Chapter 2 Primitive Data Type and Operations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1=Haskell =1=Making Our Own Types and Typeclasses
Haskell Making Our Own Types and Typeclasses http://igm.univ-mlv.fr/~vialette/?section=teaching St´ephaneVialette LIGM, Universit´eParis-Est Marne-la-Vall´ee November 13, 2016 Making Our Own Types and Typeclasses Algebraic data types intro So far, we've run into a lot of data types: Bool, Int, Char, Maybe, etc. But how do we make our own? One way is to use the data keyword to define a type. Let's see how the Bool type is defined in the standard library. data Bool= False| True data means that we're defining a new data type. Making Our Own Types and Typeclasses Algebraic data types intro data Bool= False| True The part before the = denotes the type, which is Bool. The parts after the = are value constructors. They specify the different values that this type can have. The | is read as or. So we can read this as: the Bool type can have a value of True or False. Both the type name and the value constructors have to be capital cased. Making Our Own Types and Typeclasses Algebraic data types intro We can think of the Int type as being defined like this: data Int=-2147483648|-2147483647| ...|-1|0|1|2| ...| 2147483647 The first and last value constructors are the minimum and maximum possible values of Int. It's not actually defined like this, the ellipses are here because we omitted a heapload of numbers, so this is just for illustrative purposes. Shape let's think about how we would represent a shape in Haskell. -

A Polymorphic Type System for Extensible Records and Variants
A Polymorphic Typ e System for Extensible Records and Variants Benedict R. Gaster and Mark P. Jones Technical rep ort NOTTCS-TR-96-3, November 1996 Department of Computer Science, University of Nottingham, University Park, Nottingham NG7 2RD, England. fbrg,[email protected] Abstract b oard, and another indicating a mouse click at a par- ticular p oint on the screen: Records and variants provide exible ways to construct Event = Char + Point : datatyp es, but the restrictions imp osed by practical typ e systems can prevent them from b eing used in ex- These de nitions are adequate, but they are not par- ible ways. These limitations are often the result of con- ticularly easy to work with in practice. For example, it cerns ab out eciency or typ e inference, or of the di- is easy to confuse datatyp e comp onents when they are culty in providing accurate typ es for key op erations. accessed by their p osition within a pro duct or sum, and This pap er describ es a new typ e system that reme- programs written in this way can b e hard to maintain. dies these problems: it supp orts extensible records and To avoid these problems, many programming lan- variants, with a full complement of p olymorphic op era- guages allow the comp onents of pro ducts, and the al- tions on each; and it o ers an e ective type inference al- ternatives of sums, to b e identi ed using names drawn gorithm and a simple compilation metho d. -

Lecture 2: Variables and Primitive Data Types
Lecture 2: Variables and Primitive Data Types MIT-AITI Kenya 2005 1 In this lecture, you will learn… • What a variable is – Types of variables – Naming of variables – Variable assignment • What a primitive data type is • Other data types (ex. String) MIT-Africa Internet Technology Initiative 2 ©2005 What is a Variable? • In basic algebra, variables are symbols that can represent values in formulas. • For example the variable x in the formula f(x)=x2+2 can represent any number value. • Similarly, variables in computer program are symbols for arbitrary data. MIT-Africa Internet Technology Initiative 3 ©2005 A Variable Analogy • Think of variables as an empty box that you can put values in. • We can label the box with a name like “Box X” and re-use it many times. • Can perform tasks on the box without caring about what’s inside: – “Move Box X to Shelf A” – “Put item Z in box” – “Open Box X” – “Remove contents from Box X” MIT-Africa Internet Technology Initiative 4 ©2005 Variables Types in Java • Variables in Java have a type. • The type defines what kinds of values a variable is allowed to store. • Think of a variable’s type as the size or shape of the empty box. • The variable x in f(x)=x2+2 is implicitly a number. • If x is a symbol representing the word “Fish”, the formula doesn’t make sense. MIT-Africa Internet Technology Initiative 5 ©2005 Java Types • Integer Types: – int: Most numbers you’ll deal with. – long: Big integers; science, finance, computing. – short: Small integers. -

Source Code Auditing: Day 2
Source Code Auditing: Day 2 Penetration Testing & Vulnerability Analysis Brandon Edwards [email protected] Data Types Continued Data Type Signedness Remember, by default all data types are signed unless specifically declared otherwise But many functions which accept size arguments take unsigned values What is the difference of the types below? char y; unsigned char x; x = 255; y = -1; 3 Data Type Signedness These types are the same size (8-bits) char y; unsigned char x; 4 Data Type Signedness A large value in the unsigned type (highest bit set) is a negative value in the signed type char y; unsigned char x; 5 Data Type Bugs Same concept applies to 16 and 32 bit data types What are the implications of mixing signed & unsigned types ? #define MAXSOCKBUF 4096 int readNetworkData(int sock) { char buf[MAXSOCKBUF]; int length; read(sock, (char *)&length, 4); if (length < MAXSOCKBUF) { read(sock, buf, length); } } 6 Data Type Signedness The check is between two signed values… #define MAXSOCKBUF 4096 if (length < MAXSOCKBUF) So if length is negative (highest bit / signed bit set), it will evaluate as less than MAXSOCKBUF But the read() function takes only unsigned values for it’s size Remember, the highest bit (or signed bit is set), and the compiler implicitly converts the length to unsigned for read() 7 Data Type Signedness So what if length is -1 (or 0xFFFFFFFF in hex)? #define MAXSOCKBUF 4096 if (length < MAXSOCKBUF) { read(sock, buf, length); } When the length check is performed, it is asking if -1 is less than 4096 When the length is passed to read, it is converted to unsigned and becomes the unsigned equivalent of -1, which for 32bits is 4294967295 8 Data Type Bugs Variation in data type sizes can also introduce bugs Remember the primitive data type sizes? (x86): An integer type is 32bits A short type is 16bits A char type is 8 bits Sometimes code is written without considering differences between these. -

UML Profile for Communicating Systems a New UML Profile for the Specification and Description of Internet Communication and Signaling Protocols
UML Profile for Communicating Systems A New UML Profile for the Specification and Description of Internet Communication and Signaling Protocols Dissertation zur Erlangung des Doktorgrades der Mathematisch-Naturwissenschaftlichen Fakultäten der Georg-August-Universität zu Göttingen vorgelegt von Constantin Werner aus Salzgitter-Bad Göttingen 2006 D7 Referent: Prof. Dr. Dieter Hogrefe Korreferent: Prof. Dr. Jens Grabowski Tag der mündlichen Prüfung: 30.10.2006 ii Abstract This thesis presents a new Unified Modeling Language 2 (UML) profile for communicating systems. It is developed for the unambiguous, executable specification and description of communication and signaling protocols for the Internet. This profile allows to analyze, simulate and validate a communication protocol specification in the UML before its implementation. This profile is driven by the experience and intelligibility of the Specification and Description Language (SDL) for telecommunication protocol engineering. However, as shown in this thesis, SDL is not optimally suited for specifying communication protocols for the Internet due to their diverse nature. Therefore, this profile features new high-level language concepts rendering the specification and description of Internet protocols more intuitively while abstracting from concrete implementation issues. Due to its support of several concrete notations, this profile is designed to work with a number of UML compliant modeling tools. In contrast to other proposals, this profile binds the informal UML semantics with many semantic variation points by defining formal constraints for the profile definition and providing a mapping specification to SDL by the Object Constraint Language. In addition, the profile incorporates extension points to enable mappings to many formal description languages including SDL. To demonstrate the usability of the profile, a case study of a concrete Internet signaling protocol is presented. -

Java Secrets.Pdf
Java Secrets by Elliotte Rusty Harold IDG Books, IDG Books Worldwide, Inc. ISBN: 0764580078 Pub Date: 05/01/97 Buy It Preface About the Author Part I—How Java Works Chapter 1—Introducing Java SECRETS A Little Knowledge Can Be a Dangerous Thing What’s in This Book? Part I: How Java Works Part II: The sun Classes Part III: Platform-Dependent Java Why Java Secrets? Broader applicability More power Inspiration Where Did the Secrets Come From? Where is the documentation? The source code The API documentation What Versions of Java Are Covered? Some Objections Java is supposed to be platform independent Why aren’t these things documented? FUD (fear, uncertainty, and doubt) How secret is this, anyway? Summary Chapter 2—Primitive Data Types Bytes in Memory Variables, Values, and Identifiers Place-Value Number Systems Binary notation Hexadecimal notation Octal notation Integers ints Long, short, and byte Floating-Point Numbers Representing floating-point numbers in binary code Special values Denormalized floating-point numbers CHAR ASCII ISO Latin-1 Unicode UTF8 Boolean Cross-Platform Issues Byte order Unsigned integers Integer widths Conversions and Casting Using a cast The mechanics of conversion Bit-Level Operators Some terminology Bitwise operators Bit shift operators Summary Chapter 2—Primitive Data Types Bytes in Memory Variables, Values, and Identifiers Place-Value Number Systems Binary notation Hexadecimal notation Octal notation Integers ints Long, short, and byte Floating-Point Numbers Representing floating-point numbers in binary code -

Lecture Slides
Outline Meta-Classes Guy Wiener Introduction AOP Classes Generation 1 Introduction Meta-Classes in Python Logging 2 Meta-Classes in Python Delegation Meta-Classes vs. Traditional OOP 3 Meta-Classes vs. Traditional OOP Outline Meta-Classes Guy Wiener Introduction AOP Classes Generation 1 Introduction Meta-Classes in Python Logging 2 Meta-Classes in Python Delegation Meta-Classes vs. Traditional OOP 3 Meta-Classes vs. Traditional OOP What is Meta-Programming? Meta-Classes Definition Guy Wiener Meta-Program A program that: Introduction AOP Classes One of its inputs is a program Generation (possibly itself) Meta-Classes in Python Its output is a program Logging Delegation Meta-Classes vs. Traditional OOP Meta-Programs Nowadays Meta-Classes Guy Wiener Introduction AOP Classes Generation Compilers Meta-Classes in Python Code Generators Logging Delegation Model-Driven Development Meta-Classes vs. Traditional Templates OOP Syntactic macros (Lisp-like) Meta-Classes The Problem With Static Programming Meta-Classes Guy Wiener Introduction AOP Classes Generation Meta-Classes How to share features between classes and class hierarchies? in Python Logging Share static attributes Delegation Meta-Classes Force classes to adhere to the same protocol vs. Traditional OOP Share code between similar methods Meta-Classes Meta-Classes Guy Wiener Introduction AOP Classes Definition Generation Meta-Classes in Python Meta-Class A class that creates classes Logging Delegation Objects that are instances of the same class Meta-Classes share the same behavior vs. Traditional OOP Classes that are instances of the same meta-class share the same behavior Meta-Classes Meta-Classes Guy Wiener Introduction AOP Classes Definition Generation Meta-Classes in Python Meta-Class A class that creates classes Logging Delegation Objects that are instances of the same class Meta-Classes share the same behavior vs. -

Haskell-Style Type Classes with Isabelle/Isar
Isar ∀ Isabelle= α λ β → Haskell-style type classes with Isabelle/Isar Florian Haftmann 20 February 2021 Abstract This tutorial introduces Isar type classes, which are a convenient mech- anism for organizing specifications. Essentially, they combine an op- erational aspect (in the manner of Haskell) with a logical aspect, both managed uniformly. 1 INTRODUCTION 1 1 Introduction Type classes were introduced by Wadler and Blott [8] into the Haskell lan- guage to allow for a reasonable implementation of overloading1. As a canon- ical example, a polymorphic equality function eq :: α ) α ) bool which is overloaded on different types for α, which is achieved by splitting introduc- tion of the eq function from its overloaded definitions by means of class and instance declarations: 2 class eq where eq :: α ) α ) bool instance nat :: eq where eq 0 0 = True eq 0 - = False eq - 0 = False eq (Suc n)(Suc m) = eq n m instance (α::eq; β::eq) pair :: eq where eq (x1; y1) (x2; y2) = eq x1 x2 ^ eq y1 y2 class ord extends eq where less-eq :: α ) α ) bool less :: α ) α ) bool Type variables are annotated with (finitely many) classes; these annotations are assertions that a particular polymorphic type provides definitions for overloaded functions. Indeed, type classes not only allow for simple overloading but form a generic calculus, an instance of order-sorted algebra [5, 6, 10]. From a software engineering point of view, type classes roughly correspond to interfaces in object-oriented languages like Java; so, it is naturally desirable that type classes do not only provide functions (class parameters) but also state specifications implementations must obey. -

OMG Meta Object Facility (MOF) Core Specification
Date : October 2019 OMG Meta Object Facility (MOF) Core Specification Version 2.5.1 OMG Document Number: formal/2019-10-01 Standard document URL: https://www.omg.org/spec/MOF/2.5.1 Normative Machine-Readable Files: https://www.omg.org/spec/MOF/20131001/MOF.xmi Informative Machine-Readable Files: https://www.omg.org/spec/MOF/20131001/CMOFConstraints.ocl https://www.omg.org/spec/MOF/20131001/EMOFConstraints.ocl Copyright © 2003, Adaptive Copyright © 2003, Ceira Technologies, Inc. Copyright © 2003, Compuware Corporation Copyright © 2003, Data Access Technologies, Inc. Copyright © 2003, DSTC Copyright © 2003, Gentleware Copyright © 2003, Hewlett-Packard Copyright © 2003, International Business Machines Copyright © 2003, IONA Copyright © 2003, MetaMatrix Copyright © 2015, Object Management Group Copyright © 2003, Softeam Copyright © 2003, SUN Copyright © 2003, Telelogic AB Copyright © 2003, Unisys USE OF SPECIFICATION - TERMS, CONDITIONS & NOTICES The material in this document details an Object Management Group specification in accordance with the terms, conditions and notices set forth below. This document does not represent a commitment to implement any portion of this specification in any company's products. The information contained in this document is subject to change without notice. LICENSES The companies listed above have granted to the Object Management Group, Inc. (OMG) a nonexclusive, royalty-free, paid up, worldwide license to copy and distribute this document and to modify this document and distribute copies of the modified version. Each of the copyright holders listed above has agreed that no person shall be deemed to have infringed the copyright in the included material of any such copyright holder by reason of having used the specification set forth herein or having conformed any computer software to the specification. -
Metaclasses 4 ◆ Dynamic Binding Implies That Classes Must Have Some ◆ Meta-: Beyond; Transcending; More Comprehensive; E.G., As Memory Representation
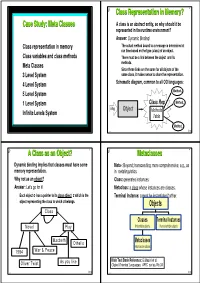
® 1 ® Class Representation in Memory? 2 Case Study: Meta Classes ◆ A class is an abstract entity, so why should it be represented in the runtime environment? ◆ Answer: Dynamic Binding! ◆ Class representation in memory ● The actual method bound to a message is determined at run time based on the type (class) of an object. ◆ Class variables and class methods ● There must be a link between the object and its ◆ Meta Classes methods. ● Since these links are the same for all objects of the ◆ 3 Level System same class, it makes sense to share the representation. ◆ ◆ 4 Level System Schematic diagram, common to all OO languages: Method ◆ 5 Level System 1 Method ◆ 1 Level System Class Rep 2 ◆ Msg Object Methods Infinite Levels System Table Methodn oop Õ Ö oop Õ Ö ® A Class as an Object? 3 ® Metaclasses 4 ◆ Dynamic binding implies that classes must have some ◆ Meta-: Beyond; transcending; more comprehensive; e.g., as memory representation. in metalinguistics. ◆ Why not as an object? ◆ Class: generates instances. ◆ Answer: Let's go for it! ◆ Metaclass: a class whose instances are classes. ● Each object o has a pointer to its class object c which is the ◆ Terminal Instance: cannot be instantiated further. object representing the class to which o belongs. Objects Class Classes Terminal Instances Novel Play Instantiable objects Non instantiable objects Macbeth Othello Metaclasses Instances are classes 1984 War & Peace As you like Main Text Book Reference: G.Masini et al. Oliver Twist Object-Oriented Languages, APIC series, No.34 oop Õ Ö oop Õ Ö ® 5 ® 6 Taxonomy of Metaclass Systems The 3 Level System ◆ 1-Level System: Objects only Object ● Each object describes itself INSTANCE _OF ● No need for classes: objects are ìinstantiatedî or ìinheritedî from SUBCLASS _OF other objects Class Example: Self VARIABLES instance_of ,167$1&(B2) ◆ 2-Level System: Objects, Classes METHODS .. -

UNIT–IV: Pointers
Q&A for Previous Year Questions Subject: CPDS (B.Tech. I Year) Subject Code: GR11A1003 UNIT-IV ------------------------------------------------------------------------------------------------------------------------------------------ UNIT–IV: Pointers: Pointers and Addresses, Pointers and function Arguments, Pointers and arrays, Address Arithmetic, Character pointers and Functions, Pointer Arrays, Pointers to Structures, Pointers to Pointers, Command Line Arguments. Files: Introduction, Types of Files, File Access Functions, I/O on Files, Random Access to Files, Error Handling. UNIT-IV 1) What is pointer in c programming? What are its benefits? Pointer is a user defined data type that creates special types of variables which can hold the address of primitive data type like char, int, float, double or user defined data type like function, pointer etc. or derived data type like array, structure, union, enum. Examples: int *ptr; int (*ptr)(); int (*ptr)[2]; Benefits of using pointers are:- 1) Pointers are more efficient in handling arrays and data tables. 2) Pointers can be used to return multiple values from a function via function arguments. 3) The use of pointer arrays to character strings results in saving of data storage space in memory. 4) Pointers allow C to support dynamic memory management. 5) Pointers provide an efficient tool for manipulating dynamic data structures such as structures , linked lists , queues , stacks and trees. 6) Pointers reduce length and complexity of programs. 7) They increase the execution speed and thus reduce the program execution time. 2) Explain the concept of pointers? In C programming every variable keeps two type of values. 1. Value of variable. 2. Address of variable where it has stored in the memory. -

Preprocessing C++ : Meta-Class Aspects
Preprocessing C++ : Meta-Class Aspects Edward D. Willink Racal Research Limited, Worton Drive, Reading, England +44 118 923 8278 [email protected] Vyacheslav B. Muchnick Department of Computing, University of Surrey, Guildford, England +44 1483 300800 x2206 [email protected] ABSTRACT C++ satisfies the previously conflicting goals of Object-Orientation and run-time efficiency within an industrial strength language. Run-time efficiency is achieved by ignoring the meta-level aspects of Object-Orientation. In a companion paper [15] we show how extensions that replace the traditional preprocessor lexical substitution by an Object-Oriented meta-level substitution fit naturally into C++. In this paper, we place those extensions in the context of a compile-time meta-level, in which application meta-programs can execute to browse, check or create program declarations. An extended example identifies the marshalling aspect as a programming concern that can be fully separated and automatically generated by an application meta-program. Keywords Object-Oriented Language; Preprocessor; C++; Meta-Level; Composition; Weaving; Aspect-Oriented Programming; Pattern Implementation 1 INTRODUCTION Prior to C++, Object Orientation, as exemplified by Smalltalk, was perceived to be inherently inefficient because of the run-time costs associated with message dispatch. C++ introduced a more restrictive Object Model that enabled most of the run-time costs to be resolved by compile-time computation. As a result Object Orientation in C++ is efficient and widely used. C++ requires that the layout of objects be frozen at compile-time, and that the type of the recipient of any message is known. The layout constraint enables a single contiguous memory allocation for each object.