Problem Set 4: the Lorenz Cipher and the Postman's Computer 2/11/2007
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How I Learned to Stop Worrying and Love the Bombe: Machine Research and Development and Bletchley Park
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by CURVE/open How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park Smith, C Author post-print (accepted) deposited by Coventry University’s Repository Original citation & hyperlink: Smith, C 2014, 'How I learned to stop worrying and love the Bombe: Machine Research and Development and Bletchley Park' History of Science, vol 52, no. 2, pp. 200-222 https://dx.doi.org/10.1177/0073275314529861 DOI 10.1177/0073275314529861 ISSN 0073-2753 ESSN 1753-8564 Publisher: Sage Publications Copyright © and Moral Rights are retained by the author(s) and/ or other copyright owners. A copy can be downloaded for personal non-commercial research or study, without prior permission or charge. This item cannot be reproduced or quoted extensively from without first obtaining permission in writing from the copyright holder(s). The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the copyright holders. This document is the author’s post-print version, incorporating any revisions agreed during the peer-review process. Some differences between the published version and this version may remain and you are advised to consult the published version if you wish to cite from it. Mechanising the Information War – Machine Research and Development and Bletchley Park Christopher Smith Abstract The Bombe machine was a key device in the cryptanalysis of the ciphers created by the machine system widely employed by the Axis powers during the Second World War – Enigma. -

Crypto Review
Crypto Review Track 3: Security Workshop Overview • What is Cryptography? • Symmetric Key Cryptography • Asymmetric Key Cryptography • Block and Stream Cipher • Digital Signature and Message Digest Cryptography • Cryptography is everywhere German Lorenz cipher machine Cryptography • Cryptography deals with creang documents that can be shared secretly over public communicaon channels • Other terms closely associated – Cryptanalysis = code breaking – Cryptology • Kryptos (hidden or secret) and Logos (descripGon) = secret speech / communicaon • combinaon of cryptography and cryptanalysis • Cryptography is a funcGon of plaintext and a Notaon: Plaintext (P) cryptographic key Ciphertext (C) C = F(P, k) Cryptographic Key (k) Typical Scenario • Alice wants to send a “secret” message to Bob • What are the possible problems? – Data can be intercepted • What are the ways to intercept this message? • How to conceal the message? – Encrypon Crypto Core • Secure key establishment Alice has key (k) Bob has key (k) • Secure communicaon m Confidenality and integrity m m Alice has key (k) Bob has key (k) Source: Dan Boneh, Stanford It can do much more • Digital Signatures • Anonymous communicaon • Anonymous digital cash – Spending a digital coin without anyone knowing my idenGty – Buy online anonymously? • ElecGons and private aucGons – Finding the winner without actually knowing individual votes (privacy) Source: Dan Boneh, Stanford Other uses are also theoreGcally possible (Crypto magic) What did she • Privately outsourcing computaon search for? E(query) -

VISIT to BLETCHLEY PARK
REPORT of STAR GROUP – VISIT to BLETCHLEY PARK It was 8-30 on the damp drizzly Monday morning of 5th October when our intrepid group of bleary-eyed third-agers left Keyworth to visit the former codebreaking and cipher centre at Bletchley Park. As we progressed south along the M1 motorway the weather started to clear and by the time we arrived in Milton Keynes the rain and drizzle had stopped. For me the first stop was a cup of coffee in the Block C Visitor Centre. We moved out of the Visitor Centre and towards the lake. We were told that many a wartime romantic coupling around this beautiful lake had led to marriage. The beautiful Bletchley Park Lake So… Moving on. We visited the Mansion House with it’s curious variety of styles of architecture. The original owners of the estate had travelled abroad extensively and each time they returned home they added an extension in the styles that they visited on their travels. The Mansion House At the Mansion we saw the sets that had been designed for the Film “The Imitation Game.” The attention to detail led one to feel that you were back there in the dark days of WWII. History of The Mansion Captain Ridley's Shooting Party The arrival of ‘Captain Ridley's Shooting Party’ at a mansion house in the Buckinghamshire countryside in late August 1938 was to set the scene for one of the most remarkable stories of World War Two. They had an air of friends enjoying a relaxed weekend together at a country house. -

The First Americans the 1941 US Codebreaking Mission to Bletchley Park
United States Cryptologic History The First Americans The 1941 US Codebreaking Mission to Bletchley Park Special series | Volume 12 | 2016 Center for Cryptologic History David J. Sherman is Associate Director for Policy and Records at the National Security Agency. A graduate of Duke University, he holds a doctorate in Slavic Studies from Cornell University, where he taught for three years. He also is a graduate of the CAPSTONE General/Flag Officer Course at the National Defense University, the Intelligence Community Senior Leadership Program, and the Alexander S. Pushkin Institute of the Russian Language in Moscow. He has served as Associate Dean for Academic Programs at the National War College and while there taught courses on strategy, inter- national relations, and intelligence. Among his other government assignments include ones as NSA’s representative to the Office of the Secretary of Defense, as Director for Intelligence Programs at the National Security Council, and on the staff of the National Economic Council. This publication presents a historical perspective for informational and educational purposes, is the result of independent research, and does not necessarily reflect a position of NSA/CSS or any other US government entity. This publication is distributed free by the National Security Agency. If you would like additional copies, please email [email protected] or write to: Center for Cryptologic History National Security Agency 9800 Savage Road, Suite 6886 Fort George G. Meade, MD 20755 Cover: (Top) Navy Department building, with Washington Monument in center distance, 1918 or 1919; (bottom) Bletchley Park mansion, headquarters of UK codebreaking, 1939 UNITED STATES CRYPTOLOGIC HISTORY The First Americans The 1941 US Codebreaking Mission to Bletchley Park David Sherman National Security Agency Center for Cryptologic History 2016 Second Printing Contents Foreword ................................................................................ -

Docib: 3853634
DOCib: 3853634 Before BOURBON: American and British COMINT Efforts against Russia and the Soviet Union before 1945 MICHAEL L. PETERSON INTRODUCTION ~BOURBON was the·formally assigned covername for a joint American-British COMINT proje<:t to target the Soviet Union after World War II. But it quickly came to be used as a covername for the target country itself. This was because, from the beginning of the project in August 1945 until June 1946, the project was compartmented. ~Why, looking back from the 1990s, would the Soviet problem be compartmented? The simple answer is that Russia was an ally of the United States and Great Britain, and allies were not supposed to be listening in on each other's communications. Nevertheless, what started out as policy quickly became habit. Correspondence produced several years after the project title was formaJly cance1led continued to refer to the "BOURBON problem.n It wasn't the Soviet Navy, it was the "BOURBON Navy." Those weren't Soviet or even Russian callsigns, those were "BOURBON callsigns," and so on. -('Ss0S~BOURBON is believed to be the first organized, collaborative, cryptologic attack on the Soviet Union, although, ~s we will see, the Army's Signal Intelligence Service (forerunner to the Army Security Agency) actually assigned two cryptanalysts full time to the Soviet diplomatic problem in 1943.1 ~0SiQ!But this story, .. Before BOURBON," is about the earJiest documented American and British ventures against Imperial Russia and the Soviet Union. It should come as no surprise to anyone that the British, who were experts in this business for a couple of hundred years, had been reading Imperial Russian diplomatic correspondence since the eighteenth century. -

Churchill's Diplomatic Eavesdropping and Secret Signals Intelligence As
CHURCHILL’S DIPLOMATIC EAVESDROPPING AND SECRET SIGNALS INTELLIGENCE AS AN INSTRUMENT OF BRITISH FOREIGN POLICY, 1941-1944: THE CASE OF TURKEY Submitted for the Degree of Ph.D. Department of History University College London by ROBIN DENNISTON M.A. (Oxon) M.Sc. (Edin) ProQuest Number: 10106668 All rights reserved INFORMATION TO ALL USERS The quality of this reproduction is dependent upon the quality of the copy submitted. In the unlikely event that the author did not send a complete manuscript and there are missing pages, these will be noted. Also, if material had to be removed, a note will indicate the deletion. uest. ProQuest 10106668 Published by ProQuest LLC(2016). Copyright of the Dissertation is held by the Author. All rights reserved. This work is protected against unauthorized copying under Title 17, United States Code. Microform Edition © ProQuest LLC. ProQuest LLC 789 East Eisenhower Parkway P.O. Box 1346 Ann Arbor, Ml 48106-1346 2 ABSTRACT Churchill's interest in secret signals intelligence (sigint) is now common knowledge, but his use of intercepted diplomatic telegrams (bjs) in World War Two has only become apparent with the release in 1994 of his regular supply of Ultra, the DIR/C Archive. Churchill proves to have been a voracious reader of diplomatic intercepts from 1941-44, and used them as part of his communication with the Foreign Office. This thesis establishes the value of these intercepts (particularly those Turkey- sourced) in supplying Churchill and the Foreign Office with authentic information on neutrals' response to the war in Europe, and analyses the way Churchill used them. -

Simply Turing
Simply Turing Simply Turing MICHAEL OLINICK SIMPLY CHARLY NEW YORK Copyright © 2020 by Michael Olinick Cover Illustration by José Ramos Cover Design by Scarlett Rugers All rights reserved. No part of this publication may be reproduced, distributed, or transmitted in any form or by any means, including photocopying, recording, or other electronic or mechanical methods, without the prior written permission of the publisher, except in the case of brief quotations embodied in critical reviews and certain other noncommercial uses permitted by copyright law. For permission requests, write to the publisher at the address below. [email protected] ISBN: 978-1-943657-37-7 Brought to you by http://simplycharly.com Contents Praise for Simply Turing vii Other Great Lives x Series Editor's Foreword xi Preface xii Acknowledgements xv 1. Roots and Childhood 1 2. Sherborne and Christopher Morcom 7 3. Cambridge Days 15 4. Birth of the Computer 25 5. Princeton 38 6. Cryptology From Caesar to Turing 44 7. The Enigma Machine 68 8. War Years 85 9. London and the ACE 104 10. Manchester 119 11. Artificial Intelligence 123 12. Mathematical Biology 136 13. Regina vs Turing 146 14. Breaking The Enigma of Death 162 15. Turing’s Legacy 174 Sources 181 Suggested Reading 182 About the Author 185 A Word from the Publisher 186 Praise for Simply Turing “Simply Turing explores the nooks and crannies of Alan Turing’s multifarious life and interests, illuminating with skill and grace the complexities of Turing’s personality and the long-reaching implications of his work.” —Charles Petzold, author of The Annotated Turing: A Guided Tour through Alan Turing’s Historic Paper on Computability and the Turing Machine “Michael Olinick has written a remarkably fresh, detailed study of Turing’s achievements and personal issues. -

Agnes Meyer Driscoll Vs. the Enigma and the Bombe Colin Burke
Colin Burke 1-2001 © Agnes Meyer Driscoll vs. the Enigma and the Bombe Colin Burke ABSTRACT: Documents in Britain‘s National Archives/ Public Record Office and in the U.S. National Archive‘s Record Groups RG457 and RG38 indicate that in mid-1941 the United States Navy‘s codebreaking organization, OP-20-G ignored an opportunity to gain full knowledge of Britain‘s anti-Enigma methods and machines. Spending a year and one-half working on what it felt was a unique and much more effective method– but one that failed--OP-20-G‘s, staff, at a critical time in U.S.- British relations ,did not inform America‘s decision makers of Britain‘s willingness to share its crypto-secrets . As a result, American leaders believed that England‘s GC&CS had deliberately withheld vital information that would have allowed the development of an independent American attack on Naval Enigma. That belief lasted Colin Burke 1-2001 © throughout the war and caused friction between the two nations. Other consequences of OP-20-G‘s mid-1941 decision were to delay the adoption of the British Bombe and its allied methods and to waste perhaps six months of the vital time of the new team of cryptanalysts and engineers assigned, in early 1942, to develop an American Bombe. KEYWORDS: OP-20-G, Enigma, Driscoll, Denniston, GC&CS, Bombe, Safford, Wenger, Weeks, Currier, Engstrom, catalog, Banburismus, hot-point, cold-point, Tiltman. Introduction: A Fragile British-American Crypto-Alliance By the end of World War II Great Britain and the United States had forged uniquely close relationships--even among their intelligence agencies.1 Much had to be overcome to achieve the long-lasting 1 Robert Louis Benson, A History of U.S. -

Code Breaking in the Pacific
Code Breaking in the Pacific Peter Donovan • John Mack Code Breaking in the Pacific 123 Peter Donovan John Mack School of Mathematics and Statistics School of Mathematics and Statistics University of New South Wales University of Sydney Sydney, NSW, Australia Sydney, NSW, Australia Additional material to this book can be downloaded from http://extras.springer.com ISBN 978-3-319-08277-6 ISBN 978-3-319-08278-3 (eBook) DOI 10.1007/978-3-319-08278-3 Springer Cham Heidelberg New York Dordrecht London Library of Congress Control Number: 2014945227 © Springer International Publishing Switzerland 2014 This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifically the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfilms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. Exempted from this legal reservation are brief excerpts in connection with reviews or scholarly analysis or material supplied specifically for the purpose of being entered and executed on a computer system, for exclusive use by the purchaser of the work. Duplication of this publication or parts thereof is permitted only under the provisions of the Copyright Law of the Publisher’s location, in its current version, and permission for use must always be obtained from Springer. Permissions for use may be obtained through RightsLink at the Copyright Clearance Center. Violations are liable to prosecution under the respective Copyright Law. The use of general descriptive names, registered names, trademarks, service marks, etc. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -
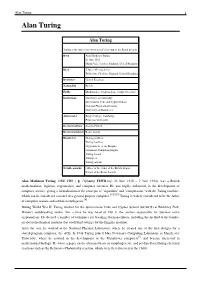
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright
Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright 1 Introduction 2 2 The Enigma Machine 2 2.1 Encryption and Decryption Process 3 2.2 Enigma Weaknesses 4 2.2.1 Encrypting the Key Twice 4 2.2.2 Cillies 5 2.2.3 The Enigma Machine Itself 5 3 Zygalski Sheets 6 3.1 Using Zygalski Sheets 6 3.2 Programmatic Replication 7 3.3 Weaknesses/Problems 7 4 The Bombe 8 4.1 The Bombe In Code 10 4.1.1 Making Menus 10 4.1.2 Running Menus through the Bombe 10 4.1.3 Checking Stops 11 4.1.4 Creating Messages 11 4.1.5 Automating the Process 11 5 Conclusion 13 References 14 1 Introduction To keep radio communications secure during World War II, forces on both sides of the war relied on encryption. The main encryption scheme used by the German military for most of World War II employed the use of an Enigma machine. As such, Britain employed a large number of codebreakers and analysts to work towards breaking the Enigma-created codes, using many different methods. In this paper, we lay out information we learned while researching these methods, as well as describe our attempts at programatically recreating two methods: Zygalski sheets and the Bombe. 2 The Enigma Machine The Enigma machine was invented at the end of World War I, by a German engineer named Arthur Scherbius. It was commercially available in the 1920s before being adopted by the German military, among others, around the beginning of World War II.