Crypto Review
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Simply Turing
Simply Turing Simply Turing MICHAEL OLINICK SIMPLY CHARLY NEW YORK Copyright © 2020 by Michael Olinick Cover Illustration by José Ramos Cover Design by Scarlett Rugers All rights reserved. No part of this publication may be reproduced, distributed, or transmitted in any form or by any means, including photocopying, recording, or other electronic or mechanical methods, without the prior written permission of the publisher, except in the case of brief quotations embodied in critical reviews and certain other noncommercial uses permitted by copyright law. For permission requests, write to the publisher at the address below. [email protected] ISBN: 978-1-943657-37-7 Brought to you by http://simplycharly.com Contents Praise for Simply Turing vii Other Great Lives x Series Editor's Foreword xi Preface xii Acknowledgements xv 1. Roots and Childhood 1 2. Sherborne and Christopher Morcom 7 3. Cambridge Days 15 4. Birth of the Computer 25 5. Princeton 38 6. Cryptology From Caesar to Turing 44 7. The Enigma Machine 68 8. War Years 85 9. London and the ACE 104 10. Manchester 119 11. Artificial Intelligence 123 12. Mathematical Biology 136 13. Regina vs Turing 146 14. Breaking The Enigma of Death 162 15. Turing’s Legacy 174 Sources 181 Suggested Reading 182 About the Author 185 A Word from the Publisher 186 Praise for Simply Turing “Simply Turing explores the nooks and crannies of Alan Turing’s multifarious life and interests, illuminating with skill and grace the complexities of Turing’s personality and the long-reaching implications of his work.” —Charles Petzold, author of The Annotated Turing: A Guided Tour through Alan Turing’s Historic Paper on Computability and the Turing Machine “Michael Olinick has written a remarkably fresh, detailed study of Turing’s achievements and personal issues. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -
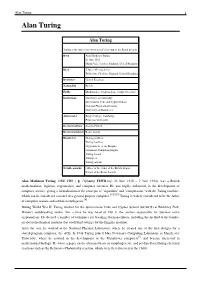
Alan Turing 1 Alan Turing
Alan Turing 1 Alan Turing Alan Turing Turing at the time of his election to Fellowship of the Royal Society. Born Alan Mathison Turing 23 June 1912 Maida Vale, London, England, United Kingdom Died 7 June 1954 (aged 41) Wilmslow, Cheshire, England, United Kingdom Residence United Kingdom Nationality British Fields Mathematics, Cryptanalysis, Computer science Institutions University of Cambridge Government Code and Cypher School National Physical Laboratory University of Manchester Alma mater King's College, Cambridge Princeton University Doctoral advisor Alonzo Church Doctoral students Robin Gandy Known for Halting problem Turing machine Cryptanalysis of the Enigma Automatic Computing Engine Turing Award Turing test Turing patterns Notable awards Officer of the Order of the British Empire Fellow of the Royal Society Alan Mathison Turing, OBE, FRS ( /ˈtjʊərɪŋ/ TEWR-ing; 23 June 1912 – 7 June 1954), was a British mathematician, logician, cryptanalyst, and computer scientist. He was highly influential in the development of computer science, giving a formalisation of the concepts of "algorithm" and "computation" with the Turing machine, which can be considered a model of a general purpose computer.[1][2][3] Turing is widely considered to be the father of computer science and artificial intelligence.[4] During World War II, Turing worked for the Government Code and Cypher School (GC&CS) at Bletchley Park, Britain's codebreaking centre. For a time he was head of Hut 8, the section responsible for German naval cryptanalysis. He devised a number of techniques for breaking German ciphers, including the method of the bombe, an electromechanical machine that could find settings for the Enigma machine. -

Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright
Breaking Enigma Samantha Briasco-Stewart, Kathryn Hendrickson, and Jeremy Wright 1 Introduction 2 2 The Enigma Machine 2 2.1 Encryption and Decryption Process 3 2.2 Enigma Weaknesses 4 2.2.1 Encrypting the Key Twice 4 2.2.2 Cillies 5 2.2.3 The Enigma Machine Itself 5 3 Zygalski Sheets 6 3.1 Using Zygalski Sheets 6 3.2 Programmatic Replication 7 3.3 Weaknesses/Problems 7 4 The Bombe 8 4.1 The Bombe In Code 10 4.1.1 Making Menus 10 4.1.2 Running Menus through the Bombe 10 4.1.3 Checking Stops 11 4.1.4 Creating Messages 11 4.1.5 Automating the Process 11 5 Conclusion 13 References 14 1 Introduction To keep radio communications secure during World War II, forces on both sides of the war relied on encryption. The main encryption scheme used by the German military for most of World War II employed the use of an Enigma machine. As such, Britain employed a large number of codebreakers and analysts to work towards breaking the Enigma-created codes, using many different methods. In this paper, we lay out information we learned while researching these methods, as well as describe our attempts at programatically recreating two methods: Zygalski sheets and the Bombe. 2 The Enigma Machine The Enigma machine was invented at the end of World War I, by a German engineer named Arthur Scherbius. It was commercially available in the 1920s before being adopted by the German military, among others, around the beginning of World War II. -

Problem Set 4: the Lorenz Cipher and the Postman's Computer 2/11/2007
CS150: Problem Set 4: The Lorenz Cipher and the Postman's Computer Page 1 of 8 University of Virginia, Department of Computer Science cs150: Computer Science — Spring 2007 Out: 12 February 2007 Problem Set 4: Creating Colossi Due: 19 February 2007 (beginning of class) Collaboration Policy - Read Carefully This problem set is intended to help you prepare for Exam 1. You may work on it by yourself or with other students, but you will need to do the exam on your own. Regardless of whether you work alone or with a partner, you are encouraged to discuss this assignment with other students in the class and ask and provide help in useful ways. You may consult any outside resources you wish including books, papers, web sites and people. If you use resources other than the class materials, indicate what you used along with your answer. You have only one week to complete this problem set. We recommend you start early and take advantage of the staffed lab hours . Purpose Get practice with some of the material that will be on Exam 1 including: recursive definitions, procedures, lists, and measuring work. Learn about cryptography and the first problems that were solved by computers. Download: Download ps4.zip to your machine and unzip it into your home directory J:\cs150\ps4 . This file contains: ps4.scm — A template for your answers. You should do the problem set by editing this file. lorenz.scm — Some helpful definitions for this problem set. Background Cryptography means secret writing . The goal of much cryptography is for one person to send a message to another person over a channel that an adversary may be eavesdropping on without the eavesdropper understanding the message. -

Copyrighted Material
k Trim Size: 170mm x 244mm Walker c01.tex V3 - 01/27/2016 3:11 P.M. Page 1 1 Why Graphics Processing Units Perri Needham1, Andreas W. Götz2 and Ross C. Walker1,2 1San Diego Supercomputer Center, UCSD, La Jolla, CA, USA 2Department of Chemistry and Biochemistry, UCSD, La Jolla, CA, USA 1.1 A Historical Perspective of Parallel Computing k The first general-purpose electronic computers capable of storing instructions came into existence in k 1950. That is not to say, however, that the use of computers to solve electronic structure problems had not already been considered, or realized. From as early as 1930 scientists used a less advanced form of computation to solve their quantum mechanical problems, albeit a group of assistants simultaneously working on mechanical calculators but an early parallel computing machine nonetheless [1]. It was clear from the beginning that solutions to electronic structure problems could not be carried forward to many-electron systems without the use of some computational device to lessen the mathematical burden. Today’s computational scientists rely heavily on the use of parallel electronic computers. Parallel electronic computers can be broadly classified as having either multiple processing ele- ments in the same machine (shared memory) or multiple machines coupled together to form a cluster/ grid of processing elements (distributed memory). These arrangements make it possible to perform calculations concurrently across multiple processing elements, enabling large problems to be broken down into smaller parts that can be solved simultaneously (in parallel). The first electronic computers were primarily designed for and funded by military projects to assist in World War II and the start of the Cold War [2]. -

An Introduction to Applied Cryptography
SI4 { R´eseauxAvanc´es Introduction `ala s´ecurit´edes r´eseauxinformatiques An Introduction to Applied Cryptography Dr. Quentin Jacquemart [email protected] http://www.qj.be/teaching/ 1 / 129 Outline ) Introduction • Classic Cryptography and Cryptanalysis • Principles of Cryptography • Symmetric Cryptography (aka. Secret-Key Cryptography) • Asymmetric Cryptography (aka. Public-Key Cryptography) • Hashes and Message Digests • Conclusion 1 / 129 2 / 129 Introduction I • Cryptography is at the crossroads of mathematics, electronics, and computer science • The use of cryptography to provide confidentiality is self-evident • But cryptography is a cornerstone of network security • Cryptology is a (mathematical) discipline that includes | cryptography: studies how to exchange confidential messages over an unsecured/untrusted channel | cryptanalysis: studies how to extract meaning out of a confidential message, i.e. how to breach cryptography 2 / 129 3 / 129 Introduction II • Plaintext: the message to be exchanged between Alice and Bob (P) • Ciphering: a cryptographic function that encodes the plaintext into ciphertext (encrypt: E(·)) • Ciphertext: result of applying the cipher function to the plain text (unreadable) (C) • Deciphering: a cryptographic function that decodes the ciphertext into plaintext (decrypt: D(·)) • Key: a secret parameter given to the cryptographic functions (K ) 3 / 129 4 / 129 Introduction III Trudy Alice Bob plaintext ciphertext plaintext P E(P) P E(P) = D(E(P)) Encryption Decryption Algorithm Algorithm E(·) D(·) -

Jewel Theatre Audience Guide Addendum: Alan Turing Biography
Jewel Theatre Audience Guide Addendum: Alan Turing Biography directed by Kirsten Brandt by Susan Myer Silton, Dramaturg © 2019 ALAN TURING The outline of the following overview of Turing’s life is largely based on his biography on Alchetron.com (https://alchetron.com/Alan-Turing), a “social encyclopedia” developed by Alchetron Technologies. It has been embellished with additional information from sources such as Andrew Hodges’ books, Alan Turing: The Enigma (1983) and Turing (1997) as well as his website, https://www.turing.org.uk. The following books have also provided additional information: Prof: Alan Turing Decoded (2015) by Dermot Turing, who is Alan’s nephew by way of his only sibling, John; The Turing Guide by B. Jack Copeland, Jonathan Bowen, Mark Sprevak, and Robin Wilson (2017); and Alan M. Turing, written by his mother, Sara, shortly after he died. The latter was republished in 2012 as Alan M. Turing – Centenary Edition with an Afterword entitled “My Brother Alan” by John Turing. The essay was added when it was discovered among John’s writings following his death. The republication also includes a new Foreword by Martin Davis, an American mathematician known for his model of post-Turing machines. Extended biographies of Christopher Morcom, Dillwyn Knox, Joan Clarke (the character of Pat Green in the play) and Sara Turing, which are provided as Addendums to this Guide, provide additional information about Alan. Beginnings Alan Mathison Turing was an English computer scientist, mathematician, logician, cryptanalyst, philosopher and theoretical biologist. He was born in a nursing home in Maida Vale, a tony residential district of London, England on June 23, 1912. -

Lorenz Cipher
Cryptography in World War II Jefferson Institute for Lifelong Learning at UVa Spring 2006 David Evans Menu Class 4: • Some loose ends on WWII Modern •Maurice Burnett Cryptography • Modern Cryptography – Modern symmetric ciphers – Public-key cryptosystems http://www.cs.virginia.edu/jillcrypto JILL WWII Crypto Spring 2006 - Class 4: Modern Cryptography 2 British Cipher Machine German Code-Breaking Efforts • Design based on commercial Enigma • About 6,000 people (compare to 12,000 working at Bletchley Park) • 5 rotor wheels (instead • Decentralized: each military branch had of 3 in Enigma) their own, didn’t share what they learned • Multiple rings per rotor • Effective against manual codes: broke • Last 2 rotor wheels about 50% of manually coded messages didn’t rotate • Didn’t attempt to break rotor-based • British attempted to ciphers – so confident Enigma was break it (without unbreakable, didn’t try to Typex and success) similar machines Typex Machine JILL WWII Crypto Spring 2006 - Class 4: Modern Cryptography 3 JILL WWII Crypto Spring 2006 - Class 4: Modern Cryptography 4 Lorenz Cipher From http://www.codesandciphers.org.uk/lorenz/fish.htm JILL WWII Crypto Spring 2006 - Class 4: Modern Cryptography 5 JILL WWII Crypto Spring 2006 - Class 4: Modern Cryptography 6 1 Modern Symmetric Ciphers Modern Ciphers A billion billion is a large number, but it's not that large a number. Whitfield Diffie • AES (Rijndael) successor to DES selected 2001 • Same idea but: • 128-bit keys, encrypt 128-bit blocks –Use digital logic instead of • Brute force -

19 Lorenz Cipher Machine 19 Lorenz Cipher Machine
Pupil Text MEP: Codes and Ciphers, UNIT 19 Lorenz Cipher Machine 19 Lorenz Cipher Machine During the Second World War, the codebreakers at Bletchley Park devised a variety of techniques that enabled the Allies to break the major codes used by the Germans. Not only was this hugely significant in helping the Allies to win the war, but it also led on to whole new branches of statistical analysis and to the development of the electronic computer. In this unit we will illustrate how one of the important ciphers used by the Germans was broken. The cipher is the Lorenz cipher which was based on the use of five bit binary numbers. ENCIPHER The code used to convert letters to binary numbers is given below. A 11000 B 10011 C 01110 D 10010 E 10000 F 10110 G 01011 H 00101 I 01100 J 11010 K 11110 L 01001 M 00111 N 00110 O 00011 P 01101 Q 11101 R 01010 S 10100 T 00001 U 11100 V 01111 W 11001 X 10111 Y 10101 Z 10001 There were also six special symbols used to control the automatic printers – these are given below. 3 00010 4 01000 8 11111 9 00100 + 11011 / 00000 These special symbols did not have their usual meanings; the only one to be used in messages is '9' which means 'a space' (between words). Clearly, if this was the code, it would not take too long to break it (letter frequency, for example, could be used). But the code-writers also used a 'key' letter to add to each plaintext letter in order to disguise it. -

John Hunt Professor Derek Bruff FYWS Cryptography 28 October
Hunt 1 John Hunt Professor Derek Bruff FYWS Cryptography 28 October 2010 Most people familiar with codes and cryptography have at least heard of the German Enigma Machines. However, very few people have heard of the Lorenz Cipher Machine. The Lorenz Schlüsselzusatz 43, also known as the Lorenz SZ 43, was the successor of the enigma machines and was used throughout World War II by the Hitler and his commanding officers. The SZ 43 is notable not only for the advancements that it created in the field of cryptography but also the advancements made by cryptanalysis in order to counter the innovation, specifically the invention of Colossus, the predecessor of the modern computer. The German Enigma machines offered the strongest form of encryption available to the Germans for quite a while. Unfortunately those machines had their flaws, namely the difficulty and amount of time needed to send a message. When an enigma machine was used one person would type the message in plaintext, for each letter struck, a different letter of cipher text would be flashed on a bulb and an assistant would record whatever letter appeared in the ciphertext. Then a radio operator would take the encrypted message and, using Morse code, send the message to the receiver. The entire process would then have to be reversed in order for the original message to be read (Copeland 36). This process required six people and obviously took a substantial amount of time to do. The SZ 43 simplified the process by requiring only one person to type in the original message. -

Cryptography in the Digital Age
UNLV Retrospective Theses & Dissertations 1-1-2007 Cryptography in the digital age Thomas R. Hodge University of Nevada, Las Vegas Follow this and additional works at: https://digitalscholarship.unlv.edu/rtds Repository Citation Hodge, Thomas R., "Cryptography in the digital age" (2007). UNLV Retrospective Theses & Dissertations. 2237. http://dx.doi.org/10.25669/eb4o-rhq3 This Thesis is protected by copyright and/or related rights. It has been brought to you by Digital Scholarship@UNLV with permission from the rights-holder(s). You are free to use this Thesis in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you need to obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Thesis has been accepted for inclusion in UNLV Retrospective Theses & Dissertations by an authorized administrator of Digital Scholarship@UNLV. For more information, please contact [email protected]. CRYPTOGRAPHY IN THE DIGITAL AGE by Thomas R. Hodge, Jr. Bachelor of Science Angelo State University, San Angelo, Texas 2002 A thesis submitted in partial fulfillment of the requirements for the Master of Science Degree in Mathematical Sciences Department of Mathematical Sciences College of Sciences Graduate College University of Nevada, Las Vegas December 2007 Reproduced with permission of the copyright owner. Further reproduction prohibited without permission. UMI Number: 1452248 INFORMATION TO USERS The quality of this reproduction is dependent upon the quality of the copy submitted. Broken or indistinct print, colored or poor quality illustrations and photographs, print bleed-through, substandard margins, and improper alignment can adversely affect reproduction.