Powermax OS User's Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

Tortoisemerge a Diff/Merge Tool for Windows Version 1.11
TortoiseMerge A diff/merge tool for Windows Version 1.11 Stefan Küng Lübbe Onken Simon Large TortoiseMerge: A diff/merge tool for Windows: Version 1.11 by Stefan Küng, Lübbe Onken, and Simon Large Publication date 2018/09/22 18:28:22 (r28377) Table of Contents Preface ........................................................................................................................................ vi 1. TortoiseMerge is free! ....................................................................................................... vi 2. Acknowledgments ............................................................................................................. vi 1. Introduction .............................................................................................................................. 1 1.1. Overview ....................................................................................................................... 1 1.2. TortoiseMerge's History .................................................................................................... 1 2. Basic Concepts .......................................................................................................................... 3 2.1. Viewing and Merging Differences ...................................................................................... 3 2.2. Editing Conflicts ............................................................................................................. 3 2.3. Applying Patches ........................................................................................................... -

CST8207 – Linux O/S I
Mounting a Filesystem Directory Structure Fstab Mount command CST8207 - Algonquin College 2 Chapter 12: page 467 - 496 CST8207 - Algonquin College 3 The mount utility connects filesystems to the Linux directory hierarchy. The mount point is a directory in the local filesystem where you can access mounted filesystem. This directory must exist before you can mount a filesystem. All filesystems visible on the system exist as a mounted filesystem someplace below the root (/) directory CST8207 - Algonquin College 4 can be mounted manually ◦ can be listed in /etc/fstab, but not necessary ◦ all mounting information supplied manually at command line by user or administrator can be mounted automatically on startup ◦ must be listed /etc/fstab, with all appropriate information and options required Every filesystem, drive, storage device is listed as a mounted filesystem associated to a directory someplace under the root (/) directory CST8207 - Algonquin College 5 CST8207 - Algonquin College 6 Benefits Scalable ◦ As new drives are added and new partitions are created, further filesystems can be mounted at various mount points as required. ◦ This means a Linux system does not need to worry about running out of disk space. Transparent ◦ No application would stop working if transferred to a different partition, because access to data is done via the mount point. ◦ Also transparent to user CST8207 - Algonquin College 7 All known filesystems volumes are typically listed in the /etc/fstab (static information about filesystem) file to help automate the mounting process If it is not listed in the /etc/fstab file, then all appropriate information about the filesystem needs to be listed manually at the command line. -

Job Scheduling for SAP® Contents at a Glance
Kees Verruijt, Arnoud Roebers, Anjo de Heus Job Scheduling for SAP® Contents at a Glance Foreword ............................................................................ 13 Preface ............................................................................... 15 1 General Job Scheduling ...................................................... 19 2 Decentralized SAP Job Scheduling .................................... 61 3 SAP Job Scheduling Interfaces .......................................... 111 4 Centralized SAP Job Scheduling ........................................ 125 5 Introduction to SAP Central Job Scheduling by Redwood ... 163 6Installation......................................................................... 183 7 Principles and Processes .................................................... 199 8Operation........................................................................... 237 9Customer Cases................................................................. 281 The Authors ........................................................................ 295 Index .................................................................................. 297 Contents Foreword ............................................................................................... 13 Preface ................................................................................................... 15 1 General Job Scheduling ...................................................... 19 1.1 Organizational Uses of Job Scheduling .................................. -

Unix Command Line; Editors
Unix command line; editors Karl Broman Biostatistics & Medical Informatics, UW–Madison kbroman.org github.com/kbroman @kwbroman Course web: kbroman.org/AdvData My goal in this lecture is to convince you that (a) command-line-based tools are the things to focus on, (b) you need to choose a powerful, universal text editor (you’ll use it a lot), (c) you want to be comfortable and skilled with each. For your work to be reproducible, it needs to be code-based; don’t touch that mouse! Windows vs. Mac OSX vs. Linux Remote vs. Not 2 The Windows operating system is not very programmer-friendly. Mac OSX isn’t either, but under the hood, it’s just unix. Don’t touch the mouse! Open a terminal window and start typing. I do most of my work directly on my desktop or laptop. You might prefer to work remotely on a server, instead. But I can’t stand having any lag in looking at graphics. If you use Windows... Consider Git Bash (or Cygwin) or turn on the Windows subsystem for linux 3 Cygwin is an effort to get Unix command-line tools in Windows. Git Bash combines git (for version control) and bash (the unix shell); it’s simpler to deal with than Cygwin. Linux is now accessible in Windows 10, but you have to enable it. If you use a Mac... Consider Homebrew and iTerm2 Also the XCode command line tools 4 Homebrew is a packaging system; iTerm2 is a Terminal replacement. The XCode command line tools are a must for most unixy things on a Mac. -

Motor Vehicle Division Prestige License Plate Application
For State or County use only: Denied Refund Form MV-9B (Rev. 08-2017) Web and MV Manual Georgia Department of Revenue - Motor Vehicle Division Prestige License Plate Application ______________________________________________________________________________________ Purpose of this Form: This form is to be used by a vehicle owner to request the manufacture of a Special Prestige (Personalized) License Plate. This form should not be used to record a change of ownership, change of address, or change of license plate classification. How to submit this form: After reviewing the MV-9B form instructions, this fully completed form must be submitted to your local County tag office. Please refer to our website at https://mvd.dor.ga.gov/motor/tagoffices/SelectTagOffice.aspx to locate the address(es) for your specific County. OWNER INFORMATION First Name Middle Initial Last Name Suffix Owners’ Full Legal Name: Mailing Address: City: State: Zip: Telephone Number: Owner(s)’ Full Legal Name: First Name Middle Initial Last Name Suffix If secondary Owner(s) are listed Mailing Address: City: State: Zip: Telephone Number: VEHICLE INFORMATION Vehicle Identification Number (VIN): Year: Make: Model: LICENSE PLATE COMBINATION Private Passenger Vehicle (Includes Motor Home and Non-Commercial Trailer) Note: Private passenger vehicles cannot exceed seven (7) letters and/or numbers including spaces. Meaning: ___________________________ Meaning: ___________________________ Meaning: ___________________________ (Required) (Required) (Required) Motorcycle Note: Motorcycles cannot exceed six (6) letters and/or numbers including spaces. Meaning: ___________________________ Meaning: ___________________________ Meaning: ___________________________ (Required) (Required) (Required) Note: No punctuation or symbols are allowed on a license plate. Only letters, numbers, and spaces are allowed. I request that a personal prestige license plate be manufactured. -

Release Notes (100 001420)
VERITAS File System™ 3.3.3 Release Notes Solaris January 2000 100-001420 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. Copyright Copyright © 2000 VERITAS Software Corporation. All rights reserved. VERITAS is a registered trademark of VERITAS Software Corporation in the US and other countries. The VERITAS logo and VERITAS File System are trademarks of VERITAS Software Corporation. All other trademarks or registered trademarks are the property of their respective owners. Printed in the USA, January 2000. VERITAS Software Corporation 1600 Plymouth St. Mountain View, CA 94043 Phone 650–335–8000 Fax 650–335–8050 www.veritas.com VERITAS File System Release Notes This guide provides information on VERITAS File System™ (VxFS) Release 3.3.3 for Solaris 2.5.1, Solaris 2.6, Solaris 7 (32-bit and 64-bit), and Solaris 8 (32-bit and 64-bit) operating systems. References in this document to VxFS 3.3 regarding new features, end of product support, compatibility, and software limitations apply to VxFS 3.3.3. Review this entire document before installing VxFS. The VERITAS File System packages include VxFS software, documentation, -

A Brief Introduction to Unix-2019-AMS
Brief Intro to Linux/Unix Brief Intro to Unix (contd) A Brief Introduction to o Brief History of Unix o Compilers, Email, Text processing o Basics of a Unix session o Image Processing Linux/Unix – AMS 2019 o The Unix File System Pete Pokrandt o Working with Files and Directories o The vi editor UW-Madison AOS Systems Administrator o Your Environment [email protected] o Common Commands Twitter @PTH1 History of Unix History of Unix History of Unix o Created in 1969 by Kenneth Thompson and Dennis o Today – two main variants, but blended o It’s been around for a long time Ritchie at AT&T o Revised in-house until first public release 1977 o System V (Sun Solaris, SGI, Dec OSF1, AIX, o It was written by computer programmers for o 1977 – UC-Berkeley – Berkeley Software Distribution (BSD) linux) computer programmers o 1983 – Sun Workstations produced a Unix Workstation o BSD (Old SunOS, linux, Mac OSX/MacOS) o Case sensitive, mostly lowercase o AT&T unix -> System V abbreviations 1 Basics of a Unix Login Session Basics of a Unix Login Session Basics of a Unix Login Session o The Shell – the command line interface, o Features provided by the shell o Logging in to a unix session where you enter commands, etc n Create an environment that meets your needs n login: username n Some common shells n Write shell scripts (batch files) n password: tImpAw$ n Define command aliases (this Is my password At work $) Bourne Shell (sh) OR n Manipulate command history IHateHaving2changeMypasswordevery3weeks!!! C Shell (csh) n Automatically complete the command -

Epmp Command Line Interface User Guide
USER GUIDE ePMP Command Line Interface ePMP Command Line Interface User Manual Table of Contents 1 Introduction ...................................................................................................................................... 3 1.1 Purpose ................................................................................................................................ 3 1.2 Command Line Access ........................................................................................................ 3 1.3 Command usage syntax ...................................................................................................... 3 1.4 Basic information ................................................................................................................. 3 1.4.1 Context sensitive help .......................................................................................................... 3 1.4.2 Auto-completion ................................................................................................................... 3 1.4.3 Movement keys .................................................................................................................... 3 1.4.4 Deletion keys ....................................................................................................................... 4 1.4.5 Escape sequences .............................................................................................................. 4 2 Command Line Interface Overview .............................................................................................. -
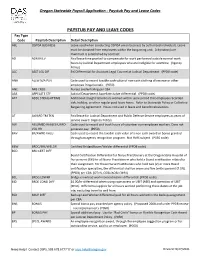
Oregon Statewide Payroll Application ‐ Paystub Pay and Leave Codes
Oregon Statewide Payroll Application ‐ Paystub Pay and Leave Codes PAYSTUB PAY AND LEAVE CODES Pay Type Code Paystub Description Detail Description ABL OSPOA BUSINESS Leave used when conducting OSPOA union business by authorized individuals. Leave must be donated from employees within the bargaining unit. A donation/use maximum is established by contract. AD ADMIN LV Paid leave time granted to compensate for work performed outside normal work hours by Judicial Department employees who are ineligible for overtime. (Agency Policy) ALC ASST LGL DIF 5% Differential for Assistant Legal Counsel at Judicial Department. (PPDB code) ANA ALLW N/A PLN Code used to record taxable cash value of non-cash clothing allowance or other employee fringe benefit. (P050) ANC NRS CRED Nurses credentialing per CBA ASA APPELATE STF Judicial Department Appellate Judge differential. (PPDB code) AST ADDL STRAIGHTTIME Additional straight time hours worked within same period that employee recorded sick, holiday, or other regular paid leave hours. Refer to Statewide Policy or Collective Bargaining Agreement. Hours not used in leave and benefit calculations. AT AWARD TM TKN Paid leave for Judicial Department and Public Defense Service employees as years of service award. (Agency Policy) AW ASSUMED WAGES-UNPD Code used to record and track hours of volunteer non-employee workers. Does not VOL HR generate pay. (P050) BAV BP/AWRD VALU Code used to record the taxable cash value of a non-cash award or bonus granted through an agency recognition program. Not PERS subject. (P050 code) BBW BRDG/BM/WELDR Certified Bridge/Boom/Welder differential (PPDB code) BCD BRD CERT DIFF Board Certification Differential for Nurse Practitioners at the Oregon State Hospital of five percent (5%) for all Nurse Practitioners who hold a Board certification related to their assignment. -

Student Number: Surname: Given Name
Computer Science 2211a Midterm Examination Sample Solutions 9 November 20XX 1 hour 40 minutes Student Number: Surname: Given name: Instructions/Notes: The examination has 35 questions on 9 pages, and a total of 110 marks. Put all answers on the question paper. This is a closed book exam. NO ELECTRONIC DEVICES OF ANY KIND ARE ALLOWED. 1. [4 marks] Which of the following Unix commands/utilities are filters? Correct answers are in blue. mkdir cd nl passwd grep cat chmod scriptfix mv 2. [1 mark] The Unix command echo HOME will print the contents of the environment variable whose name is HOME. True False 3. [1 mark] In C, the null character is another name for the null pointer. True False 4. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod a=x abc.dat is equivalent to the command: a. chmod 755 abc.dat b. chmod 711 abc.dat c. chmod 155 abc.dat d. chmod 111 abc.dat e. none of the above 5. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod ug+w abc.dat is equivalent to the command: a. chmod 766 abc.dat b. chmod 764 abc.dat c. chmod 754 abc.dat d. chmod 222 abc.dat e. none of the above 2 6. [3 marks] The protection code for def.dat is currently dr-xr--r-- , and the protection code for def.dat/ghi.dat is currently -r-xr--r-- . Give one or more chmod commands that will set the protections properly so that the owner of the two files will be able to delete ghi.dat using the command rm def.dat/ghi.dat chmod u+w def.dat or chmod –r u+w def.dat 7. -
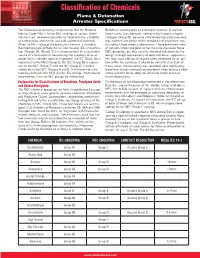
Classification of Chemicals
Classification of Chemicals Flame & Detonation Arrester Specifications PROTECTOSEAL ® The Protectoseal Company recommends that the National Butadiene would qualify as a Group D material. In each of Electric Code (NEC) Article 500, rankings of various chemi - these cases, the chemicals were primarly listed in a higher cals be used, whenever possible, to determine the suitability category (Group B), because of relatively high pressure read - of a detonation arrester for use with a particular chemical. ings noted in one phase of the standard test procedure con - When no NEC rating of the particular chemical is available, ducted by Underwriters Laboratories. These pressures were the International Electrotechnical Commission (IEC) classifica - of concern when categorizing the chemicals because these tion (Groups IIA, IIB and IIC) is recommended as a secondary NEC groupings are also used as standard indicators for the source of information for determining the suitability of an ar - design strength requirements of electrical boxes, apparatus, rester for its intended service. In general, the IEC Group IIA is etc. that must withstand the pressures generated by an igni - equivalent to the NEC Group D; the IEC Group IIB is equiva - tion within the container. It should be noted that, in each of lent to the NEC Group C; and the IEC Group IIC includes these cases, the test pressures recorded were significantly chemicals in the NEC Groups A and B. In the event of a dis - lower than those commonly encountered when testing a deto - crepancy between the NEC and the IEC ratings, Protectoseal nation arrester for its ability to withstand stable and over - recommends that the NEC groups be referenced.