acquisition of Sleepycat Software, Inc., and Sleepycat’s complementary products, expertise and resources a privately held supplier of open source will help accelerate innovation and provide customers with richer, database software for developers of more complete solutions. Oracle currently intends to continue embedded applications. Sleepycat’s dual license model and plans to continue to invest in the Berkeley DB products and support offerings, and to utilize Oracle’s global channel reach to service even more customers. With the proliferation of new applications, devices, appliances, Web Services and highly available Software as a Service (SaaS), In conjunction with the expansion of available embedded there is significant and growing demand for embedded databases. database options, Oracle has formed a global initiative focused In addition to Oracle Database Lite Edition for mobile devices on marketing, selling and servicing the Oracle Lite, TimesTen and Oracle TimesTen In-Memory Database for highly dynamic, and Berkeley DB products. This will include support procedures standards-compliant applications, Oracle now adds Berkeley DB and product release cycles tuned to the rapid-response needs database products for developers of tightly embedded, highly of embedded systems developers, and packaging and pricing customized applications. Berkeley DB is added to the Oracle flexibility that adjusts to the needs of Oracle’s partners. -

Release Notes (100 001420)
VERITAS File System™ 3.3.3 Release Notes Solaris January 2000 100-001420 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. Copyright Copyright © 2000 VERITAS Software Corporation. All rights reserved. VERITAS is a registered trademark of VERITAS Software Corporation in the US and other countries. The VERITAS logo and VERITAS File System are trademarks of VERITAS Software Corporation. All other trademarks or registered trademarks are the property of their respective owners. Printed in the USA, January 2000. VERITAS Software Corporation 1600 Plymouth St. Mountain View, CA 94043 Phone 650–335–8000 Fax 650–335–8050 www.veritas.com VERITAS File System Release Notes This guide provides information on VERITAS File System™ (VxFS) Release 3.3.3 for Solaris 2.5.1, Solaris 2.6, Solaris 7 (32-bit and 64-bit), and Solaris 8 (32-bit and 64-bit) operating systems. References in this document to VxFS 3.3 regarding new features, end of product support, compatibility, and software limitations apply to VxFS 3.3.3. Review this entire document before installing VxFS. The VERITAS File System packages include VxFS software, documentation, -

Mac OS X Server Administrator's Guide
034-9285.S4AdminPDF 6/27/02 2:07 PM Page 1 Mac OS X Server Administrator’s Guide K Apple Computer, Inc. © 2002 Apple Computer, Inc. All rights reserved. Under the copyright laws, this publication may not be copied, in whole or in part, without the written consent of Apple. The Apple logo is a trademark of Apple Computer, Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, AppleScript, AppleShare, AppleTalk, ColorSync, FireWire, Keychain, Mac, Macintosh, Power Macintosh, QuickTime, Sherlock, and WebObjects are trademarks of Apple Computer, Inc., registered in the U.S. and other countries. AirPort, Extensions Manager, Finder, iMac, and Power Mac are trademarks of Apple Computer, Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. Java and all Java-based trademarks and logos are trademarks or registered trademarks of Sun Microsystems, Inc. in the U.S. and other countries. Netscape Navigator is a trademark of Netscape Communications Corporation. RealAudio is a trademark of Progressive Networks, Inc. © 1995–2001 The Apache Group. All rights reserved. UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company, Ltd. 062-9285/7-26-02 LL9285.Book Page 3 Tuesday, June 25, 2002 3:59 PM Contents Preface How to Use This Guide 39 What’s Included -

Oracle Berkeley DB Installation and Build Guide Release 18.1
Oracle Berkeley DB Installation and Build Guide Release 18.1 Library Version 18.1.32 Legal Notice Copyright © 2002 - 2019 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Berkeley DB, and Sleepycat are trademarks or registered trademarks of Oracle. All rights to these marks are reserved. No third- party use is permitted without the express prior written consent of Oracle. Other names may be trademarks of their respective owners. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -
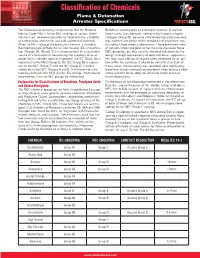
Classification of Chemicals
Classification of Chemicals Flame & Detonation Arrester Specifications PROTECTOSEAL ® The Protectoseal Company recommends that the National Butadiene would qualify as a Group D material. In each of Electric Code (NEC) Article 500, rankings of various chemi - these cases, the chemicals were primarly listed in a higher cals be used, whenever possible, to determine the suitability category (Group B), because of relatively high pressure read - of a detonation arrester for use with a particular chemical. ings noted in one phase of the standard test procedure con - When no NEC rating of the particular chemical is available, ducted by Underwriters Laboratories. These pressures were the International Electrotechnical Commission (IEC) classifica - of concern when categorizing the chemicals because these tion (Groups IIA, IIB and IIC) is recommended as a secondary NEC groupings are also used as standard indicators for the source of information for determining the suitability of an ar - design strength requirements of electrical boxes, apparatus, rester for its intended service. In general, the IEC Group IIA is etc. that must withstand the pressures generated by an igni - equivalent to the NEC Group D; the IEC Group IIB is equiva - tion within the container. It should be noted that, in each of lent to the NEC Group C; and the IEC Group IIC includes these cases, the test pressures recorded were significantly chemicals in the NEC Groups A and B. In the event of a dis - lower than those commonly encountered when testing a deto - crepancy between the NEC and the IEC ratings, Protectoseal nation arrester for its ability to withstand stable and over - recommends that the NEC groups be referenced. -

Unbound: a New Secure and High Performance Open Source DNS Server
New Open Source DNS Server Released Today Unbound – A Secure, High-Performance Alternative to BIND – Makes its Debut within Open Source Community Amsterdam, The Netherlands and Mountain View, CA – May 20, 2008 – Unbound – a new open source alternative to the BIND domain name system (DNS) server– makes its worldwide debut today with the worldwide public release of Unbound 1.0 at http://unbound.net. Released to open source developers by NLnet Labs, VeriSign, Inc. (NASDAQ: VRSN), Nominet, and Kirei, Unbound is a validating, recursive, and caching DNS server designed as a high- performance alternative for BIND (Berkeley Internet Name Domain). Unbound will be supported by NLnet Labs. An essential component of the Internet, the DNS ties domain names (such as www.verisign.com) to the IP addresses and other information that Web browsers need to access and interact with specific sites. Though it is unknown to the vast majority of Web users, DNS is at the heart of a range of Internet-based services beyond Web browsing, including email, messaging and Voice Over Internet Protocol (VOIP) telecommunications. Although BIND has been the de facto choice for DNS servers since the 1980s, a desire to seek an alternative server that excels in security, performance and ease of use prompted an effort to develop an open source DNS implementation. Unbound is the result of that effort. Mostly deployed by ISPs and enterprise users, Unbound will also be available for embedding in customer devices, such as dedicated DNS appliances and ADSL modems. By making Unbound code available to open source developers, its originators hope to enable rapid development of features that have not traditionally been associated with DNS. -

Stateless DNS
Technical Report KN{2014{DiSy{004 Distributed System Laboratory Stateless DNS Daniel Kaiser, Matthias Fratz, Marcel Waldvogel, Valentin Dietrich, Holger Strittmatter Distributed Systems Laboratory Department of Computer and Information Science University of Konstanz { Germany Konstanzer Online-Publikations-System (KOPS) URL: http://nbn-resolving.de/urn:nbn:de:bsz:352-0-267760 Abstract. Several network applications, like service discovery, file dis- covery in P2P networks, distributed hash tables, and distributed caches, use or would benefit from distributed key value stores. The Domain Name System (DNS) is a key value store which has a huge infrastructure and is accessible from almost everywhere. Nevertheless storing information in this database makes it necessary to be authoritative for a domain or to be \registered" with a domain, e.g. via DynDNS, to be allowed to store and update resource records using nsupdate . Applications like the ones listed above would greatly benefit from a configurationless approach, giving users a much more convenient experience. In this report we describe a technique we call Stateless DNS, which allows to store data in the cache of the local DNS server. It works without any infrastructure updates; it just needs our very simple, configurationless echo DNS server that can parse special queries containing information desired to be stored, process this information, and generate DNS answers in a way that the DNS cache that was asked the special query will store the desired information. Because all this happens in the authority zone of our echo DNS server, we do not cause cache poisoning. Our tests show that Stateless DNS works with a huge number of public DNS servers. -

UNIX (Solaris/Linux) Quick Reference Card Logging in Directory Commands at the Login: Prompt, Enter Your Username
UNIX (Solaris/Linux) QUICK REFERENCE CARD Logging In Directory Commands At the Login: prompt, enter your username. At the Password: prompt, enter ls Lists files in current directory your system password. Linux is case-sensitive, so enter upper and lower case ls -l Long listing of files letters as required for your username, password and commands. ls -a List all files, including hidden files ls -lat Long listing of all files sorted by last Exiting or Logging Out modification time. ls wcp List all files matching the wildcard Enter logout and press <Enter> or type <Ctrl>-D. pattern Changing your Password ls dn List files in the directory dn tree List files in tree format Type passwd at the command prompt. Type in your old password, then your new cd dn Change current directory to dn password, then re-enter your new password for verification. If the new password cd pub Changes to subdirectory “pub” is verified, your password will be changed. Many systems age passwords; this cd .. Changes to next higher level directory forces users to change their passwords at predetermined intervals. (previous directory) cd / Changes to the root directory Changing your MS Network Password cd Changes to the users home directory cd /usr/xx Changes to the subdirectory “xx” in the Some servers maintain a second password exclusively for use with Microsoft windows directory “usr” networking, allowing you to mount your home directory as a Network Drive. mkdir dn Makes a new directory named dn Type smbpasswd at the command prompt. Type in your old SMB passwword, rmdir dn Removes the directory dn (the then your new password, then re-enter your new password for verification. -

Brave Gnu World
LINUXCOVERCOMMUNITY USERSTORY SchlagwortSchlagwortBrave GNU sollte Worldsollte hier hier stehen stehen Schlagwort sollte hier stehen COVER STORY The Monthly GNU Column BRAVE GNU WORLD This column looks into projects and current affairs in the world of free software from the perspective of the GNU Project and the FSF. In this issue, I’ll focus on Comspari and the EU decision on software patents. BY GEORG C.F. GREVE n the past, the German government the Kroupware project in 2002. The pub- principles back to front. For example, has often caused a (positive) stir due lic tender by the BSI was aimed to pro- many other solutions are based on the Ito its activities with free software. duce a groupware solution that would principle that the server is the king of The Federal Ministry of the Economy support strong cryptography and inte- the hill and the users have to bow down (BMWi) sponsored Gnupg [1], for exam- grate seamlessly into a heterogeneous and worship it. The Kolab server does ple. Add to this a number of accompany- environment. things differently. The program makes ing activities, such as a report by the The government office gave a consor- the user king, and gives the user power Bavarian Accounts Office, the KBST let- tium comprising Erfrakon, Klarälvdalens to do things. The software simply helps ter, and the highly acclaimed migration Datakonsult [2], and Intevation [3] the coordinate things as a central intermedi- guide by the Federal Ministry of the Inte- task of developing the software. Inter- ary. rior (BMI). nally, the design and the software was Kolab 1 combined so-called partial referred to as Kolab 1. -

The GNU C Library: System & Network Applications
The GNU C Library: System & Network Applications For GNU C Libraries version 2.3.x by Sandra Loosemore with Richard M. Stallman, Roland McGrath, Andrew Oram, and Ulrich Drepper This manual documents the GNU C Libraries version 2.3.x. ISBN 1-882114-24-8, First Printing, March 2004. Published by: GNU Press Website: www.gnupress.org a division of the General: [email protected] Free Software Foundation Orders: [email protected] 51 Franklin St, Fifth Floor Tel: 617-542-5942 Boston, MA 02110-1301 USA Fax: 617-542-2652 Copyright © 1999, 2000, 2001, 2002, 2003, 2004 Free Software Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2, or any later version published by the Free Software Foundation; with the Invariant Sections being “Free Software and Free Manuals”, the “GNU Free Documentation License”," and the “GNU Lesser General Public License”, with the Front Cover Texts being “A GNU Manual”, and with the Back Cover Texts as in (a) below. A copy of the license is included in the section entitled “GNU Free Documentation License”. (a) The Back Cover Text is: You are free to copy and modify this GNU Manual. Buying copies from GNU Press supports the FSF in developing GNU and promoting software freedom. Cover art by Etienne Suvasa. Cover design by Jonathan Richard. Printed in USA. i Short Contents 1 Introduction ............................................ 1 2 Low-Level Input/Output .................................. 17 3 File-System Interface .................................... 71 4 Pipes and FIFOs ...................................... 119 5 Sockets .............................................. 125 6 Low-Level Terminal Interface ...........................